 web3.0
web3.0 What technology does Bitcoin use? What technology does Bitcoin use to ensure transaction security?
What technology does Bitcoin use? What technology does Bitcoin use to ensure transaction security?What technology does Bitcoin use? What technology does Bitcoin use to ensure transaction security?
What network technology does Bitcoin use? As a decentralized digital currency, Bitcoin uses a series of technologies to ensure the security of transactions. First of all, Bitcoin uses blockchain technology, which is a distributed ledger system in which all transaction records are stored in a network composed of multiple nodes. Each node has a complete transaction history record, so that even if someone tries to tamper with a transaction record, other nodes can confirm the real transaction information through the consensus algorithm. Secondly, Bitcoin also uses cryptography technology, including the encryption and decryption process of public and private keys, and the verification mechanism of digital signatures. The application of these technologies effectively guarantees the security of Bitcoin transactions.
Blockchain is a technology based on a cryptographic consensus mechanism that ensures data security through workload proof. Bitcoin's blockchain network uses the Bitcoin network protocol, which is a special P2P network that enables seamless transactions between users. The Bitcoin network uses a protocol called the "Bitcoin Protocol", which ensures the security of Bitcoin and prevents abuse. The protocol also introduces the concept of "blocks" to further ensure the security of Bitcoin and prevent abuse. The Bitcoin network also uses a technology called "Bitcoin Node" to ensure the security of Bitcoin and the security of transactions. A Bitcoin node is a network node whose role is to verify and record Bitcoin transactions while maintaining the security of the entire network. By connecting to other nodes and sharing transaction information, Bitcoin nodes are able to ensure the validity and accuracy of each transaction, thereby protecting users' funds. In addition, Bitcoin nodes also participate in Bitcoin’s consensus mechanism, helping to decide which transactions are approved and added to the blockchain. Through this distributed node network, Bitcoin's security has been enhanced, making Bitcoin a relatively safe and reliable digital currency. Bitcoin uses blockchain technology, which ensures secure transactions between Bitcoin users and ensures the security and non-tamperability of Bitcoin. The Bitcoin network uses the Bitcoin protocol, which ensures the security of Bitcoin and prevents abuse. In addition, the Bitcoin network also uses Bitcoin node technology, which not only ensures the security of Bitcoin, but also ensures the security of transactions.
Bitcoin is a distributed digital currency. It is a decentralized digital currency based on cryptography. It uses distributed accounting technology and consensus mechanism to ensure transaction security. Bitcoin's security mainly relies on the technology it uses.
Bitcoin uses a hashing algorithm to ensure transaction security. The hash algorithm is a computer algorithm that can map data into fixed-length data, ensuring uniqueness and irreversibility, thereby ensuring the security of transactions. Bitcoin uses public key cryptography to ensure transaction security. Public key cryptography uses public and private keys for encryption and decryption, ensuring the security of transactions. In addition, Bitcoin also uses distributed ledger technology to ensure transaction security. Distributed ledger technology is a distributed database technology that can distribute and store transaction data on multiple nodes, thus ensuring the security of transactions. Finally, Bitcoin also uses a consensus mechanism to ensure transaction security. The consensus mechanism is a distributed consensus algorithm that ensures the integrity and consistency of transaction data, thereby ensuring the security of transactions. In short, Bitcoin uses hashing algorithms, public key cryptography, distributed ledger technology and consensus mechanisms to ensure transaction security. These technologies can effectively prevent transactions from being destroyed.The above is the detailed content of What technology does Bitcoin use? What technology does Bitcoin use to ensure transaction security?. For more information, please follow other related articles on the PHP Chinese website!
 Tokenized Treasuries Near $6B Milestone, Led by BlackRockApr 19, 2025 am 11:44 AM
Tokenized Treasuries Near $6B Milestone, Led by BlackRockApr 19, 2025 am 11:44 AMThe value of blockchain-based U.S. Treasuries is closing in on a new milestone, with total holdings approaching $6 billion.
 title: Canary Capital Is Launching a TRX-Tracking ETFApr 19, 2025 am 11:42 AM
title: Canary Capital Is Launching a TRX-Tracking ETFApr 19, 2025 am 11:42 AMCanary Capital is looking to launch an exchange-traded fund (ETF) tracking the price of Tron's native token, TRX, according to a filing.
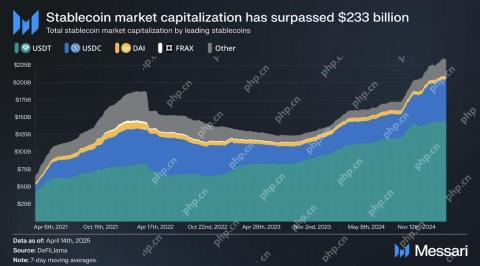 Solana Stablecoin Market Cap Hits Record $12.73 Billion as Sui Supply Reaches $800M with $60M InflowsApr 19, 2025 am 11:40 AM
Solana Stablecoin Market Cap Hits Record $12.73 Billion as Sui Supply Reaches $800M with $60M InflowsApr 19, 2025 am 11:40 AMThe stablecoin market has surpassed a total capitalization of $233 billion. Within this sector, Solana's stablecoins have reached a new all-time high market capitalization of $12.73 billion
 Canary Capital Files for Staking TRX ETF, Targeting Launch Before Spot Bitcoin ETFsApr 19, 2025 am 11:38 AM
Canary Capital Files for Staking TRX ETF, Targeting Launch Before Spot Bitcoin ETFsApr 19, 2025 am 11:38 AMCanary Capital is looking to get the U.S. Securities and Exchange Commission's sign-off for an exchange-traded fund that would track the Tron token TRX and has a staking component.
 MoonPay CEO Ivan Soto-Wright calls on US lawmakers to leave a path open to state-level regulators when passing legislation on stablecoinsApr 19, 2025 am 11:36 AM
MoonPay CEO Ivan Soto-Wright calls on US lawmakers to leave a path open to state-level regulators when passing legislation on stablecoinsApr 19, 2025 am 11:36 AMIn an April 18 X post, Soto-Wright said he wanted Congress to “keep state-regulated issuers in the game” when it comes to stablecoin regulation, referencing efforts in the House of Representatives and Senate to create a federal regulatory framework.
 Michael Saylor Dissects the Philosophy and Technological Potential of Bitcoin in '21 Truths of Bitcoin'Apr 19, 2025 am 11:34 AM
Michael Saylor Dissects the Philosophy and Technological Potential of Bitcoin in '21 Truths of Bitcoin'Apr 19, 2025 am 11:34 AMSaylor's ideas centre on the fixed 21 million coin supply of Bitcoin. He presents this shortage as a revolutionary economic idea rather than only a technical one.
 Official Trump (TRUMP) memecoin unlocked 40 million tokens, worth around $300 millionApr 19, 2025 am 11:32 AM
Official Trump (TRUMP) memecoin unlocked 40 million tokens, worth around $300 millionApr 19, 2025 am 11:32 AMThe TRUMP memecoin has gained significant popularity on the Solana network primarily due to its direct affiliation with the U.S. President Donald Trump.
 TRUMP (TRUMP) memecoin unlocks 40 million tokens, worth around $300 millionApr 19, 2025 am 11:30 AM
TRUMP (TRUMP) memecoin unlocks 40 million tokens, worth around $300 millionApr 19, 2025 am 11:30 AMThe TRUMP memecoin has gained significant popularity on the Solana network primarily due to its direct affiliation with the U.S. President Donald Trump.

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

SecLists
SecLists is the ultimate security tester's companion. It is a collection of various types of lists that are frequently used during security assessments, all in one place. SecLists helps make security testing more efficient and productive by conveniently providing all the lists a security tester might need. List types include usernames, passwords, URLs, fuzzing payloads, sensitive data patterns, web shells, and more. The tester can simply pull this repository onto a new test machine and he will have access to every type of list he needs.

EditPlus Chinese cracked version
Small size, syntax highlighting, does not support code prompt function

Zend Studio 13.0.1
Powerful PHP integrated development environment

SublimeText3 English version
Recommended: Win version, supports code prompts!

PhpStorm Mac version
The latest (2018.2.1) professional PHP integrated development tool




