Maintaining web server load balancing is one of the key measures to prevent downtime. Using a load balancer is a reliable approach, with HAProxy being a highly regarded choice. Using HAProxy, you can accurately configure the load balancing method and support SSL passthrough to ensure the security of communication between the client and the server.
First discusses the importance of implementing SSL passthrough in HAProxy, followed by a detailed discussion of the steps required to implement this feature, and an example is provided for better understanding.
What is SSL pass? Why is it important?
As a load balancer, HAProxy accepts and distributes the load flowing to your web servers, distributing it among the configured servers. The load is distributed across traffic shared between client devices and backend servers. In the process of load balancing, security is crucial, and SSL is the key to ensuring security.
Ideally, SSL passthrough involves forwarding SSL/TLS traffic to your web server and distributing it to configured servers without terminating SSL/TLS at HAProxy or any other load balancer you are using connect. With SSL Passthrough, you'll enjoy better end-to-end encryption, and the client's original IP address will be preserved. Additionally, this is a recommended security measure that creates better backend server flexibility and reduces HAProxy overload.
A step-by-step guide on how to implement SSL tunneling in HAProxy
After understanding the concept of SSL passthrough and its necessity, the next step is to implement it on the HAProxy load balancer by following the prescribed steps. Follow the instructions to quickly enable SSL passthrough on your HAProxy load balancer.
Step 1: Install HAProxy
Assuming you do not have HAProxy installed. The first step is to install it before we configure it for SSL passthrough. So start by updating the repository.
$sudo apt update

Next, install HAProxy from the default repository using the following command. Note that we use Ubuntu to handle this situation:
$sudo apt install haproxy

Once you have HAProxy installed, you can achieve SSL passthrough. Read on!
Step 2: Implement SSL passthrough in HAProxy
For this step, we must access the HAProxy configuration file located in "/etc/haproxy" and edit it to specify how we want to achieve SSL passthrough. You can open the configuration file using any text editor. We used Nano in this demo.
$sudo nano/etc/haproxy/haproxy,cfg
Once you access the configuration file, there are two sections you must create: "Frontend" and "Backend". In the "Front End" you can specify which port to bind to connect to. Likewise, you must specify which protocol to use and which backend server to use to distribute the traffic.
In this case, since we want to protect the traffic, we will bind port 443 for HTTPS connections. Likewise, we specify the TCP modes in which we wish to accept HAProxy operating at the transport layer.
We also added the "tcp_request" line as a rule to specify the duration of checking SSL "hello" messages to verify that we are accepting SSL traffic. Finally, we specify the backend servers for load distribution. Our final "frontend" part looks like this:

For the "Backend" part, we set the mode to TCP. We then specify the IP address of the server used for load balancing. Make sure you replace these IPs to match your live server's IP and set the connection port to 443.
Add "option tcplog" to allow logging of tcp-related issues in a log file contained in the "global" section of the configuration file.

Step 3: Restart HAProxy and test the configuration
After editing the HAProxy configuration file, save it and exit. Restart the HAProxy service to apply the changes.

that's all! We implemented SSL passthrough in HAProxy. Try sending a stream of traffic to your web server using a command like curl and see how it responds. If SSL passthrough is implemented successfully, you will get an output showing that the connection was established through port 443, and you will be connected to the backend server. Your server will respond with the required details and give a 200 status response.

in conclusion
Implementing SSL passthrough helps create end-to-end encryption and ensures that SSL/TLS connections are maintained when load balancing occurs. To implement SSL passthrough in HAProxy, install HAProxy and edit the configuration file to specify how load balancing occurs. Please refer to this example to better understand the process.
The above is the detailed content of How to implement SSL passthrough in HAProxy. For more information, please follow other related articles on the PHP Chinese website!
 等不及通用控制?现在通过 Barrier 在 Mac、PC 之间共享键盘和鼠标Apr 14, 2023 pm 12:04 PM
等不及通用控制?现在通过 Barrier 在 Mac、PC 之间共享键盘和鼠标Apr 14, 2023 pm 12:04 PM如何使用 Barrier 在 Mac / PC 之间共享键盘和鼠标您需要确保要与其共享鼠标和键盘的计算机都在同一个网络上,并且在初始设置期间您将在不同的 Mac 之间来回切换。在此处获取最新版本的 Barrier(适用于 Mac 的 DMG,适用于 Windows 的 exe)– 将其下载到您希望能够使用键盘和鼠标的每台计算机上将 Barrier 从 DMG(或使用 exe 安装到 Windows)复制到您打算使用它的每台 Mac 上的 /Applications 文件夹,然后右键单击 Barr
 Java8(291)之后禁用了TLS1.1使JDBC无法用SSL连接SqlServer2008怎么解决May 16, 2023 pm 11:55 PM
Java8(291)之后禁用了TLS1.1使JDBC无法用SSL连接SqlServer2008怎么解决May 16, 2023 pm 11:55 PMJava8-291之后,禁用了TLS1.1,使JDBC无法用SSL连接SqlServer2008怎么办,以下是解决办法修改java.security文件1.找到jre的java.security文件如果是jre,在{JAVA_HOME}/jre/lib/security中,比如????C:\ProgramFiles\Java\jre1.8.0_301\lib\security如果是Eclipse绿色免安装便携版在安装文件夹搜索java.security,比如????xxx\plugins\org
 MySQL: SSL 连接简介及设置步骤Sep 08, 2023 pm 03:51 PM
MySQL: SSL 连接简介及设置步骤Sep 08, 2023 pm 03:51 PMMySQL:SSL连接简介及设置步骤摘要:MySQL提供了SSL(SecureSocketsLayer)连接来加密在客户端和服务器之间传输的数据。本文将介绍SSL连接的概念和作用,并提供在MySQL中设置SSL连接的步骤以及相关的代码示例。导语:随着网络和数据传输的不断扩大,数据安全性变得越来越重要。通过使用SSL连接,我们可以加
 Nginx与SSL:配置HTTPS保护Web服务器Jun 09, 2023 pm 09:24 PM
Nginx与SSL:配置HTTPS保护Web服务器Jun 09, 2023 pm 09:24 PMNginx是一个高性能的Web服务器软件,同时也是一款强大的反向代理服务器和负载均衡器。随着互联网的迅速发展,越来越多的网站开始采用SSL协议保护敏感用户数据,而Nginx也提供了强大的SSL支持,使得Web服务器的安全性能更进一步。本文将介绍如何配置Nginx以支持SSL协议,并保护Web服务器的安全性能。什么是SSL协议?SSL(SecureSocke
 如何使用Nginx代理服务器实现Web服务的动态SSL证书生成?Sep 05, 2023 pm 02:24 PM
如何使用Nginx代理服务器实现Web服务的动态SSL证书生成?Sep 05, 2023 pm 02:24 PM如何使用Nginx代理服务器实现Web服务的动态SSL证书生成?Nginx是一款高性能的开源Web服务器,可以用于代理服务器、反向代理和负载均衡等多种用途。它的灵活性使得我们可以利用其强大的功能实现动态SSL证书生成,以提供更安全、更灵活的Web服务。本文将详细介绍如何利用Nginx代理服务器实现动态SSL证书生成。首先,我们需要生成一个自签名的根证书和私钥
 修复:Windows PC 上 Chrome 中的 ERR_CERT_WEAK_SIGNATURE_ALGORITHM 错误Apr 18, 2023 am 09:41 AM
修复:Windows PC 上 Chrome 中的 ERR_CERT_WEAK_SIGNATURE_ALGORITHM 错误Apr 18, 2023 am 09:41 AM许多Windows用户最近开始抱怨一个问题,即他们在浏览chrome浏览器发现不安全的网页时收到错误消息并抛出错误消息YourconnectionisnotprivatewithaerrorcodeNET::ERR_CERT_WEAK_SIGNATURE_ALGORITHMonWindows11系统。现在Windows用户不确定是什么原因导致了这个问题,以及他们如何解决这个问题以便轻松浏览网页。下面提到了可能导致此错误消息的一些原因。SSL证书缓存问题损坏的浏览数据
 Windows环境下Nginx服务器SSL证书怎么安装部署May 15, 2023 am 09:37 AM
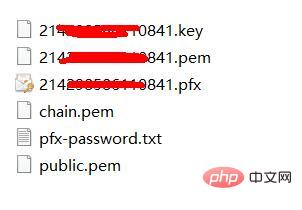
Windows环境下Nginx服务器SSL证书怎么安装部署May 15, 2023 am 09:37 AMNginx类型的服务器证书压缩包证书压缩文件夹内容如下(这里使用baidu.com的域名作为示例):baidu.com_bundle.crt证书文件baidu.com_bundle.pem证书文件(可忽略该文件)baidu.com.key私钥文件baidu.com.csrCSR文件拷贝证书文件和私钥文件将已获取到的baidu.com_bundle.crt证书文件和baidu.com.key私钥文件从本地目录拷贝到Nginx根目录下的conf目录修改nginx.conf配置编辑Nginx根目录下的
 Nginx怎么配置SSL证书监听443端口May 13, 2023 am 09:19 AM
Nginx怎么配置SSL证书监听443端口May 13, 2023 am 09:19 AM一、准备证书文件我使用的是阿里云symantec免费版ssl证书。将证书文件下载后解压得到如下文件在nginx–>cert目录中建一个ssl目录,将上面的所有文件拷贝到ssl目录中二、修改nginx.conf文件在nginx.conf的http{}中填下如下内容server{listen443;server_namewww.httpstest.com;sslon;roothtml;indexindex.htmlindex.htm;#这里的.pem/.key文件替换成自己对应的文件名ssl_


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

DVWA
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is very vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, to help web developers better understand the process of securing web applications, and to help teachers/students teach/learn in a classroom environment Web application security. The goal of DVWA is to practice some of the most common web vulnerabilities through a simple and straightforward interface, with varying degrees of difficulty. Please note that this software

EditPlus Chinese cracked version
Small size, syntax highlighting, does not support code prompt function

Dreamweaver CS6
Visual web development tools

SublimeText3 Chinese version
Chinese version, very easy to use

MantisBT
Mantis is an easy-to-deploy web-based defect tracking tool designed to aid in product defect tracking. It requires PHP, MySQL and a web server. Check out our demo and hosting services.






