How to set up no network access permission
With the popularity and development of the Internet, the Internet has become an important part of people's daily life. However, in some cases we may need to limit or disable network access to certain devices or users. Whether it is to protect personal privacy, ensure the security of company confidential information, or to control the reasonable allocation of network resources, setting no network access permissions is essential.
A common countermeasure is to set up no network access through the router. A router is a key device that connects multiple devices to the Internet, so it has the ability to control network access. The following are some common settings:
- MAC address filtering: Each device has a unique MAC address, and the router can control whether to allow or prohibit the device from accessing the network through MAC address filtering. First, find the MAC address filtering option in the router's settings interface, and then add the MAC address of the device you want to restrict access to the blacklist. This way, devices added to the blacklist will not be able to connect to the network.
- IP address filtering: In the router settings interface, find the IP address filtering option. Then, add the device to a whitelist or blacklist based on its IP address to control its access. Devices in the whitelist will be allowed to access the network, while devices in the blacklist will be denied access.
- Access Control List (ACL): An access control list is a set of rules configured on a router to control the data packets transmitted in the network. Access control to specified devices or users can be achieved by configuring appropriate access control lists.
- Timing settings: Some routers also provide a timing setting function, which can turn on or off network access according to a set time period. For example, you can set it to prohibit access when you go to bed at night to protect your rest time.
While setting up no network access through a router is an effective way, there are other ways to achieve the same purpose. For example, a device or user's network access can be controlled through the operating system's firewall settings. A firewall is a network security device that monitors and filters data traffic in and out of a network. In the operating system settings, users can set firewall rules based on ports, protocols or IP addresses to control network access permissions.
Also, specific software or applications can be used to achieve a setup without network access. These software can provide flexible network access control functions according to user needs. For example, parental control software can be used to limit children's Internet access during specific periods of time to ensure that they can concentrate on studying or resting.
In summary, the setting of no network access permissions is very important for protecting personal privacy, ensuring company information security, and controlling resource allocation. Through routers, firewalls, software, etc., we can effectively set no network access permissions for devices or users, thereby achieving network security and a good usage environment. However, when setting up non-network access permissions, reasonable technical means are required, personal privacy and legitimate rights and interests must also be considered, and full communication and understanding must be carried out with users.
The above is the detailed content of Set up no network access. For more information, please follow other related articles on the PHP Chinese website!
 Black Boxes on Desktop Icons: Find Powerful Tips to RemoveMay 12, 2025 pm 08:07 PM
Black Boxes on Desktop Icons: Find Powerful Tips to RemoveMay 12, 2025 pm 08:07 PMEncountering black squares instead of desktop icons in Windows 11/10? This comprehensive guide offers several straightforward solutions to restore your icons to their original appearance. Quick Navigation: Black Squares on Desktop Icons Solution 1:
 CapCut Project File Location: How to Find, Recover, and ShareMay 12, 2025 pm 08:06 PM
CapCut Project File Location: How to Find, Recover, and ShareMay 12, 2025 pm 08:06 PMThis MiniTool guide offers a complete walkthrough for managing CapCut projects, covering location, recovery, and sharing. Mastering these steps ensures efficient project handling. Quick Navigation: CapCut Project File Location on PC Backing Up CapC
 Persistent Fake Virus Alerts in Edge: How to Identify & AvoidMay 12, 2025 pm 08:05 PM
Persistent Fake Virus Alerts in Edge: How to Identify & AvoidMay 12, 2025 pm 08:05 PMEdge browser fake virus warning: a guide to identifying, handling and prevention Many users report encountering fake virus warnings in Microsoft Edge browser. These warnings usually appear in the form of pop-ups, claiming that malware or viruses are detected, attempting to induce users to download malware or take harmful actions. This article will guide you on how to identify, deal with, and prevent such false warnings. How to identify fake virus warnings in Edge browser? False virus warnings usually have the following characteristics: Use emergency and panic language: Try to force users to act by creating panic. Use fake company logos: Imitate the logo of well-known security software or Microsoft. Regular companies will not issue warnings in this way. Request to dial
 Effective Ways to Fix EVERSPACE 2 Crashing/Not LaunchingMay 12, 2025 pm 08:03 PM
Effective Ways to Fix EVERSPACE 2 Crashing/Not LaunchingMay 12, 2025 pm 08:03 PMEVERSPACE 2 Crash Problem and Solutions Have you encountered a crash problem while playing EVERSPACE 2? If this problem bothers you, this MiniTool article will help you. This article will explain common causes and effective solutions to EVERSPACE 2 crashes. Quick navigation: EVERSPACE 2 Startup Crash How to fix EVERSPACE 2 crash Summarize EVERSPACE 2 Startup Crash The EVERSPACE 2 crash problem has always been the focus of players. Many players have reported different types of crashes, including crashes at startup, sudden exits during the game, and interactions with Unreal Engine
 Apex Integrity Error 0x8000001: 3 Useful Methods HereMay 12, 2025 pm 08:02 PM
Apex Integrity Error 0x8000001: 3 Useful Methods HereMay 12, 2025 pm 08:02 PMEncountering the Apex Legends integrity error 0x8000001, causing game crashes? This guide provides effective solutions. Let's explore the fixes. Apex Integrity Error 0x8000001: A Crashing Problem Many Apex Legends players report encountering the &quo
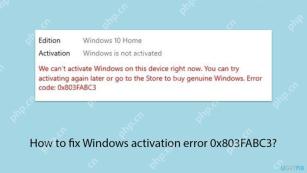 How to fix Windows activation error 0x803FABC3?May 12, 2025 pm 06:00 PM
How to fix Windows activation error 0x803FABC3?May 12, 2025 pm 06:00 PMWindows activation is a critical process in Windows 11 that verifies your operating system copy is genuine, enabling full functionality like personalization fea
 How to Use Copilot in Microsoft OneDrive? Everything You NeedMay 11, 2025 pm 08:02 PM
How to Use Copilot in Microsoft OneDrive? Everything You NeedMay 11, 2025 pm 08:02 PMUnlock the Power of Microsoft OneDrive Copilot: Your AI-Powered File Assistant This MiniTool guide unveils the capabilities of Copilot in OneDrive, a revolutionary AI assistant designed to streamline your file management and boost productivity. Expl
 A Guide to Fix A Supported Game Is Required to Use This FeatureMay 11, 2025 pm 08:01 PM
A Guide to Fix A Supported Game Is Required to Use This FeatureMay 11, 2025 pm 08:01 PMTroubleshooting the NVIDIA GeForce Experience "Supported Game Required" Error Encountering the "A supported game is required to use this feature" error in NVIDIA GeForce Experience while using game filters, screen recording, or ad


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Dreamweaver Mac version
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

EditPlus Chinese cracked version
Small size, syntax highlighting, does not support code prompt function

MinGW - Minimalist GNU for Windows
This project is in the process of being migrated to osdn.net/projects/mingw, you can continue to follow us there. MinGW: A native Windows port of the GNU Compiler Collection (GCC), freely distributable import libraries and header files for building native Windows applications; includes extensions to the MSVC runtime to support C99 functionality. All MinGW software can run on 64-bit Windows platforms.

SecLists
SecLists is the ultimate security tester's companion. It is a collection of various types of lists that are frequently used during security assessments, all in one place. SecLists helps make security testing more efficient and productive by conveniently providing all the lists a security tester might need. List types include usernames, passwords, URLs, fuzzing payloads, sensitive data patterns, web shells, and more. The tester can simply pull this repository onto a new test machine and he will have access to every type of list he needs.






