如何設定能限制某個IP某一時段的造訪次數是一個讓人頭痛的問題,特別面對惡意的ddos攻擊的時候。其中CC攻擊(Challenge Collapsar)是DDOS(分散式拒絕服務)的一種,也是一種常見的網站攻擊方法,攻擊者透過代理伺服器或肉雞向受害主機不停地發大量資料包,造成對方伺服器資源耗盡,一直到宕機崩潰。 cc攻擊一般就是使用有限的ip數對伺服器頻繁發送資料來達到攻擊的目的,nginx可以透過HttpLimitReqModul和HttpLimitZoneModule配置來限制ip在同一時間段的訪問次數來防cc攻擊。 HttpLimitReqModul用來限制連單位時間內連接數的模組,使用limit_req_zone和limit_req指令搭配使用來達到限制。一旦並發連接超過指定數量,就會傳回503錯誤。 HttpLimitConnModul用來限制單一ip的並發連接數,使用limit_zone和limit_conn指令這兩個模組的區別前一個是對一段時間內的連接數限制,後者是對同一時刻的連接數限制。
HttpLimitReqModul 限制某一段時間內相同ip存取數實例
<span>http<span>{<span> <span>...<span>
<span>#定义一个名为allips的limit_req_zone用来存储session,大小是10M内存,<span> <span>#以$binary_remote_addr 为key,限制平均每秒的请求为20个,<span> <span>#1M能存储16000个状态,rete的值必须为整数,<span> <span>#如果限制两秒钟一个请求,可以设置成30r/m<span>
limit_req_zone $binary_remote_addr zone<span>=<span>allips<span>:<span>10m<span> rate<span>=<span>20r<span>/<span>s<span>;<span> <span>...<span> server<span>{<span> <span>...<span> location <span>{<span> <span>...<span>
<span>#限制每ip每秒不超过20个请求,漏桶数burst为5<span> <span>#brust的意思就是,如果第1秒、2,3,4秒请求为19个,<span> <span>#第5秒的请求为25个是被允许的。<span> <span>#但是如果你第1秒就25个请求,第2秒超过20的请求返回503错误。<span> <span>#nodelay,如果不设置该选项,严格使用平均速率限制请求数,<span> <span>#第1秒25个请求时,5个请求放到第2秒执行,<span> <span>#设置nodelay,25个请求将在第1秒执行。<span>
limit_req zone<span>=<span>allips burst<span>=<span>5<span> nodelay<span>;<span> <span>...<span> <span>}<span> <span>...<span> <span>}<span> <span>...<span><span>}</span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span>
HttpLimitZoneModule 限制並發連接數個實例可以在連接數位作用域
<span>http<span>{<span> <span>...<span>
<span>#定义一个名为one的limit_zone,大小10M内存来存储session,<span> <span>#以$binary_remote_addr 为key<span> <span>#nginx 1.18以后用limit_conn_zone替换了limit_conn<span> <span>#且只能放在http作用域<span> limit_conn_zone one $binary_remote_addr <span>10m<span>;<span>
<span>...<span> server<span>{<span> <span>...<span> location <span>{<span> <span>...<span> limit_conn one <span>20<span>;<span> <span>#连接数限制<span>
<span>#带宽限制,对单个连接限数,如果一个ip两个连接,就是500x2k<span> limit_rate <span>500k<span>;<span>
<span>...<span> <span>}<span> <span>...<span> <span>}<span> <span>...<span><span>}</span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span> nginx白名單設定
以上配置會對所有的ip都進行限制,有些時候我們不希望對搜尋引擎的蜘蛛或自己測試ip進行限制,對於特定的白名單ip我們可以藉助geo指令實現。
1.<span>http<span>{<span> geo $limited<span>{<span> <span>default<span> <span>1<span>;<span> <span>#google <span> <span>64.233<span>.<span>160.0<span>/<span>19<span> <span>0<span>;<span> <span>65.52<span>.<span>0.0<span>/<span>14<span> <span>0<span>;<span> <span>66.102<span>.<span>0.0<span>/<span>20<span> <span>0<span>;<span> <span>66.249<span>.<span>64.0<span>/<span>19<span> <span>0<span>;<span> <span>72.14<span>.<span>192.0<span>/<span>18<span> <span>0<span>;<span> <span>74.125<span>.<span>0.0<span>/<span>16<span> <span>0<span>;<span> <span>209.85<span>.<span>128.0<span>/<span>17<span> <span>0<span>;<span> <span>216.239<span>.<span>32.0<span>/<span>19<span> <span>0<span>;<span> <span>#M$<span> <span>64.4<span>.<span>0.0<span>/<span>18<span> <span>0<span>;<span> <span>157.60<span>.<span>0.0<span>/<span>16<span> <span>0<span>;<span> <span>157.54<span>.<span>0.0<span>/<span>15<span> <span>0<span>;<span> <span>157.56<span>.<span>0.0<span>/<span>14<span> <span>0<span>;<span> <span>207.46<span>.<span>0.0<span>/<span>16<span> <span>0<span>;<span> <span>207.68<span>.<span>192.0<span>/<span>20<span> <span>0<span>;<span> <span>207.68<span>.<span>128.0<span>/<span>18<span> <span>0<span>;<span> <span>#yahoo<span> <span>8.12<span>.<span>144.0<span>/<span>24<span> <span>0<span>;<span> <span>66.196<span>.<span>64.0<span>/<span>18<span> <span>0<span>;<span> <span>66.228<span>.<span>160.0<span>/<span>19<span> <span>0<span>;<span> <span>67.195<span>.<span>0.0<span>/<span>16<span> <span>0<span>;<span> <span>74.6<span>.<span>0.0<span>/<span>16<span> <span>0<span>;<span> <span>68.142<span>.<span>192.0<span>/<span>18<span> <span>0<span>;<span> <span>72.30<span>.<span>0.0<span>/<span>16<span> <span>0<span>;<span> <span>209.191<span>.<span>64.0<span>/<span>18<span> <span>0<span>;<span> <span>#My IPs<span> <span>127.0<span>.<span>0.1<span>/<span>32<span> <span>0<span>;<span> <span>123.456<span>.<span>0.0<span>/<span>28<span> <span>0<span>;<span> <span>#example for your server CIDR<span> <span>}</span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span>
geo指令定義了一個白名單$limited變量,預設值為1,如果客戶端ip在上面的範圍內,$limited的值為0
2.使用map ip為空串,如果不是搜尋引擎就顯示本身真是的ip,這樣搜尋引擎ip就不能存到limit_req_zone記憶體session中,所以不會限制搜尋引擎的ip存取map $limited $limit {
1 $binary_remote_addr ;
0 "";}
3.設定limit_req_zone和limit_req
limit_req_zone $limit z rate=10r/m;
limit_req z burst=5;=10r/m;
首先我們準備一個php腳本放在根目錄下$document_root
test. php
nginx配置增加
limit_req_zone
limit_req
<span>http<span>{<span> <span>...<span> limit_req_zone $binary_remote_addr zone<span>=<span>allips<span>:<span>10m<span> rate<span>=<span>60r<span>/<span>m<span>;<span> <span>...<span> server<span>{<span> <span>...<span> location <span>{<span> <span>...<span> limit_req zone<span>=<span>allips<span>;<span> <span>...<span> <span>}<span> <span>...<span> <span>}<span> <span>...<span><span>}</span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span>
ab -n 5 -c 1 http://www.weizhang.org/test.ab -n 5 -c 1 http://www.weizhang.org/test.ab -n 5 -c 1 http://www.weizhang.org/test.ab -n 5 -c 1 http://www.weizhang.org/test.
ab -n 5 -c 1 http://www.weizhang.org/test. 06:27:06 +0000] "GET /test.php HTTP/1.0" 200 11000 "-" "ApacheBench/2.3"
118.144.94.193 - - [22/Dec/2012:06:27:06 +0000] GET /test.php HTTP/1.0" 503 537 "-" "ApacheBench/2.3"
118.144.94.193 - - [22/Dec/2012:06:27:07 +0000] "GET /test. HTTP/1. 503 537 "-" "ApacheBench/2.3"
118.144.94.193 - - [22/Dec/2012:06:27:07 +0000] "GET /test.php HTTP/1.0" 503 537 "
118.144.94.193 - - [22/Dec/2012:06:27:07 +0000] "GET /test.php HTTP/1.0" 503 537 "-" "ApacheBench/2.3"
<span>http<span>{<span> <span>...<span> limit_req_zone $binary_remote_addr zone<span>=<span>allips<span>:<span>10m<span> rate<span>=<span>60r<span>/<span>m<span>;<span> <span>...<span> server<span>{<span> <span>...<span> location <span>{<span> <span>...<span> limit_req zone<span>=<span>allips burst<span>=<span>1<span> nodelay<span>;<span> <span>...<span> <span>}<span> <span>...<span> <span>}<span> <span>...<span><span>}</span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span></span>ab -n 5 -c 1 http://www.weizhang.org/test.php118.144.94.193 - - [22 /Dec/2012:07:01:00 +0000] "GET /test.php HTTP/1.0" 200 11000 "-" "ApacheBench/2.3"118.144.94.193 - - [22/Dec/2012:011: 00 +0000] "GET /test.php HTTP/1.0" 200 11000 "-" "ApacheBench/2.3"
118.144.94.193 - - [22/Dec/2012:07:01:01 +0000] php HTTP/1.0" 503 537 "-" "ApacheBench/2.3"
118.144.94.193 - - [22/Dec/2012:07:01:01 +0000] "GET /test.php HTTP/1.0" 503 537 "- " "ApacheBench/2.3"
118.144.94.193 - - [22/Dec/2012:07:01:01 +0000] "GET /test.php HTTP/1.0" 503 537 "-" "ApacheB/test.php HTTP/1.0" 503 537 "-" "ApacheB/test.php HTTP/1.0" 503 537 "-" "ApacheB/233". brust=1和nodelay後允許第1秒處理兩個請求。
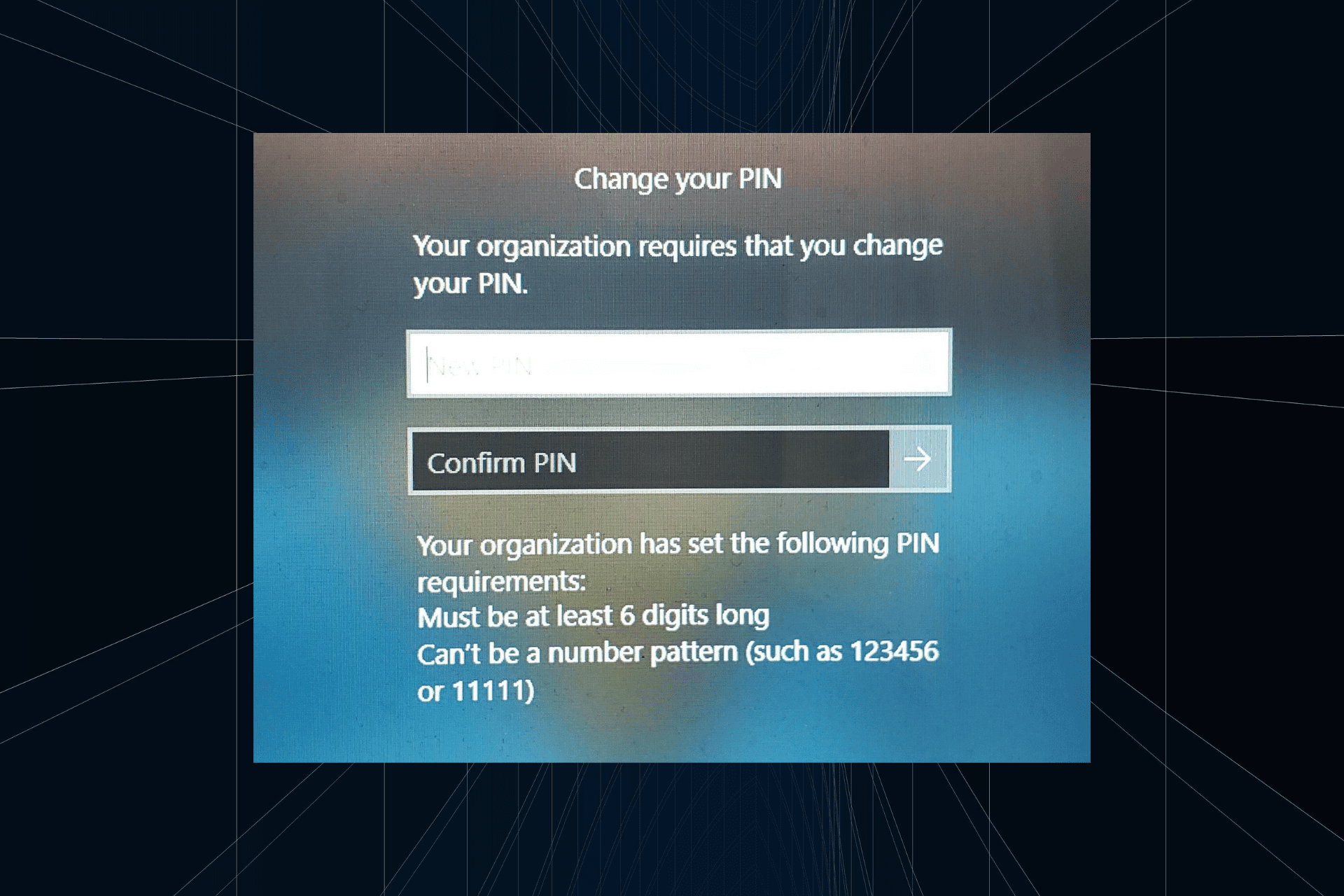 解决方法:您的组织要求您更改 PIN 码Oct 04, 2023 pm 05:45 PM
解决方法:您的组织要求您更改 PIN 码Oct 04, 2023 pm 05:45 PM“你的组织要求你更改PIN消息”将显示在登录屏幕上。当在使用基于组织的帐户设置的电脑上达到PIN过期限制时,就会发生这种情况,在该电脑上,他们可以控制个人设备。但是,如果您使用个人帐户设置了Windows,则理想情况下不应显示错误消息。虽然情况并非总是如此。大多数遇到错误的用户使用个人帐户报告。为什么我的组织要求我在Windows11上更改我的PIN?可能是您的帐户与组织相关联,您的主要方法应该是验证这一点。联系域管理员会有所帮助!此外,配置错误的本地策略设置或不正确的注册表项也可能导致错误。即
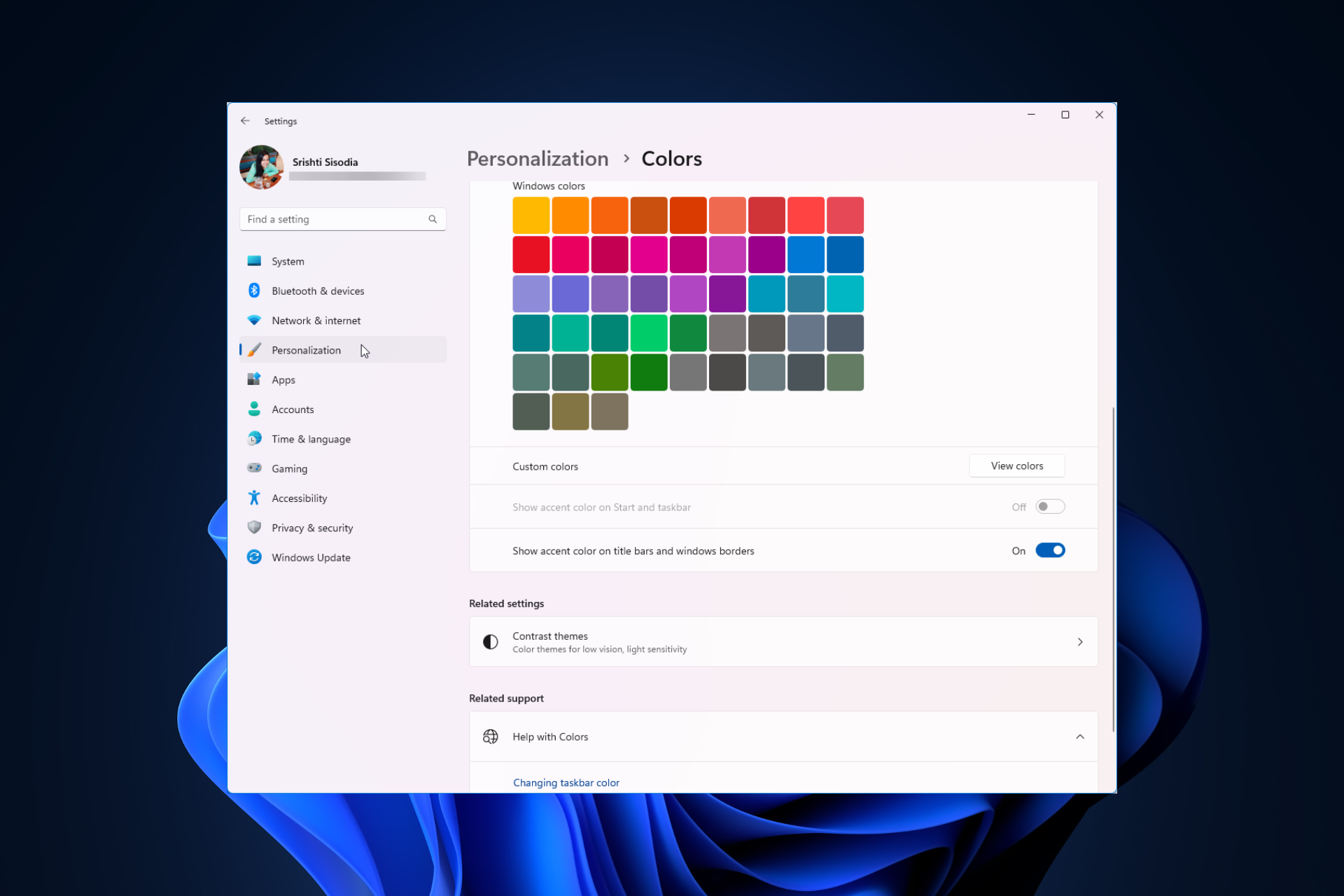 Windows 11 上调整窗口边框设置的方法:更改颜色和大小Sep 22, 2023 am 11:37 AM
Windows 11 上调整窗口边框设置的方法:更改颜色和大小Sep 22, 2023 am 11:37 AMWindows11将清新优雅的设计带到了最前沿;现代界面允许您个性化和更改最精细的细节,例如窗口边框。在本指南中,我们将讨论分步说明,以帮助您在Windows操作系统中创建反映您的风格的环境。如何更改窗口边框设置?按+打开“设置”应用。WindowsI转到个性化,然后单击颜色设置。颜色更改窗口边框设置窗口11“宽度=”643“高度=”500“>找到在标题栏和窗口边框上显示强调色选项,然后切换它旁边的开关。若要在“开始”菜单和任务栏上显示主题色,请打开“在开始”菜单和任务栏上显示主题
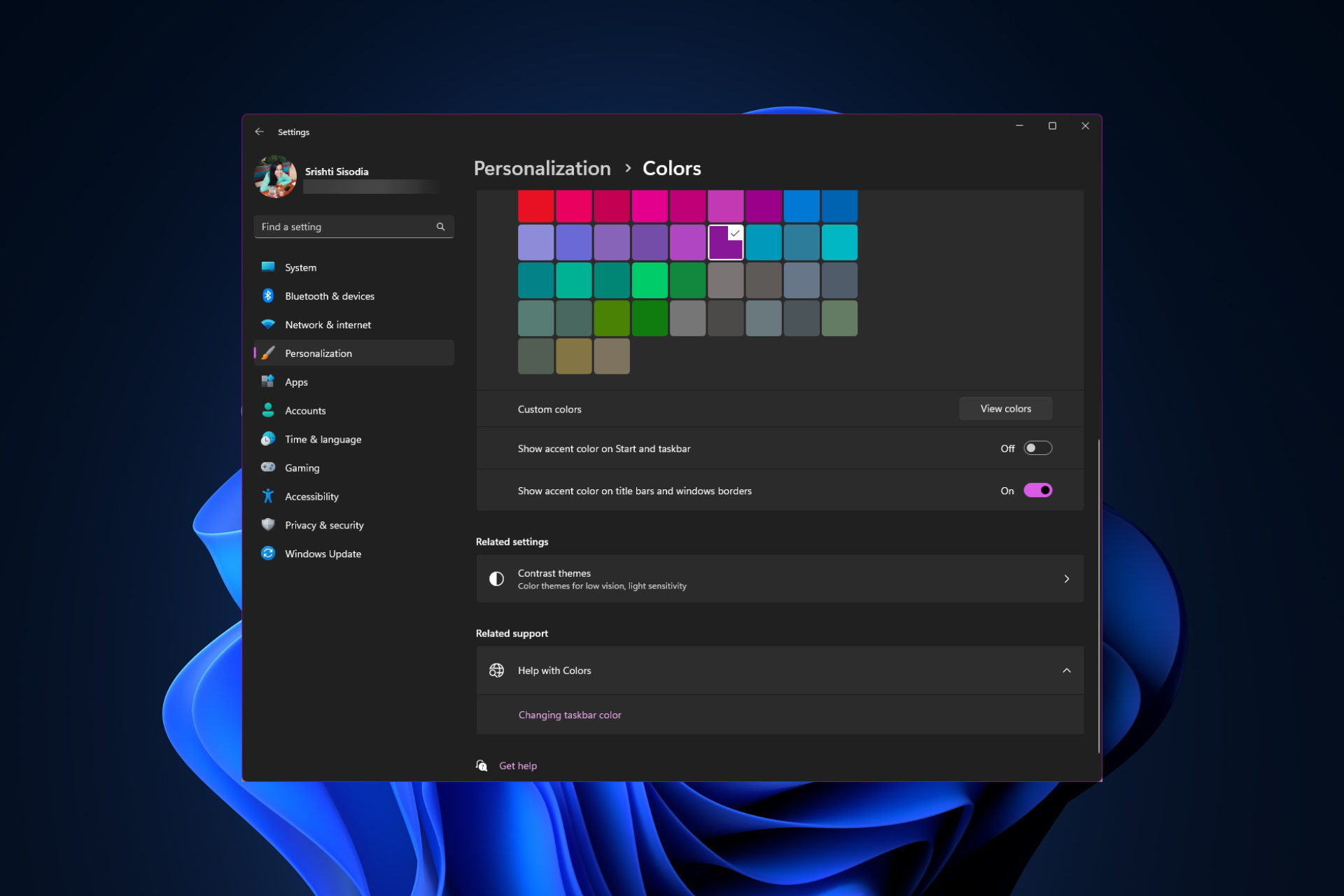 如何在 Windows 11 上更改标题栏颜色?Sep 14, 2023 pm 03:33 PM
如何在 Windows 11 上更改标题栏颜色?Sep 14, 2023 pm 03:33 PM默认情况下,Windows11上的标题栏颜色取决于您选择的深色/浅色主题。但是,您可以将其更改为所需的任何颜色。在本指南中,我们将讨论三种方法的分步说明,以更改它并个性化您的桌面体验,使其具有视觉吸引力。是否可以更改活动和非活动窗口的标题栏颜色?是的,您可以使用“设置”应用更改活动窗口的标题栏颜色,也可以使用注册表编辑器更改非活动窗口的标题栏颜色。若要了解这些步骤,请转到下一部分。如何在Windows11中更改标题栏的颜色?1.使用“设置”应用按+打开设置窗口。WindowsI前往“个性化”,然
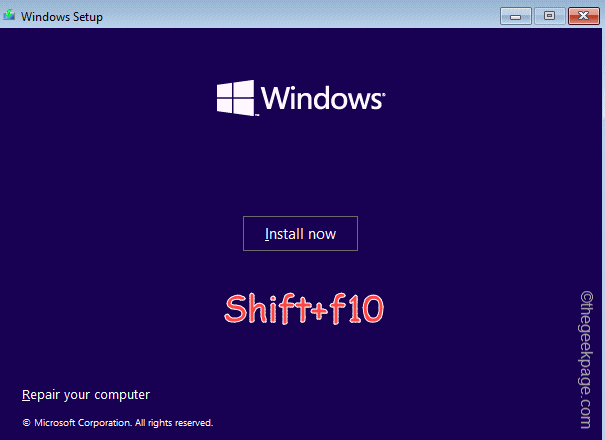 OOBELANGUAGE错误Windows 11 / 10修复中出现问题的问题Jul 16, 2023 pm 03:29 PM
OOBELANGUAGE错误Windows 11 / 10修复中出现问题的问题Jul 16, 2023 pm 03:29 PM您是否在Windows安装程序页面上看到“出现问题”以及“OOBELANGUAGE”语句?Windows的安装有时会因此类错误而停止。OOBE表示开箱即用的体验。正如错误提示所表示的那样,这是与OOBE语言选择相关的问题。没有什么可担心的,你可以通过OOBE屏幕本身的漂亮注册表编辑来解决这个问题。快速修复–1.单击OOBE应用底部的“重试”按钮。这将继续进行该过程,而不会再打嗝。2.使用电源按钮强制关闭系统。系统重新启动后,OOBE应继续。3.断开系统与互联网的连接。在脱机模式下完成OOBE的所
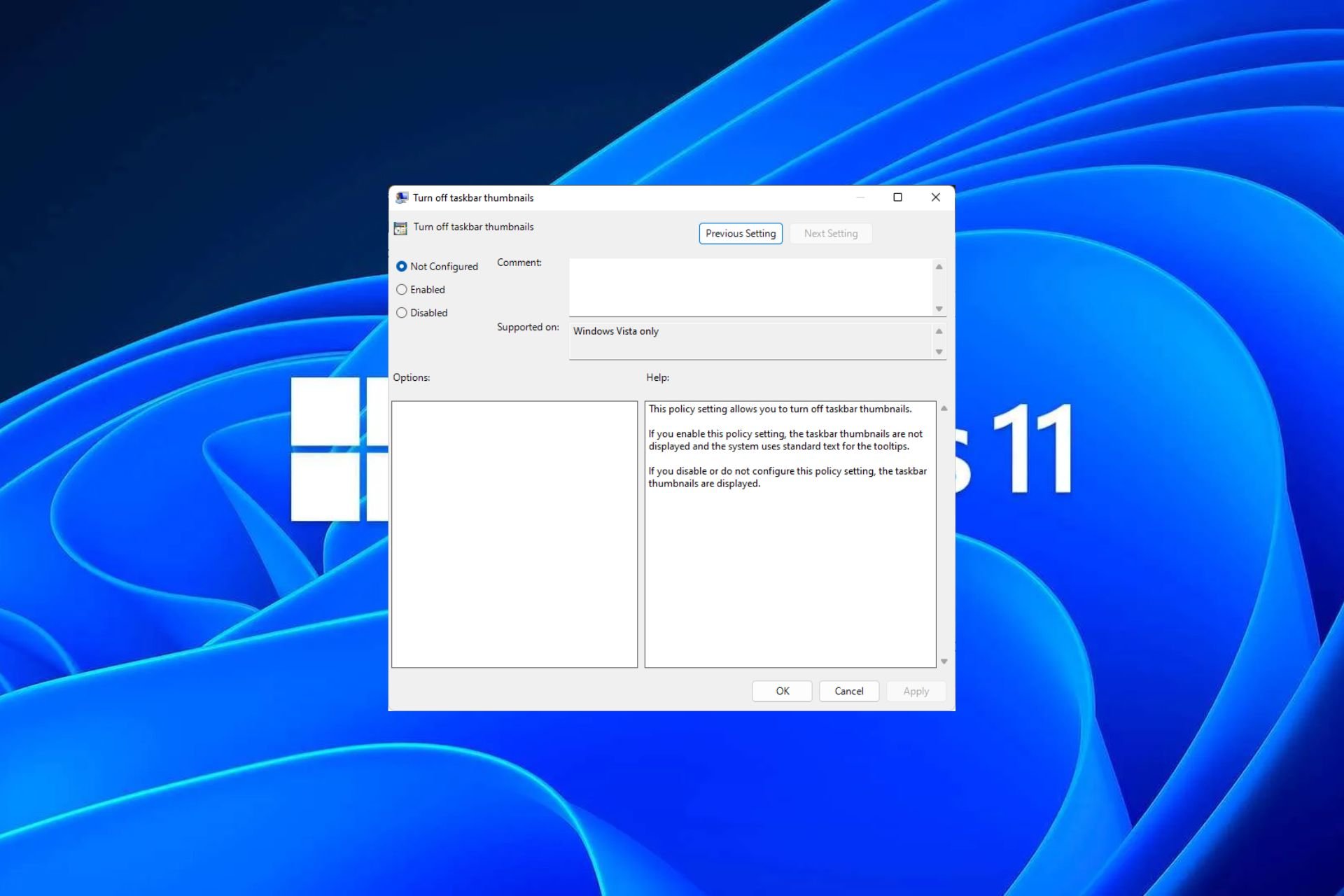 Windows 11 上启用或禁用任务栏缩略图预览的方法Sep 15, 2023 pm 03:57 PM
Windows 11 上启用或禁用任务栏缩略图预览的方法Sep 15, 2023 pm 03:57 PM任务栏缩略图可能很有趣,但它们也可能分散注意力或烦人。考虑到您将鼠标悬停在该区域的频率,您可能无意中关闭了重要窗口几次。另一个缺点是它使用更多的系统资源,因此,如果您一直在寻找一种提高资源效率的方法,我们将向您展示如何禁用它。不过,如果您的硬件规格可以处理它并且您喜欢预览版,则可以启用它。如何在Windows11中启用任务栏缩略图预览?1.使用“设置”应用点击键并单击设置。Windows单击系统,然后选择关于。点击高级系统设置。导航到“高级”选项卡,然后选择“性能”下的“设置”。在“视觉效果”选
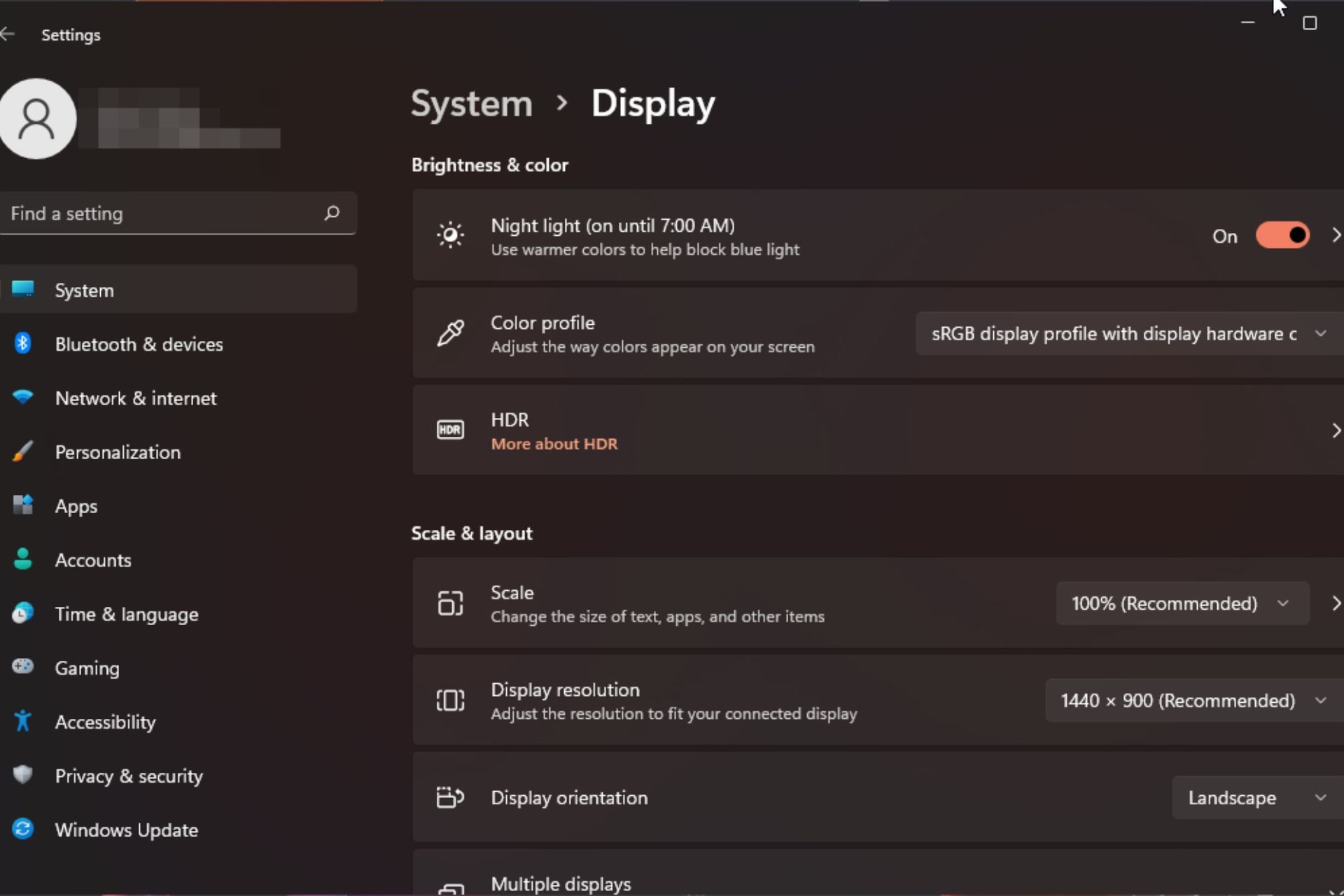 Windows 11 上的显示缩放比例调整指南Sep 19, 2023 pm 06:45 PM
Windows 11 上的显示缩放比例调整指南Sep 19, 2023 pm 06:45 PM在Windows11上的显示缩放方面,我们都有不同的偏好。有些人喜欢大图标,有些人喜欢小图标。但是,我们都同意拥有正确的缩放比例很重要。字体缩放不良或图像过度缩放可能是工作时真正的生产力杀手,因此您需要知道如何对其进行自定义以充分利用系统功能。自定义缩放的优点:对于难以阅读屏幕上的文本的人来说,这是一个有用的功能。它可以帮助您一次在屏幕上查看更多内容。您可以创建仅适用于某些监视器和应用程序的自定义扩展配置文件。可以帮助提高低端硬件的性能。它使您可以更好地控制屏幕上的内容。如何在Windows11
 10种在 Windows 11 上调整亮度的方法Dec 18, 2023 pm 02:21 PM
10种在 Windows 11 上调整亮度的方法Dec 18, 2023 pm 02:21 PM屏幕亮度是使用现代计算设备不可或缺的一部分,尤其是当您长时间注视屏幕时。它可以帮助您减轻眼睛疲劳,提高易读性,并轻松有效地查看内容。但是,根据您的设置,有时很难管理亮度,尤其是在具有新UI更改的Windows11上。如果您在调整亮度时遇到问题,以下是在Windows11上管理亮度的所有方法。如何在Windows11上更改亮度[10种方式解释]单显示器用户可以使用以下方法在Windows11上调整亮度。这包括使用单个显示器的台式机系统以及笔记本电脑。让我们开始吧。方法1:使用操作中心操作中心是访问
 如何修复Windows服务器中的激活错误代码0xc004f069Jul 22, 2023 am 09:49 AM
如何修复Windows服务器中的激活错误代码0xc004f069Jul 22, 2023 am 09:49 AMWindows上的激活过程有时会突然转向显示包含此错误代码0xc004f069的错误消息。虽然激活过程已经联机,但一些运行WindowsServer的旧系统可能会遇到此问题。通过这些初步检查,如果这些检查不能帮助您激活系统,请跳转到主要解决方案以解决问题。解决方法–关闭错误消息和激活窗口。然后,重新启动计算机。再次从头开始重试Windows激活过程。修复1–从终端激活从cmd终端激活WindowsServerEdition系统。阶段–1检查Windows服务器版本您必须检查您使用的是哪种类型的W


熱AI工具

Undresser.AI Undress
人工智慧驅動的應用程序,用於創建逼真的裸體照片

AI Clothes Remover
用於從照片中去除衣服的線上人工智慧工具。

Undress AI Tool
免費脫衣圖片

Clothoff.io
AI脫衣器

AI Hentai Generator
免費產生 AI 無盡。

熱門文章

熱工具

SublimeText3 英文版
推薦:為Win版本,支援程式碼提示!

禪工作室 13.0.1
強大的PHP整合開發環境

Atom編輯器mac版下載
最受歡迎的的開源編輯器

MinGW - Minimalist GNU for Windows
這個專案正在遷移到osdn.net/projects/mingw的過程中,你可以繼續在那裡關注我們。 MinGW:GNU編譯器集合(GCC)的本機Windows移植版本,可自由分發的導入函式庫和用於建置本機Windows應用程式的頭檔;包括對MSVC執行時間的擴展,以支援C99功能。 MinGW的所有軟體都可以在64位元Windows平台上運作。

Dreamweaver Mac版
視覺化網頁開發工具





