In the digital age, personal and financial information is more vulnerable than ever. Creating and using strong passwords is one of the best defenses against potential security vulnerabilities. However, a Google study shows that the situation is not optimistic when it comes to creating and maintaining passwords. Many people use simple and easy-to-guess passwords (such as abc123, password, 123456, Qwerty, etc.) and even reuse the same password in multiple accounts.
To avoid becoming a victim of a security accident, follow these suggestions to create safe and reliable passwords and learn how to remember these complex passwords:

The best tips for creating strong passwords
Strong passwords are easy to remember, but difficult to guess. Please remember the following points:
- Combination Characters: Use a combination of uppercase, lowercase letters, numbers, and symbols to create unique and difficult to guess passwords. For example, $K80Fx8#8j and i5eBv^h5#.
- Password length: The longer the password, the better. Many websites require at least 8 characters, but at least 12 characters are recommended.
- Use meaningless phrases: combine random words and phrases to grow passwords, avoiding words or common phrases in the dictionary.
- Different websites use different passwords: This reduces the risk of hackers being able to access other websites after hacking into one website.
- Change password regularly: For sensitive information, change passwords more frequently. After the change, avoid using the same password for a long time.
- Using Password Generator: Password Generators (such as Secrets) can generate hard-to-remember but more secure passwords and provide password management capabilities.

The Secrets application can store passwords, credit cards, bank details, and more.
Notes on creating passwords
- Avoid using personal information: Do not include information such as birth year, month, date, name, family member name, hobby or workplace in your password.
- Avoid dictionary words: replace letters with numbers or symbols, or spell the word intentionally wrongly.
- Avoid reuse of passwords: Use different passwords for different accounts. If all passwords are difficult to remember, you can use a password manager such as Secrets or 1Password.
- Avoid using the same password for a long time: Regular changes to passwords can significantly reduce the risk of hackers guessing passwords.
- Avoid storing passwords in unencrypted files: This makes it easier for hackers to steal passwords.
Additional safety measures
In addition to strong passwords, other security measures can be used to protect data, such as two-factor authentication. Two-factor authentication prevents intruders from accessing their accounts even if their passwords are stolen.

Step Two can protect the security of your Google, Twitter, Facebook, Amazon and other accounts.
How to remember complex passwords
Do not write passwords on paper or store them in unsafe places. Using a secure encryption password manager such as Secrets is a better choice. Use two-factor authentication where possible to increase account security. Both Secrets and Step Two are available on Setapp and offer a free trial.
The above is the detailed content of How to create a strong password: do's and don'ts. For more information, please follow other related articles on the PHP Chinese website!
 How to Install MacOS Sequoia Public BetaMay 15, 2025 am 10:39 AM
How to Install MacOS Sequoia Public BetaMay 15, 2025 am 10:39 AMThe MacOS Sequoia public beta program is now available, providing Mac users with an early chance to explore the new major MacOS system software update. However, it's important to note that, like all beta versions, MacOS Sequoia public beta may be mor
 How to Run Ubuntu Linux on Apple Silicon MacMay 15, 2025 am 10:37 AM
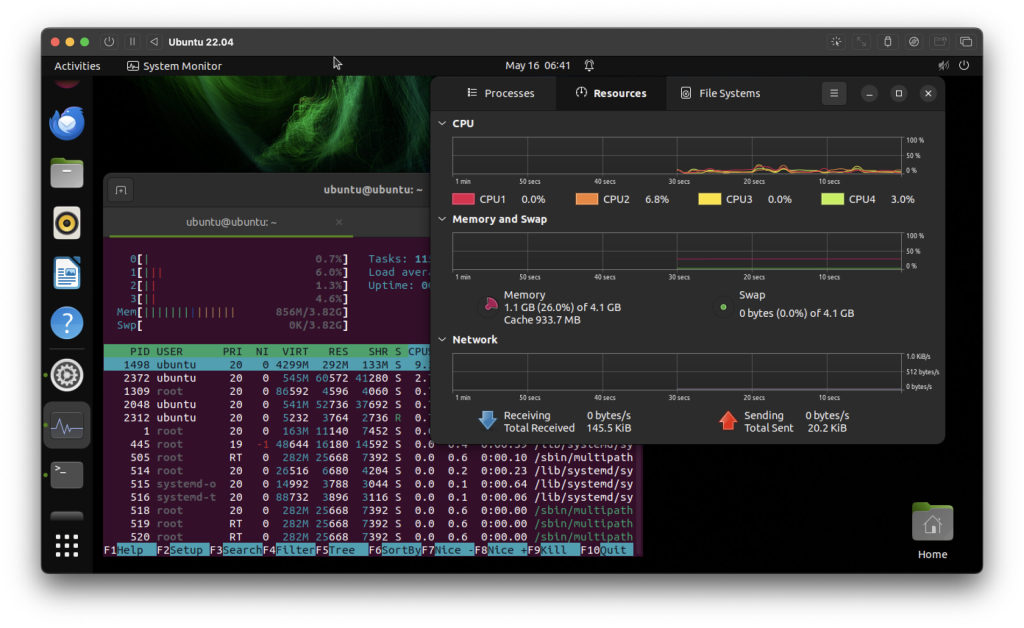
How to Run Ubuntu Linux on Apple Silicon MacMay 15, 2025 am 10:37 AMInterested in running Ubuntu Linux on your Apple Silicon Mac? It's now simpler than ever to run Ubuntu alongside MacOS without the hassle of partitioning, dual booting, or risking your Mac's operating system. Thanks to virtual machine technology, you
 How to See Individual Core CPU Usage on Mac with powermetricsMay 15, 2025 am 10:31 AM
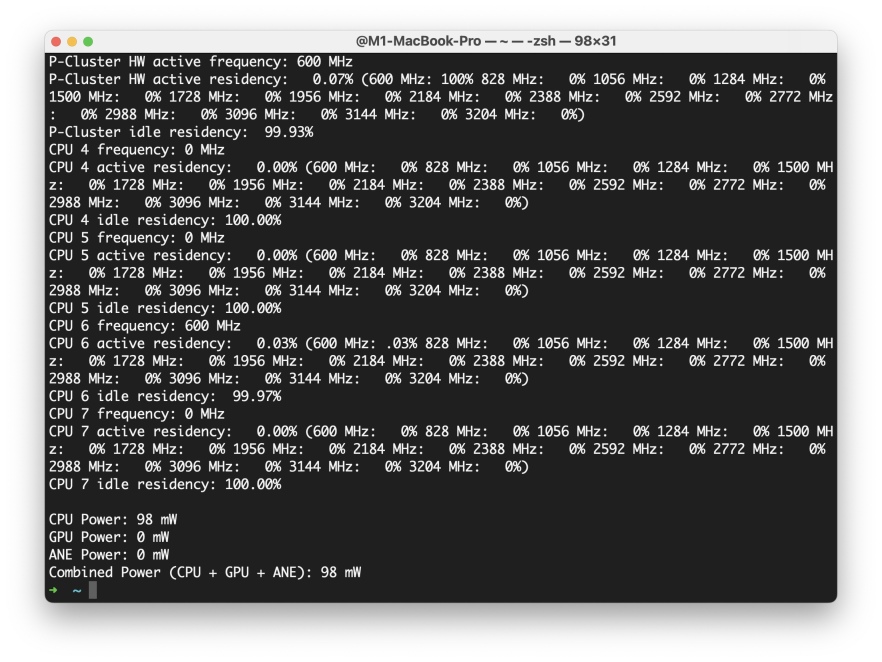
How to See Individual Core CPU Usage on Mac with powermetricsMay 15, 2025 am 10:31 AMThere are multiple methods to track CPU usage on a Mac, with the most popular being Activity Monitor for the graphical interface and htop or top for command line users. While Activity Monitor can display an optional core graph and htop shows CPU core
 chronod on Mac – High CPU Use & Network Access Requests ExplainedMay 15, 2025 am 10:18 AM
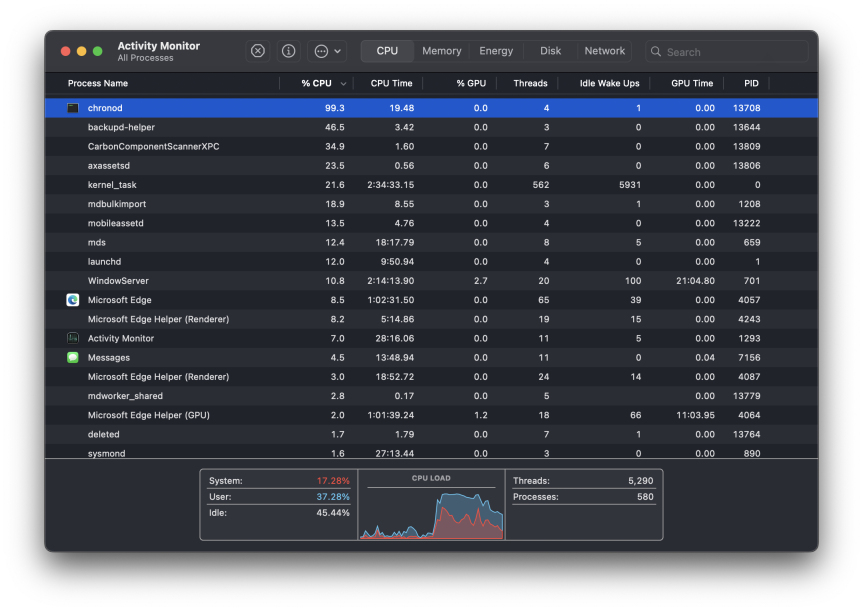
chronod on Mac – High CPU Use & Network Access Requests ExplainedMay 15, 2025 am 10:18 AMSome Mac users occasionally find that the "chronod" process in MacOS either consumes a lot of system resources or requests access to a network connection. Sometimes, chronods are also marked by overly alert antivirus applications. While many people will ignore this situation, there are also curious Mac users who actively explore what specific processes that consume a lot of resources are, or what the intentions are of a process that requires or requires Internet access. So, what is chronod on Mac? Why does it use high CPU and system resources? Why does it require network access? Let's dive into the chronod process to better understand its functionality. What is chronod? The chronod process is
 Security Agent on Mac: What Is It & What Does It Do on MacBook Air/Pro?May 15, 2025 am 10:11 AM
Security Agent on Mac: What Is It & What Does It Do on MacBook Air/Pro?May 15, 2025 am 10:11 AMWhat is Security Agent on MacSecurity Agent on Mac functions as a background process responsible for managing user authentication, system security notifications, and requests for application permissions. It collaborates with macOS's Security Server t
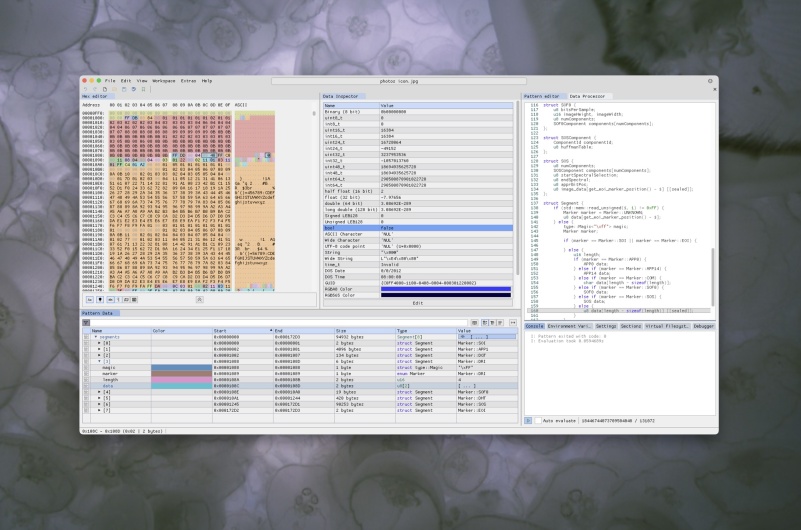 2 of the Best Hex Editors for Mac: ImHex & Hex FiendMay 15, 2025 am 10:05 AM
2 of the Best Hex Editors for Mac: ImHex & Hex FiendMay 15, 2025 am 10:05 AMHex editors are specialized software tools designed for viewing and editing hexadecimal data as well as raw binary data within files. These tools are indispensable for programmers, developers, and reverse engineers who need to inspect, debug, and ana
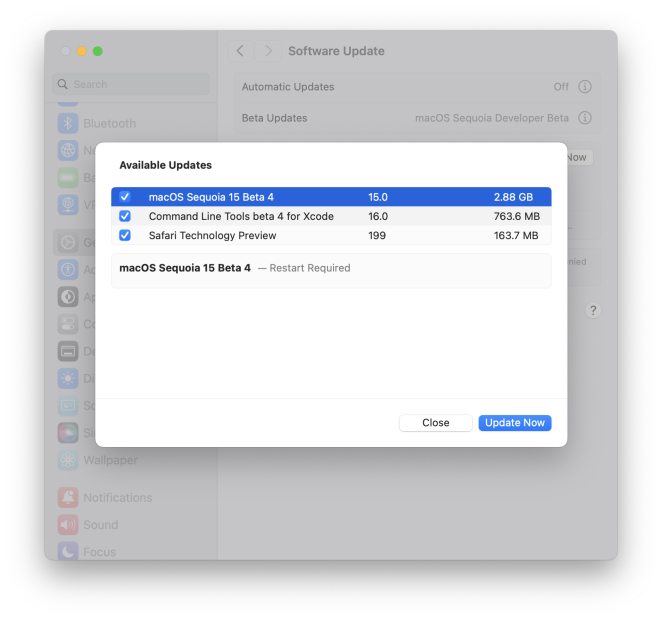 MacOS Sequoia 15 Beta 4 Available to DownloadMay 15, 2025 am 09:54 AM
MacOS Sequoia 15 Beta 4 Available to DownloadMay 15, 2025 am 09:54 AMApple has unveiled the fourth beta release of MacOS Sequoia 15 for those engaged in the macOS Sequoia developer beta testing program. Typically, the corresponding build for public beta testers, labeled as macOS Sequoia public beta 2, is released shor
 FaceTime Not Working on Mac? Here's How to Fix ItMay 15, 2025 am 09:49 AM
FaceTime Not Working on Mac? Here's How to Fix ItMay 15, 2025 am 09:49 AMApple's FaceTime application is designed to connect Apple users seamlessly, offering features such as dual-camera support on smartphones for enhanced video chat experiences.Occasionally, though, FaceTime might not function as intended. This article d


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

SecLists
SecLists is the ultimate security tester's companion. It is a collection of various types of lists that are frequently used during security assessments, all in one place. SecLists helps make security testing more efficient and productive by conveniently providing all the lists a security tester might need. List types include usernames, passwords, URLs, fuzzing payloads, sensitive data patterns, web shells, and more. The tester can simply pull this repository onto a new test machine and he will have access to every type of list he needs.

SublimeText3 English version
Recommended: Win version, supports code prompts!

SublimeText3 Linux new version
SublimeText3 Linux latest version

VSCode Windows 64-bit Download
A free and powerful IDE editor launched by Microsoft

SublimeText3 Mac version
God-level code editing software (SublimeText3)






