The Vanishing Mango: Understanding the MangoFarmSOL Exit Scam
- 王林forward
- 2024-03-01 12:52:181004browse
php Editor Baicao will take you through the entire process of MangoFarmSOL exiting the scam. Recently, the MangoFarmSOL project suddenly announced its closure, and many investors faced losses. This incident has aroused widespread attention and heated discussion. What is the truth hidden behind it? Let us uncover this mystery together and explore the story behind the disappearing mango.
Event Overview
MangoFarmSOL positions itself as a staking protocol on the Solana network, encouraging users to earn rewards for depositing SOL. The project gained attention from the Solana community by promising an airdrop on January 10th.
However, the promise of January 10 was never fulfilled. On January 6, 2024, MangoFarmSOL implemented an exit scam, transferring 13,512 SOLs deposited by users from the project contract (approximately US$1.26 million at the time), and deployed a malicious front end to mislead users to authorize "emergency migration" and here Approximately $60,000 was stolen. This is the largest exit scam we’ve uncovered so far in 2024.
Subsequently, MangoFarmSOL closed its social accounts and website.
Similar to the previously reported xKingdom incident, this incident once again highlights the risk of exit scams in the DeFi field, emphasizing the importance of users’ KYC on the team and the need to remain vigilant.
Scam Timeline
Step One: Lay the Trap
① On January 3, the project used social media KOL promotion to increase its credibility and attract more users.
On January 5, the team announced plans to conduct a MANGO token airdrop on January 10, and encouraged users to participate by staking SOL and recommending other users to receive additional rewards.
Users will start depositing SOL into the MangoFarmSOL contract from January 3 to January 7. Thanks to the MANGO token airdrop commitment and the impact of online marketing, the protocol’s TVL exceeded $1.3 million.
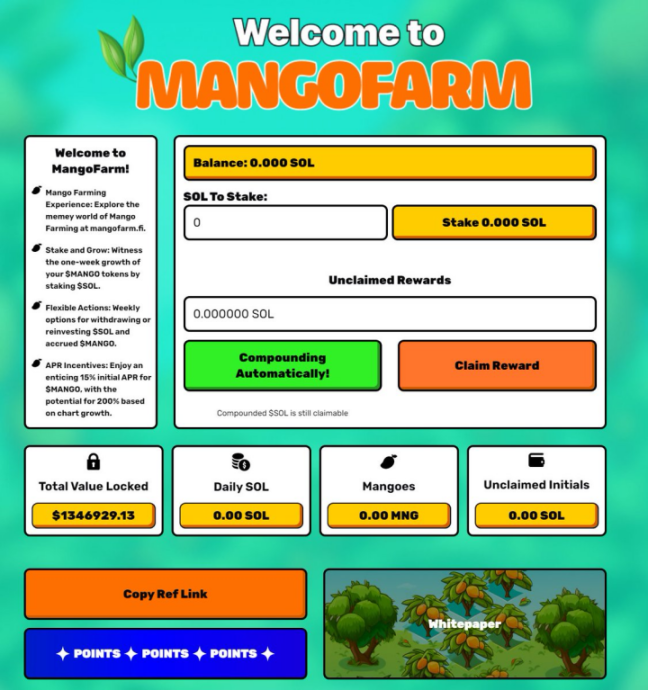
Step 2: Implement the scam
① Stealing contract funds: The MangoFarmSOL team launched a scam and deposited users into the Mango contract 13,514 SOL (approximately $1.26 million) was withdrawn to wallet 8ggvi.

First transaction: 135 SOL transferred from Mango contract (Bfg5SM) to wallet 8ggvi.
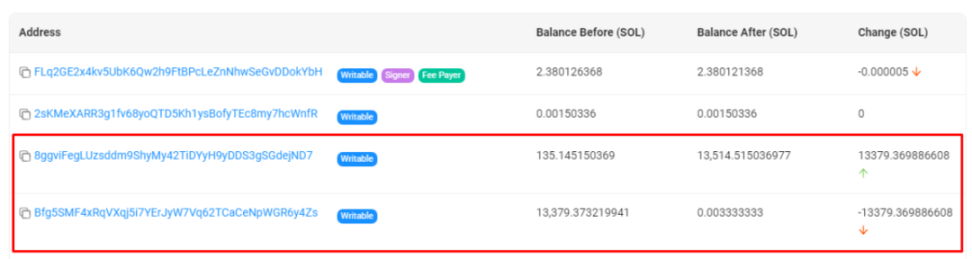
Second transaction: 13,379 SOL transferred from Mango contract (Bfg5SM) to wallet 8ggvi.
② Deploying a malicious front-end to commit fraud again: Subsequently, the team also used the previous theft incident to deploy a front-end containing malicious code under the guise of "emergency migration". The project's official social media account also posted the malicious frontend, tricking users into conducting transactions that resulted in the theft of approximately $60,000 in additional assets.
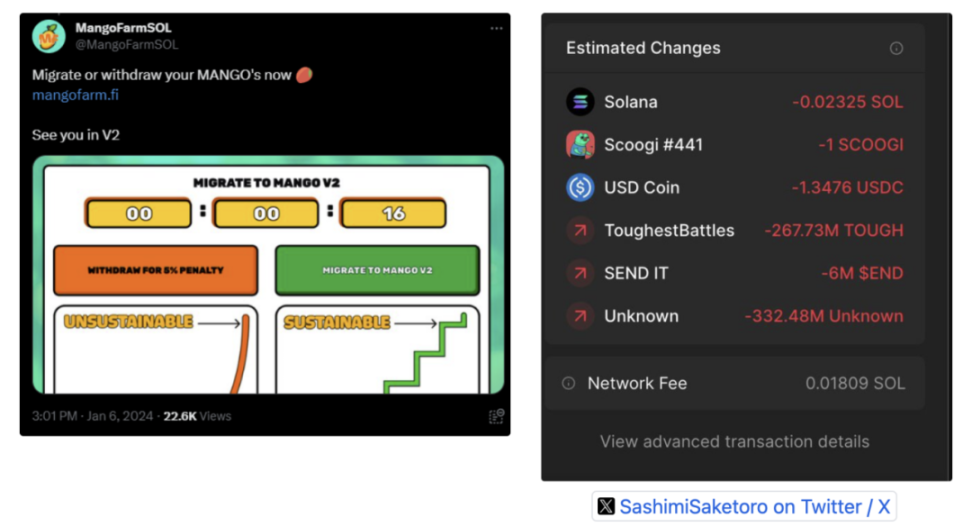
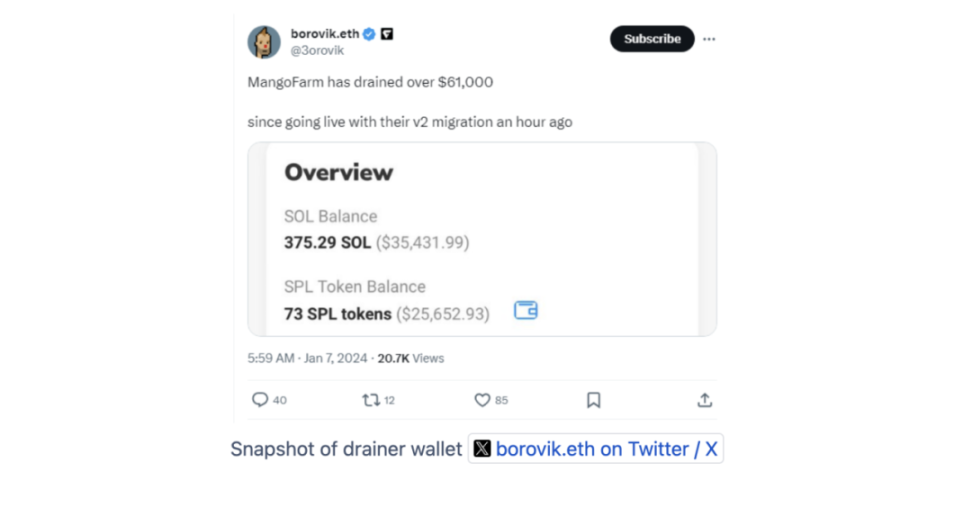 ③ Complete disappearance: MangoFarmSOL subsequently deactivated its social media accounts and closed its official website, and began transferring funds.
③ Complete disappearance: MangoFarmSOL subsequently deactivated its social media accounts and closed its official website, and began transferring funds.
Step Three: Fund Transfer
Mango Contract Stolen Fund Flow
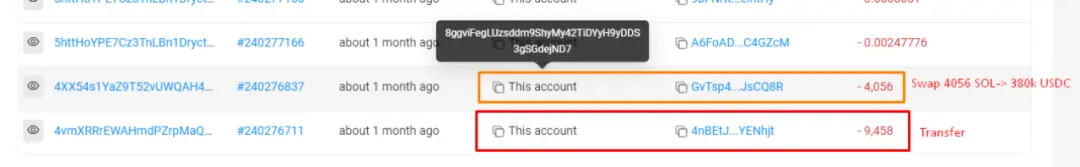
① Initial Transfer: Mango There are a total of 13.5K SOL in the contract, worth approximately US$1.26 million. After being stolen, they were sent to the address 8ggvi....ejND7.
② Mixing & Conversion: Next, 9,458 SOL were sent to 4nBETJ to obfuscate the funding link; all SOL in 8ggvi and 4nBE were subsequently converted to USDC.
③ Cross-chain to Ethereum: These USDC are cross-chained from the Solana network to Ethereum through Wormhole, and these USDC are sent to 4 different ETH through multiple transactions address.
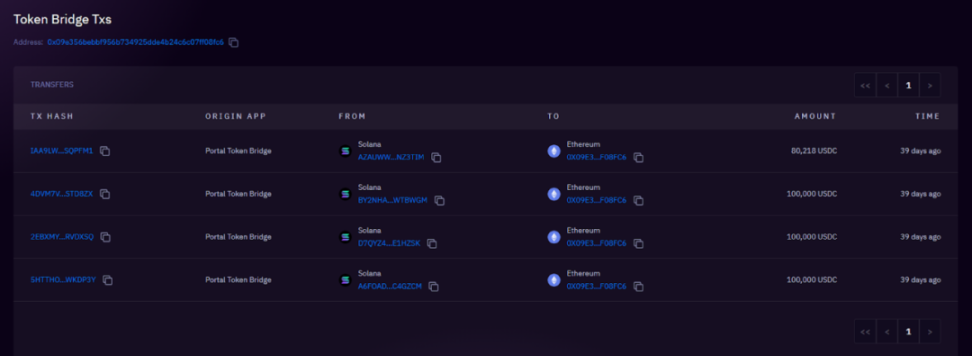 380k USDC cross-chain to 0x09e3 after 4 transactions
380k USDC cross-chain to 0x09e3 after 4 transactions
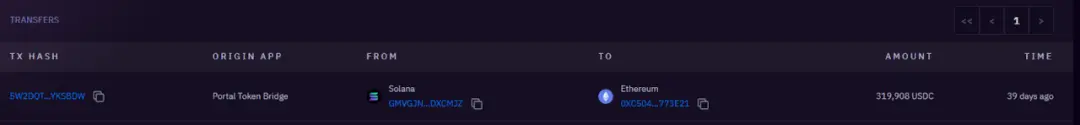 319k USDC cross-chain to 0xc504
319k USDC cross-chain to 0xc504
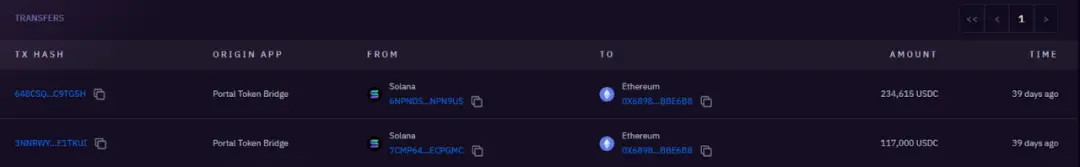 ##351k USDC cross-chain to 0x6898
##351k USDC cross-chain to 0x6898
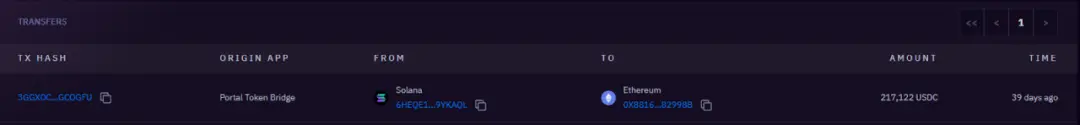 217k USDC cross-chain to 0x8816
217k USDC cross-chain to 0x8816
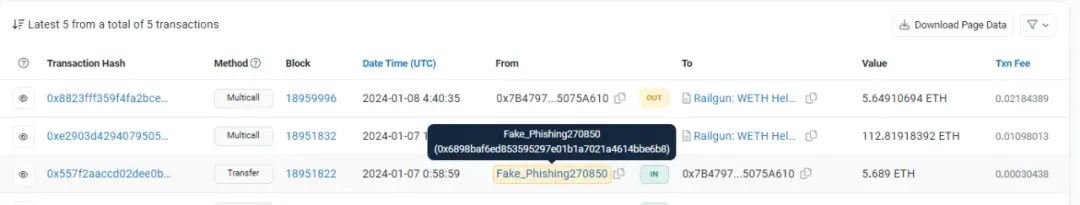 Transaction example transferred to Railgun
Transaction example transferred to Railgun
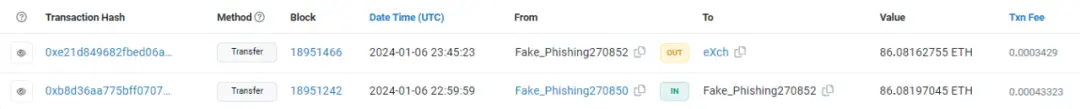
Transferred to eXch’s transaction example
Flow of funds stolen by malicious front-end① Integration and conversion: User assets stolen through the malicious front-end are integrated into SOL and then converted into approximately 5.86 million USDC.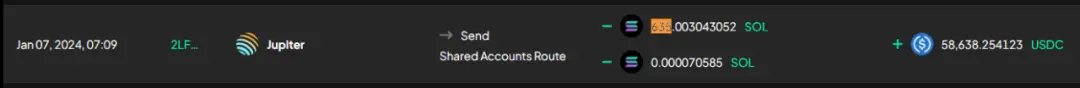
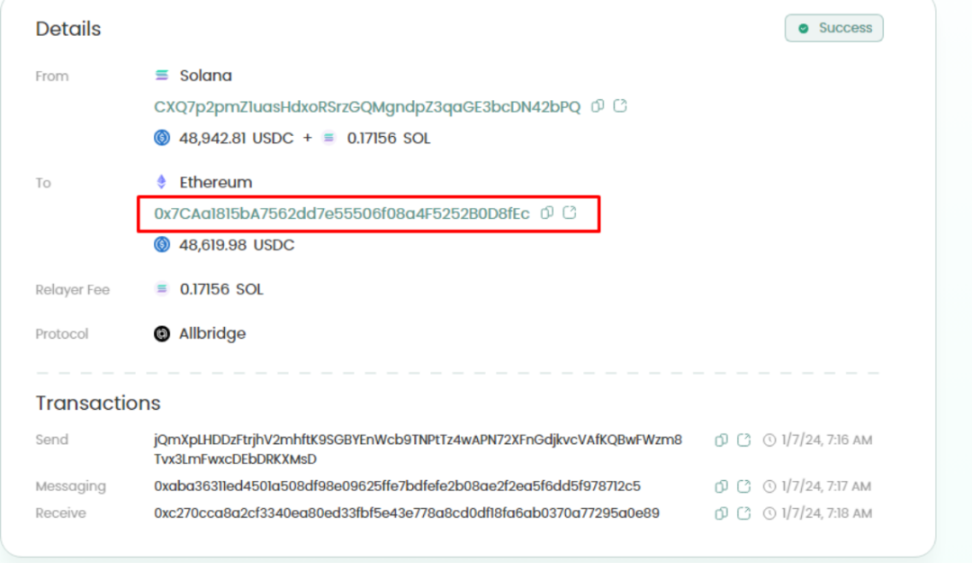
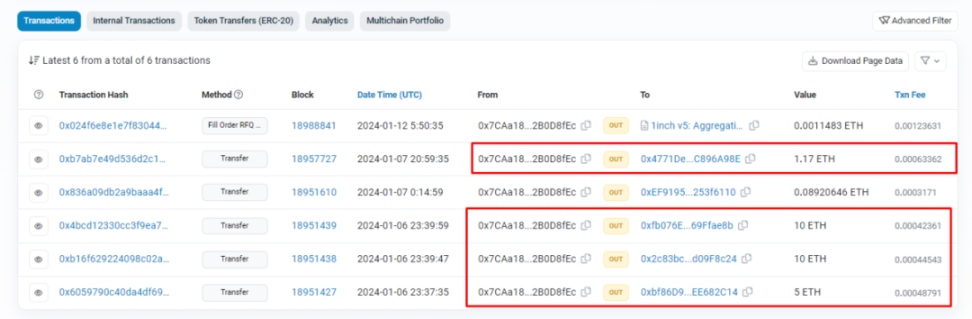
- eXch: About 292ETH
- Railgun: About 263ETH
- FixedFloat: About 26ETH
The above is the detailed content of The Vanishing Mango: Understanding the MangoFarmSOL Exit Scam. For more information, please follow other related articles on the PHP Chinese website!
Related articles
See more- Solution to the problem of vue router routing parameters disappearing after refreshing
- golang Ethereum transfer
- How to display active status on Mango TV
- After the Cancun upgrade, will the gas fee of Ethereum L2 really be reduced by more than 90%?
- S&P Ratings: Ethereum spot ETF integration of pledges may lead to the risk of pledge concentration

