Definition and different types of blockchain nodes
php editor Zimo is here to introduce you to the blockchain node. Blockchain is a decentralized distributed ledger technology, and blockchain nodes are the participants that make up the entire network. Nodes can be understood as computers or devices in the network. They jointly participate in the maintenance and operation of the blockchain by connecting to the blockchain network. According to different functions and roles, blockchain nodes can be divided into different types such as full nodes, light nodes, miner nodes and verification nodes. Different node types have different characteristics and functions, which together build the security and reliability of the blockchain.

What does blockchain node mean?
Blockchain nodes are network stakeholders, devices authorized to track ledgers and serve as communication hubs for network tasks.
Blockchain nodes mainly confirm the legality of transactions and assign unique identifiers to distinguish nodes.
Proof-of-work (PoW) blockchains, such as Bitcoin (BTC) or Monero (XMR), include miners responsible for the following.
Only "full nodes" can store all blockchain transactions on their devices. These nodes are responsible for validating blocks and transactions.
On the other hand, lightweight nodes have lower storage requirements and only need to download block headers to verify transactions. Block rewards are not always included in both versions of a full node.
What are the types of blockchain nodes?
Nodes are an important part of the blockchain infrastructure and are responsible for verifying transactions and adding new blocks. There are three main types: full nodes, light nodes, and miner nodes.
1. Full nodes
Full nodes are the most important node type in the blockchain network because they maintain a complete copy of the blockchain ledger. These nodes download and store a copy of every transaction and block on the network, which allows them to independently verify the entire blockchain history. Full nodes are the backbone of a blockchain network and are vital to maintaining its integrity.
Full nodes operate in a peer-to-peer network, meaning they communicate with other nodes to ensure the blockchain is up to date and accurate. They verify transactions and blocks by checking for differences, such as double spends or invalid signatures, before adding them to the blockchain. Full nodes are typically run by cryptocurrency enthusiasts, blockchain developers, and organizations that require a high degree of security and control over their blockchain transactions.
2. Light node
Light node, also known as SPV (Simplified Payment Verification) node, is a lighter weight version of the full node. They are designed to run on devices with limited storage and processing capabilities, such as smartphones and tablets. Light nodes do not download the entire blockchain, but a small portion of it that contains information related to their transactions.
Light nodes rely on full nodes for transaction verification and block verification. They communicate with several full nodes in the network to obtain the information needed to verify transactions. Light nodes are faster and more efficient than full nodes, but are also less secure because they rely on full nodes for validation.
3. Miner Node
The miner node is responsible for verifying transactions and adding new blocks to the blockchain. These nodes perform complex calculations to solve mathematical problems, allowing them to create new blocks and receive rewards in the form of cryptocurrency.
Miner nodes require specialized hardware and software to perform the calculations required for mining. They are usually run by large mining pools or individuals who have the resources to invest in the necessary equipment. Miner nodes are vital to the blockchain network as they ensure that new transactions are processed and added to the blockchain in a timely and secure manner.
The above is the detailed content of Definition and different types of blockchain nodes. For more information, please follow other related articles on the PHP Chinese website!
 FloppyPepe (FPPE) Price Could Explode As Bitcoin (BTC) Price Rallies Towards $450,000May 09, 2025 am 11:54 AM
FloppyPepe (FPPE) Price Could Explode As Bitcoin (BTC) Price Rallies Towards $450,000May 09, 2025 am 11:54 AMAccording to a leading finance CEO, the Bitcoin price could be set for a move to $450,000. This Bitcoin price projection comes after a resurgence of good performances, signaling that the bear market may end.
 Pi Network Confirms May 14 Launch—Qubetics and OKB Surge as Best Cryptos to Join for Long Term in 2025May 09, 2025 am 11:52 AM
Pi Network Confirms May 14 Launch—Qubetics and OKB Surge as Best Cryptos to Join for Long Term in 2025May 09, 2025 am 11:52 AMExplore why Qubetics, Pi Network, and OKB rank among the Best Cryptos to Join for Long Term. Get updated presale stats, features, and key real-world use cases.
 Sun Life Financial Inc. (TSX: SLF) (NYSE: SLF) Declares a Dividend of $0.88 Per ShareMay 09, 2025 am 11:50 AM
Sun Life Financial Inc. (TSX: SLF) (NYSE: SLF) Declares a Dividend of $0.88 Per ShareMay 09, 2025 am 11:50 AMTORONTO, May 8, 2025 /CNW/ - The Board of Directors (the "Board") of Sun Life Financial Inc. (the "Company") (TSX: SLF) (NYSE: SLF) today announced that a dividend of $0.88 per share on the common shares of the Company has been de
 Sun Life Announces Intended Renewal of Normal Course Issuer BidMay 09, 2025 am 11:48 AM
Sun Life Announces Intended Renewal of Normal Course Issuer BidMay 09, 2025 am 11:48 AMMay 7, 2025, the Company had purchased on the TSX, other Canadian stock exchanges and/or alternative Canadian trading platforms
 The Bitcoin price has hit $100k for the first time since February, trading at $101.3k at press time.May 09, 2025 am 11:46 AM
The Bitcoin price has hit $100k for the first time since February, trading at $101.3k at press time.May 09, 2025 am 11:46 AMBTC's strong correlation with the Global M2 money supply is playing out once again, with the largest cryptocurrency now poised for new all-time highs.
 Coinbase (COIN) Q1 CY2025 Highlights: Revenue Falls Short of Expectations, but Sales Rose 24.2% YoY to $2.03BMay 09, 2025 am 11:44 AM
Coinbase (COIN) Q1 CY2025 Highlights: Revenue Falls Short of Expectations, but Sales Rose 24.2% YoY to $2.03BMay 09, 2025 am 11:44 AMBlockchain infrastructure company Coinbase (NASDAQ: COIN) fell short of the market’s revenue expectations in Q1 CY2025, but sales rose 24.2% year
 Ripple Labs and the SEC Have Officially Reached a Settlement AgreementMay 09, 2025 am 11:42 AM
Ripple Labs and the SEC Have Officially Reached a Settlement AgreementMay 09, 2025 am 11:42 AMRipple Labs and the U.S. Securities and Exchange Commission (SEC) have officially reached a deal that, if approved by a judge, will bring their years-long legal battle to a close.
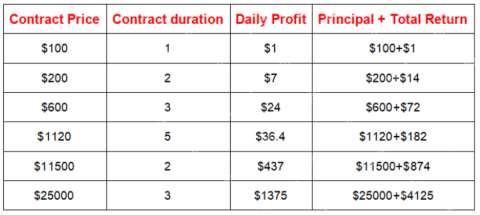 JA Mining Helps Global Users Share the Benefits of the Bitcoin Bull MarketMay 09, 2025 am 11:40 AM
JA Mining Helps Global Users Share the Benefits of the Bitcoin Bull MarketMay 09, 2025 am 11:40 AMBy lowering the threshold for mining and providing compliance protection, JA Mining helps global users share the benefits of the Bitcoin bull market.

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Dreamweaver Mac version
Visual web development tools

SAP NetWeaver Server Adapter for Eclipse
Integrate Eclipse with SAP NetWeaver application server.

SublimeText3 Chinese version
Chinese version, very easy to use

MantisBT
Mantis is an easy-to-deploy web-based defect tracking tool designed to aid in product defect tracking. It requires PHP, MySQL and a web server. Check out our demo and hosting services.

DVWA
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is very vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, to help web developers better understand the process of securing web applications, and to help teachers/students teach/learn in a classroom environment Web application security. The goal of DVWA is to practice some of the most common web vulnerabilities through a simple and straightforward interface, with varying degrees of difficulty. Please note that this software







