我的repo 分别推送到github,gitcafe。 正确添加了两个公钥私钥之后,并命名为id_github和id_gitcafe,发现每次push 代码 都必须重新ssh-add 上私钥。将id_github 名改回默认的id_rsa,就可以直接push了。但是gitcafe 被拒绝。有没有办法可以一次都设置上,不需要每次 ssh-add 私钥的。
淡淡烟草味2017-04-28 09:06:12
First of all, I have to say that all the mechanisms related to ssh are indeed relatively complicated and can easily make people confused. If you want to completely master this knowledge system, you must systematically learn the relevant knowledge. So first thing first, I recommend a book to you, you might as well take the time to read it once and for all:
SSH, The Secure Shell, the first edition of this book is in Chinese.
Let’s talk about your specific question.
You must understand one thing first: ssh-add This command is not used to permanently remember the private key you use. In fact, its function is just to add the private key you specify to a session managed by ssh-agent. And ssh-agent is a temporary session service used to store private keys, which means that when you restart, the ssh-agent service will be reset.
If it is to permanently remember the corresponding private key, we cannot rely on the ssh-agent service. What you can rely on depends on which of the following options are suitable for your use case.
You didn’t describe the operating system you’re using in your question, so I’ll use the Mac OS X I use daily as an example. The Mac system has a built-in Keychain service and its management program, which can easily help you manage various keys, including ssh keys. ssh-add will add the specified secret key to the currently running ssh-agent service by default, but you can change this default behavior to add it to the keychain service and let Mac remember and manage it for you. And ensure the security of these secret keys.
All you have to do is execute the following command:
$ ssh-add -K [path/to/your/ssh-key]
Afterwards, when other programs request ssh keys, they will request them through the Keychain service. In the screenshot below you can see the ssh keys managed by Keychain on my current machine, including four generated by myself and one used by the Github Client App - the former are all for Used by ssh-related commands, and the latter specifies that it is only used by the application Github.app. In addition, they are all login keychains, which means they will only take effect after the current user logs in. They cannot be used if the user is changed or the user is not logged in. This is what the Keychain service does for you.
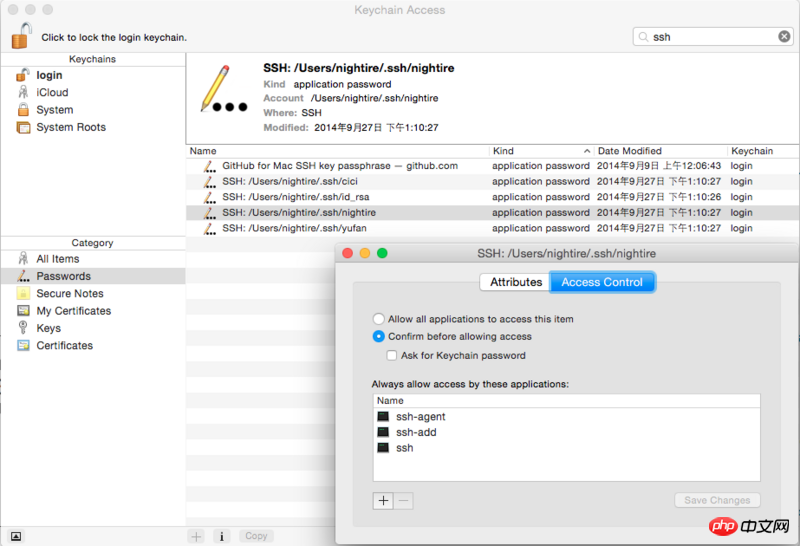
This problem is something I haven’t fully understood yet. According to some information, after doing the above work, the application should be able to automatically match the applicable ssh key. But in the process of my study, I also encountered situations where I had to manually specify it (I didn’t understand the role of Keychain at that time, so I always manually ssh-add), so another mechanism can help you solve this problem. , namely ssh config.
In a nutshell, ssh config is a configuration file that describes the settings corresponding to different keys - including host name, user name, access policy, etc.
Below I have captured two snippets of the local configuration:
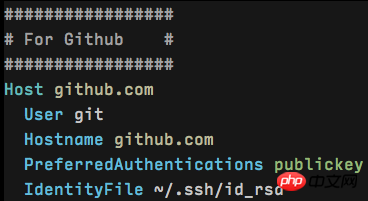
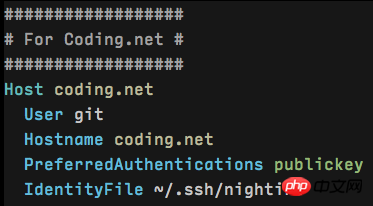
These two configurations correspond to the secret keys used by Github and Coding services respectively. The Host in the first line is just a name, and the Hostname in the third line is the corresponding real address, but it is best to keep the two consistent so that you don’t have to convert them in your head.
With this configuration, when I git clone https://github.com/user/repo 的时候,id_rsa 秘钥会被使用,当我 git clone https://coding.net/user/repo 的时候,很显然 nightire the secret key will be used.
Of course, this configuration is not limited to Git. All underlying applications and commands that use SSH will follow the instructions in the configuration file to find the corresponding private key.
Back to the topic at the beginning of this section, I believe that with Keychain for management, this configuration file should not be needed, but I haven’t had a chance to test it yet. Everything is fine in the current environment. I will give it a try when I change to a new machine and reconfigure the environment.
Regarding the corresponding relationship between Host and Hostname, if Hostname is a domain name, it is best to keep it consistent. But here are two tips:
1. What if there are two different configurations under the same domain name?
Taking Github as an example, if I have two accounts, one personal and one organizational, and I want to use different keys, then I can write like this:
The Host here corresponds to the two user names of Github, namely github.com/nightire and github.com/very-geek
2. If the domain name is a digital IP, can it be simplified?
Host can help you turn the corresponding IP into an easy-to-remember name. For example, if I configure Git Server (based on gitolite or Gitlab or any tool) within the company, the normal access address is:git://xxx.xxx.xxx.xxx:repo.git,如下的配置则可以帮你把它简化成:git.visionet:repo.git
very useful.
Yes. If ssh-add already meets your requirements (except having to do it again after startup), then you can completely automate this with a script. Simply write the contents of the ssh-add command you entered into .bashrc 或 .bash_profile (or any other shell environment configuration file you use), so that whenever you open the terminal, it will automatically do this.
But as I said before, this mechanism relies on the ssh-agent service and is only valid under the terminal. If the Keychain mechanism is used, it is valid throughout the system (including applications that do not rely on the terminal) and there is no need to open the ssh-agent service.
Lastly, the Keychain service is not only available on Mac. I just searched and found that Windows and various Linux have corresponding mechanisms, but I have never used them, so I can only use Mac as an example. Once you understand these concepts, I believe you can find the specific methods yourself.
巴扎黑2017-04-28 09:06:12
A small addition to the accepted answer
You can learn how to add it to the current session from the github article:ssh-add This command is not used to permanently remember the private key you use. In fact, its function is just to add the private key you specify to a
session managed by ssh-agent. And ssh-agent is a temporary session service used to store private keys, which means that when you restart, the ssh-agent service will be reset.
Generating a new SSH key and adding it to the ssh-agent
Error: Permission denied (publickey)
/Users/you/.ssh/config
伊谢尔伦2017-04-28 09:06:12
I simply use the same account and password github.com coding.net. This can be used.