Rumah >tutorial komputer >pengetahuan komputer >Konfigurasi kepercayaan bersama log masuk SSH Linux
Konfigurasi kepercayaan bersama log masuk SSH Linux
- 王林ke hadapan
- 2024-02-19 19:48:56819semak imbas
1. Tujuan ssh saling percaya
1. Apabila membina kluster, anda memerlukan SSHSaling mempercayai, yang sesuai untuk memudahkan operasi pada nod lain.
2. Apabila menggunakan scp远程拷贝操作时,需要输入目标服务器的用户名和密码,这个时候可以做linux服务器之间ssh互信配置, 这样在多个linuxuntuk beroperasi antara pelayan, anda boleh log masuk tanpa kata laluan.
2. Prinsip konfigurasi saling percaya ssh
Ringkasnya, pelayan menyimpan sijil hos sasaran supaya pengesahan dilakukan secara automatik tanpa memasukkan kata laluan.
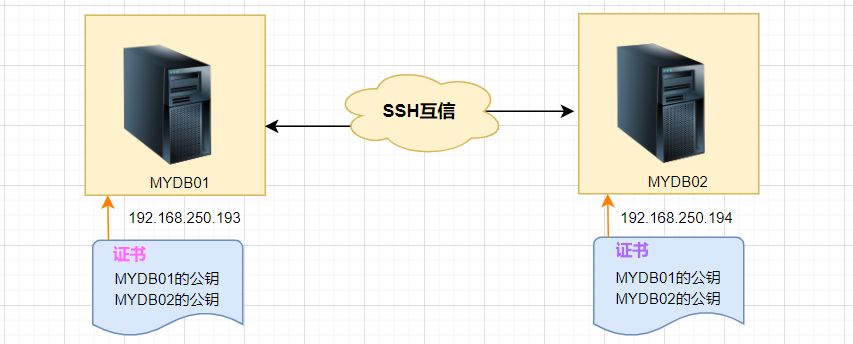
3. Langkah konfigurasi saling percaya SSH
1. Setiap nod menjana kunci awam dan pasangan kunci peribadinya sendiri.
2 Hantar fail kunci awam anda kepada pihak lain.
3. Sahkan sama ada konfigurasi kepercayaan bersama berjaya.
4. Konfigurasikan ssh saling percaya
Berikut ialah MYDB01和MYDB02两台LINUXhos sebagai contoh:
4.1 Hasilkan kunci awam dan pasangan kunci peribadi
Jana pada dua hos masing-masing, tekan enter terus apabila digesa untuk memasukkan maklumat:
# MYDB01Hos:
[root@MYDB01 ~]# ssh-keygen -t rsa Generating public/private rsa key pair. Enter file in which to save the key (/root/.ssh/id_rsa): Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in /root/.ssh/id_rsa. Your public key has been saved in /root/.ssh/id_rsa.pub. The key fingerprint is: SHA256:lQex2+SbdmGGNBvU8vjaTKVCbfAmk8Eva+C6BPJ49G0 root@MYDB01 The key's randomart image is: +---[RSA 2048]----+ |oo.. | | == .| |+ *@ | | ..BB=B .| |. o S..o=O+o | | = o .. +=+. | |. o o.E.+*.| | . ... ...o| |.. | +----[SHA256]-----+ [root@MYDB01 ~]#
# MYDB02Hos:
[root@MYDB02 ~]# ssh-keygen -t rsa Generating public/private rsa key pair. Enter file in which to save the key (/root/.ssh/id_rsa): Created directory '/root/.ssh'. Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in /root/.ssh/id_rsa. Your public key has been saved in /root/.ssh/id_rsa.pub. The key fingerprint is: SHA256:8DGfMHFZDrEOOYhcpFGXI8tndQXTE4FampR6cTowAo4 root@MYDB02 The key's randomart image is: +---[RSA 2048]----+ |o++ o.+=+=+o | | + =oo=+*+=.o| |E =.o+OB.X.. | |oo+XB. | | oS.+. | | | | | | | | | +----[SHA256]-----+ [root@MYDB02 ~]#
Dengan cara ini, kunci awam dan kunci rahsia dicipta, dan **id_rsa和id_rsa.pub** dua fail akan dijana.
Menjanassh密钥后,密钥将默认存储在家目录下的**.ssh/目录**.
Kebenaran kunci persendirian dan kunci awam adalah **600和644** masing-masing.
.ssh kebenaran direktori mestilah 700
Pilihan:
-t rsa|dsa默认是rsaFormat.
Kemudian anda boleh melihat kunci awam dan fail kunci peribadi yang dijana:
[root@MYDB01 ~]# cd /root/.ssh [root@MYDB01 .ssh]# pwd /root/.ssh [root@MYDB01 .ssh]# ll -sh 总用量 12K 4.0K -rw-------1 root root 1.7K 2月14 16:17 id_rsa 4.0K -rw-r--r--1 root root393 2月14 16:17 id_rsa.pub [root@MYDB01 .ssh]#
4.2 Hantar fail kunci awam anda kepada pihak lain
# Format arahan:
ssh-copy-id [-i [identity_file]] [user@]machine
Fungsi arahan ini adalah untuk membuang id_rsa.pub文件内容传输至对方的 .ssh目录中,生成文件名为authorized_keys 文件,并且会设置远程主机用户目录的**.ssh和.ssh/authorized_keys** kebenaran.
# Lakukan perkara berikut pada MYDB01:
[root@MYDB01 .ssh]# ssh-copy-id 192.168.250.194 /usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "/root/.ssh/id_rsa.pub" /usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed /usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys root@192.168.250.194's password: Number of key(s) added: 1 Now try logging into the machine, with: "ssh '192.168.250.194'" and check to make sure that only the key(s) you wanted were added. [root@MYDB01 .ssh]#
Lihat di sini di MYDB02hos:
[root@MYDB02 ~]# cd /root/.ssh [root@MYDB02 .ssh]# ll 总用量 12 -rw------- 1 root root393 2月14 16:41 authorized_keys -rw------- 1 root root 1679 2月14 16:20 id_rsa -rw-r--r-- 1 root root393 2月14 16:20 id_rsa.pub [root@MYDB02 .ssh]# cat authorized_keys ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCtQ+pBp1T9fHAkrifEShaOAfBJFT+HdljR8mBxl7wZ1a91g3Zuzu35gJKsUjD+NqP9JcdyKapE309SHPvosvsJjLfccF4PaEZAgqHryu+S3cBn8zqA6fm62hsx/qI4I80PV0btcqfwphsD+5+vgkDJWAsUGQtqZdmMClAIy5gs0He0K2jpciKHvxWWClB3+dTJ0e9yIuIkV7lM+jqVIqYFJD0bRyy0zgNsY5/cLYFllM42TQDos93hVdqGXOHREpWo01KX2Jd8MKj4yNeiqgnj2mDtiNFWOUSkAbHpcKInuUOErJMqkV7MP0er5UKY/NemDzuORr2RxYqSTWaz/T7N root@MYDB01 [root@MYDB02 .ssh]#
Operasi di atas hanyalah kepercayaan sebelah pihak MYDB01登录主机MYDB02log masuk ke hos
MYDB02上将其钥复制到主机MYDB01# Salin kuncinya pada hos
:
[root@MYDB02 .ssh]# ssh-copy-id 192.168.250.193 /usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "/root/.ssh/id_rsa.pub" The authenticity of host '192.168.250.193 (192.168.250.193)' can't be established. ECDSA key fingerprint is SHA256:vThEoRhUOECeD5jhE+m8TZA2+6OoElIoNOQ3XqtopZw. ECDSA key fingerprint is MD5:97:40:b2:35:6e:07:5a:61:1f:73:f1:b2:6e:54:5b:7d. Are you sure you want to continue connecting (yes/no)? y Please type 'yes' or 'no': yes /usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed /usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys root@192.168.250.193's password: Number of key(s) added: 1 Now try logging into the machine, with: "ssh '192.168.250.193'" and check to make sure that only the key(s) you wanted were added. [root@MYDB02 .ssh]#
4.3 Sahkan kepercayaan bersamaMYDB01主机和MYDB02主机上通过SSH
pada MYDB01主机上登录MYDB02 hos dan
Log masuk ke
hos MYDB02主机上登录MYDB01Hos:
[root@MYDB01 .ssh]# ssh 192.168.250.194 Last login: Tue Jan 9 15:41:56 2023 from 192.168.250.193 [root@MYDB02 ~]#🎜Berjaya log masuk tanpa kata laluan. 🎜 🎜Begitu juga, log masuk pada 🎜hos: 🎜
[root@MYDB02 .ssh]# ssh 192.168.250.193 Last failed login: Tue Feb 14 16:48:54 CST 2023 from 192.168.250.194 on ssh:notty There was 1 failed login attempt since the last successful login. Last login: Tue Jan 9 15:41:34 2024 from 192.168.250.194 [root@MYDB01 ~]#
Atas ialah kandungan terperinci Konfigurasi kepercayaan bersama log masuk SSH Linux. Untuk maklumat lanjut, sila ikut artikel berkaitan lain di laman web China PHP!

