Python 정적 분석의 차원
- WBOYWBOYWBOYWBOYWBOYWBOYWBOYWBOYWBOYWBOYWBOYWBOYWB원래의
- 2024-07-19 06:07:20876검색
'린팅'이라고도 알려진 Python 정적 분석은 소프트웨어 개발의 중요한 측면입니다. 여기에는 잠재적인 버그, 프로그래밍 오류, 스타일 문제 또는 미리 정의된 코딩 표준을 따르지 않는 패턴을 식별하기 위해 실행하지 않고 Python 코드를 검사하는 작업이 포함됩니다. 또한 개발 프로세스 초기에 취약점을 식별하여 안전하지 않은 코드를 프로덕션에 배포할 가능성을 줄이는 데 도움이 됩니다. 예를 들어, 하드 코딩된 자격 증명 사용, SQL 주입 공격으로 이어질 수 있는 일반적인 실수 또는 데이터 정리와 관련된 잠재적인 문제와 같은 안전하지 않은 코딩 관행을 찾아낼 수 있습니다.
Python은 Pylint, Pyflakes, Flake8 등 정적 분석을 위한 여러 라이브러리와 도구를 제공합니다. 예를 들어, Pylint는 코딩 표준을 시행하고, 오류를 감지하고, 코드 복잡성을 검사하는 데 도움을 줄 수 있습니다. 다음은 Pylint 사용 방법을 보여주는 간단한 코드 조각입니다.
# test.py
def add(x, y):
return x + y
add(1, '2')
Pylint를 실행하면 다음이 제공됩니다.
$ pylint test.py ************* Module test test.py:5:4: E1136: Value '2' is unsubscriptable (unsubscriptable-object) -------------------------------------------------- Your code has been rated at -10.00/10
Pylint가 정수와 문자열을 추가하려고 할 때 오류를 감지했는데, 이는 Python에서 유효한 작업이 아닙니다.
1. Python 정적 분석에서 유형 확인
Python은 다재다능하고 역동적인 언어이며, 유연성은 개발자들 사이에서 선호되는 이유 중 하나입니다. 그러나 이러한 역동성은 때로는 찾기 어려운 버그로 이어질 수 있으며, 특히 유형 오류의 경우 더욱 그렇습니다. Python 정적 분석이 시작되는 곳입니다.
유형 검사에 대해 알아보기 전에 Python에서 동적 유형 지정이 무엇을 의미하는지 이해해 보겠습니다. Python은 동적으로 유형이 지정됩니다. 즉, 변수 유형이 런타임에 확인되므로 명시적으로 지정할 필요가 없습니다. 이는 아래 코드 조각에서 설명됩니다.
# x is an integer x = 5 # x is now a string x = "Hello, World!"
동적 유형 지정을 사용하면 Python을 더 쉽게 사용하고 읽을 수 있지만 코드가 실제로 실행될 때만 발견되는 유형 오류가 발생할 수도 있습니다.
정적 유형 검사의 역할
정적 유형 검사는 개발 프로세스 초기, 즉 런타임이 아닌 코딩이나 빌드 중에 유형 오류를 포착하는 접근 방식입니다. 이를 통해 잠재적인 버그가 프로덕션 코드로 유입되는 것을 방지하여 코드 보안과 안정성을 향상할 수 있습니다. 정적으로 유형이 지정된 프로그래밍 언어의 예로는 Java 및 C++가 있습니다.
Python은 동적 유형 지정 언어이지만 유형 주석을 통해 선택적 정적 유형 지정도 지원합니다. 이 기능을 사용하면 예상되는 변수 유형, 함수 매개변수 및 반환 값에 주석을 달 수 있습니다. Python 런타임은 이러한 유형을 적용하지 않지만 정적 분석 도구에서 잠재적인 유형 오류를 포착하는 데 사용할 수 있습니다.
def greet(name: str) -> str:
return 'Hello, ' + name
이 예에서 name은 문자열이어야 하고 함수도 문자열을 반환해야 합니다.
Python의 정적 유형 검사 도구
Python의 정적 유형 검사에 도움이 되는 여러 도구가 있습니다. 그 중에서도 Mypy, Pyright 및 Pyre는 Python 커뮤니티에서 견고성과 폭넓은 수용력을 자랑합니다.
- Mypy: 동적 유형 지정과 정적 유형 지정의 이점을 결합하는 것을 목표로 하는 Python용 선택적 정적 유형 검사기입니다. 다용도로 사용할 수 있으며 CI/CD 파이프라인에서 유형 오류가 프로덕션에 들어가기 전에 이를 포착하는 데 사용할 수 있습니다.
- Pyright: Microsoft에서 개발한 Pyright는 성능에 중점을 둔 정적 유형 검사기입니다. TypeScript로 작성되었으며 Node.js에서 실행됩니다.
- Pyre: Pyre는 Facebook에서 개발한 Python용 고성능 유형 검사기입니다. 터미널이나 즐겨 사용하는 편집기에서 유형 오류를 대화형으로 표시하여 코드 품질과 개발 속도를 향상시키도록 설계되었습니다.
코드 예: 유형 확인을 위해 Mypy 사용
Mypy 설치는 pip install mypy를 실행하는 것만큼 간단합니다. 일단 설치되면 이를 사용하여 Python 파일에 유형 오류가 있는지 확인할 수 있습니다. 다음은 간단한 예입니다.
# file: hello.py
def greet(name: str) -> str:
return 'Hello, ' + name
# This will cause a type error
greet(123)
다음과 같이 Mypy를 사용하여 이 파일을 확인할 수 있습니다.
$ mypy hello.py hello.py:5: error: Argument 1 to "greet" has incompatible type "int"; expected "str" Found 1 error in 1 file (checked 1 source file)
보시다시피 Mypy는 코드가 실행되기 전에 유형 오류를 포착했습니다.
2. Python 정적 분석의 린터
Linter는 프로그래밍 오류, 버그, 문체 오류 및 의심스러운 구문을 표시하는 데 사용되는 정적 코드 분석 도구입니다. Python의 맥락에서 린터는 코드의 품질과 보안을 유지하는 데 중요한 역할을 합니다. 이는 코딩 표준을 시행하고 개발 프로세스 초기에 잠재적인 버그와 보안 취약성을 감지하며 Python 코드의 전반적인 가독성과 유지 관리성을 향상시키는 데 도움이 됩니다.
Python 생태계에서 가장 널리 사용되는 린터로는 Pylint, Flake8, Pyflakes가 있습니다.
- Pylint: Pylint is a highly configurable, open-source tool that checks for errors in Python code, enforces a coding standard, and looks for code smells. Pylint can also be used to write custom plugins for specific use cases.
- Flake8: Flake8 is a Python library that wraps PyFlakes, pycodestyle, and Ned Batchelder’s McCabe script. It is a great toolkit that checks your project for compliance with PEP 8, Python’s style guide.
- Pyflakes: Pyflakes checks Python source files for errors quickly but without executing them. It's faster than Pylint and Flake8 because it doesn't enforce style guides, making it a good option for a quick, basic check of your Python code.
The concept of code smells and enforcing coding standards
Code smells are indicators of deeper problems with your code. They are patterns in code that suggest violations of fundamental design principles and negatively impact design quality. Some common examples of code smells in Python include large classes, long method, duplicate code, and dead code.
Linters like Pylint, Flake8, and Pyflakes help detect such code smells and enforce coding standards in your Python code to improve code quality and keep it at an acceptable standard. They do this by checking your code against pre-defined rules and guidelines, which are often based on community-adopted best practices such as PEP 8 for Python.
Code example demonstrating a linter in action
Here's an example of how to use Pylint to perform static analysis on a Python file named example.py:
# example.py
def add(a, b):
return a+b
To run Pylint on this file, you would use the following command:
pylint example.py
If there are any issues with your code, Pylint will flag them and provide a detailed report. For example, it might highlight that the function add is missing function docstring, which is a violation of PEP 8's guidelines for writing good Python code.
Custom rules in linters
Linters like Pylint allow you to define custom rules for your Python projects. This is particularly useful when you have specific coding standards or guidelines that are unique to your project or organization.
Creating a custom rule in Pylint involves creating a Python class that extends from one of Pylint’s checker classes and then defining methods that perform the actual checking of the code. Once you've defined your custom rules, you can then add them to your Pylint checker using the register_checker method.
Here's a simple example of a custom Pylint rule that checks for the use of the print statement:
from pylint.checkers import BaseChecker
from pylint.interfaces import IAstroidChecker
class NoPrintStatementsChecker(BaseChecker):
__implements__ = IAstroidChecker
name = 'no-print-statements'
msgs = {
'W0001': (
'Print statement used',
'no-print-statements',
'Print statements should not be used',
),
}
def visit_print(self, node):
self.add_message('no-print-statements', node=node)
def register(linter):
linter.register_checker(NoPrintStatementsChecker(linter))
In this example, the NoPrintStatementsChecker class checks for the use of the print statement and raises a warning if it finds one. The register function is then used to register this custom checker with Pylint.
3. Security vulnerability detection
One of the critical dimensions of Python static analysis is security vulnerability detection. Let's break down the importance of security in Python static analysis, common security risks in Python code, and a few tools you can use for security vulnerability detection, such as Bandit and Snyk Code.
When you write Python code, security should not be an afterthought but an integral part of the development process. Python static analysis plays a crucial role in ensuring code security, as it can help identify potential security vulnerabilities at an early stage of the development cycle, even before the code execution. Vulnerabilities such as injection attacks, insecure direct object references, security misconfigurations, and cross-site scripting are prevalent in Python code.
For instance, an SQL injection vulnerability in Python code might look like this:
def get_user_details(user_id):
return database.execute(f'SELECT * FROM users WHERE id = {user_id}')
In the above example, the user_id is directly used in a SQL query, which opens up the possibility for SQL injection if the user_id is not properly sanitized and is provided by the user.
Tools for security vulnerability detection
Bandit
Bandit is a tool designed to find common security issues in Python code. It processes each file, builds an AST (Abstract Syntax Tree) from the Python code, and runs appropriate plugins against the AST nodes.
Here's how you can use Bandit to scan your Python code for security vulnerabilities:
$ bandit -r path/to/your/python/code
Would Bandit find an insecure direct object reference in Python? Unsure? read more about Snyk next.
Snyk Code
Snyk Code is another tool that provides a fast, symbolic AI-powered analysis engine. With Snyk Code, you can quickly find security vulnerabilities in your Python code. Snyk Code's static analysis engine is designed to understand the context and flow of your code, enabling it to detect complex security vulnerabilities that other tools might miss.
Snyk Code also comes with a PyCharm IDE plugin, allowing developers to detect and fix security issues in real time as they code.
To get started with Snyk Code, you simply need to download the PyCharm IDE plugin for Snyk, and you can start using it for free.
Implementing security vulnerability detection as part of your Python static analysis is crucial in ensuring the security of your software. Tools like Bandit and Snyk Code provide developers with an easy and efficient way to detect and fix security vulnerabilities in their Python code.
4. Code complexity analysis
Code complexity is a metric that is used to gauge how hard your code is to understand or modify. Higher complexity often translates to increased difficulty in comprehending the code, which in turn affects the code's maintainability.
Maintaining code is a regular part of a developer's job, but when the codebase becomes complex, it becomes increasingly challenging to understand and modify. This issue can lead to bugs and decrease the overall quality of the software. As a result, code complexity analysis is crucial in software development to ensure high-quality, maintainable code.
Cyclomatic complexity measurement with radon
To measure code complexity in Python, one can use various tools, and one of such is Radon. Radon is a Python tool that computes various metrics from the information extracted from the Abstract Syntax Tree (AST). One of these metrics is the Cyclomatic Complexity.
Cyclomatic Complexity is a software metric used to indicate the complexity of a program. It is a quantitative measure of the number of linearly independent paths through a program's source code. Radon analyzes your Python code and gives it a rank from A to F, where A means the code is simple and easy to understand, while F signifies it's too complex.
To use Radon, you need to install it first. You can install it using pip:
pip install radon
Code example demonstrating code complexity analysis
After installing Radon, you can use it to analyze your Python code. Let's consider the following Python code:
def calculate_sum(n):
if n < 0:
return "Negative number"
else:
return sum(range(n+1))
To measure the complexity of the above code, you would run the following command:
radon cc your_file.py
This command will return the cyclomatic complexity of the code. The complexity of the above code is 2, which means it is not very complex.
But if we look at a more complex function, for example:
def complex_function(a, b, c):
if a > b:
if a > c:
return a
else:
return c
else:
if b > c:
return b
else:
return c
Running Radon on this code would return a complexity of 5, indicating a higher level of complexity.
Using cyclomatic complexity tools helps maintain the quality of the code, making it easier to understand and modify. Tools like Radon provide a simple way to measure code complexity in Python, thus making your code more maintainable and less prone to bugs.
5. Dependency analysis
In the world of open source software taking a pillar step in software development, dependency analysis is a significant aspect that developers cannot afford to overlook. This procedure is crucial when dealing with large codebases in languages such as Python. Dependency analysis involves the identification of dependencies between different elements in a software project. Let's explore the importance of understanding and managing dependencies, tools for dependency analysis like Snyk and the Snyk Advisor, and a practical example showcasing dependency analysis in action.
Importance of understanding and managing dependencies
In Python projects, dependencies are the external packages or libraries that your project uses. These could range from web frameworks like Django or Flask to data science libraries like NumPy or pandas.
Understanding and managing dependencies is crucial for several reasons:
- It helps maintain the stability and reliability of your software. If a dependency that your project relies on has a bug or breaks, your software could also break.
- It assists in improving the security of your project. Dependencies can have security vulnerabilities that could affect your project if left unpatched.
- It aids in aligning with licensing requirements. Each dependency may have its own license, and you need to ensure you comply with all of them.
Snyk Advisor for dependency analysis
Snyk Advisor is a tool that provides insights into your Python project's dependencies, including information about security vulnerabilities, licensing issues, and outdated packages. It helps you understand the risks associated with your dependencies and provides actionable advice on how to mitigate them.
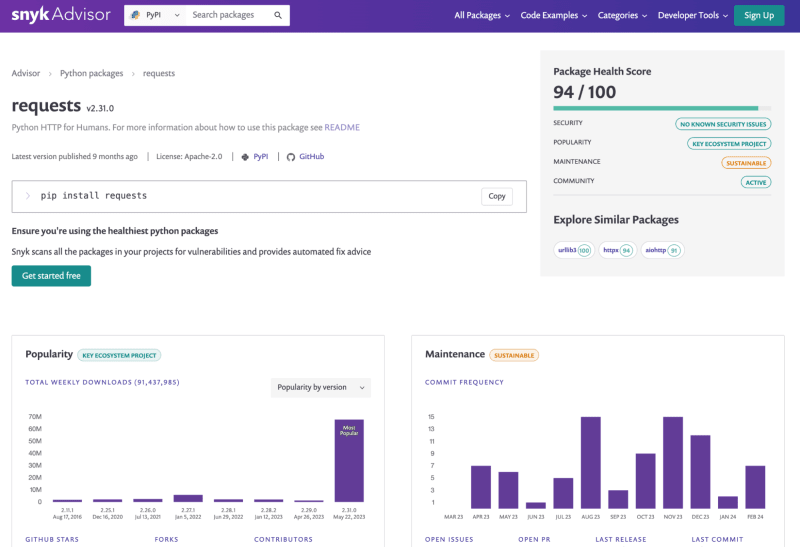
The Snyk CLI can be used to analyze your Python project's dependencies and alert you of vulnerable open source packages installed from PyPI or insecure code in your Python program. After installing the Snyk CLI, you can run the following command to analyze your project:
snyk test --all-projects
This command will analyze your project's dependencies and provide a report on any security vulnerabilities, licensing issues, or outdated packages. For example, it might alert you of vulnerabilities when you scan a Python FastAPI project:
Testing FastAPI... ✗ High severity vulnerability found in requests Description: Out-of-bounds Read Info: https://snyk.io/vuln/SNYK-PYTHON-REQUESTS-174006 Introduced through: requests@2.25.1 From: requests@2.25.1 > urllib3@1.26.3 > requests Fix: https://snyk.io/vuln/SNYK-PYTHON-REQUESTS-174006 Organization: snyk Package manager: pip Target file: requirements.txt
Get started with Snyk for Python security to secure your first line of code and all the way to your last pip dependency and your deployed Python container applications.
Using pipenv graph for dependency analysis
Let's consider a simple Python Flask application to showcase dependency analysis in action. Here's the app.py file:
from flask import Flask
app = Flask(__name__)
@app.route('/')
def hello_world():
return 'Hello, World!'
We will use Pipenv for this example. First, initialize Pipenv and install Flask:
pipenv install flask
Now, running pipenv graph will show:
flask==1.1.2
- click [required: >=5.1, installed: 7.1.2]
- itsdangerous [required: >=0.24, installed: 1.1.0]
- Jinja2 [required: >=2.10.1, installed: 2.11.2]
- MarkupSafe [required: >=0.23, installed: 1.1.1]
- Werkzeug [required: >=0.15, installed: 1.0.1]
This output reveals that Flask, our project's direct dependency, depends on click, itsdangerous, Jinja2, and Werkzeug. Jinja2 further depends on MarkupSafe. Thus, we have successfully analyzed the dependencies of our project.
If you're new to pipenv and want to learn more about it, I recommend reading mastering Python virtual environments: A complete guide to venv, Docker, and securing your code to familiarize yourself with the concept of virtual environments in Python.
In conclusion, regular dependency analysis in Python projects is necessary to maintain code reliability, enhance security, and ensure licensing compliance. Tools like Snyk, Snyk Advisor, and Pipenv make this task more manageable and provide a clear picture of the dependency tree.
6. Code formatting tools
Adhering to a consistent code style and format is another aspect of maintaining code readability and efficiency. Code formatting tools play a vital role in this context. They help developers automatically format their codebase according to a set of predefined rules. This not only improves the code's overall quality but also reduces the time and effort required for manual code reviews. Let's introduce you to popular cde formatters like Black and YAPF.
Let's consider an example to understand the difference that a code formatter can make. Below is a piece of Python code before and after applying the Black formatter.
Before formatting:
def function(arg1,arg2,arg3=4,arg4=8,arg5=16):
return arg1+arg2+arg3+arg4+arg5
print(function(1,2))
After formatting with Black:
def function(arg1, arg2, arg3=4, arg4=8, arg5=16):
return arg1 + arg2 + arg3 + arg4 + arg5
print(function(1, 2))
YAPF Python code formatter
YAPF (Yet Another Python Formatter) is another code formatter for Python that goes beyond PEP8 to provide a more uniform code style. Unlike PEP8, YAPF takes into consideration how the code looks and makes it more readable.
Here is an example of how to use YAPF:
# install yapf pip install yapf # use yapf to format a python file yapf -i your_python_file.py
7. Abstract syntax trees (AST) in Python
What is an abstract syntax tree (AST)? An abstract syntax tree is a tree representation of the syntactic structure of source code written in a programming language. Each node of the tree denotes a construct in the source code. The syntax is 'abstract' in not representing every detail appearing in the real syntax.
In Python, when the interpreter executes code, it first converts it into an intermediate form known as bytecode. This conversion process involves the creation of an AST. An AST in Python is a simplified representation of the Python code structure. It strips away details like formatting and whitespace, focusing only on the commands and their order, providing a structural view of the code.
The Python ast module and its capabilities
Python's standard library includes the ast module, which enables the creation, manipulation, and inspection of ASTs. This module provides a set of classes, functions, and helper methods to work with Python ASTs programmatically.
The ast.parse() function is a common entry point to create ASTs. It parses Python source code into an AST node, which can then be manipulated or inspected.
The ast module also provides a NodeVisitor class to walk the AST and call a visitor function for every node found. This class can be used as-is or subclassed to override methods and provide functionality for specific node types.
AST inspection and manipulation: A practical example
Let's dive into a simple example of using the ast module to inspect and manipulate an AST in Python.
import ast
# Parse some code into an AST
root = ast.parse("print('Hello, World!')")
# Print all the nodes in the AST
for node in ast.walk(root):
print(type(node))
# Modify the AST to print a different message
for node in ast.walk(root):
if isinstance(node, ast.Str): # Change the string literal in the Print node
node.s = 'Hello, AST!'
# Convert the modified AST back into code
code = compile(root, filename="", mode="exec")
# Execute the modified code
exec(code)
In this example, we first parse a simple Python print statement into an AST using ast.parse(). We then inspect the AST by walking through all the nodes and printing their types. After that, we modify the AST by changing the string literal in the Print node. Finally, we convert the modified AST back into code using compile() and execute it with exec(). The output of this code will be 'Hello, AST!', not 'Hello, World!'.
This example showcases the inspection and modification capabilities of the ast module in Python. The potential applications of ASTs in the field of code security and software development are vast, from automated code refactoring to advanced static code analysis for security vulnerabilities.
8. Control and data flow analysis
Control and data flow analysis are vital components. This technique facilitates efficient error detection, boosts code readability, and enhances the overall quality of Python applications.
Control flow analysis involves evaluating the execution order of statements or instructions in a program, while data flow analysis focuses on the tracking and analysis of data values as they change throughout the program. Here are some reasons why these analyses are important:
- Detection of potential errors: Control and data flow analysis can help identify potential bugs and vulnerabilities in the code, such as infinite loops, unreachable code, or unused variables.
- Code optimization: By understanding how data moves through your code and how control flows, you can identify areas of inefficiency and make necessary improvements.
- Enhanced code readability: Control and data flow analysis can help to make the code more understandable by highlighting the dependencies and interactions between different parts of the code.
- Security assurance: Understanding the flow of data and control in your application is essential for ensuring security. It can help identify potential security vulnerabilities, such as data leaks or injection attacks.
Code example demonstrating control and data flow analysis
To illustrate the concept of control and data flow analysis in Python, let's consider a simple Python function:
def calculate_total(price, quantity):
if quantity <= 0:
return "Invalid quantity"
else:
total = price * quantity
return total
In this function, the control flow is determined by the if-else statement. If the quantity is less than or equal to 0, the function returns an error message. Otherwise, it calculates and returns the total price.
The data flow, on the other hand, can be traced from the input parameters (price and quantity) to the final result (total). The values of these variables change as they pass through the function.
A static analysis tool would analyze this function's control and data flow to detect any potential issues. For instance, it might flag an issue if price or quantity were used before being defined or if there was a possible path through the function where total wasn't defined before it was returned.
Through control and data flow analysis, you can develop efficient, understandable, and secure Python applications. By integrating this process into your software development life cycle, you can uphold code quality and prevent potential security vulnerabilities from creeping into your application.
9. Integration with Python development environments
Python static analysis tools are not meant to be standalone utilities. They are most effective when seamlessly integrated into the development environment, which can enhance development workflows, continuous integration (CI) pipelines, and code editors.
The following describes the roles of Python static analysis tools in these areas and provides a practical example of such integration:
- Role in development workflows: Static analysis tools play a pivotal role in development workflows. Python developers can use these tools to identify and fix potential issues during the development phase, even before the code is run. This early detection can save significant debugging time and enhance code quality.
- Role in CI pipelines: In Continuous Integration pipelines, static analysis tools can be used to automatically analyze the code in each commit or pull request. This ensures that any new changes adhere to the coding standards and do not introduce potential vulnerabilities. These tools can be integrated into CI pipelines such as Jenkins, GitLab CI, GitHub Actions, etc.
- Role in Code Editors: Most modern code editors, such as Visual Studio Code, PyCharm, Atom, and Sublime Text, support the integration of static analysis tools. This allows developers to get real-time feedback on their code structure, style, and potential vulnerabilities as they write the code.
Practical example: Integrating PyLint into Visual Studio Code
PyLint is a popular Python static analysis tool. Here's how you can integrate it into Visual Studio Code, a widely-used code editor.
Firstly, ensure you have PyLint installed in your Python environment. If not, you can install it using pip:
pip install pylint
Next, open Visual Studio Code and install the Python extension by Microsoft from the Extensions view.
After the extension is installed, open the settings (File > Preferences > Settings). In the User Settings section, search for Python Linting. Make sure the Enabled checkbox is checked and Pylint is selected in the Linter dropdown.
Now, every time you open a Python file in Visual Studio Code, PyLint will automatically analyze the code and highlight any issues it finds.
Here's a sample Python code and how PyLint would highlight an issue:
def add_numbers(a, b):
return a + c
In the above code, PyLint would underline c and show a warning message Undefined variable 'c', helping you catch the error before running the code.
10. Performance profiling
Performance profiling is an essential dimension of Python static analysis. It involves examining your code to identify bottlenecks, inefficient sections, or parts of the code that consume significant CPU or memory resources. By conducting a thorough performance profiling, developers can optimize their code, enhancing the overall speed and efficiency of the application.
Performance profiling allows you to measure the complexity of your code in terms of time and space. Time complexity relates to the total time required to execute a program, while space complexity pertains to the amount of memory used by the program. A performance profile provides a detailed report of the function call count, the time spent in each function, and other information that can help optimize the application's performance.
Python code example demonstrating performance profiling
Python provides several tools for performance profiling, but one of the most common is the built-in cProfile module, which provides a robust and flexible profiler. Here's a simple example of how you can use it:
import cProfile
import re
def re_test():
re.compile("foo|bar")
cProfile.run('re_test()')
When you run this code, cProfile will generate a report showing how much time was spent in each function. The output might look something like this:
200 function calls (195 primitive calls) in 0.002 seconds
Ordered by: standard name
ncalls tottime percall cumtime percall filename:lineno(function)
1 0.000 0.000 0.001 0.001 :0(setprofile)
43 0.000 0.000 0.000 0.000 :0(time)
5 0.000 0.000 0.000 0.000 :1(re\_test)
...
This output shows the number of calls to each function (ncalls), the total time spent in the function excluding calls to sub-functions (tottime), the cumulative time spent in the function including sub-functions (cumtime), and other useful information.
Performance profiling in relation to memory leaks and memory usage is also crucial for production applications. Drew Wright has written a great article on diagnosing and fixing memory leaks in Python from his own experience and struggles with memory leak issues faced during his time in the Snyk engineering team.
Performance profiling has a direct impact on your code. It helps you identify areas of your code that are performance bottlenecks, enabling you to focus on those areas for optimization. Profiling can also help find bugs that might not be visible during regular testing. Moreover, performance profiling can influence the way you write code. A proper understanding of time and space complexity can guide you to write more efficient code, ultimately leading to improved application performance.
결론
정적 분석은 코드 품질을 크게 향상하고 보안을 강화할 수 있는 강력한 도구입니다. 이 기사에서 논의한 Python 정적 분석의 10가지 차원을 활용하면 소프트웨어 개발 프로세스를 향상시키고 잠재적인 버그가 코드베이스에 유입되는 것을 방지하며 애플리케이션이 보안 위협에 덜 취약한지 확인할 수 있습니다.
Python 정적 분석의 여러 측면이 함께 작동하여 프로덕션 환경에서 실제 문제가 되기 전에 잠재적인 문제를 찾아냅니다. 버그를 조기에 발견하면 나중에 수정하는 데 드는 비용을 절약할 수 있습니다. 코드 보안을 보장하려면 Python 정적 분석도 필수적입니다. 수동 코드 검토에서 간과하기 쉬운 잠재적인 보안 취약점을 찾아낼 수 있습니다. Python 정적 분석을 소프트웨어 개발 프로세스에 통합하면 애플리케이션을 더욱 안전하게 만들고 잠재적인 공격으로부터 보호할 수 있습니다.
더 나은 코드와 보안을 위해 개발자를 격려합니다.
이 기사를 통해 Python 정적 분석의 10가지 차원과 이를 사용하여 코드 품질과 보안을 향상하는 방법을 더 잘 이해할 수 있었기를 바랍니다. 고품질의 안전한 코드는 단순히 버그나 취약점을 예방하는 것이 아니라 안정적이고 강력하며 현실 세계의 과제를 해결할 수 있는 소프트웨어를 만드는 것임을 기억하세요.
Python에서 명령 삽입을 방지하는 방법을 알고 있나요? Python에서 코드 삽입을 방지하려면 어떻게 해야 하나요?
Python 애플리케이션의 보안을 보장하려면 Python 보안 모범 사례를 따르는 것이 중요합니다. 지금 무료 Snyk 계정으로 시작하고 Snyk IDE 확장 프로그램을 설치하여 Python 코드의 보안 취약점을 빠르고 쉽게 찾아 수정하세요.
위 내용은 Python 정적 분석의 차원의 상세 내용입니다. 자세한 내용은 PHP 중국어 웹사이트의 기타 관련 기사를 참조하세요!

