 Technology peripherals
Technology peripherals AI
AI ICLR 2024 Oral: Noise correlation learning in long videos, single-card training only takes 1 day
ICLR 2024 Oral: Noise correlation learning in long videos, single-card training only takes 1 dayICLR 2024 Oral: Noise correlation learning in long videos, single-card training only takes 1 day

Paper title: Multi-granularity Correspondence Learning from Long-term Noisy Videos Paper address: https://openreview.net/pdf?id=9Cu8MRmhq2 Project address: https://lin-yijie.github.io/projects/Norton Code address: https://github.com/XLearning-SCU/2024-ICLR-Norton


Coarse-grained NC (between Clip-Caption). Coarse-grained NC includes two categories: asynchronous (Asynchronous) and irrelevant (Irrelevant). The difference lies in whether the video clip or title can correspond to an existing title or video clip. "Asynchronous" refers to the timing misalignment between the video clip and the title, such as t1 in Figure 2. This results in a mismatch between the sequence of statements and actions, as the narrator explains before and after the actions are actually performed. "Irrelevant" refers to meaningless titles that cannot be aligned with the video clips (such as t2 and t6), or irrelevant video clips. According to relevant research by the Oxford Visual Geometry Group [5], only about 30% of the video clips and titles in the HowTo100M dataset are visually aligned, and only 15% are originally aligned; Fine-grained NC (Frame-Word). For a video clip, only part of the text description may be relevant to it. In Figure 2, the title t5 "Sprinkle sugar on it" is strongly related to the visual content v5, but the action "Observe the glaze peeling off" is not related to the visual content. Irrelevant words or video frames may hinder the extraction of key information, affecting the alignment between segments and titles.

Oriented to fine-grained NC. The researchers use log-sum-exp approximation as the soft-maximum operator to identify keywords and key frames in frame-word and word-frame alignment, realize important information extraction in a fine-grained interactive manner, and accumulate segment-title similarities. sex. For coarse-grained asynchronous NC. The researchers used the optimal transmission distance as the distance metric between video clips and titles. Given a video clip-text title similarity matrix  , where
, where  represents the number of clips and titles, the optimal transmission goal is to maximize the overall alignment similarity, which can naturally handle timing asynchronous or one-to-many (such as t3 Corresponding to v4, v5) complex alignment situation.
represents the number of clips and titles, the optimal transmission goal is to maximize the overall alignment similarity, which can naturally handle timing asynchronous or one-to-many (such as t3 Corresponding to v4, v5) complex alignment situation.

 is uniform distribution giving equal weight to each segment and title,
is uniform distribution giving equal weight to each segment and title,  is the transmission assignment or realignment moment, which can be solved by the Sinkhorn algorithm.
is the transmission assignment or realignment moment, which can be solved by the Sinkhorn algorithm. Oriented to coarse-grained irrelevant NC. Inspired by SuperGlue [6] in feature matching, we design an adaptive alignable hint bucket to try to filter irrelevant segments and titles. The prompt bucket is a vector of the same value in one row and one column, spliced on the similarity matrix  , and its value represents the similarity threshold of whether it can be aligned. Tip Buckets integrate seamlessly into the Optimal Transport Sinkhorn solver.
, and its value represents the similarity threshold of whether it can be aligned. Tip Buckets integrate seamlessly into the Optimal Transport Sinkhorn solver.

 represents the similarity matrix between the
represents the similarity matrix between the  th long video and the
th long video and the  th text paragraph.
th text paragraph. 

 represents the number of all video clips and titles in the training batch, the identity matrix
represents the number of all video clips and titles in the training batch, the identity matrix  represents the standard alignment target in the contrastive learning cross-entropy loss,
represents the standard alignment target in the contrastive learning cross-entropy loss,  represents the realignment target after incorporating the optimal transmission correction target
represents the realignment target after incorporating the optimal transmission correction target  ,
,  is the weight coefficient.
is the weight coefficient. 

The above is the detailed content of ICLR 2024 Oral: Noise correlation learning in long videos, single-card training only takes 1 day. For more information, please follow other related articles on the PHP Chinese website!
 How to Run LLM Locally Using LM Studio? - Analytics VidhyaApr 19, 2025 am 11:38 AM
How to Run LLM Locally Using LM Studio? - Analytics VidhyaApr 19, 2025 am 11:38 AMRunning large language models at home with ease: LM Studio User Guide In recent years, advances in software and hardware have made it possible to run large language models (LLMs) on personal computers. LM Studio is an excellent tool to make this process easy and convenient. This article will dive into how to run LLM locally using LM Studio, covering key steps, potential challenges, and the benefits of having LLM locally. Whether you are a tech enthusiast or are curious about the latest AI technologies, this guide will provide valuable insights and practical tips. Let's get started! Overview Understand the basic requirements for running LLM locally. Set up LM Studi on your computer
 Guy Peri Helps Flavor McCormick's Future Through Data TransformationApr 19, 2025 am 11:35 AM
Guy Peri Helps Flavor McCormick's Future Through Data TransformationApr 19, 2025 am 11:35 AMGuy Peri is McCormick’s Chief Information and Digital Officer. Though only seven months into his role, Peri is rapidly advancing a comprehensive transformation of the company’s digital capabilities. His career-long focus on data and analytics informs
 What is the Chain of Emotion in Prompt Engineering? - Analytics VidhyaApr 19, 2025 am 11:33 AM
What is the Chain of Emotion in Prompt Engineering? - Analytics VidhyaApr 19, 2025 am 11:33 AMIntroduction Artificial intelligence (AI) is evolving to understand not just words, but also emotions, responding with a human touch. This sophisticated interaction is crucial in the rapidly advancing field of AI and natural language processing. Th
 12 Best AI Tools for Data Science Workflow - Analytics VidhyaApr 19, 2025 am 11:31 AM
12 Best AI Tools for Data Science Workflow - Analytics VidhyaApr 19, 2025 am 11:31 AMIntroduction In today's data-centric world, leveraging advanced AI technologies is crucial for businesses seeking a competitive edge and enhanced efficiency. A range of powerful tools empowers data scientists, analysts, and developers to build, depl
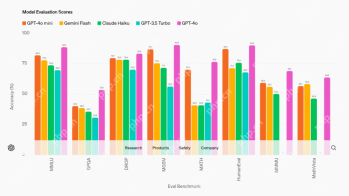 AV Byte: OpenAI's GPT-4o Mini and Other AI InnovationsApr 19, 2025 am 11:30 AM
AV Byte: OpenAI's GPT-4o Mini and Other AI InnovationsApr 19, 2025 am 11:30 AMThis week's AI landscape exploded with groundbreaking releases from industry giants like OpenAI, Mistral AI, NVIDIA, DeepSeek, and Hugging Face. These new models promise increased power, affordability, and accessibility, fueled by advancements in tr
 Perplexity's Android App Is Infested With Security Flaws, Report FindsApr 19, 2025 am 11:24 AM
Perplexity's Android App Is Infested With Security Flaws, Report FindsApr 19, 2025 am 11:24 AMBut the company’s Android app, which offers not only search capabilities but also acts as an AI assistant, is riddled with a host of security issues that could expose its users to data theft, account takeovers and impersonation attacks from malicious
 Everyone's Getting Better At Using AI: Thoughts On Vibe CodingApr 19, 2025 am 11:17 AM
Everyone's Getting Better At Using AI: Thoughts On Vibe CodingApr 19, 2025 am 11:17 AMYou can look at what’s happening in conferences and at trade shows. You can ask engineers what they’re doing, or consult with a CEO. Everywhere you look, things are changing at breakneck speed. Engineers, and Non-Engineers What’s the difference be
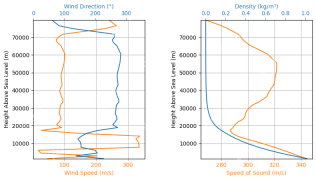 Rocket Launch Simulation and Analysis using RocketPy - Analytics VidhyaApr 19, 2025 am 11:12 AM
Rocket Launch Simulation and Analysis using RocketPy - Analytics VidhyaApr 19, 2025 am 11:12 AMSimulate Rocket Launches with RocketPy: A Comprehensive Guide This article guides you through simulating high-power rocket launches using RocketPy, a powerful Python library. We'll cover everything from defining rocket components to analyzing simula


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

SublimeText3 Linux new version
SublimeText3 Linux latest version

Dreamweaver Mac version
Visual web development tools

ZendStudio 13.5.1 Mac
Powerful PHP integrated development environment

SecLists
SecLists is the ultimate security tester's companion. It is a collection of various types of lists that are frequently used during security assessments, all in one place. SecLists helps make security testing more efficient and productive by conveniently providing all the lists a security tester might need. List types include usernames, passwords, URLs, fuzzing payloads, sensitive data patterns, web shells, and more. The tester can simply pull this repository onto a new test machine and he will have access to every type of list he needs.

SublimeText3 Mac version
God-level code editing software (SublimeText3)


 , where
, where  represents the number of clips and titles, the optimal transmission goal is to maximize the overall alignment similarity, which can naturally handle timing asynchronous or one-to-many (such as t3 Corresponding to v4, v5) complex alignment situation.
represents the number of clips and titles, the optimal transmission goal is to maximize the overall alignment similarity, which can naturally handle timing asynchronous or one-to-many (such as t3 Corresponding to v4, v5) complex alignment situation.  , and its value represents the similarity threshold of whether it can be aligned. Tip Buckets integrate seamlessly into the Optimal Transport Sinkhorn solver.
, and its value represents the similarity threshold of whether it can be aligned. Tip Buckets integrate seamlessly into the Optimal Transport Sinkhorn solver. 

