 Java
Java javaTutorial
javaTutorial log4j vulnerability repair tutorial: guide you step by step to repair log4j vulnerabilities
log4j vulnerability repair tutorial: guide you step by step to repair log4j vulnerabilities
log4j vulnerability repair tutorial: Detailed guide to repair log4j vulnerability step by step, specific code examples are required
Introduction
Recently, "log4j vulnerability" (also known as CVE-2021-44228 vulnerability) has caused widespread attention and concern around the world. This vulnerability poses a serious security risk to applications that use the Apache Log4j logging library. An attacker can use this vulnerability to remotely execute malicious code, resulting in complete control of the system. This article will provide you with a detailed log4j vulnerability repair tutorial to help you ensure the security of your application.
- Detecting vulnerabilities
First, you need to determine whether your application is affected by the log4j vulnerability. You can confirm this by checking the log4j version used in your application. If your application is using log4j 2.x version and includes log4j-core and log4j-api dependencies, then your application is likely to be vulnerable. - Upgrade log4j version
If you determine that your application is affected by a vulnerability, then you need to upgrade the log4j version to fix the vulnerability. The Apache Log4j project has released a version that fixes the vulnerability. You can download the latest version of log4j from the official website (https://logging.apache.org/log4j/2.x/). - Check and update dependencies
In addition to updating the log4j version, you also need to check whether your application has other dependencies that use the log4j library. In most cases, you may need to update these dependencies to use the latest version of log4j. Please note that some third-party libraries may have log4j dependencies independent of the main application, so you need to double-check and ensure that all relevant dependencies are updated. - Configuring log4j properties
After upgrading the log4j version, you also need to do some configuration to ensure that the vulnerability has been fixed. Specifically, you need to make the following changes in log4j's configuration file:
- If your application is using log4j2.xml as the configuration file, make sure that in the configuration section of the file Add the following code in:
true - If your application The program uses log4j2.properties as the configuration file. Please make sure to add the following code in the file:
log4j2.formatMsgNoLookups=true
- Test the repair effect
After completing the above repair After the steps, you need to test the application to ensure that the vulnerability has been fixed. You can write a simple test case to verify the fix. For example, you can use the following code to test whether the vulnerability is successfully fixed:
import org.apache.logging.log4j.LogManager;
import org.apache.logging.log4j.Logger;
public class Log4jVulnerabilityTest {
private static final Logger logger = LogManager.getLogger(Log4jVulnerabilityTest.class);
public static void main(String[] args) {
logger.info("This is a test log message");
}}
You can run this test case and ensure that the log4j vulnerability is no longer triggered.
Summary
By following the above steps, you should be able to successfully fix the log4j vulnerability and ensure the security of your application. After fixing a vulnerability, be sure to monitor the log4j project for any subsequent releases of fixes and security recommendations. Keeping your application's dependent libraries updated and secure is key to ensuring system security.
The above is the detailed content of log4j vulnerability repair tutorial: guide you step by step to repair log4j vulnerabilities. For more information, please follow other related articles on the PHP Chinese website!
 3分钟快速使用ChatGPT教程,用它帮我写简历,太牛了Apr 11, 2023 pm 07:40 PM
3分钟快速使用ChatGPT教程,用它帮我写简历,太牛了Apr 11, 2023 pm 07:40 PM已经火了很久了,身边的同事也用它来进行一些调研,资源检索,工作汇报等方面都有很大的的效率提升。很多人问ChatGPT会不会取代程序员?我的回答是:不会!ChatGPT并不是我们的敌人,相反的是,它是我们的好帮手。未来人和人的竞争,可能就会从原先的我懂得更多,我实操经验更丰富,变成了我比你更会用工具,我比你更懂得提问,我比你更会发挥机器人的最大特性,所以,为了不掉队,你还不准备体验下ChatGPT吗?快速体验面试官经常会问你的项目有啥重难点?很多人不会回答,直接看看ChatGPT怎么说,真的太牛了
 教大家win10电脑怎么屏蔽各种弹窗广告Jul 09, 2023 pm 05:57 PM
教大家win10电脑怎么屏蔽各种弹窗广告Jul 09, 2023 pm 05:57 PM电脑上广告弹窗太多了怎么办,有的小伙伴不想重装系统,下面就和大家讲讲关闭win10广告的方法吧,大家可以借鉴一下。1、右键点击电脑桌面下方任务栏,在弹出的菜单中选择并打开“任务管理器”。2、右键点击需要关闭的启动项,选择“禁用”。对应软件的开机启动项就关闭成功了。弹窗拦截设置1、打开毒霸,在首页点击左下方的“弹窗拦截”。2、点击“扫描”,对电脑进行全面扫描找出带有弹窗的软件。3、勾选需要拦截的软件,然后点击“一键拦截”。4、一键拦截后,对应的软件弹窗问题就已被拦截了。综上所述,如果大家电脑win
 u盘怎么重装win11系统的步骤教程Jul 08, 2023 pm 09:33 PM
u盘怎么重装win11系统的步骤教程Jul 08, 2023 pm 09:33 PM微软近日透露了将推出win11系统,很多用户都在期待新系统呢。网上已经有泄露关于win11的镜像安装系统。大家不知道如何安装的话,可以使用U盘来进行安装。小编现在就给大家带来了win11的U盘安装教程。1、首先准备一个8G以上大小的u盘,将它制作成系统盘。2、接着下载win11系统镜像文件,将它放入u盘中,大家可以直接点击右侧的链接进行下载。3、下载完成后装载该iso文件。4、装载完成之后会进入新的文件夹,在其中找到并运行win11的安装程序。5、在列表中选择“win11”然后点击“下一步”。6
 2023年最流行的5个php开发框架视频教程推荐May 08, 2017 pm 04:26 PM
2023年最流行的5个php开发框架视频教程推荐May 08, 2017 pm 04:26 PM如果想快速进行php web开发,选择一个好用的php开发框架至关重要,一个好的php开发框架可以让开发工作变得更加快捷、安全和有效。那2023年最流行的php开发框架有哪些呢?这些php开发框架排名如何?
 PHP基础教程:从入门到精通Jun 18, 2023 am 09:43 AM
PHP基础教程:从入门到精通Jun 18, 2023 am 09:43 AMPHP是一种广泛使用的开源服务器端脚本语言,它可以处理Web开发中所有的任务。PHP在网页开发中的应用广泛,尤其是在动态数据处理上表现优异,因此被众多开发者喜爱和使用。在本篇文章中,我们将一步步地讲解PHP基础知识,帮助初学者从入门到精通。一、基本语法PHP是一种解释性语言,其代码类似于HTML、CSS和JavaScript。每个PHP语句都以分号;结束,注
 老电脑系统xp升级win7教程步骤Jul 07, 2023 pm 10:21 PM
老电脑系统xp升级win7教程步骤Jul 07, 2023 pm 10:21 PMxp系统曾经是使用最多的系统,不过随着硬件的不断升级,xp系统已经不能发挥硬件的性能,所以很多朋友就想升级win7系统,下面就和大家分享一下老电脑升级win7系统的方法吧。1、在小白一键重装系统官网中下载小白三步装机版软件并打开,软件会自动帮助我们匹配合适的系统,然后点击立即重装。2、接下来软件就会帮助我们直接下载系统镜像,只需要耐心等候即可。3、下载完成后软件会帮助我们直接进行在线重装Windows系统,请根据提示操作。4、安装完成后会提示我们重启,选择立即重启。5、重启后在PE菜单中选择Xi
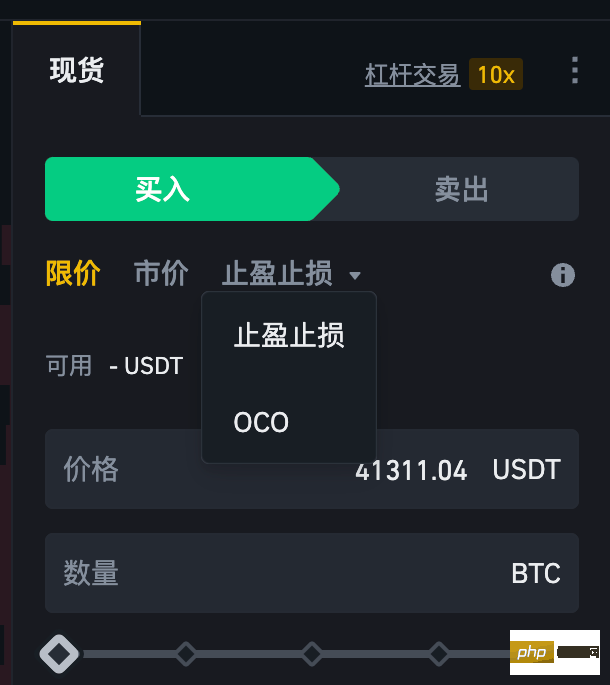 什么是OCO订单?Apr 25, 2023 am 11:26 AM
什么是OCO订单?Apr 25, 2023 am 11:26 AM二选一订单(OneCancelstheOther,简称OCO)可让您同时下达两个订单。它结合了限价单和限价止损单,但只能执行其中一个。换句话说,只要其中的限价单被部分或全部成交、止盈止损单被触发,另一个订单将自动取消。请注意,取消其中一个订单也会同时取消另一个订单。在币安交易平台进行交易时,您可以将二选一订单作为交易自动化的基本形式。这个功能可让您选择同时下达两个限价单,从而有助于止盈和最大程度减少潜在损失。如何使用二选一订单?登录您的币安帐户之后,请前往基本交易界面,找到下图所示的交易区域。点
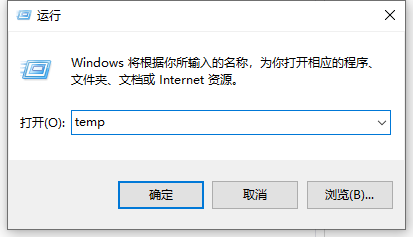 教你学会win10如何删除temp文件夹Jul 08, 2023 pm 04:13 PM
教你学会win10如何删除temp文件夹Jul 08, 2023 pm 04:13 PM在win10的系统盘中,很多网友会看到一个temp文件夹,里面占用的内存非常大,占用了c盘很多空间。有网友想删除temp文件夹,但是不知道能不能删,win10如何删除temp文件夹。下面小编就教下大家win10删除temp文件夹的方法。首先,Temp是指系统临时文件夹。而很多收藏夹,浏览网页的临时文件都放在这里,这是根据你操作的过程临时保存下来的。如有需要,可以手动删除的。如何删除temp文件夹?具体步骤如下:方法一:1、按下【Win+R】组合键打开运行,在运行框中输入temp,点击确定;2、此


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

EditPlus Chinese cracked version
Small size, syntax highlighting, does not support code prompt function

ZendStudio 13.5.1 Mac
Powerful PHP integrated development environment

Safe Exam Browser
Safe Exam Browser is a secure browser environment for taking online exams securely. This software turns any computer into a secure workstation. It controls access to any utility and prevents students from using unauthorized resources.

Dreamweaver Mac version
Visual web development tools

VSCode Windows 64-bit Download
A free and powerful IDE editor launched by Microsoft





