php小编百草为您精心撰写了一篇关于使用AAD和AWS Cognito保护Spring Boot REST API的Java问答文章。在这篇文章中,我们将探讨如何利用这两种身份验证服务来保护不同端点,确保您的API安全可靠。跟随我们的指引,学习如何在您的Spring Boot项目中实现身份验证和授权,让您的REST API更加强大和可靠。
问题内容
希望有人可以在这里帮助我,因为我在任何地方都找不到有关此主题的任何资源。
我有一个 spring boot restapi,当前配置有两种路由:1. 未经授权 2. 通过 aad/entra 的 bearer 授权
我的配置方法当前设置如下:
@override
protected void configure(httpsecurity http) throws exception {
super.configure(http);
http.csrf().disable();
http.authorizerequests(requests -> requests
.antmatchers(httpmethod.options, "/**/**").permitall()
.antmatchers("/api/protected/**").fullyauthenticated()
.anyrequest().permitall()
);
}
它包装在一个扩展 aadresourceserverwebsecurityconfigureradapter 的类中。
通过以这种方式配置我们的 api,我们能够按如下方式保护我们的路由:
@preauthorize("hasauthority('approle_appname.rolename')")
@getmapping(value = "/some-method", produces = mediatype.application_json_value)
public responseentity<list<string>> getstrings() {
return responseentity.ok(...);
}
我们的 api 现在应该进行扩展,以允许新型用户使用授权端点。这些用户由 aws cognito 管理。如何设置我的 websecurityconfigureradapter 以允许某些路径未经授权,某些路径通过 aad 进行保护,某些路径通过 aws cognito 进行保护?
我似乎遇到的主要问题是 aadresourceserverwebsecurityconfigureradapter 以这样的方式配置 jwt 验证,它仅适用于 microsoft 提供的 bearers。
理想情况下我想要这样的东西:
@configuration
@enablewebsecurity
@enableglobalmethodsecurity(prepostenabled = true)
public class securityconfig extends websecurityconfigureradapter {
@configuration
@order(1)
public static class azureadsecurityconfig extends aadresourceserverwebsecurityconfigureradapter {
@override
protected void configure(httpsecurity http) throws exception {
http.authorizerequests(requests -> requests
.antmatchers("/api/aad/**").fullyauthenticated()
);
http.oauth2resourceserver().jwt([utilize aad jwt validation]);
}
}
@configuration
@order(2)
public static class awscognitosecurityconfig extends websecurityconfigureradapter {
@override
protected void configure(httpsecurity http) throws exception {
http.authorizerequests(requests -> requests
.antmatchers("/api/cognito/**").fullyauthenticated()
);
http.oauth2resourceserver().jwt([utilize aws cognito jwt validation]);
}
}
@configuration
@order(3)
public static class defaultsecurityconfig extends websecurityconfigureradapter {
@override
protected void configure(httpsecurity http) throws exception {
http.csrf().disable();
http.authorizerequests(requests -> requests
.antmatchers(httpmethod.options, "/**/**").permitall()
.anyrequest().permitall()
);
}
}
}
我发现的另一个问题是 aadresourceserverwebsecurityconfigureradapter 自动将 jwtclaimnames“roles”和“scp”的所有可能的前缀设置为“scope_”和“approle_”。理想情况下,我希望 aad 和 aws cognito 的它们有所不同,以便我将“aad_scope_”、“aad_approle_”和“cognito_group_”作为前缀。
我找到了一些资料解释如何为 spring boot 实现多租户 jwt 验证,但它们都仅使用 sql 数据库实现基于密码/用户的身份验证。
有没有办法基本上必须重新实现所有 aad 逻辑,以便我可以混合对 aws cognito 给出的 jwt 的验证,或者有没有办法根据路由进行决定?
我已经知道您可以在 httpsecurity 上使用 oauth2resourceserver() 函数来配置 jwt 使用情况,但我只找到有关如何为单个租户实现该功能的信息。
如果有人已经成功实施了这个特定或类似的案例,或者可以将我推向正确的方向,我将非常感激。 或者也许我的想法是完全错误的,那么请告诉我。
使用工作解决方案更新(2024 年 1 月 25 日)
感谢 @ch4mp 的回答,我已经成功了。 >工作答案
现在我的实现已经高度简化,如下所示:
应用程序.yml
com:
c4-soft:
springaddons:
oidc:
ops:
- iss: https://cognito-idp.<region>.amazonaws.com/<cognito-pool>
authorities:
- path: $.cognito:groups
prefix: cognito_group_
- iss: https://sts.windows.net/<entra objectid>/
authorities:
- path: $.roles.*
prefix: aad_approle_
- path: $.scp
prefix: aad_scope_
aud: <enterprise application id>
resource-server:
permit-all:
- /api/route/noauth
安全配置
package some.package;
import org.springframework.context.annotation.configuration;
import org.springframework.security.config.annotation.method.configuration.enablemethodsecurity;
import org.springframework.security.config.annotation.web.configuration.enablewebsecurity;
@enablewebsecurity
@enablemethodsecurity
@configuration
public class securityconfig { }
我的控制器现在看起来像这样:
package some.package;
import org.springframework.http.responseentity;
import org.springframework.security.access.prepost.preauthorize;
import org.springframework.security.core.context.securitycontextholder;
import org.springframework.security.oauth2.jwt.jwt;
import org.springframework.web.bind.annotation.getmapping;
import org.springframework.web.bind.annotation.requestmapping;
import org.springframework.web.bind.annotation.restcontroller;
@restcontroller
@requestmapping("/api/route")
public class jwttestcontroller {
@getmapping("/aadauth")
@preauthorize("hasauthority('aad_approle_grantedapprole.xxx')")
public responseentity<string> aadauthrole() {
jwt jwt = (jwt) securitycontextholder.getcontext().getauthentication().getprincipal();
return responseentity.ok(jwt.getclaims().tostring());
}
@getmapping("/aadauth")
@preauthorize("hasauthority('aad_scope_grantedscope.xxx')")
public responseentity<string> aadauthscope() {
jwt jwt = (jwt) securitycontextholder.getcontext().getauthentication().getprincipal();
return responseentity.ok(jwt.getclaims().tostring());
}
@preauthorize("hasauthority('cognito_group_somegroup')")
@getmapping("/cognitoauth")
public responseentity<string> cognitoauth() {
jwt jwt = (jwt) securitycontextholder.getcontext().getauthentication().getprincipal();
return responseentity.ok(jwt.getclaims().tostring());
}
@getmapping("/noauth")
public responseentity<string> noauth() {
return responseentity.ok("hello world!");
}
}
构建.gradle
implementation 'org.springframework.boot:spring-boot-starter-oauth2-resource-server'
implementation 'com.c4-soft.springaddons:spring-addons-starter-oidc:7.3.5'
这不是 spring 的官方启动器,而是 oss 实现:https://www.php.cn/link/49844ba129a1cbc3d964703fcdb756ba
如果我遇到任何其他问题,我会再次更新,但目前它正在工作。
解决方法
我将在这里公开一个使用 my starter 的解决方案,因为它更容易。
如果您更喜欢仅使用“官方”spring boot 启动器构建安全配置,则必须使用 iss 声明提供自己的 authenticationmanagerresolver<httpservletrequest></httpservletrequest>,每个身份验证管理器都有自己的身份验证转换器和自己的权限转换器来处理源声明和您想要的前缀。浏览 my tutorials 或 official documentation 以获取示例和实施提示。 This other answer 也可以提供帮助(权限映射要求完全不同,但身份验证管理器解析器类似)。
使用 boot 3.2.2 和 spring-addons
<?xml version="1.0" encoding="utf-8"?>
<project xmlns="http://maven.apache.org/pom/4.0.0" xmlns:xsi="http://www.w3.org/2001/xmlschema-instance"
xsi:schemalocation="http://maven.apache.org/pom/4.0.0 https://maven.apache.org/xsd/maven-4.0.0.xsd">
<modelversion>4.0.0</modelversion>
<parent>
<groupid>org.springframework.boot</groupid>
<artifactid>spring-boot-starter-parent</artifactid>
<version>3.2.2</version>
<relativepath/> <!-- lookup parent from repository -->
</parent>
<groupid>com.c4-soft.demo</groupid>
<artifactid>multi-tenant-resource-server</artifactid>
<version>0.0.1-snapshot</version>
<properties>
<java.version>21</java.version>
<spring-addons.version>7.3.5</spring-addons.version>
</properties>
<dependencies>
<dependency>
<groupid>org.springframework.boot</groupid>
<artifactid>spring-boot-starter-oauth2-resource-server</artifactid>
</dependency>
<dependency>
<groupid>org.springframework.boot</groupid>
<artifactid>spring-boot-starter-web</artifactid>
</dependency>
<dependency>
<groupid>com.c4-soft.springaddons</groupid>
<artifactid>spring-addons-starter-oidc</artifactid>
<version>${spring-addons.version}</version>
</dependency>
<dependency>
<groupid>com.c4-soft.springaddons</groupid>
<artifactid>spring-addons-starter-oidc-test</artifactid>
<version>${spring-addons.version}</version>
<scope>test</scope>
</dependency>
</dependencies>
<build>
<plugins>
<plugin>
<groupid>org.springframework.boot</groupid>
<artifactid>spring-boot-maven-plugin</artifactid>
</plugin>
</plugins>
</build>
</project>
@configuration
@enablemethodsecurity
public class securityconf {
}
编辑以下 application.yaml 以放置您自己的发行者:
com:
c4-soft:
springaddons:
oidc:
ops:
- iss: https://cognito-idp.us-west-2.amazonaws.com/us-west-2_rzhmglwjl
authorities:
- path: $.cognito:groups
prefix: cognito_group_
- iss: https://sts.windows.net/0a962d63-6b23-4416-81a6-29f88c553998/
authorities:
- path: $.approles.*.displayname
prefix: aad_approle_
- path: $.scope
prefix: aad_scope_
resourceserver:
# spring-addons whitelist is for permitall() (rather than isauthenticated())
# which is probably much safer
permit-all:
- /actuator/health/readiness
- /actuator/health/liveness
- /v3/api-docs/**
- /api/public/**
上面 path 的值是 json 路径。您可以使用 jsonpath.com 等工具根据您自己的令牌有效负载(使用 jwt.io 等工具提取)测试路径表达式。
是的,就这么简单。不,我没有省略任何 yaml 属性或 java 配置(如果您不相信我,只需在新项目中进行测试)。
示例控制器
@restcontroller
public class greetcontroller {
@getmapping("/greet")
@preauthorize("isauthenticated()")
public string getgreet(authentication auth) {
return "hello %s! you are granted with %s.".formatted(auth.getname(), auth.getauthorities());
}
@getmapping(value = "/strings")
@preauthorize("hasanyauthority('aad_approle_admin', 'cognito_group_admin')")
public list<string> getstrings() {
return list.of("protected", "strings");
}
}
示例测试
@webmvctest(controllers = greetcontroller.class)
@autoconfigureaddonswebmvcresourceserversecurity
@import(securityconf.class)
class greetcontrollertest {
@autowired
mockmvcsupport api;
@test
@withanonymoususer
void givenuserisanonymous_whengetgreet_thenunauthorized() throws unsupportedencodingexception, exception {
api.get("/greet").andexpect(status().isunauthorized());
}
@test
@withjwt("aad_admin.json")
void givenuserisaadadmin_whengetgreet_thenok() throws unsupportedencodingexception, exception {
final var actual = api.get("/greet").andexpect(status().isok()).andreturn().getresponse().getcontentasstring();
assertequals(
"hello aad-admin! you are granted with [aad_approle_msiam_access, aad_approle_admin, aad_scope_openid, aad_scope_profile, aad_scope_machin:truc].",
actual);
}
@test
@withjwt("cognito_admin.json")
void givenuseriscognitoadmin_whengetgreet_thenok() throws unsupportedencodingexception, exception {
final var actual = api.get("/greet").andexpect(status().isok()).andreturn().getresponse().getcontentasstring();
assertequals("hello amazon-cognito-admin! you are granted with [cognito_group_admin, cognito_group_machin:truc].", actual);
}
@test
@withjwt("aad_machin-truc.json")
void givenuserisaadmachintruc_whengetgreet_thenok() throws unsupportedencodingexception, exception {
final var actual = api.get("/greet").andexpect(status().isok()).andreturn().getresponse().getcontentasstring();
assertequals("hello aad-user! you are granted with [aad_approle_msiam_access, aad_scope_openid, aad_scope_profile, aad_scope_machin:truc].", actual);
}
@test
@withjwt("cognito_machin-truc.json")
void givenuseriscognitomachintruc_whengetgreet_thenok() throws unsupportedencodingexception, exception {
final var actual = api.get("/greet").andexpect(status().isok()).andreturn().getresponse().getcontentasstring();
assertequals("hello amazon-cognito-user! you are granted with [cognito_group_machin:truc].", actual);
}
@test
@withanonymoususer
void givenuserisanonymous_whengetstrings_thenunauthorized() throws unsupportedencodingexception, exception {
api.get("/strings").andexpect(status().isunauthorized());
}
@test
@withjwt("aad_admin.json")
void givenuserisaadadmin_whengetstrings_thenok() throws unsupportedencodingexception, exception {
final var actual = api.get("/strings").andexpect(status().isok()).andreturn().getresponse().getcontentasstring();
assertequals("[\"protected\",\"strings\"]", actual);
}
@test
@withjwt("cognito_admin.json")
void givenuseriscognitoadmin_whengetstrings_thenok() throws unsupportedencodingexception, exception {
final var actual = api.get("/strings").andexpect(status().isok()).andreturn().getresponse().getcontentasstring();
assertequals("[\"protected\",\"strings\"]", actual);
}
@test
@withjwt("aad_machin-truc.json")
void givenuserisaadmachintruc_whengetstrings_thenforbidden() throws unsupportedencodingexception, exception {
api.get("/strings").andexpect(status().isforbidden());
}
@test
@withjwt("cognito_machin-truc.json")
void givenuseriscognitomachintruc_whengetstrings_thenforbidden() throws unsupportedencodingexception, exception {
api.get("/strings").andexpect(status().isforbidden());
}
}
使用此测试资源:
aad_admin.json
{
"sub": "aad-admin",
"iss": "https://sts.windows.net/0a962d63-6b23-4416-81a6-29f88c553998/",
"approles": [
{
"allowedmembertypes": [
"user"
],
"description": "msiam_access",
"displayname": "msiam_access",
"id": "ef7437e6-4f94-4a0a-a110-a439eb2aa8f7",
"isenabled": true,
"origin": "application",
"value": null
},
{
"allowedmembertypes": [
"user"
],
"description": "administrators only",
"displayname": "admin",
"id": "4f8f8640-f081-492d-97a0-caf24e9bc134",
"isenabled": true,
"origin": "serviceprincipal",
"value": "administrator"
}
],
"scope": "openid profile machin:truc"
}
aad_machin-truc.json
{
"sub": "aad-user",
"iss": "https://sts.windows.net/0a962d63-6b23-4416-81a6-29f88c553998/",
"approles": [
{
"allowedmembertypes": [
"user"
],
"description": "msiam_access",
"displayname": "msiam_access",
"id": "ef7437e6-4f94-4a0a-a110-a439eb2aa8f7",
"isenabled": true,
"origin": "application",
"value": null
}
],
"scope": "openid profile machin:truc"
}
cognito_admin.json
{
"sub": "amazon-cognito-admin",
"iss": "https://cognito-idp.us-west-2.amazonaws.com/us-west-2_rzhmglwjl",
"cognito:groups": ["admin", "machin:truc"],
"scope": "openid profile cog:scope"
}
cognito_machin-truc.json
{
"sub": "amazon-cognito-user",
"iss": "https://cognito-idp.us-west-2.amazonaws.com/us-west-2_RzhmgLwjl",
"cognito:groups": ["machin:truc"],
"scope": "openid profile cog:scope"
}
以上是使用 AAD 和 AWS Cognito 为不同端点保护 Spring Boot REST API的详细内容。更多信息请关注PHP中文网其他相关文章!
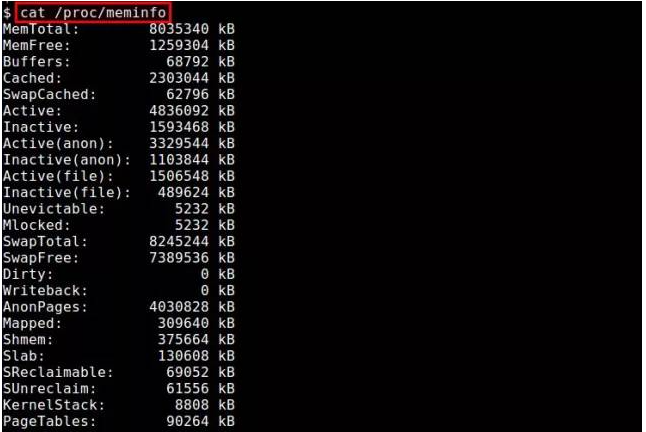 Linux下查看内存使用情况方法总结Feb 05, 2024 am 11:45 AM
Linux下查看内存使用情况方法总结Feb 05, 2024 am 11:45 AMQ:我有一个问题,我想要监视Linux系统的内存使用情况。在Linux下有哪些可用的视图或命令行工具可以使用呢?A:在Linux系统中,有多种方法可以监视内存使用情况。下面是一些通过视图工具或命令行来查看内存使用情况的方法。/proc/meminfo:最简单的方法是查看/proc/meminfo文件。这个虚拟文件会动态更新,并提供了关于内存使用情况的详细信息。它列出了各种内存指标,可以满足你对内存使用情况的大部分需求。另外,你还可以通过/proc//statm和/proc//status来查看进
 揭秘NVIDIA大模型推理框架:TensorRT-LLMFeb 01, 2024 pm 05:24 PM
揭秘NVIDIA大模型推理框架:TensorRT-LLMFeb 01, 2024 pm 05:24 PM一、TensorRT-LLM的产品定位TensorRT-LLM是NVIDIA为大型语言模型(LLM)开发的可扩展推理方案。它基于TensorRT深度学习编译框架构建、编译和执行计算图,并借鉴了FastTransformer中高效的Kernels实现。此外,它还利用NCCL实现设备间的通信。开发者可以根据技术发展和需求差异,定制算子以满足特定需求,例如基于cutlass开发定制的GEMM。TensorRT-LLM是NVIDIA官方推理方案,致力于提供高性能并不断完善其实用性。TensorRT-LL
 Linux 上的最佳白板应用程序Feb 05, 2024 pm 12:48 PM
Linux 上的最佳白板应用程序Feb 05, 2024 pm 12:48 PM“我们将介绍几款适用于Linux系统的白板应用程序,相信这些信息对您会非常有帮助。请继续阅读!”一般来说,数字白板是一种用于大型互动显示面板的工具,常见的设备类型包括平板电脑、大屏手机、触控笔记本和表面显示设备等。当教师使用白板时,您可以使用触控笔、手写笔、手指甚至鼠标在设备屏幕上进行绘画、书写或操作元素。这意味着您可以在白板上拖动、点击、删除和绘画,就像在纸上使用笔一样。然而,要实现这一切,需要有一款软件来支持这些功能,并实现触控和显示之间的精细协调。目前市面上有许多商业应用可以完成这项工作。
 ZR币升值空间大吗? ZR币在哪里购买交易?Feb 01, 2024 pm 08:09 PM
ZR币升值空间大吗? ZR币在哪里购买交易?Feb 01, 2024 pm 08:09 PMZRX(0x)是一个基于以太坊区块链的开放协议,用于实现分布式交易和去中心化交易所(DEX)功能。作为0x协议的原生代币,ZRX可用于支付交易费用、治理协议变更和获取平台优惠。1.ZRX币升值空间展望:从技术角度来看,ZRX作为0x协议的核心代币,在去中心化交易所的应用逐渐增多,市场对其认可度也在增加。以下是几个关键因素,有助于提升ZRX币的价值空间:市场需求潜力大、社区活跃度高、开发者生态繁荣等。这些因素共同促进了ZRX的广泛应用和使用,进而推动了其市场价格的上升。市场需求的增长潜力,意味着更
 BOSS直聘怎么创建多个简历Feb 05, 2024 pm 02:18 PM
BOSS直聘怎么创建多个简历Feb 05, 2024 pm 02:18 PMBOSS直聘怎么创建多个简历?BOSS直聘是很多小伙伴找工作的一大招聘平台,为用户们提供了非常多便利的求职服务。各位在使用BOSS直聘的时候,可以创建多个不同的简历,以便投送到不同的工作岗位上,获取到更高成功率的求职操作,各位如果对此感兴趣的话,就随小编一起来看看BOSS直聘双简历创建教程吧。BOSS直聘怎么创建多个简历1.登录Boss直聘:在您的电脑或手机上,登录您的Boss直聘账户。2.进入简历管理:在Boss直聘首页,点击“简历管理”,进入简历管理页面。3.创建新简历:在简历管理页面,点击
 手把手教你构建linux rootfsFeb 05, 2024 pm 03:51 PM
手把手教你构建linux rootfsFeb 05, 2024 pm 03:51 PMbusybox概述众所周知,在Linux环境下,一切皆文件,文件可以表示一切。而文件系统则是这些普通组件的集合。在嵌入式领域中,常常使用基于busybox构建的rootfs来构建文件系统。busybox诞生至今已有近20年的历史,如今已成为嵌入式行业中主流的rootfs构建工具。busybox的代码是完全开源的。你可以进入官方网站,点击”GetBusyBox”下面的”DownloadSource”进入源码下载界面。“官方网站链接:https://busybox.net/”2.busybox的配置
 Linux字节对齐的那些事Feb 05, 2024 am 11:06 AM
Linux字节对齐的那些事Feb 05, 2024 am 11:06 AM最近,我正在进行一个项目,遇到了一个问题。在ARM上运行的ThreadX与DSP通信时采用了消息队列的方式传递消息(最终实现使用了中断和共享内存的方法)。然而,在实际的操作过程中,发现ThreadX经常崩溃。经过排查,发现问题出在传递消息的结构体没有考虑字节对齐的问题上。我想顺便整理一下关于C语言中字节对齐的问题,并与大家分享。一、概念字节对齐与数据在内存中的位置有关。如果一个变量的内存地址恰好是它长度的整数倍,那么它就被称为自然对齐。例如,在32位CPU下,假设一个整型变量的地址为0x0000
 比 Vim 更现代直观的 Linux 文本编辑器Feb 05, 2024 pm 02:00 PM
比 Vim 更现代直观的 Linux 文本编辑器Feb 05, 2024 pm 02:00 PM如果你厌倦了Vi和Vim的奇怪界面和繁琐的键绑定,为什么不试试Micro编辑器呢?命令行文本编辑器证明了Linux终端的实用性,让您可以在不离开终端的情况下进行文件编辑。这些编辑器使用的资源更少,速度也非常快,非常适合进行一些快速编辑。一些流行的命令行文本编辑器包括Vi、Vim和Nano。它们在大多数Linux发行版中都预装了。然而,对于初学者来说,学习Vi或Vim的曲线和键绑定可能有些困难。这时,Micro文本编辑器就成为了一个更简单的选择。Micro与其他编辑相比的表现如何Micro宣称自己

热AI工具

Undresser.AI Undress
人工智能驱动的应用程序,用于创建逼真的裸体照片

AI Clothes Remover
用于从照片中去除衣服的在线人工智能工具。

Undress AI Tool
免费脱衣服图片

Clothoff.io
AI脱衣机

AI Hentai Generator
免费生成ai无尽的。

热门文章

热工具

螳螂BT
Mantis是一个易于部署的基于Web的缺陷跟踪工具,用于帮助产品缺陷跟踪。它需要PHP、MySQL和一个Web服务器。请查看我们的演示和托管服务。

VSCode Windows 64位 下载
微软推出的免费、功能强大的一款IDE编辑器

Dreamweaver Mac版
视觉化网页开发工具

SublimeText3 英文版
推荐:为Win版本,支持代码提示!

记事本++7.3.1
好用且免费的代码编辑器






