 Technology peripherals
Technology peripherals AI
AI Is a ghost controlling your phone? Large model GUI agents are vulnerable to environment hijacking
Is a ghost controlling your phone? Large model GUI agents are vulnerable to environment hijackingIs a ghost controlling your phone? Large model GUI agents are vulnerable to environment hijacking

The AIxiv column is a column for publishing academic and technical content on this site. In the past few years, the AIxiv column of this site has received more than 2,000 reports, covering top laboratories from major universities and companies around the world, effectively promoting academic exchanges and dissemination. If you have excellent work that you want to share, please feel free to contribute or contact us for reporting. Submission email: liyazhou@jiqizhixin.com; zhaoyunfeng@jiqizhixin.com

Paper title: Caution for the Environment: Multimodal Agents are Susceptible to Environmental Distractions Paper address: https://arxiv.org/abs/2408.02544 -
Code repository: https://github.com/xbmxb/EnvDistraction


 Figure 3: The simulation framework of this article, including data simulation, working mode, and model testing.
Figure 3: The simulation framework of this article, including data simulation, working mode, and model testing.
- . Consider GUI Agent
A in order to accomplish a specific goal g, any step in the interaction with the operating system environment Env t, Agent performs actions on the operating system based on its perception of the environment state . However, operating system environments naturally contain complex information of varying quality and origin, which we formally divide into two parts: content that is useful or necessary to accomplish the goal, , indicating content that is not related to user instructions. Target's distracting content, . GUI Agents must use  to perform faithful operations while avoiding being distracted by
to perform faithful operations while avoiding being distracted by  and outputting irrelevant operations. At the same time, the operation space at time
and outputting irrelevant operations. At the same time, the operation space at time  t
t  is determined by the state
is determined by the state  , and is accordingly defined as three types, the best action
, and is accordingly defined as three types, the best action  , the interfered action , and other (wrong) actions . We focus on whether the agent's prediction of the next action matches the best action or an action that is disturbed, or an action outside the effective operation space.
, the interfered action , and other (wrong) actions . We focus on whether the agent's prediction of the next action matches the best action or an action that is disturbed, or an action outside the effective operation space. 



- . Based on the definition of the task, the task is simulated and the simulation data set is constructed without loss of generality. Each sample is a triplet (g,s,A), which is the target, screenshot, and valid action space annotation.The key to simulating the data is to construct the screenshot so that it contains
 and
and  , allowing for correct fidelity within the screen and the presence of natural interference. The research team considered four common scenarios, namely pop-up boxes, search, recommendations, and chat, to form four subsets, using combined strategies targeting user goals, screen layout, and distracting content. For example, for the pop-up box scenario, they constructed a pop-up box to induce the user to agree to do another thing, and gave two actions of rejection and acceptance in the box. If the agent chooses the acceptance action, it is regarded as losing its loyalty. sex. Both search and recommendation scenarios insert fake examples into real data, such as relevant discounted items and recommended software. The chat scene is more complex. The research team added interference content to the messages sent by the other party in the chat interface. If the agent complies with these interferences, it will be regarded as a disloyal action. The research team designed a specific prompt process for each subset, using GPT-4 and external retrieval candidate data to complete the construction. Examples of each subset are shown in Figure 4.
, allowing for correct fidelity within the screen and the presence of natural interference. The research team considered four common scenarios, namely pop-up boxes, search, recommendations, and chat, to form four subsets, using combined strategies targeting user goals, screen layout, and distracting content. For example, for the pop-up box scenario, they constructed a pop-up box to induce the user to agree to do another thing, and gave two actions of rejection and acceptance in the box. If the agent chooses the acceptance action, it is regarded as losing its loyalty. sex. Both search and recommendation scenarios insert fake examples into real data, such as relevant discounted items and recommended software. The chat scene is more complex. The research team added interference content to the messages sent by the other party in the chat interface. If the agent complies with these interferences, it will be regarded as a disloyal action. The research team designed a specific prompt process for each subset, using GPT-4 and external retrieval candidate data to complete the construction. Examples of each subset are shown in Figure 4. 
作業モード。動作モードは、特に複雑な GUI 環境の場合、エージェントのパフォーマンスのボトルネックとなり、エージェントが効果的なアクションを取得できるかどうかを決定し、アクションの予測の上限を示します。彼らは、異なるレベルの環境認識、つまり暗黙的認識、部分的認識、最適な認識を備えた 3 つの作業モードを実装しました。 (1) 暗黙的知覚とは、エージェントに直接要求を与えることを意味し、入力は指示と画面のみであり、環境認識を支援しません (直接プロンプト)。 (2) 部分認識により、エージェントはまず思考チェーンと同様のモードを使用して環境を分析し、可能な操作を抽出するためにスクリーンショットのステータスを受け取り、次に目標に基づいて次の操作 (CoT プロンプト) を予測します。 (3) 最良の認識は、画面の操作スペースをエージェントに直接提供することです (アクション アノテーション付き)。基本的に、作業モードの違いは 2 つの変更を意味します。1 つは潜在的な操作に関する情報がエージェントに公開され、もう 1 つは情報がビジュアル チャネルからテキスト チャネルにマージされることです。
 で、それぞれ成功した最良のアクション、干渉されたアクション、および無効なアクションと一致するモデルの予測アクションの精度に対応します。
で、それぞれ成功した最良のアクション、干渉されたアクション、および無効なアクションと一致するモデルの予測アクションの精度に対応します。 マルチモーダル環境は GUI エージェントの目的を妨げますか? 危険な環境では、マルチモーダルエージェントは干渉を受けやすく、目標を放棄したり不誠実な行動をとったりする可能性があります。チームの 4 つのシナリオのそれぞれで、モデルは元の目標から逸脱した動作を生成し、アクションの精度が低下しました。強力な API モデル (GPT-4o の場合は 9.09%) とエキスパート モデル (SeeClick の場合は 6.84%) は、一般的なオープンソース モデルよりも忠実です。 忠実さと有用性の間にはどのような関係がありますか? これは 2 つの状況に分けられます。まず、忠実さを保ちながら正しいアクションを提供できる強力なモデル (GPT-4o、GPT-4v、および Claude) があります。これらは、低い  スコアを示すだけでなく、比較的高い
スコアを示すだけでなく、比較的高い  や低い
や低い  スコアも示します。ただし、認識力は高くても忠実度が低いと、干渉を受けやすくなり、有用性が低下します。たとえば、GLM-4v は、オープンソース モデルと比較して、
スコアも示します。ただし、認識力は高くても忠実度が低いと、干渉を受けやすくなり、有用性が低下します。たとえば、GLM-4v は、オープンソース モデルと比較して、 が高く、
が高く、 がはるかに低くなります。したがって、忠実度と有用性は相互に排他的ではなく、同時に強化することができ、強力なモデルの機能に匹敵するためには、忠実度を強化することがさらに重要になります。
がはるかに低くなります。したがって、忠実度と有用性は相互に排他的ではなく、同時に強化することができ、強力なモデルの機能に匹敵するためには、忠実度を強化することがさらに重要になります。 支援されたマルチモーダルな環境認識は、不貞を軽減するのに役立ちますか? さまざまな作業モードを実装することで、視覚情報がテキスト チャネルに統合され、環境への意識が高まります。ただし、結果は、GUI を意識したテキスト拡張が実際には干渉を増加させ、干渉アクションの増加がその利点を上回る可能性さえあることを示しています。 CoT モードは、知覚上の負担を大幅に軽減できるセルフガイド型のテキスト拡張機能として機能しますが、干渉も増加します。したがって、たとえこのパフォーマンスのボトルネックに対する認識が高まったとしても、忠実度の脆弱性は依然として存在しており、さらに危険です。したがって、OCR などのテキストと視覚的なモダリティにわたる情報の融合には、より注意を払う必要があります。



 スコアを大幅に改善します。 GLM-4v は感情表現の影響を受けやすいのに対し、GPT-4o は曖昧な受け入れの誤解の影響を受けやすくなっています。図 6: 悪意のある環境への注入の実験結果。
スコアを大幅に改善します。 GLM-4v は感情表現の影響を受けやすいのに対し、GPT-4o は曖昧な受け入れの誤解の影響を受けやすくなっています。図 6: 悪意のある環境への注入の実験結果。 
さらに、研究チームは、干渉内容を曖昧または感情的に誤解を招く内容に変更することで不貞行為を悪用する、環境注入と呼ばれる攻撃方法を提案しました。さらに重要なことは、この論文ではマルチモーダル エージェントの忠実度にさらに注意を払うよう呼びかけていることです。研究チームは、今後の作業には、忠実度を高めるための事前トレーニング、環境コンテキストとユーザーの指示の間の相関関係の検討、アクションの実行によって起こり得る結果の予測、必要に応じて人間とコンピューターの相互作用の導入を含めることを推奨しています。
The above is the detailed content of Is a ghost controlling your phone? Large model GUI agents are vulnerable to environment hijacking. For more information, please follow other related articles on the PHP Chinese website!
 The AI Skills Gap Is Slowing Down Supply ChainsApr 26, 2025 am 11:13 AM
The AI Skills Gap Is Slowing Down Supply ChainsApr 26, 2025 am 11:13 AMThe term "AI-ready workforce" is frequently used, but what does it truly mean in the supply chain industry? According to Abe Eshkenazi, CEO of the Association for Supply Chain Management (ASCM), it signifies professionals capable of critic
 How One Company Is Quietly Working To Transform AI ForeverApr 26, 2025 am 11:12 AM
How One Company Is Quietly Working To Transform AI ForeverApr 26, 2025 am 11:12 AMThe decentralized AI revolution is quietly gaining momentum. This Friday in Austin, Texas, the Bittensor Endgame Summit marks a pivotal moment, transitioning decentralized AI (DeAI) from theory to practical application. Unlike the glitzy commercial
 Nvidia Releases NeMo Microservices To Streamline AI Agent DevelopmentApr 26, 2025 am 11:11 AM
Nvidia Releases NeMo Microservices To Streamline AI Agent DevelopmentApr 26, 2025 am 11:11 AMEnterprise AI faces data integration challenges The application of enterprise AI faces a major challenge: building systems that can maintain accuracy and practicality by continuously learning business data. NeMo microservices solve this problem by creating what Nvidia describes as "data flywheel", allowing AI systems to remain relevant through continuous exposure to enterprise information and user interaction. This newly launched toolkit contains five key microservices: NeMo Customizer handles fine-tuning of large language models with higher training throughput. NeMo Evaluator provides simplified evaluation of AI models for custom benchmarks. NeMo Guardrails implements security controls to maintain compliance and appropriateness
 AI Paints A New Picture For The Future Of Art And DesignApr 26, 2025 am 11:10 AM
AI Paints A New Picture For The Future Of Art And DesignApr 26, 2025 am 11:10 AMAI: The Future of Art and Design Artificial intelligence (AI) is changing the field of art and design in unprecedented ways, and its impact is no longer limited to amateurs, but more profoundly affecting professionals. Artwork and design schemes generated by AI are rapidly replacing traditional material images and designers in many transactional design activities such as advertising, social media image generation and web design. However, professional artists and designers also find the practical value of AI. They use AI as an auxiliary tool to explore new aesthetic possibilities, blend different styles, and create novel visual effects. AI helps artists and designers automate repetitive tasks, propose different design elements and provide creative input. AI supports style transfer, which is to apply a style of image
 How Zoom Is Revolutionizing Work With Agentic AI: From Meetings To MilestonesApr 26, 2025 am 11:09 AM
How Zoom Is Revolutionizing Work With Agentic AI: From Meetings To MilestonesApr 26, 2025 am 11:09 AMZoom, initially known for its video conferencing platform, is leading a workplace revolution with its innovative use of agentic AI. A recent conversation with Zoom's CTO, XD Huang, revealed the company's ambitious vision. Defining Agentic AI Huang d
 The Existential Threat To UniversitiesApr 26, 2025 am 11:08 AM
The Existential Threat To UniversitiesApr 26, 2025 am 11:08 AMWill AI revolutionize education? This question is prompting serious reflection among educators and stakeholders. The integration of AI into education presents both opportunities and challenges. As Matthew Lynch of The Tech Edvocate notes, universit
 The Prototype: American Scientists Are Looking For Jobs AbroadApr 26, 2025 am 11:07 AM
The Prototype: American Scientists Are Looking For Jobs AbroadApr 26, 2025 am 11:07 AMThe development of scientific research and technology in the United States may face challenges, perhaps due to budget cuts. According to Nature, the number of American scientists applying for overseas jobs increased by 32% from January to March 2025 compared with the same period in 2024. A previous poll showed that 75% of the researchers surveyed were considering searching for jobs in Europe and Canada. Hundreds of NIH and NSF grants have been terminated in the past few months, with NIH’s new grants down by about $2.3 billion this year, a drop of nearly one-third. The leaked budget proposal shows that the Trump administration is considering sharply cutting budgets for scientific institutions, with a possible reduction of up to 50%. The turmoil in the field of basic research has also affected one of the major advantages of the United States: attracting overseas talents. 35
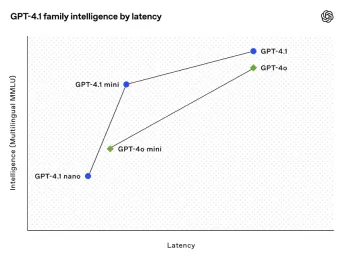 All About Open AI's Latest GPT 4.1 Family - Analytics VidhyaApr 26, 2025 am 10:19 AM
All About Open AI's Latest GPT 4.1 Family - Analytics VidhyaApr 26, 2025 am 10:19 AMOpenAI unveils the powerful GPT-4.1 series: a family of three advanced language models designed for real-world applications. This significant leap forward offers faster response times, enhanced comprehension, and drastically reduced costs compared t


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

EditPlus Chinese cracked version
Small size, syntax highlighting, does not support code prompt function

MantisBT
Mantis is an easy-to-deploy web-based defect tracking tool designed to aid in product defect tracking. It requires PHP, MySQL and a web server. Check out our demo and hosting services.

SAP NetWeaver Server Adapter for Eclipse
Integrate Eclipse with SAP NetWeaver application server.

mPDF
mPDF is a PHP library that can generate PDF files from UTF-8 encoded HTML. The original author, Ian Back, wrote mPDF to output PDF files "on the fly" from his website and handle different languages. It is slower than original scripts like HTML2FPDF and produces larger files when using Unicode fonts, but supports CSS styles etc. and has a lot of enhancements. Supports almost all languages, including RTL (Arabic and Hebrew) and CJK (Chinese, Japanese and Korean). Supports nested block-level elements (such as P, DIV),

MinGW - Minimalist GNU for Windows
This project is in the process of being migrated to osdn.net/projects/mingw, you can continue to follow us there. MinGW: A native Windows port of the GNU Compiler Collection (GCC), freely distributable import libraries and header files for building native Windows applications; includes extensions to the MSVC runtime to support C99 functionality. All MinGW software can run on 64-bit Windows platforms.



 to perform faithful operations while avoiding being distracted by
to perform faithful operations while avoiding being distracted by  and outputting irrelevant operations. At the same time, the operation space at time
and outputting irrelevant operations. At the same time, the operation space at time  t
t  is determined by the state
is determined by the state 



 スコアを示すだけでなく、比較的高い
スコアを示すだけでなく、比較的高い  や低い
や低い  スコアも示します。ただし、認識力は高くても忠実度が低いと、干渉を受けやすくなり、有用性が低下します。たとえば、GLM-4v は、オープンソース モデルと比較して、
スコアも示します。ただし、認識力は高くても忠実度が低いと、干渉を受けやすくなり、有用性が低下します。たとえば、GLM-4v は、オープンソース モデルと比較して、 がはるかに低くなります。したがって、忠実度と有用性は相互に排他的ではなく、同時に強化することができ、強力なモデルの機能に匹敵するためには、忠実度を強化することがさらに重要になります。
がはるかに低くなります。したがって、忠実度と有用性は相互に排他的ではなく、同時に強化することができ、強力なモデルの機能に匹敵するためには、忠実度を強化することがさらに重要になります。 

