Documentation description
Business Agreement
Three-party application access can only use the account system provided by Alibaba for login and authorization, and independent account registration functions cannot be provided .
Communication Convention
The payment server supports two communication modes, namely http (https) mode and TOP mode .
Https communication method: suitable for digital entertainment server callback after successful payment. Use https communication method and use RSA public and private key encryption and decryption. In this CP method, you need to first fill in the developer's RSA public key information on the Digital Entertainment TV Open Platform (http://open.aliplay.com/). Digital Entertainment uses the public key filled in by CP to sign. After CP's server receives the callback, it uses the private key to decrypt the signature. The original content of the callback is in json format. For specific field definitions, please refer to Network Payment Interface-Server Payment Callback notification chapter after success. The content encryptedData based on the original content json string and the RSA public key will be used by the CP in the data field of the http parameter after decryption using the RSA private key
TOP communication method: suitable for CP Scenarios for actively calling payment services (such as querying order status, etc.) Through the TOP communication method, in this method the CP needs to use the appkey and appsecret issued by the Digital Entertainment TV Open Platform (http://open.aliplay.com/) when checking in (this information It can be viewed in the Alibaba TV open platform application management page). For the call of the TOP interface, please refer to //open.taobao.com/doc2/detail.htm? spm=a219a.7629140.0.0.jlQptD&treeId=49&articleId=101617&docType=1
Security Specifications
In order to prevent unnecessary security risks caused by the abuse of the interface (server) agreed by both parties, access Partners need to comply with the following requirements and conduct security controls. If you have any questions, you can join the Wangwang group 621730614 for consultation.
1. Interface security specifications
1) The interface is open in HTTP mode.
2) The design interface needs to have identity authentication, authorize the source, and only allow authorized IP access.
3) All interface calls need to be logged to record the transfer and storage of the key. The agreed upon key should not be delivered by email on a large scale, but should be delivered from developer to developer. The key needs to be kept properly to avoid security risks caused by leaking the key.
2 Transmission and storage of keys and appsecret
Sensitive information held by access partners should not be transmitted on a large scale by email, and should be addressed to developers. Passed to people. The private key and appsecret need to be kept properly to avoid security risks caused by leaking the private key.
Technical Example
1. RSA key generation method
RSA is an asymmetric algorithm that can be used for signatures, that is, the signature key (private key) and the verification key (public key) are different. The private key is used for signatures and the public key is used for verification. . Signatures using this algorithm can not only prevent data tampering, but also prevent repudiation, because the private key is known only to the signer. You can use the Openssl RSA key generation tool to generate a set of RSA public and private keys.
RSA key generation command:
Generate RSA private key
openssl genrsa -out rsa_private_key.pem 1024
Generate RSA public key
openssl rsa -in rsa_private_key.pem -pubout -out rsa_public_key.pem
Convert RSA private key to PKCS8 format
openssl pkcs8 -topk8 -inform PEM -in rsa_private_key.pem -outform PEM -nocrypt
The key file generated by this tool contains some comments and carriage returns and line feeds, which need to be removed to form a string of characters!
2. RSA signature (sign) algorithm Example
Java Reference Code
/**
* RSA signature algorithm
* @param privateKey
* @param content
* @param charset
* @return
* @throws Exception
*/
public static String sign(String privateKey, String content, String charset) throws Exception {
PKCS8EncodedKeySpec priPKCS8 = new PKCS8EncodedKeySpec ( Base64.decodeBase64(privateKey) );
KeyFactory keyf = KeyFactory.getInstance("RSA");
PrivateKey priKey = keyf. generatePrivate(priPKCS8);
.initSign(priKey);
signature.update(content.getBytes(charset) );
byte[] signed = signature.sign();
return
Base64.encodeBase64String(signed);
}
PHP Reference Code
$privkey = file_get_contents("rsa_private_key.pem"); //
No need to convert to PKCS8$res = openssl_get_privatekey($privkey);
$sign = base64_encode ($sign);
3. Server-side notify decryption demo (java version)
package testRsa;import java.io.ByteArrayInputStream;
import java.io.ByteArrayOutputStream;
import java.io.InputStream;
import java.io.UnsupportedEncodingException;
import java.security.InvalidKeyException;
import java.security.KeyFactory;
import java.security. NoSuchAlgorithmException;
import java.security.PrivateKey;
import java.security.SignatureException;
import java.security.spec.InvalidKeySpecException;
import java.security.spec.PKCS8EncodedKeySpec;
import javax.crypto.Cipher;
import org.apache.commons.codec.binary.Base64;
/**
*
* @author zhiyong.xiongzy
*
*/
public class testRSA {
private static String prikey = "MIICdwIBADANBgkqhkiG9w0BAQEFAASCAmEwggJdAgEAAoGBAMhDP5oVLHPJpM0QDuAGPupAkF4N3bMOD252BIYncKd8ppYJP0sA1wxnJxrVJN6UOzgK2qEReHUCzda5Hj GaR8dmYz3v4UMozNeXhx7iqI7EK4Myp/qjCV2ROgh2LaL1ycugacTVx6dSfFvIOcczyhs8D4BUiJlSMsTWPVCSKsPAgMBAAECgYEAkL5KUgvLvUSZIL3ignkBMD7KGbDb9HbNIIGcc3o KlAl93tni8ZnqEdGNFap91YcFz2BF7mQ3sHQFMpn2nJDtzj0tPsCKtNLHmpOi0ctAxedhzip rOT6obNK POL6czMWGJOaW8zLefxftgZWkT eZactn507xc GiwNsodAMECQQD4OjjnMhQWaSv8kHI27pH92PTv4zFb1msB0H65Im2zQ 8JrlqEH/7AqqMIxkPjIMC/vJLpkZG4TYMCYXjd4rx7AkEAzoiLGwUsXDApbDJJxxgYV6y50H/oJm6ooIOHoCwrluJhlOD81oUQyrLGfgNL95v4avvuQezZ4kmkeWDPvQ35fQJACBM8zqieZqw9NhYs4QSZ0zw/m540eNxc1s5FkRhBoVdQa2w0nZ 81d 3Ng3dH4JtQs Lp/WIXAqJfIZXPECoCQJAW8QBgrTuu9tOXFuPul1zW2lMel6KiKD8Xa1zUnCtwXG h8bbsHkZN btGMpgM5libC6Z80LIoKm14ZRpWQffhQJBAJyxWEnzZA9dvqEhj6I/BTPJgvzc/boGzZ2lKQlN8j57MDkZHryoWtoKjB3Hp5dvTasweI6WHtIm313TSLuoXrg=";
public static void main(String[] args) {
String content = "c/BOhNHjhvCXvOenIyNqmr0FI1M3cYt/BR/WEoMgoi37ZFvKe418xOlRU4AN/QyvY2H7g2osL9oLmArsw35jk43reMFUyemTLnZ4Xw/DXT5xxPzHy4NWLt2/K0mqA2e5PiShf8RX9EdLnoIYZPXKe3Ldnw0ha3RZtP4X2tBsHqU=";
String jsonStr;
try {
//解密
jsonStr = decrypt(content, prikey, "UTF-8");
System.out.println(jsonStr);
//sign签名
System.out.println(sign(prikey, content, "UTF-8"));
} catch (Exception e) {
e.printStackTrace();
}
}
/**
* RSA signature algorithm
* @param privateKey
* @param content
* @param charset
* @return
* @throws Exception
*/
public static String sign(String privateKey, String content, String charset) throws Exception {
PKCS8EncodedKeySpec priPKCS8 = new PKCS8EncodedKeySpec( Base64.decodeBase64(privateKey) );
KeyFactory keyf = KeyFactory.getInstance("RSA");
PrivateKey priKey = keyf.generatePrivate(priPKCS8);
java.security.Signature signature = java.security.Signature.getInstance("SHA1WithRSA");
signature.initSign(priKey);
signature.update(content.getBytes(charset) );
byte[] signed = signature.sign();
return Base64.encodeBase64String(signed);
}
public static String decrypt(String content, String private_key, String input_charset) throws Exception {
PrivateKey prikey = getPrivateKey(private_key);
Cipher cipher = Cipher.getInstance("RSA");
cipher.init(Cipher.DECRYPT_MODE, prikey);
InputStream ins = new ByteArrayInputStream(Base64.decodeBase64(content.getBytes()));
ByteArrayOutputStream writer = new ByteArrayOutputStream();
//rsa解密的字节大小最多是128,将需要解密的内容,按128位拆开解密
byte[] buf = new byte[128];
int bufl;
while ((bufl = ins.read(buf)) != -1) {
byte[] block = null;
if (buf.length == bufl) {
block = buf;
} else {
block = new byte[bufl];
for (int i = 0; i < bufl; i ) {
block[i] = buf[i];
}
}
writer.write(cipher.doFinal(block));
}
return new String(writer.toByteArray(), input_charset);
}
public static PrivateKey getPrivateKey(String key) throws Exception {
byte[] keyBytes;
keyBytes = Base64.decodeBase64(key.getBytes());
//使用PKCS8
PKCS8EncodedKeySpec keySpec = new PKCS8EncodedKeySpec(keyBytes);
KeyFactory keyFactory = KeyFactory.getInstance("RSA");
return privateKey;
}
}
PrivateKey privateKey = keyFactory.generatePrivate(keySpec);
4. 服务端notify解密demo(php版)
<?php
$privkey=<<<EOT
-----BEGIN PRIVATE KEY-----
MIICdwIBADANBgkqhkiG9w0BAQEFAASCAmEwggJdAgEAAoGBAN/dCMqrU4GCvJ1s
QwPxvCnYSsXsm0 wdIzPBajdRiI9rvgtxRDq10yHGwXs RNOGxaglj0F 9kRQ7l5
BEkN/HgPg90uWT6bNp5Qf4K3qJWfY6FmWoNDKYyIYjDacAVheAC/Idg/0nKgTUKH
sowx8iXHnKBB3o7B7XGoKCjFKc2PAgMBAAECgYEAjIVAqYdVyav5HZABmQ46oMGm
Xgshiqom3uRslw0eowu5Mwv38aCYOO9t5RBVYOrcUh3HcNK6vgz6SAhQylK/MKk8
hynSBnawh5/XZUUI7Zqw5NFoLIHgdKxcNzGhp5a6eTGOyPVXBi9/ PczeD5Enf2n
2RSCJV2yyAzxAzdM DECQQD4eVHsYzkkmMFaPnJPWcGuLpl7hz1Fte5n83SiZhY/
6WJsC0FpKiCmpxrGhl2yM3gp0kS4b7/uuulIEQyPOAWdAkEA5qTiHZL/ GJOtxwU
kvvVplEmOKGHEcUSoLgxnBYS35S3qgxH4X989coyHV6EMNUXd5hO1vz3RnIVRvrx
sYsuGwJAcV9x2OlBNoiYmKOrprcun1pV375KX9duS3ITQtJPzqOfq rK0sBNG51d
oz3F3LyNVI/DmWAr9DLGpIJa97I5JQJBALcqTmAKM7m/6J9Gb5hi4sMYQvBKZwfX
p/l3Df7VENv6MPmckyEjq8tObgog234kXGSf0kytzHpnczpRY8wJqe0CQCNv7Th8
jnlWQ21UVBL1Lr3KcMM/0RJ0hiVGH46Gp93h9c2zsAgHQ01HLi1BeRcM1tZZNPIh
GqEuuIa/iXjzNNc=
-----END PRIVATE KEY-----
EOT;
$res = openssl_get_privatekey($privkey);
//$content = "ycoYI7SXtj9GWHHNS27jeF18x7B0JVFxyb0 X/k4fjHpe7Jvwk7TGdT5VF NWjBKpPVfyv5NRUYMNrHsHSeQgd4AWO6y3e5HWGmhCa92YdAzriSqoU2fAud4zJQtu1lKQP iM5sC21GhSHlhm 2q443kKjuUX2Fl6wv4 H2onXBmbw2KHbz knQW9AhjVoamYhy2X0XoAK6KtcQk7frk9ASqgf8iob0kteFp9HN/86 QFLUiH7BQm Dh3tkDTBzIm4huCN4 bi71FLYLXLUYVWxcSC24S16Z11ihm771dFa 4w2taeAlhOEZHcE1w8uBXZPMlxlkT66OhvQXZRf88g==";
$content = $_POST['data'];
$content = base64_decode($content);
$i = 0;
$result = "";
while($head = substr($content, $i, 128)) {
$i = 128;
openssl_private_decrypt($head,$newsource,$res);
$result .= $newsource;
}
$result = json_decode($result, true);
var_dump($result);
SDK接入方法
1 在eclipse中导入demo,能看到2个工程:
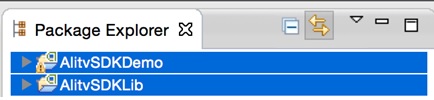
1)AlitvSDKLib包含了SDK用到的lib和res
2)AlitvSDKDemo引用上述Lib工程
2 按照以下截图配置,把SDK引入您的工程
1) 在项目属性中配置
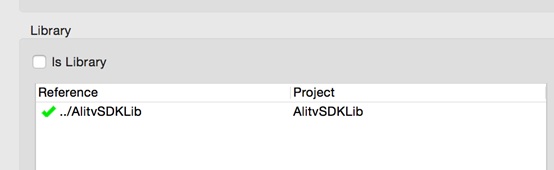
2) Configure in Java Build Path
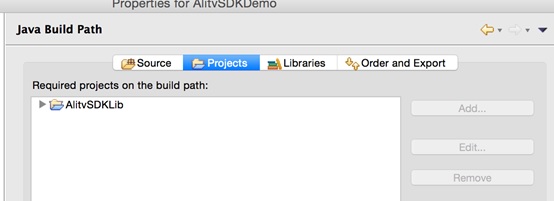
3) Configure the manifest to be merged
Add a line of code to project.properties in the root directory of your project: manifestmerger.enabled=true








