 Technology peripherals
Technology peripherals AI
AI Artificial Intelligence and Cybersecurity: How to Navigate Risks and Opportunities
Artificial Intelligence and Cybersecurity: How to Navigate Risks and OpportunitiesArtificial Intelligence and Cybersecurity: How to Navigate Risks and Opportunities
- In the race for artificial intelligence dominance, cybersecurity considerations have taken center stage.
- Although artificial intelligence will enhance the effectiveness of cyber attacks, its impact can be offset by using artificial intelligence technology to enhance cyber defense capabilities.
- Harnessing the benefits of artificial intelligence will require global public-private collaboration to ensure that its applications can be translated across society in a fair and safe manner.

The new technological development of artificial intelligence (AI) has swept the world, prompting governments of various countries to compete for strategic advantages, and also prompting technology companies to compete to develop new artificial intelligence system and commercialize it.
Emerging AI applications have the potential to bring numerous benefits to society, but they may also have serious security implications, ranging from national security and democratic instability to large-scale economic disruption.
The impact of artificial intelligence on cybersecurity is manifold and constantly evolving, with threat actors using these new technologies to their advantage and enhancing their cyber attack capabilities. Here are a few ways to navigate these risks and opportunities:
Navigating Risks:
- ##Privacy and Data Protection Risks: AI Technology requires a large amount of data support, and data leakage may lead to the leakage of user privacy. Encryption, anonymization and other measures should be taken to protect data security, and strict data protection policies should be formulated.
- Malicious attacks and abuse risks: Malicious use of AI technology may lead to various security threats, including the spread of false information, phishing, social engineering, etc. Monitoring and prevention of malicious behaviors should be strengthened and security incidents should be responded to in a timely manner.
- Risk of algorithmic bias and discrimination: AI algorithms may be biased and discriminatory, leading to unfair results. Algorithms should be reviewed and tested to ensure their fairness and transparency and to avoid discrimination against specific groups.
- Supply chain security risks: The supply chain of the AI system may be subject to malicious attacks, causing backdoors or malicious code to be implanted in the system. Supply chain management should be strengthened to ensure that software and hardware are obtained from trustworthy sources.
Seize the opportunity:
- Automated security defense: AI can be used to automate security defense, such as behavioral analysis, Anomaly detection, etc., to improve the efficiency and accuracy of security incident detection and response.
- Intelligent threat intelligence: AI can analyze large amounts of security data, extract key information, and generate intelligent threat intelligence to help organizations predict and respond to security threats.
- Identity authentication and access control: AI can be applied to identity authentication and access control, such as biometric identification, behavioral analysis, etc., to improve system security and user experience.
- Strengthen vulnerability management: AI can help discover and repair system vulnerabilities, improve the efficiency and timeliness of vulnerability management, and reduce potential security risks.
- Intelligent safety training: AI can be used for intelligent safety training, providing personalized training content based on employees’ needs and behavioral habits, and improving employees’ safety awareness and skills.
How does artificial intelligence enhance cybersecurity?
Artificial intelligence can enhance network security in many aspects, including but not limited to the following aspects:- Anomaly detection and behavior analysis: Artificial intelligence can analyze a large amount of network traffic and user behavior data, identify abnormal activities and potential security threats, and help timely detect and respond to attack behaviors.
- Threat intelligence analysis: Artificial intelligence can analyze threat intelligence from various sources, identify threat information related to the organization, and help the organization understand the current threat situation and take corresponding defensive measures.
- Intelligent identity authentication: Artificial intelligence can be applied to biometric identification, behavior analysis and other technologies to improve the accuracy and security of user identity authentication and prevent unauthorized access.
- Automated security response: Artificial intelligence can realize automated security incident response, automatically respond to and repair threats according to pre-set rules and policies, and improve response speed and efficiency.
- Enhanced vulnerability management: Artificial intelligence can help identify vulnerabilities in systems and applications, automate vulnerability scanning and analysis, and improve the timeliness and accuracy of vulnerability management.
- Intelligent safety training: Artificial intelligence can provide personalized safety training content based on employees’ roles and behavioral habits, helping employees improve their safety awareness and skills and reduce safety risks.
- Intelligent security prediction: Artificial intelligence can analyze big data and historical security event data, predict possible future security threats and attack trends, and help organizations prepare in advance.
To sum up, artificial intelligence plays a key role in network security, helping to enhance security protection and countermeasures, helping to reduce security risks and losses.
The above is the detailed content of Artificial Intelligence and Cybersecurity: How to Navigate Risks and Opportunities. For more information, please follow other related articles on the PHP Chinese website!
 How to Run LLM Locally Using LM Studio? - Analytics VidhyaApr 19, 2025 am 11:38 AM
How to Run LLM Locally Using LM Studio? - Analytics VidhyaApr 19, 2025 am 11:38 AMRunning large language models at home with ease: LM Studio User Guide In recent years, advances in software and hardware have made it possible to run large language models (LLMs) on personal computers. LM Studio is an excellent tool to make this process easy and convenient. This article will dive into how to run LLM locally using LM Studio, covering key steps, potential challenges, and the benefits of having LLM locally. Whether you are a tech enthusiast or are curious about the latest AI technologies, this guide will provide valuable insights and practical tips. Let's get started! Overview Understand the basic requirements for running LLM locally. Set up LM Studi on your computer
 Guy Peri Helps Flavor McCormick's Future Through Data TransformationApr 19, 2025 am 11:35 AM
Guy Peri Helps Flavor McCormick's Future Through Data TransformationApr 19, 2025 am 11:35 AMGuy Peri is McCormick’s Chief Information and Digital Officer. Though only seven months into his role, Peri is rapidly advancing a comprehensive transformation of the company’s digital capabilities. His career-long focus on data and analytics informs
 What is the Chain of Emotion in Prompt Engineering? - Analytics VidhyaApr 19, 2025 am 11:33 AM
What is the Chain of Emotion in Prompt Engineering? - Analytics VidhyaApr 19, 2025 am 11:33 AMIntroduction Artificial intelligence (AI) is evolving to understand not just words, but also emotions, responding with a human touch. This sophisticated interaction is crucial in the rapidly advancing field of AI and natural language processing. Th
 12 Best AI Tools for Data Science Workflow - Analytics VidhyaApr 19, 2025 am 11:31 AM
12 Best AI Tools for Data Science Workflow - Analytics VidhyaApr 19, 2025 am 11:31 AMIntroduction In today's data-centric world, leveraging advanced AI technologies is crucial for businesses seeking a competitive edge and enhanced efficiency. A range of powerful tools empowers data scientists, analysts, and developers to build, depl
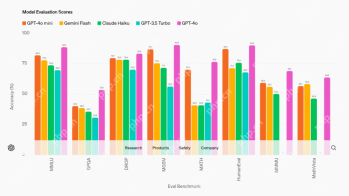 AV Byte: OpenAI's GPT-4o Mini and Other AI InnovationsApr 19, 2025 am 11:30 AM
AV Byte: OpenAI's GPT-4o Mini and Other AI InnovationsApr 19, 2025 am 11:30 AMThis week's AI landscape exploded with groundbreaking releases from industry giants like OpenAI, Mistral AI, NVIDIA, DeepSeek, and Hugging Face. These new models promise increased power, affordability, and accessibility, fueled by advancements in tr
 Perplexity's Android App Is Infested With Security Flaws, Report FindsApr 19, 2025 am 11:24 AM
Perplexity's Android App Is Infested With Security Flaws, Report FindsApr 19, 2025 am 11:24 AMBut the company’s Android app, which offers not only search capabilities but also acts as an AI assistant, is riddled with a host of security issues that could expose its users to data theft, account takeovers and impersonation attacks from malicious
 Everyone's Getting Better At Using AI: Thoughts On Vibe CodingApr 19, 2025 am 11:17 AM
Everyone's Getting Better At Using AI: Thoughts On Vibe CodingApr 19, 2025 am 11:17 AMYou can look at what’s happening in conferences and at trade shows. You can ask engineers what they’re doing, or consult with a CEO. Everywhere you look, things are changing at breakneck speed. Engineers, and Non-Engineers What’s the difference be
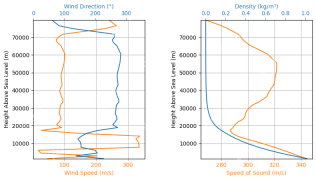 Rocket Launch Simulation and Analysis using RocketPy - Analytics VidhyaApr 19, 2025 am 11:12 AM
Rocket Launch Simulation and Analysis using RocketPy - Analytics VidhyaApr 19, 2025 am 11:12 AMSimulate Rocket Launches with RocketPy: A Comprehensive Guide This article guides you through simulating high-power rocket launches using RocketPy, a powerful Python library. We'll cover everything from defining rocket components to analyzing simula


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Atom editor mac version download
The most popular open source editor

SublimeText3 Linux new version
SublimeText3 Linux latest version

SublimeText3 Mac version
God-level code editing software (SublimeText3)

SublimeText3 English version
Recommended: Win version, supports code prompts!

SAP NetWeaver Server Adapter for Eclipse
Integrate Eclipse with SAP NetWeaver application server.





