
Ajax security protection research: How to prevent information leakage?
Overview:
With the rapid development of web applications, Ajax (Asynchronous JavaScript and XML) has become one of the main technologies for building dynamic web pages. However, while Ajax improves user experience, it also brings some security risks, among which information leakage is one of the most common and serious problems. This article will explore Ajax security and provide some specific code examples.
The harm of information leakage:
Information leakage refers to a web application leaking sensitive information without authorization. This information may include users’ personal data, database credentials, API passwords, etc. Key etc. Once this information falls into the hands of hackers, it will cause serious losses to users and enterprises, including monetary loss, reputational damage, etc.
Ajax security protection measures:
- Cross-site request forgery (CSRF) protection:
CSRF is an attack method in which hackers deceive users into controlling Logged into web applications, thereby performing illegal operations without the user's knowledge. To prevent CSRF attacks, tokens can be used in Ajax requests. The server returns a randomly generated token in each response, the client brings the token with each request, and the server verifies the validity of the token, as shown below:
Server-side code :
import random
# 生成令牌
def generate_token():
token = random.randint(1000, 9999)
return token
# 验证令牌
def validate_token(request, response):
token = request.get('token')
if not token:
response.set('error', 'Token missing')
elif token != session.get('token'):
response.set('error', 'Invalid token')Client code:
// 发送Ajax请求
function sendRequest() {
var token = sessionStorage.getItem('token');
$.ajax({
url: 'example.com/api',
type: 'POST',
data: { token: token, // 其他请求参数 },
success: function(response) {
// 处理响应
}
});
}- Cross-site scripting (XSS) protection:
XSS is an attack method that hackers insert Malicious script code is added to web pages to steal user login credentials and obtain user sensitive information. In order to prevent XSS attacks, user input can be strictly verified and escaped to ensure that the input content will not be parsed into malicious code. For example, user input can be encoded using the encodeURIComponent function as follows:
// 对用户输入进行编码
var userInput = document.getElementById('userInput').value;
var encodedInput = encodeURIComponent(userInput);- Sensitive information encryption:
To protect the security of sensitive information during transmission , you can use SSL/TLS for encrypted transmission of Ajax requests. By using the HTTPS protocol, hackers can be prevented from intercepting and tampering with data packets, effectively protecting user information from being leaked.
Summary:
By taking the above measures, you can effectively prevent the risk of information leakage in Ajax. However, security protection is a continuous process, and other risks need to be considered in actual development, such as input verification, permission control, etc. Only by comprehensively considering all aspects of security issues can the security of web applications be ensured.
Reference:
- Mozilla Developer Network - Ajax: Getting Started
- OWASP - Cross-Site Request Forgery (CSRF)
- OWASP - Cross-Site Scripting (XSS)
- OWASP - Ajax Security Cheat Sheet
The above is the detailed content of A Deep Dive into Ajax Security: Ways to Protect Information Leakage. For more information, please follow other related articles on the PHP Chinese website!
 Replace String Characters in JavaScriptMar 11, 2025 am 12:07 AM
Replace String Characters in JavaScriptMar 11, 2025 am 12:07 AMDetailed explanation of JavaScript string replacement method and FAQ This article will explore two ways to replace string characters in JavaScript: internal JavaScript code and internal HTML for web pages. Replace string inside JavaScript code The most direct way is to use the replace() method: str = str.replace("find","replace"); This method replaces only the first match. To replace all matches, use a regular expression and add the global flag g: str = str.replace(/fi
 8 Stunning jQuery Page Layout PluginsMar 06, 2025 am 12:48 AM
8 Stunning jQuery Page Layout PluginsMar 06, 2025 am 12:48 AMLeverage jQuery for Effortless Web Page Layouts: 8 Essential Plugins jQuery simplifies web page layout significantly. This article highlights eight powerful jQuery plugins that streamline the process, particularly useful for manual website creation
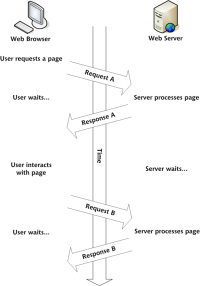 Build Your Own AJAX Web ApplicationsMar 09, 2025 am 12:11 AM
Build Your Own AJAX Web ApplicationsMar 09, 2025 am 12:11 AMSo here you are, ready to learn all about this thing called AJAX. But, what exactly is it? The term AJAX refers to a loose grouping of technologies that are used to create dynamic, interactive web content. The term AJAX, originally coined by Jesse J
 10 Mobile Cheat Sheets for Mobile DevelopmentMar 05, 2025 am 12:43 AM
10 Mobile Cheat Sheets for Mobile DevelopmentMar 05, 2025 am 12:43 AMThis post compiles helpful cheat sheets, reference guides, quick recipes, and code snippets for Android, Blackberry, and iPhone app development. No developer should be without them! Touch Gesture Reference Guide (PDF) A valuable resource for desig
 Improve Your jQuery Knowledge with the Source ViewerMar 05, 2025 am 12:54 AM
Improve Your jQuery Knowledge with the Source ViewerMar 05, 2025 am 12:54 AMjQuery is a great JavaScript framework. However, as with any library, sometimes it’s necessary to get under the hood to discover what’s going on. Perhaps it’s because you’re tracing a bug or are just curious about how jQuery achieves a particular UI
 How do I create and publish my own JavaScript libraries?Mar 18, 2025 pm 03:12 PM
How do I create and publish my own JavaScript libraries?Mar 18, 2025 pm 03:12 PMArticle discusses creating, publishing, and maintaining JavaScript libraries, focusing on planning, development, testing, documentation, and promotion strategies.
 10 jQuery Fun and Games PluginsMar 08, 2025 am 12:42 AM
10 jQuery Fun and Games PluginsMar 08, 2025 am 12:42 AM10 fun jQuery game plugins to make your website more attractive and enhance user stickiness! While Flash is still the best software for developing casual web games, jQuery can also create surprising effects, and while not comparable to pure action Flash games, in some cases you can also have unexpected fun in your browser. jQuery tic toe game The "Hello world" of game programming now has a jQuery version. Source code jQuery Crazy Word Composition Game This is a fill-in-the-blank game, and it can produce some weird results due to not knowing the context of the word. Source code jQuery mine sweeping game
 jQuery Parallax Tutorial - Animated Header BackgroundMar 08, 2025 am 12:39 AM
jQuery Parallax Tutorial - Animated Header BackgroundMar 08, 2025 am 12:39 AMThis tutorial demonstrates how to create a captivating parallax background effect using jQuery. We'll build a header banner with layered images that create a stunning visual depth. The updated plugin works with jQuery 1.6.4 and later. Download the


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

VSCode Windows 64-bit Download
A free and powerful IDE editor launched by Microsoft

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Zend Studio 13.0.1
Powerful PHP integrated development environment

mPDF
mPDF is a PHP library that can generate PDF files from UTF-8 encoded HTML. The original author, Ian Back, wrote mPDF to output PDF files "on the fly" from his website and handle different languages. It is slower than original scripts like HTML2FPDF and produces larger files when using Unicode fonts, but supports CSS styles etc. and has a lot of enhancements. Supports almost all languages, including RTL (Arabic and Hebrew) and CJK (Chinese, Japanese and Korean). Supports nested block-level elements (such as P, DIV),

SAP NetWeaver Server Adapter for Eclipse
Integrate Eclipse with SAP NetWeaver application server.






