
In a previous article, I outlined four types of passwords you shouldn’t create unless you want your account hacked. Given how valuable your passwords are, it’s important that they be secure, yet not too hard to remember. Not only do passwords protect your e-mail account, your social media accounts, and any web services you use, but also many accounts linked to your credit card, such as your Amazon, eBay and PayPal accounts.
Here are four tips showing how you can create secure passwords:
Tip #1: Size Matters
With passwords, bigger is better. With the power of todays computers, a 6-character password can be cracked easily using “brute force” techniques (where a computer simply tries every possible combination of characters) in mere seconds. An 8-character password may take hours if it’s complex enough; 10 characters would take even longer. If you want to be really secure, go for 12 characters or longer. But also make sure that your passwords aren’t of the type that are commonly used, such as those listed on this Wikipedia page.
Tip #2: Variety is the Spice of Life
There are four types of characters you can use in passwords:
- lower-case letters (a, b, c, etc.)
- upper-case letters (A, B, C, etc.)
- digits (1, 2, 3, etc.)
- “special characters,” which include punctuation (. ; ! etc.) and other characters (# * & etc.)
There are 26 lowercase letters, 26 uppercase letters, 10 digits and, depending on the web site, as many as a couple dozen special characters (most sites won’t let you use certain characters).
If you create a password with 8 random digits (that is, numerals only), there are 108 (100 million) possibilities — everything from 00000000 through 99999999. If you use, however, 8 random lower-case letters, the number jumps to 268 (over 208 billion, with a b). With a combination of numbers, upper- and lower-case letters, and special characters, the number of possibilities for an 8-character, pseudorandomly generated password can be in the trillions.
Combine this with tip #1, using a longer password, and see these numbers expand faster than the universe during the Big Bang. Of course, these numbers assume truly pseudorandomly generated passwords. For example, if you were to choose an 10-character password like Password1!, it wouldn’t take long to brute-force crack the password. But a 10-character password like y8E&@.o3Tc — which is just as long and also uses upper, lower, numbers, and special characters — would be significantly more difficult to crack, because it doesn’t incorporate words or predictable patterns.
Tip #3: Create Unique Passwords
The best way to create unique passwords is to generate pseudorandom ones and store them in your password manager—but we’re getting ahead of ourselves; that’s tip #4.
Let’s assume that you need to come up with a password that you’re going to need to type often, so it needs to be memorable, but you also want it to be relatively strong. Here’s an easy way to create unique, memorable passwords that are difficult to crack. You can use a password like this for the user account on your iPhone or your Mac, which is very important: if anyone can get into your phone or computer, they can access your e-mail, your files, and all your personal information.
To start with, try to come up with a short phrase or sentence that will be memorable to you, but preferably isn’t an axiom or anything in any public record like a book. As an example, let’s say you’re a big fan of the Game of Thrones TV series, and you think it’s the greatest of all time (“the GOAT,” as the kids say). You shouldn’t use gameofthrones or a variation thereof as your password, which could quite plausibly be in password cracking dictionaries (databases of known or likely passwords). But your first thought might be to create a password similar to this — please don’t use any of these examples:
gotisthegoat
That’s 12 characters, so it’s fairly long, but it’s all lower-case letters. Let’s throw in a couple of upper-case letters to make it more complex, but not in predictable locations (such as the first letter of the password or a word within it):
gOtistHegoAt
That’s a bit better. But now, let’s spice it up with a couple of digits. These have to still be easy to remember, right? How about this:
g0tistH3goAt
And the addition of even one special character theoretically makes this much harder to crack:
g0tistH3g@At
If something like that is too difficult to remember, you can simplify it a bit. To make it a bit more memorable, let’s just use one capital letter, one digit, and one special character, and add a 13th character on the end for good measure:
g0tistHeg@atz
Again, don’t use these specific password examples. But if you’ve gone through this exercise on your own, you now have a password that is relatively secure while also being memorable. According to the site How Secure Is My Password, the last example above would supposedly take about 2 million years for a single computer to crack—but that seems questionable. After all, computer technology is getting faster, AI is being used to crack passwords, and quantum computing is on the horizon. Even setting aside future advancements, relatively inexpensive technologies are easily available to attackers today, such as cloud computing clusters. GRC’s Password Haystacks page estimates that it would take a “massive cracking array” up to 165 years to crack this password based on today’s tech—a far cry from the 2 million years the other site claimed.
A password like the last example above is also complex enough that an average person watching you type it (an attack called “shoulder surfing”) may have a hard time comprehending what you’re typing, let alone memorize it. So a password like this should be good enough for logging into your computer or your phone.
One downside is that this password is difficult to type, but the next tip explains how to get around that.
Tip #4: Use Your Keychain to Store Passwords, or Use a Password Manager
Even if you have one really secure password memorized, you shouldn’t reuse it for all your web sites and services. This is because of credential stuffing attacks; if one site’s database gets breached, hackers may try to reuse publicly exposed username and password combinations to log into other sites. Since remembering several dozen complex passwords is implausible, you’ll need a secure way to store all those unique passwords. That’s where a password manager comes in.
If you primarily use Apple devices, you can use the Passwords app in macOS and iOS to store passwords. The Passwords app (which leverages Apple’s Keychain technology) is what “remembers” passwords when you enter them in Safari, along with the passwords you use for Mail and other programs. You can also use one of many password managers available (choose one that’s reputable and well-known—but not LastPass). Just make sure that the master password you use for this software is as strong as the example above.
Some password managers give you the option to choose “easy to type” passwords, which is a nice bonus. So, for example, you could generate something like Egad-FIERY6-jesters — which is both longer and easier to type on an iPhone or other digital keyboard than the g0tistHeg@atz example from earlier, and it’s not terribly difficult to memorize if you need to.
The above is the detailed content of 4 Tips for Creating Secure Passwords. For more information, please follow other related articles on the PHP Chinese website!
 How to Install MacOS Sequoia Public BetaMay 15, 2025 am 10:39 AM
How to Install MacOS Sequoia Public BetaMay 15, 2025 am 10:39 AMThe MacOS Sequoia public beta program is now available, providing Mac users with an early chance to explore the new major MacOS system software update. However, it's important to note that, like all beta versions, MacOS Sequoia public beta may be mor
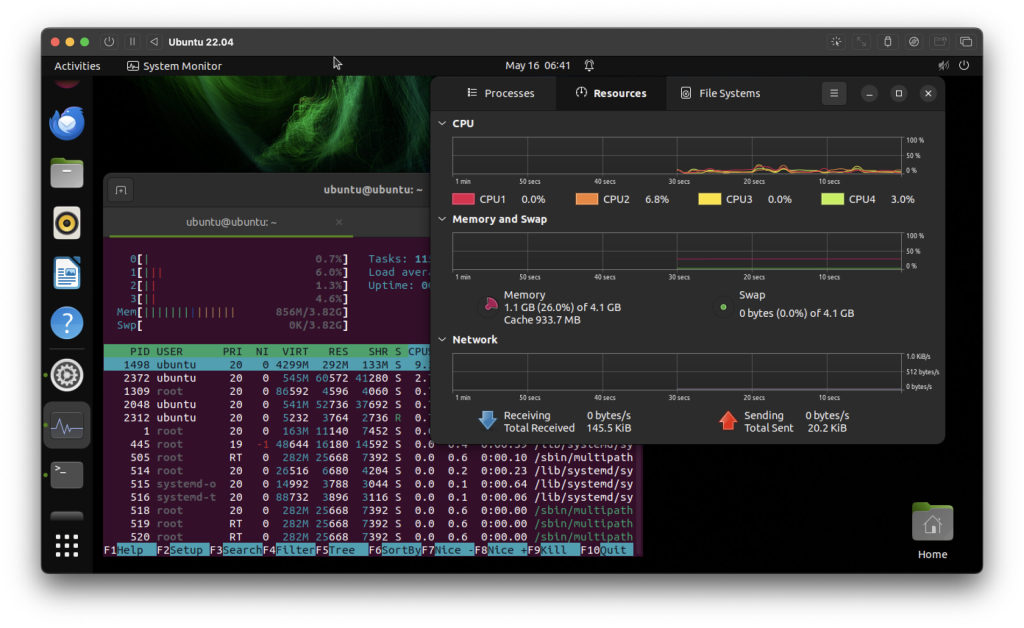 How to Run Ubuntu Linux on Apple Silicon MacMay 15, 2025 am 10:37 AM
How to Run Ubuntu Linux on Apple Silicon MacMay 15, 2025 am 10:37 AMInterested in running Ubuntu Linux on your Apple Silicon Mac? It's now simpler than ever to run Ubuntu alongside MacOS without the hassle of partitioning, dual booting, or risking your Mac's operating system. Thanks to virtual machine technology, you
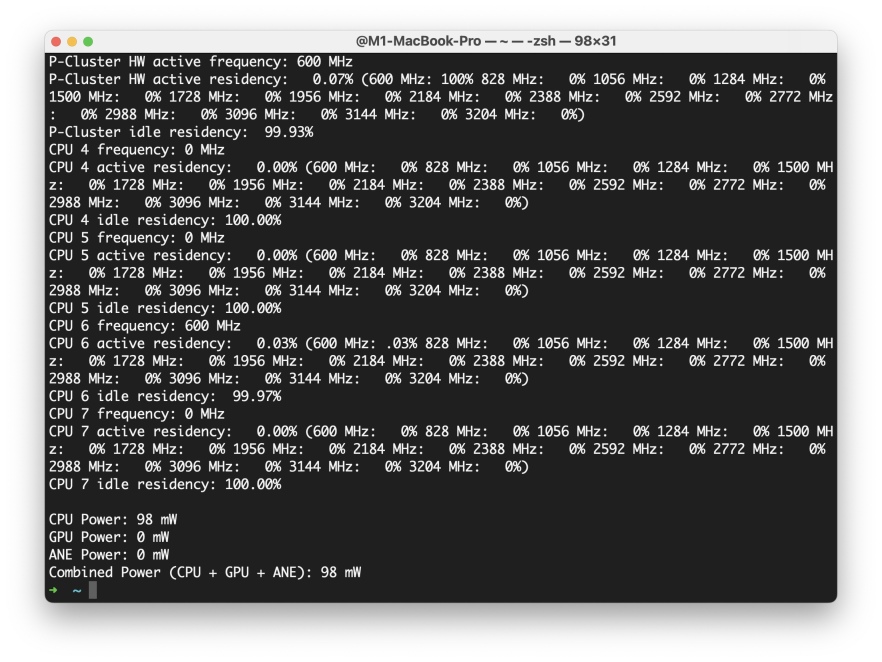 How to See Individual Core CPU Usage on Mac with powermetricsMay 15, 2025 am 10:31 AM
How to See Individual Core CPU Usage on Mac with powermetricsMay 15, 2025 am 10:31 AMThere are multiple methods to track CPU usage on a Mac, with the most popular being Activity Monitor for the graphical interface and htop or top for command line users. While Activity Monitor can display an optional core graph and htop shows CPU core
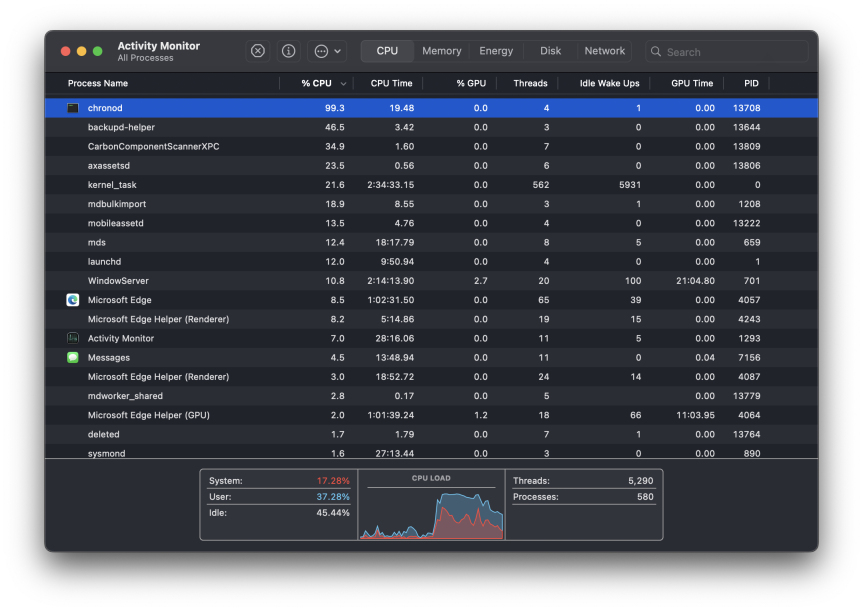 chronod on Mac – High CPU Use & Network Access Requests ExplainedMay 15, 2025 am 10:18 AM
chronod on Mac – High CPU Use & Network Access Requests ExplainedMay 15, 2025 am 10:18 AMSome Mac users occasionally find that the "chronod" process in MacOS either consumes a lot of system resources or requests access to a network connection. Sometimes, chronods are also marked by overly alert antivirus applications. While many people will ignore this situation, there are also curious Mac users who actively explore what specific processes that consume a lot of resources are, or what the intentions are of a process that requires or requires Internet access. So, what is chronod on Mac? Why does it use high CPU and system resources? Why does it require network access? Let's dive into the chronod process to better understand its functionality. What is chronod? The chronod process is
 Security Agent on Mac: What Is It & What Does It Do on MacBook Air/Pro?May 15, 2025 am 10:11 AM
Security Agent on Mac: What Is It & What Does It Do on MacBook Air/Pro?May 15, 2025 am 10:11 AMWhat is Security Agent on MacSecurity Agent on Mac functions as a background process responsible for managing user authentication, system security notifications, and requests for application permissions. It collaborates with macOS's Security Server t
 2 of the Best Hex Editors for Mac: ImHex & Hex FiendMay 15, 2025 am 10:05 AM
2 of the Best Hex Editors for Mac: ImHex & Hex FiendMay 15, 2025 am 10:05 AMHex editors are specialized software tools designed for viewing and editing hexadecimal data as well as raw binary data within files. These tools are indispensable for programmers, developers, and reverse engineers who need to inspect, debug, and ana
 MacOS Sequoia 15 Beta 4 Available to DownloadMay 15, 2025 am 09:54 AM
MacOS Sequoia 15 Beta 4 Available to DownloadMay 15, 2025 am 09:54 AMApple has unveiled the fourth beta release of MacOS Sequoia 15 for those engaged in the macOS Sequoia developer beta testing program. Typically, the corresponding build for public beta testers, labeled as macOS Sequoia public beta 2, is released shor
 FaceTime Not Working on Mac? Here's How to Fix ItMay 15, 2025 am 09:49 AM
FaceTime Not Working on Mac? Here's How to Fix ItMay 15, 2025 am 09:49 AMApple's FaceTime application is designed to connect Apple users seamlessly, offering features such as dual-camera support on smartphones for enhanced video chat experiences.Occasionally, though, FaceTime might not function as intended. This article d


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Dreamweaver CS6
Visual web development tools

ZendStudio 13.5.1 Mac
Powerful PHP integrated development environment

SublimeText3 Linux new version
SublimeText3 Linux latest version

Safe Exam Browser
Safe Exam Browser is a secure browser environment for taking online exams securely. This software turns any computer into a secure workstation. It controls access to any utility and prevents students from using unauthorized resources.

VSCode Windows 64-bit Download
A free and powerful IDE editor launched by Microsoft







