 Hardware Tutorial
Hardware Tutorial Hardware News
Hardware News 25-year-old Easter egg: AMD Athlon K7 processor found with Texas and pistol patterns
25-year-old Easter egg: AMD Athlon K7 processor found with Texas and pistol patterns25-year-old Easter egg: AMD Athlon K7 processor found with Texas and pistol patterns
News from this site on February 9th. Hardware photographer Fritzchens Fritz recently accidentally discovered an Easter egg that had been hidden for 25 years while inspecting AMD's Athlon Classic CPU.

Using a magnifying glass to examine the Athlon K7 processor, Fritz spotted the Texas logo in the corner, with a photo of a fired revolver underneath.

Note from this site: The first Athlon processor made its debut on June 23, 1999. Its name was taken from the "Decathlon" in track and field sports. ).



The main frequency of the first batch of processors is between 500 and 700 MHz. The socket is Slot A, and the core revision is "K7", continuing the naming convention of its predecessor, the K6 processor.
The first Athlon processor belonged to AMD's seventh generation (K7) and competed with Intel's Pentium III processor at the time. Athlon XP, MP, etc. were subsequently launched.
Athlon (Argon core) is manufactured on a 250nm process and has 512 KB of L2 cache and 22 million transistors. The first models had a plug-in design, designated slot A, and had strong overclocking capabilities.
The above is the detailed content of 25-year-old Easter egg: AMD Athlon K7 processor found with Texas and pistol patterns. For more information, please follow other related articles on the PHP Chinese website!
 Razer PC Remote Play lets you stream games to your iPhone – and it could convince me to switch from my gaming PCApr 12, 2025 am 09:32 AM
Razer PC Remote Play lets you stream games to your iPhone – and it could convince me to switch from my gaming PCApr 12, 2025 am 09:32 AMRazer has launched its PC Remote Play game streaming serviceThis lets you stream games from your PC to a mobile deviceIt comes with optimization features and works with controllersI love my gaming PC, but it’s not the most portable device in the wo
 All the best PS5 controllers we recommend shopping for during Black Friday this weekApr 12, 2025 am 09:02 AM
All the best PS5 controllers we recommend shopping for during Black Friday this weekApr 12, 2025 am 09:02 AMThe best PS5 controllers aren't as abundant as other platforms when it comes to overall choice. That's obviously a bit of a shame, but what is available is still absolutely worth a look - especially if you're in the market for a DualSense alternative
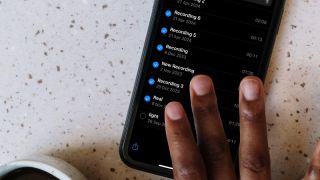 Select Faster on iPhone With This Two-Finger TrickApr 12, 2025 am 12:53 AM
Select Faster on iPhone With This Two-Finger TrickApr 12, 2025 am 12:53 AMYour iPhone has multiple touch and gesture capabilities that can enhance how you interact with apps. Some, like pinch and zoom, are well known enough to be considered second nature, but others are less obvious, like the one we're about to explain.Two
 How to Adjust Mac Volume and Brightness More PreciselyApr 11, 2025 pm 09:01 PM
How to Adjust Mac Volume and Brightness More PreciselyApr 11, 2025 pm 09:01 PMOn a Mac that has a top row of function keys, Apple includes volume and brightness controls that can be used to make adjustments in stepwise increments. However, there may be times when you want to make more fine grained adjustments to these settings
 The best JRPGs to play in 2025Apr 11, 2025 am 11:39 AM
The best JRPGs to play in 2025Apr 11, 2025 am 11:39 AMThe best JRPGs (Japanese role-playing games) in 2025 use theatrical storytelling and vibrant ensemble casts to weave powerful experiences that stay with us long after we put the controller down.Contrary to the name, JRPGs aren't necessarily all from
 Best horror games: the scariest titles to play in 2025Apr 11, 2025 am 11:09 AM
Best horror games: the scariest titles to play in 2025Apr 11, 2025 am 11:09 AMThe best horror games in 2025 may not be the most comforting things to play, but they're guaranteed to get your adrenaline rushing.There have been some fantastic additions to the horror game genre recently. With Alan Wake 2, the Resident Evil 4 remak
 Best Assassin’s Creed games in 2025: every series entry rankedApr 11, 2025 am 10:42 AM
Best Assassin’s Creed games in 2025: every series entry rankedApr 11, 2025 am 10:42 AMThe best Assassin’s Creed games still hold up in 2025, combining historical intrigue with heaps of stealth-focused action. And while the series has gone through many changes over the years, it's still one of the biggest names around, with plenty of
 Best crossplay games 2025: top titles for cross-platform play with friendsApr 11, 2025 am 09:41 AM
Best crossplay games 2025: top titles for cross-platform play with friendsApr 11, 2025 am 09:41 AMThe best crossplay games in 2025 make it easy to play with all of your friends, regardless of where they're playing. They also help with picking up your game on a different platform without having to start over, and they show that playing together do


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

ZendStudio 13.5.1 Mac
Powerful PHP integrated development environment

Dreamweaver Mac version
Visual web development tools

SecLists
SecLists is the ultimate security tester's companion. It is a collection of various types of lists that are frequently used during security assessments, all in one place. SecLists helps make security testing more efficient and productive by conveniently providing all the lists a security tester might need. List types include usernames, passwords, URLs, fuzzing payloads, sensitive data patterns, web shells, and more. The tester can simply pull this repository onto a new test machine and he will have access to every type of list he needs.

VSCode Windows 64-bit Download
A free and powerful IDE editor launched by Microsoft

Dreamweaver CS6
Visual web development tools




