 Mobile Tutorial
Mobile Tutorial Android Phone
Android Phone How to enable traffic monitoring on Xiaomi Mi 10s_Steps to enable traffic monitoring on Xiaomi Mi 10s
How to enable traffic monitoring on Xiaomi Mi 10s_Steps to enable traffic monitoring on Xiaomi Mi 10sFaced with the problem of excessive data consumption, how should Xiaomi 10s users deal with it? PHP editor Youzi brings you detailed steps to enable the traffic monitoring function to help you easily control traffic usage. Continue reading below to learn how to effectively monitor your traffic and avoid the frustration of traffic overruns.
1. Click the phone icon on the desktop of your phone.

2. Switch to the business hall interface and click the settings icon on traffic usage.

3. Turn on the switch on the right side of [Traffic Monitoring].

The above is the detailed content of How to enable traffic monitoring on Xiaomi Mi 10s_Steps to enable traffic monitoring on Xiaomi Mi 10s. For more information, please follow other related articles on the PHP Chinese website!
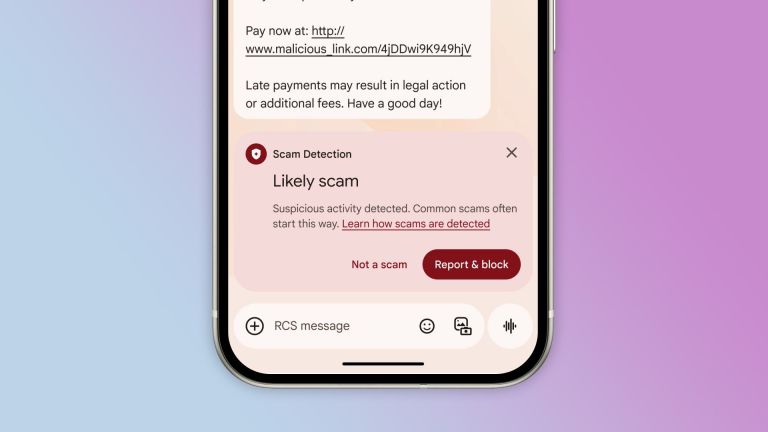 Google Messages Now Has Better Scam Text DetectionMay 15, 2025 pm 12:02 PM
Google Messages Now Has Better Scam Text DetectionMay 15, 2025 pm 12:02 PMGoogle has enhanced its scam detection capabilities within Google Messages, the standard messaging app on many Android devices. It now prevents billions of dubious messages monthly, utilizing on-device processing to safeguard user privacy.This enhanc
 Google Is Making Your Android Phone Harder to StealMay 15, 2025 pm 12:01 PM
Google Is Making Your Android Phone Harder to StealMay 15, 2025 pm 12:01 PMGoogle has significantly enhanced the theft protection capabilities within the Android operating system. These enhancements aim to make it more challenging for thieves to steal or erase Android phones and tablets without the owner's knowledge.The upd
 How to Pair a DualSense Controller to PS Remote Play on Your Android Phone to Play Your PS5 Games from Anywhere May 15, 2025 am 09:24 AM
How to Pair a DualSense Controller to PS Remote Play on Your Android Phone to Play Your PS5 Games from Anywhere May 15, 2025 am 09:24 AMIf you own a PlayStation 5 and an Android phone with Android 12, you can enjoy your PS5 games directly on your mobile device through PS Remote Play. While connecting your PS5's DualSense wireless controller to your phone will enable basic control for
 How to Pair Sony's DualSense Controller to Your Android Phone Over Bluetooth or USB Cable May 15, 2025 am 09:19 AM
How to Pair Sony's DualSense Controller to Your Android Phone Over Bluetooth or USB Cable May 15, 2025 am 09:19 AMThe gaming experience on smartphones has improved significantly since the release of Impossible Games and the original version of Temple Escape. The depth of mobile games can be comparable to console and PC games, but some games require external controllers to get the best gaming experience. The DualSense wireless controller from the PlayStation 5 is a great choice, and it is compatible with most Android devices. Why connect DualSense to your phone? Connecting the DualSense wireless controller to your Android phone allows you to experience a console-like gaming feel on a portable screen, and it is suitable for any Android game that supports wireless controllers. Although DualS
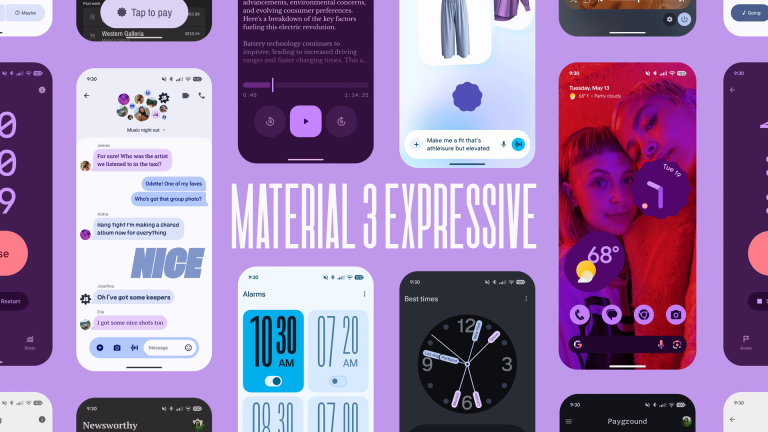 Android Is Getting Its Biggest Design Refresh in YearsMay 14, 2025 pm 09:02 PM
Android Is Getting Its Biggest Design Refresh in YearsMay 14, 2025 pm 09:02 PMIt's time for Android to undergo a significant update. As Google unintentionally revealed earlier, "Material 3 Expressive" represents a major redesign focused on enhancing personalization, fluidity, and immediate utility on your devices.And
 You Can Get the Galaxy Watch FE for As Low As $150 TodayMay 14, 2025 am 05:15 AM
You Can Get the Galaxy Watch FE for As Low As $150 TodayMay 14, 2025 am 05:15 AMSamsung Galaxy Watch FE Bluetooth
 5 Reasons Why I'm Excited About The Galaxy Z Flip 7 FE: Samsung's Affordable FoldableMay 14, 2025 am 05:14 AM
5 Reasons Why I'm Excited About The Galaxy Z Flip 7 FE: Samsung's Affordable FoldableMay 14, 2025 am 05:14 AMSummary The Galaxy Z Flip 7 FE is said to borrow its specifications from Samsung's 2024 flip-style flagship, the Galaxy Z Flip 6, including the scre
 Nextcloud Says Google Is Hurting Its Android AppMay 14, 2025 am 05:10 AM
Nextcloud Says Google Is Hurting Its Android AppMay 14, 2025 am 05:10 AMGoogle is reportedly blocking Nextcloud, the open-source cloud storage service, from full file access on Android devices. Nextcloud is accusing Google of anti-competitive behavior, while a fully functional version remains available through the F-Droi


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Safe Exam Browser
Safe Exam Browser is a secure browser environment for taking online exams securely. This software turns any computer into a secure workstation. It controls access to any utility and prevents students from using unauthorized resources.

VSCode Windows 64-bit Download
A free and powerful IDE editor launched by Microsoft

MantisBT
Mantis is an easy-to-deploy web-based defect tracking tool designed to aid in product defect tracking. It requires PHP, MySQL and a web server. Check out our demo and hosting services.

SAP NetWeaver Server Adapter for Eclipse
Integrate Eclipse with SAP NetWeaver application server.

SecLists
SecLists is the ultimate security tester's companion. It is a collection of various types of lists that are frequently used during security assessments, all in one place. SecLists helps make security testing more efficient and productive by conveniently providing all the lists a security tester might need. List types include usernames, passwords, URLs, fuzzing payloads, sensitive data patterns, web shells, and more. The tester can simply pull this repository onto a new test machine and he will have access to every type of list he needs.





