Using libpcap to capture packets under ubuntu14.04, I want to get a piece of html transmitted using http, but the results obtained are inconsistent with the data obtained by wireshark under the same situation.
The current code is as follows:
#include <pcap.h>
#include <time.h>
#include <stdlib.h>
#include <stdio.h>
#include <linux/if_ether.h>
#include <linux/ip.h>
#include <linux/tcp.h>
#include <string.h>
#include <netinet/in.h>
void getPacket(u_char * arg, const struct pcap_pkthdr * pkthdr, const u_char * packet)
{
bpf_u_int32 caplen = pkthdr->caplen;
bpf_u_int32 len = pkthdr->len;
int * id = (int *)arg;
struct iphdr *ip_header = (struct iphdr *)(packet + ETH_HLEN);
struct tcphdr *tcp_header = (struct tcphdr *)(packet + ETH_HLEN + sizeof(struct iphdr));
const u_char *tcp_data = packet + ETH_HLEN + sizeof(struct iphdr) + sizeof(struct tcphdr);
printf("%s\n\n", tcp_data);
}
int main()
{
char errBuf[PCAP_ERRBUF_SIZE];
pcap_t * device = pcap_open_live("wlan0", 65535, 1, 0, errBuf);
if(!device)
{
printf("错误: pcap_open_live(): %s\n", errBuf);
exit(1);
}
struct bpf_program filter;
pcap_compile(device, &filter, "tcp port 80 and host 123.206.7.47", 1, 0);
pcap_setfilter(device, &filter);
int id = 0;
pcap_loop(device, -1, getPacket, (u_char*)&id);
pcap_close(device);
return 0;
}The server has a simple html. When I use the browser to access the server http://123.206.7.47/test.html, wireshark (same as bpf) captures 10 packets like this:
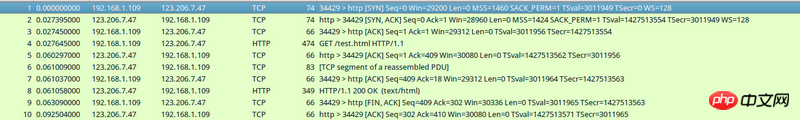
What I see when using the debugger on my program is like this. This picture corresponds to the fourth data packet (size 474) in the picture above:
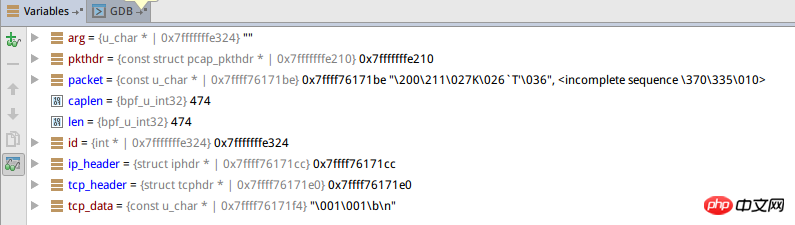
Why does unsigned char * packet appear incomplete sequence? And why is tcp_data so short?
Is there any missing configuration of libpcap in my code or is it due to other reasons?
One more thing to add is that when I visit other websites, I can occasionally capture the complete HTTP request, but not on the web page I visited.
为情所困2017-05-16 13:26:16
Already solved. Just press caplen to read char, printf("%s")输出不全似乎是因为某个二进制数据是� will be truncated.