BTC L2 Summer? An overview of the characteristics, advantages and disadvantages of mainstream Bitcoin second-layer protocols
- PHPzforward
- 2024-03-17 10:31:051238browse
The rise of Bitcoin Inscription has injected new vitality into the Bitcoin ecosystem and rekindled people's attention to Bitcoin. This has also given rise to many new Bitcoin second-layer projects, such as Merlin, Bison, Bouncebit, NuBit and BitLayer etc.
This article selects four relatively popular projects in the market: BEVM, Merlin, B² Network, and BounceBit for interpretation. What are the highlights and advantages of each?
Key Points
Merlin Chain, as a ZK Rollup BTC Layer 2 network, realizes the integration of BTC and The seamless mapping between EVM addresses provides users with an efficient and secure cross-chain interaction experience.
B² Network is the first network to implement ZPVC on Bitcoin, using ZK-Rollup technology and combining it with the zkEVM solution to process user transactions and output relevant certificates. B² Network's technical architecture includes the Rollup layer and the DA layer, aiming to transform Bitcoin into a feature-rich multi-platform.
BEVM is an EVM-compatible BTC Layer 2 solution that utilizes Bitcoin’s Taproot upgrade, adopts Schnorr signature and MAST technology, and supports the use of BTC as Gas, demonstrating its rich capabilities. Application scenarios and high ecosystem compatibility.
Bouncebit has built an infrastructure based on BTC heavy pledge, using dual-token PoS L1 to achieve full compatibility between Bitcoin security and EVM. This ecosystem combines CeFi with DeFi to provide BTC holders with earning opportunities across multiple networks.
Detailed introduction
Merlin Chain: Based on zkEVM technology, currently the highest TVL
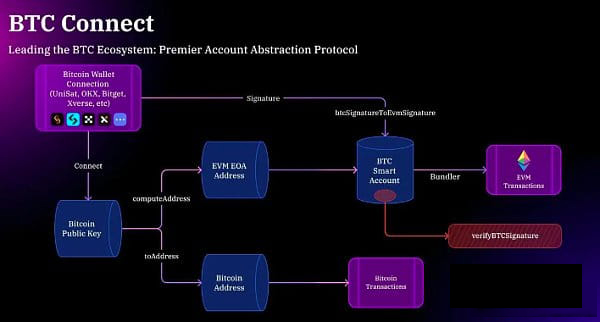
The emergence of Merlin Chain, Marking the birth of a new BTC L2 solution, it aims to improve the scalability, transaction efficiency and security of the BTC network through a series of technological innovations, while solving network congestion problems. As a ZK Rollup BTC L2 network, Merlin Chain not only supports a variety of native Bitcoin assets, but is also compatible with EVM, demonstrating a design concept that takes into account both the Bitcoin and Ethereum ecology.
The core of Merlin Chain’s technical framework lies in its chain-agnostic account system and the BTC Connect technology provided by Particle Network. These innovations not only facilitate the seamless mapping between BTC and EVM addresses, but also bring users an efficient and secure cross-chain interaction environment. With the help of multiple technical means such as smart contracts, signature abstraction, and decentralized oracles, Merlin Chain can achieve rapid bridging and transaction processing of native assets, thereby ensuring the overall security and trustworthiness of the ecosystem.
Merlin Chain developed the zkEVM Layer2 solution based on the Polygon CDK framework. It cleverly uses ZK-Rollup technology to effectively compress and verify large amounts of transaction data, greatly improving transaction processing speed and network scalability. sex. By integrating sequence nodes, Merlin Chain is able to handle higher transaction volumes. Compressed data, ZK state roots and proofs generated using zkEVM technology are securely uploaded to Bitcoin’s L1 Taproot via a decentralized oracle network, enhancing the overall transparency and security of the network.
Under the technical architecture of Polygon CDK, Merlin Chain adopts a solution called CDK Validium, which combines Polygon zkEVM technology and the concept of DAC, aiming to achieve the effectiveness of multi-signature forms on the Ethereum chain. verify. This multi-signature method echoes BTC’s Taproot technology, so the decentralized oracle on the Merlin Chain essentially serves as the DAC. The task of Merlin Chain's sequencer is to collect users' transaction data, package and verify it, and then hand it over to ZKP (zero-knowledge proof) aggregator and Prover for processing. This process is supported by Lumoz's ZK-POW function. These L2 transaction data, including hashes and signatures, are transmitted to the BTC network via a decentralized oracle network.
Through this technical layout, Merlin Chain realizes a safe and efficient cross-chain interaction method, allowing seamless connection of transaction data between BTC's L1 and L2 solutions based on zkEVM technology. This architecture not only strengthens the security and transparency of the network, but also opens up new possibilities for interoperability between Bitcoin and other blockchain ecosystems, greatly improving the overall performance and user experience of the system.
Merlin Chain has established interconnections with more than 40 public chains, simplifying the experience for users who are not familiar with BTC, allowing them to interact with familiar wallets (such as MetaMask) and assets. At the same time, Merlin is the only self-developed BTC cross-chain bridge, supporting BTC, BRC-20, BRC-420, Bitmap, Ordinals, and will soon support Atomics, Stamp and later Runes, and also supports assets such as ETH, Arbitrum, Manta, and Tron. .
B² Network: Adopting a two-layer structure, the first network to implement ZPVC Rollup

Also as BTC L2, B² Network introduces ZKP’s Rollup technology. This technology aims to increase transaction processing speed and expand the diversity of application scenarios, all without sacrificing security. B² Network has become the first network to implement Zero-Knowledge Proof Verification Commitment (ZPVC) Rollup on BTC. By adopting ZKP and Taproot's challenge-response mechanism, it not only supports Turing-complete smart contracts, but also ensures the privacy and security of transactions.
This so-called ZPVC uses ZKP to enhance the security and efficiency of BTC Layer 2. Through ZPVC, B² Network is able to take advantage of BTC’s secure consensus by ensuring the authenticity and integrity of transactions through a challenge mechanism without directly verifying each proof. This approach not only improves the efficiency of processing transactions, but also maintains the decentralized nature and security of the network.
B² Network architecture is divided into two main layers: Rollup layer and data availability (DA) layer.
The Rollup layer consists of a variety of components, including account abstraction, RPC service, Mempool, sequencer, zkEVM, aggregator, synchronizer and proof generator, etc. This layer is responsible for receiving, storing, sorting and processing user transactions, and verifying the authenticity of transactions by generating ZKP. This series of steps not only ensures the security of transactions, but also ensures the availability of data, allowing developers to build secure DApps on the B² network, including DeFi, NFT, etc., and supports migrating DApps from other EVM-compatible chains to the B² network .
The DA layer includes decentralized storage, B² nodes and the BTC network. It is mainly responsible for permanently storing Rollup data copies, verifying Rollup’s ZKP, and final confirmation on the BTC network. Decentralized storage ensures the persistence and accessibility of data; B² nodes perform various network operations, such as verification, sorting, and data packaging; the BTC network is responsible for final confirmation of transactions, ensuring the security and non-tamperability of the system. These three parts work together to greatly improve the efficiency and scalability of the network while retaining its decentralized nature.

BEVM (Bitcoin Ethereum Virtual Machine)
A decentralized, EVM-compatible BTC Layer 2 solution based on Taproot upgrades. It allows the use of BTC as gas for transactions, and allows DApps in the Ethereum ecosystem to run on the BTC network, bringing a wider range of application scenarios to BTC.
In terms of technical architecture, BEVM creates a decentralized BTC L2 solution through Taproot consensus, combining Bitcoin’s native Taproot technology stack and the BFT PoS network composed of Bitcoin SPV nodes. The Taproot consensus consists of three parts: Taproot technology (including Musig2, Schnorr signatures, MAST, etc.), a BFT PoS network composed of Bitcoin SPV, and threshold node communication formed through the Signal protocol. This architecture improves the scalability and privacy of the Bitcoin network, and at the same time improves the efficiency of Bitcoin network transactions through the batch verification processing of BEVM technology.
Schnorr signatures provide a more efficient and private way to sign, allowing the aggregation of multiple signatures, reducing transaction size and fees. MAST improves the privacy and efficiency of smart contracts by allowing contracts containing multiple execution paths to be deployed on the blockchain without only revealing the data of the actual execution paths, thereby improving data privacy and scalability. Together, these technologies improve transaction efficiency and privacy protection on BEVM. In addition, BEVM uses BTC light nodes as verification nodes and relies on network consensus to realize the management and use of BTC, thereby achieving true decentralization. The block generation node of the BEVM network also serves as the guardian node of the Bitcoin main network, automatically executing transactions through network consensus, ensuring the security and decentralization of BTC management and cross-chain processes.
In order to simplify the startup and running process of BEVM nodes, BEVM provides an intuitive and simple node deployment process through the Spheron service. Users can easily recharge Spheron wallets, select BEVM test nodes, configure recommended resources and new wallet addresses, etc., thereby ensuring smooth deployment and efficient operation of nodes.
Bouncebit: Dual Token PoS Consensus Mechanism

In Bouncebit’s official documentation, it claims to be a “PoS L1”, but it serves as a heavy pledge basis facility, which provides a base layer for different heavily collateralized products and is also considered by the market to be a unique second-tier solution.
BounceBit introduces an asset-driven PoS Layer 1 method to strengthen network security through a dual-token system of BTC and BounceBit native tokens, which is different from conventional Layer 2 solutions and enables interaction with EVM-compatible chains. Operability, combined with CeFi technology, such as Mainnet Digital custody and Ceffu's MirrorX technology, improves transaction transparency and liquidity, and enhances the flexibility and application scenarios of Bitcoin assets.
Its dual-token PoS consensus mechanism supports 50 validators, optimizing validator election and reward distribution through smart contracts and Epoch-based timelines, while allowing validators to charge commissions on rewards and balance node operating costs and benefits, jointly creating a safe and efficient blockchain ecosystem.
Summary
BEVM, Merlin Chain, B² Network and BounceBit all improve BTC’s scalability, transaction efficiency and diversity of application scenarios through unique technical solutions. BEVM is characterized by its EVM compatibility and ecosystem construction; Merlin Chain innovates in cross-chain interactive experience; B² Network strengthens transaction privacy and security through ZKP technology; and BounceBit adopts a dual-token PoS consensus mechanism and uses pledged BTC It strengthens network security with native tokens, while providing full EVM compatibility and broadening the application areas of BTC.
In addition, BTC L2 is showing a state of blooming, just like the previous ETH L2 season. In addition to the above four public chains, there are also second-layer solutions such as NuBit and BitLayer. The joint efforts of these platforms herald the future of BTC L2 solutions. It will reach new heights in scalability, transaction efficiency, security and ecosystem diversity, promoting BTC to be more widely integrated into the growing field of blockchain applications.
The above is the detailed content of BTC L2 Summer? An overview of the characteristics, advantages and disadvantages of mainstream Bitcoin second-layer protocols. For more information, please follow other related articles on the PHP Chinese website!
Related articles
See more- How to use php to develop the payment system of Ethereum
- Redis methods and application examples for implementing distributed Bitcoin wallets
- Introduction to blockchain development framework based on Go language
- Steps and Process to Buy USDT on Binance Exchange
- Binance launches Inscription Market and integrates into Bitcoin ecosystem! Web3 wallet can mint multiple inscriptions

