
MyBatis Protection Guide: Protect the system from SQL injection threats
SQL injection is a common attack method. By constructing malicious SQL statements in the application, Attackers can bypass authentication, access controls, and even tamper with database contents. In order to ensure the security of the system, developers need to pay attention to preventing SQL injection attacks when using MyBatis. This article will introduce how to avoid SQL injection attacks in MyBatis and provide specific code examples.
- Use parameterized queries
Parameterized queries are one of the effective ways to prevent SQL injection attacks. SQL injection attacks can be effectively prevented by passing user-entered data as parameters to the SQL query statement instead of directly splicing it into the SQL statement. In MyBatis, you can use #{parameter name} to set parameters to ensure that parameter values will be safely escaped and processed.
Sample code:
@Select("SELECT * FROM users WHERE username = #{username} AND password = #{password}")
User getUserByUsernameAndPassword(@Param("username") String username, @Param("password") String password);In the above example, #{username} and #{password} are used to quote parameters. MyBatis will automatically help escape special characters to avoid SQL injection attacks. .
- Using dynamic SQL
Dynamic SQL is a flexible way provided by MyBatis that can dynamically generate SQL statements based on conditions. When writing dynamic SQL, you should avoid directly splicing user-entered data, and instead use the dynamic tags provided by MyBatis to handle conditions. This can effectively reduce the risk of SQL injection attacks.
Sample code:
<select id="getUserByUsername" parameterType="String" resultType="User">
SELECT * FROM users
WHERE 1=1
<if test="username != null">
AND username = #{username}
</if>
</select>In the above example, SQL statements are dynamically generated based on the username parameter entered by the user, and the conditions are judged through the
- Use secure database access permissions
In addition to code-level protection measures, measures should also be taken at the database level to limit user access permissions to prevent attackers from using SQL Injection to obtain sensitive data. It is recommended to assign database users the minimum necessary permissions and strictly control access rights.
Summary:
When using MyBatis to develop applications, you must always pay attention to preventing SQL injection attacks. Adopting measures such as parameterized queries, dynamic SQL, and controlling database access permissions can effectively improve the security of the system and avoid security issues caused by SQL injection. We hope that the protection guidelines and code examples provided in this article can help developers better ensure system security.
The above is the detailed content of MyBatis protection strategy: Ensure the system resists SQL injection attacks. For more information, please follow other related articles on the PHP Chinese website!
 Java之Mybatis的二级缓存怎么使用May 24, 2023 pm 06:16 PM
Java之Mybatis的二级缓存怎么使用May 24, 2023 pm 06:16 PM缓存的概述和分类概述缓存就是一块内存空间.保存临时数据为什么使用缓存将数据源(数据库或者文件)中的数据读取出来存放到缓存中,再次获取的时候,直接从缓存中获取,可以减少和数据库交互的次数,这样可以提升程序的性能!缓存的适用情况适用于缓存的:经常查询但不经常修改的(eg:省市,类别数据),数据的正确与否对最终结果影响不大的不适用缓存的:经常改变的数据,敏感数据(例如:股市的牌价,银行的汇率,银行卡里面的钱)等等MyBatis缓存类别一级缓存:它是sqlSession对象的缓存,自带的(不需要配置)不
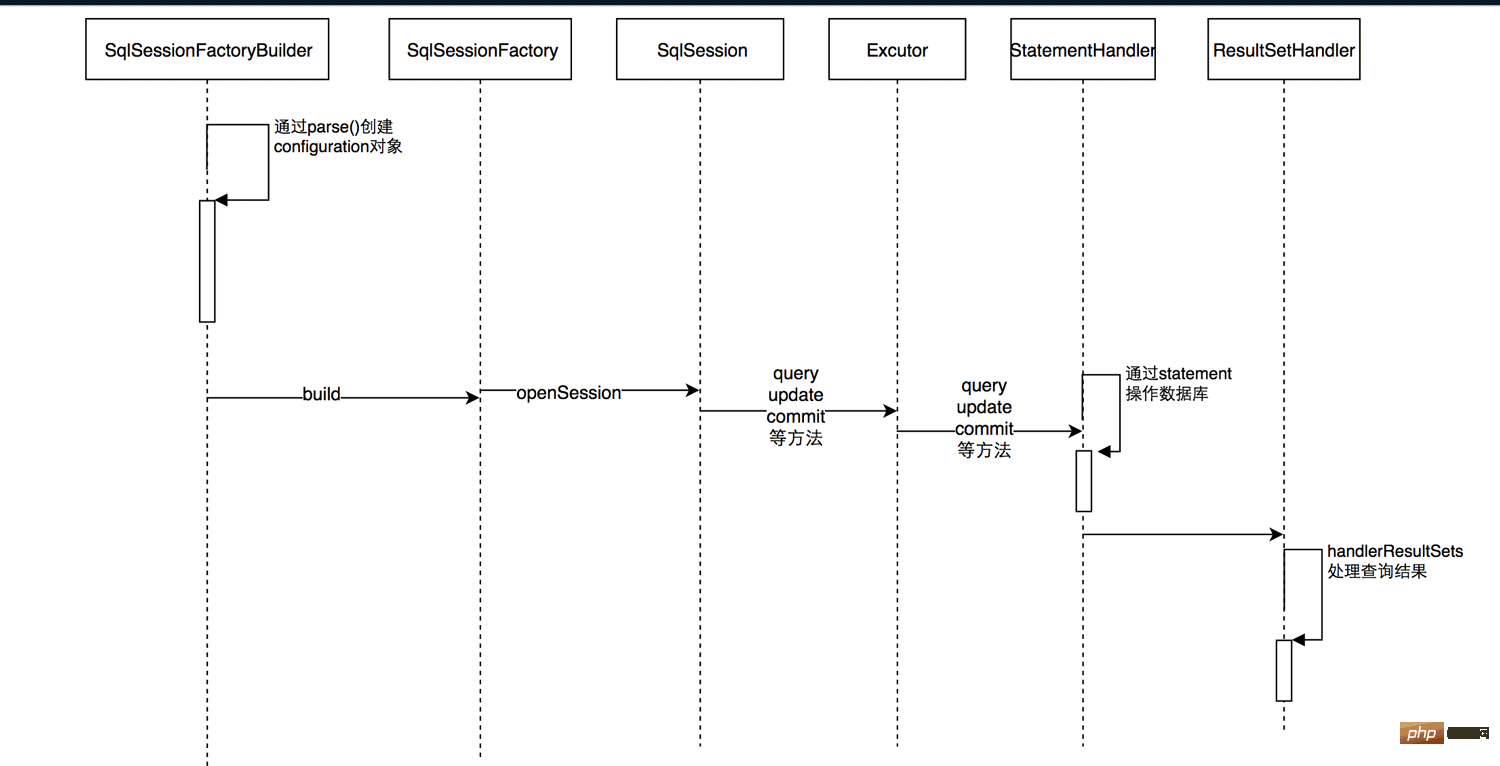 怎么使用springboot+mybatis拦截器实现水平分表May 14, 2023 pm 06:43 PM
怎么使用springboot+mybatis拦截器实现水平分表May 14, 2023 pm 06:43 PMMyBatis允许使用插件来拦截的方法Executor(update,query,flushStatements,commit,rollback,getTransaction,close,isClosed)ParameterHandler(getParameterObject,setParameters)ResultSetHandler(handleResultSets,handleOutputParameters)StatementHandler(prepare,parameterize,ba
 mybatis分页的几种方式Jan 04, 2023 pm 04:23 PM
mybatis分页的几种方式Jan 04, 2023 pm 04:23 PMmybatis分页的方式:1、借助数组进行分页,首先查询出全部数据,然后再list中截取需要的部分。2、借助Sql语句进行分页,在sql语句后面添加limit分页语句即可。3、利用拦截器分页,通过拦截器给sql语句末尾加上limit语句来分页查询。4、利用RowBounds实现分页,需要一次获取所有符合条件的数据,然后在内存中对大数据进行操作即可实现分页效果。
 springboot怎么整合mybatis分页拦截器May 13, 2023 pm 04:31 PM
springboot怎么整合mybatis分页拦截器May 13, 2023 pm 04:31 PM简介今天开发时想将自己写好的代码拿来优化,因为不想在开发服弄,怕搞坏了到时候GIT到生产服一大堆问题,然后把它分离到我轮子(工具)项目上,最后运行后发现我获取List的时候很卡至少10秒,我惊了平时也就我的正常版本是800ms左右(不要看它很久,因为数据量很大,也很正常。),前提是我也知道很慢,就等的确需要优化时,我在放出我优化的plus版本,回到10秒哪里,最开始我刚刚接到这个app项目时,在我用PageHelper.startPage(page,num);(分页),还没等查到的数据封装(Pa
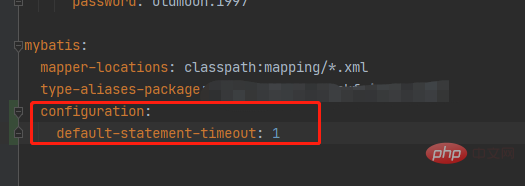 springboot配置mybatis的sql执行超时时间怎么解决May 15, 2023 pm 06:10 PM
springboot配置mybatis的sql执行超时时间怎么解决May 15, 2023 pm 06:10 PM当某些sql因为不知名原因堵塞时,为了不影响后台服务运行,想要给sql增加执行时间限制,超时后就抛异常,保证后台线程不会因为sql堵塞而堵塞。一、yml全局配置单数据源可以,多数据源时会失效二、java配置类配置成功抛出超时异常。importcom.alibaba.druid.pool.DruidDataSource;importcom.alibaba.druid.spring.boot.autoconfigure.DruidDataSourceBuilder;importorg.apache.
 mybatis怎么调用mysql存储过程并获取返回值May 27, 2023 am 09:01 AM
mybatis怎么调用mysql存储过程并获取返回值May 27, 2023 am 09:01 AMmybatis调用mysql存储过程并获取返回值1、mysql创建存储过程#结束符号默认;,delimiter$$语句表示结束符号变更为$$delimiter$$CREATEPROCEDURE`demo`(INinStrVARCHAR(100),outourStrVARCHAR(4000))BEGINSETourStr='01';if(inStr=='02')thensetourStr='02';en
 SpringBoot怎么打印mybatis的执行sql问题May 15, 2023 pm 10:55 PM
SpringBoot怎么打印mybatis的执行sql问题May 15, 2023 pm 10:55 PMSpringBoot打印mybatis的执行sql1、使用场景应为在开发过程之中跟踪后端SQL语句,因什么原因导致的错误。需要在Debug过程之中打印出执行的SQL语句。所以需要配置一下SpringBoot之中,Mybatis打印SQL语句。2、具体实现application.properties(yml)中配置的两种方式:1.logging.level.dao包名(daopackage)=debug2.mybatis.configuration.log-impl=org.apache.ibat
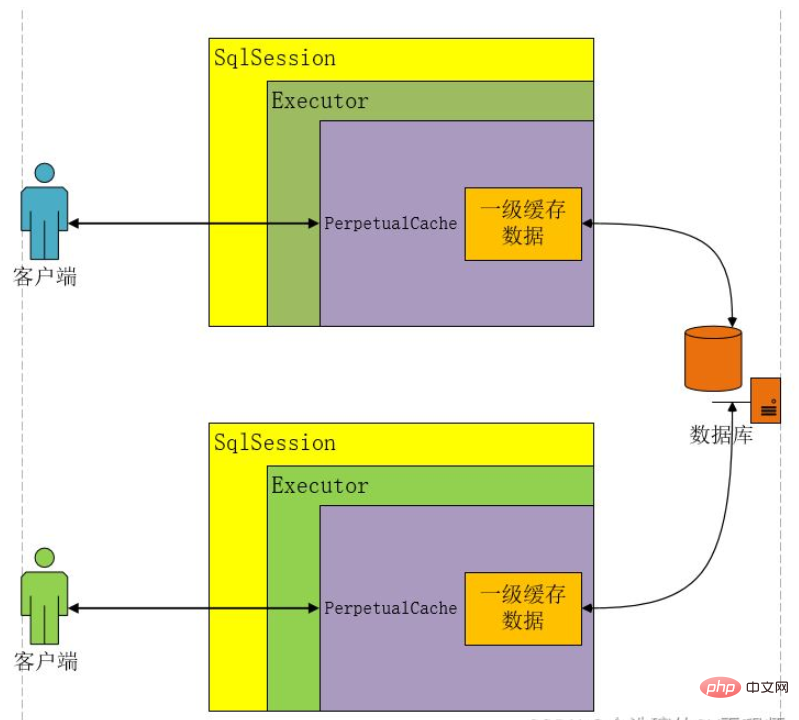 Java Mybatis一级缓存和二级缓存是什么Apr 25, 2023 pm 02:10 PM
Java Mybatis一级缓存和二级缓存是什么Apr 25, 2023 pm 02:10 PM一、什么是缓存缓存是内存当中一块存储数据的区域,目的是提高查询效率。MyBatis会将查询结果存储在缓存当中,当下次执行相同的SQL时不访问数据库,而是直接从缓存中获取结果,从而减少服务器的压力。什么是缓存?存在于内存中的一块数据。缓存有什么作用?减少程序和数据库的交互,提高查询效率,降低服务器和数据库的压力。什么样的数据使用缓存?经常查询但不常改变的,改变后对结果影响不大的数据。MyBatis缓存分为哪几类?一级缓存和二级缓存如何判断两次Sql是相同的?查询的Sql语句相同传递的参数值相同对结


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Dreamweaver Mac version
Visual web development tools

mPDF
mPDF is a PHP library that can generate PDF files from UTF-8 encoded HTML. The original author, Ian Back, wrote mPDF to output PDF files "on the fly" from his website and handle different languages. It is slower than original scripts like HTML2FPDF and produces larger files when using Unicode fonts, but supports CSS styles etc. and has a lot of enhancements. Supports almost all languages, including RTL (Arabic and Hebrew) and CJK (Chinese, Japanese and Korean). Supports nested block-level elements (such as P, DIV),

PhpStorm Mac version
The latest (2018.2.1) professional PHP integrated development tool

SublimeText3 Chinese version
Chinese version, very easy to use

MinGW - Minimalist GNU for Windows
This project is in the process of being migrated to osdn.net/projects/mingw, you can continue to follow us there. MinGW: A native Windows port of the GNU Compiler Collection (GCC), freely distributable import libraries and header files for building native Windows applications; includes extensions to the MSVC runtime to support C99 functionality. All MinGW software can run on 64-bit Windows platforms.






