The firefly algorithm is a meta-heuristic optimization algorithm inspired by the flickering behavior of fireflies and is designed to solve continuous optimization problems.
Principle of Firefly Algorithm
In the firefly algorithm, the objective function is related to the light intensity at the tail of the firefly. In terms of optimization, the attraction and movement of fireflies can inspire algorithms, which can be followed to obtain optimal solutions.
In the firefly algorithm, fireflies refer to randomly generated feasible solutions. They are assigned a light intensity proportional to their functional value based on their performance in the objective function. For minimization problems, the solution with the smallest function value will be assigned the highest light intensity. Once the light intensities of the solution are distributed, each firefly will follow the firefly with the higher light intensity. The brightest firefly will perform a local search by randomly moving around it.
The algorithm mimics how fireflies interact using flash lights. Assume that all fireflies are opposite-sex attracted, which means that any firefly can attract all other fireflies. The attractiveness of a firefly is directly proportional to its brightness, which depends on the objective function. Brighter fireflies attract other fireflies. Furthermore, according to the inverse square law, brightness gradually decreases with distance.
Firefly Algorithm and Metaheuristic Solving Algorithm
Fireflies communicate using flickering properties, and there are approximately 2,000 unique flash patterns. They produce brief, patterned flashes of light.
This flashing pattern of communication is used to attract mates and warn predators. The right partner will communicate by imitating the same pattern or responding in a specific pattern. Therefore, a firefly's flash causes a reaction in nearby fireflies.
Natural selection and survival of the fittest are the core ideas of early metaheuristic algorithms. Due to the complexity of algorithm modeling, the implementation of deterministic solution methods is challenging, thus promoting the development of metaheuristic solution algorithms.
Metaheuristic algorithms are approximate solutions to optimization problems that use the properties of randomness to iterate and improve the quality of the solution from a set of randomly generated feasible solutions.
Although metaheuristic algorithms cannot guarantee optimality, they can be tested to give reasonable and acceptable solutions.
Additionally, metaheuristic algorithms have the advantage of being immune to problem behavior, which makes them useful in many application scenarios.
The above is the detailed content of Introduction and comparison of firefly algorithm and metaheuristic solving algorithm. For more information, please follow other related articles on the PHP Chinese website!
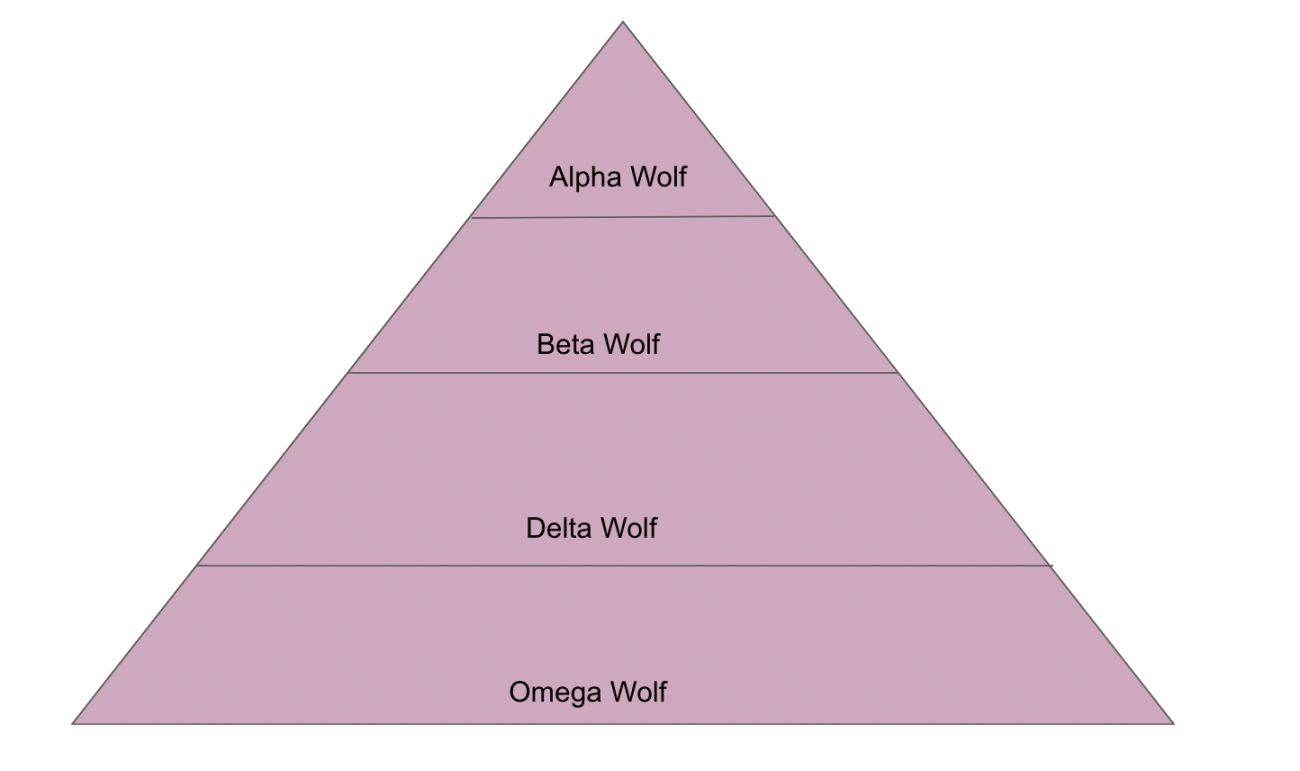 深入剖析灰狼优化算法(GWO)及其优势与弱点Jan 19, 2024 pm 07:48 PM
深入剖析灰狼优化算法(GWO)及其优势与弱点Jan 19, 2024 pm 07:48 PM灰狼优化算法(GWO)是一种基于种群的元启发式算法,模拟自然界中灰狼的领导层级和狩猎机制。灰狼算法灵感1、灰狼被认为是顶级掠食者,处于食物链的顶端。2、灰狼喜欢群居(群居),每个狼群平均有5-12只狼。3、灰狼具有非常严格的社会支配等级,如下图:Alpha狼:Alpha狼在整个灰狼群中占据优势地位,拥有统领整个灰狼群的权利。在算法应用中,Alpha狼是最佳解决方案之一,由优化算法产生的最优解。Beta狼:Beta狼定期向Alpha狼报告,并帮助Alpha狼做出最佳决策。在算法应用中,Beta狼可
 探究嵌套采样算法的基本原理和实施流程Jan 22, 2024 pm 09:51 PM
探究嵌套采样算法的基本原理和实施流程Jan 22, 2024 pm 09:51 PM嵌套采样算法是一种高效的贝叶斯统计推断算法,用于计算复杂概率分布下的积分或求和。它通过将参数空间分解为多个体积相等的超立方体,并逐步迭代地将其中一个最小体积的超立方体“推出”,然后用随机样本填充该超立方体,以更好地估计概率分布的积分值。通过不断迭代,嵌套采样算法可以得到高精度的积分值和参数空间的边界,从而可应用于模型比较、参数估计和模型选择等统计学问题。该算法的核心思想是将复杂的积分问题转化为一系列简单的积分问题,通过逐步缩小参数空间的体积,逼近真实的积分值。每个迭代步骤都通过随机采样从参数空间
 解析麻雀搜索算法(SSA)的原理、模型和构成Jan 19, 2024 pm 10:27 PM
解析麻雀搜索算法(SSA)的原理、模型和构成Jan 19, 2024 pm 10:27 PM麻雀搜索算法(SSA)是基于麻雀反捕食和觅食行为的元启发式优化算法。麻雀的觅食行为可分为两种主要类型:生产者和拾荒者。生产者主动寻找食物,而拾荒者则争夺生产者的食物。麻雀搜索算法(SSA)原理在麻雀搜索算法(SSA)中,每只麻雀都密切关注着邻居的行为。通过采用不同的觅食策略,个体能够有效地利用保留的能量来追求更多的食物。此外,鸟类在搜索空间中更容易受到捕食者的攻击,因此它们需要寻找更安全的位置。群体中心的鸟类可以通过靠近邻居来最大限度地减少自身的危险范围。当一只鸟发现捕食者时,会发出警报声,以便
 Wu-Manber算法简介及Python实现说明Jan 23, 2024 pm 07:03 PM
Wu-Manber算法简介及Python实现说明Jan 23, 2024 pm 07:03 PMWu-Manber算法是一种字符串匹配算法,用于高效地搜索字符串。它是一种混合算法,结合了Boyer-Moore和Knuth-Morris-Pratt算法的优势,可提供快速准确的模式匹配。Wu-Manber算法步骤1.创建一个哈希表,将模式的每个可能子字符串映射到该子字符串出现的模式位置。2.该哈希表用于快速识别文本中模式的潜在起始位置。3.遍历文本并将每个字符与模式中的相应字符进行比较。4.如果字符匹配,则可以移动到下一个字符并继续比较。5.如果字符不匹配,可以使用哈希表来确定在模式的下一个潜
 鲸鱼优化算法 (WOA) 的数值优化原理和分析Jan 19, 2024 pm 07:27 PM
鲸鱼优化算法 (WOA) 的数值优化原理和分析Jan 19, 2024 pm 07:27 PM鲸鱼优化算法(WOA)是一种基于自然启发的元启发式优化算法,模拟了座头鲸的狩猎行为,用于数值问题的优化。鲸鱼优化算法(WOA)以一组随机解作为起点,通过每次迭代中搜索代理的位置更新,根据随机选择的搜索代理或迄今为止的最佳解决方案来进行优化。鲸鱼优化算法灵感鲸鱼优化算法的灵感源自座头鲸的狩猎行为。座头鲸喜欢的食物位于海面附近,如磷虾和鱼群。因此,座头鲸在狩猎时通过自下而上螺旋吐泡泡的方式,将食物聚集在一起形成泡泡网。在“向上螺旋”机动中,座头鲸下潜约12m,然后开始在猎物周围形成螺旋形气泡并向上游
 尺度转换不变特征(SIFT)算法Jan 22, 2024 pm 05:09 PM
尺度转换不变特征(SIFT)算法Jan 22, 2024 pm 05:09 PM尺度不变特征变换(SIFT)算法是一种用于图像处理和计算机视觉领域的特征提取算法。该算法于1999年提出,旨在提高计算机视觉系统中的物体识别和匹配性能。SIFT算法具有鲁棒性和准确性,被广泛应用于图像识别、三维重建、目标检测、视频跟踪等领域。它通过在多个尺度空间中检测关键点,并提取关键点周围的局部特征描述符来实现尺度不变性。SIFT算法的主要步骤包括尺度空间的构建、关键点检测、关键点定位、方向分配和特征描述符生成。通过这些步骤,SIFT算法能够提取出具有鲁棒性和独特性的特征,从而实现对图像的高效
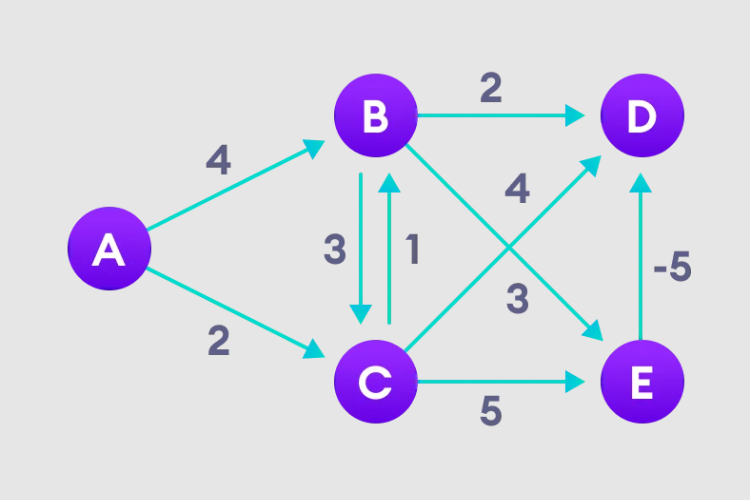 详解贝尔曼福特算法并用Python实现Jan 22, 2024 pm 07:39 PM
详解贝尔曼福特算法并用Python实现Jan 22, 2024 pm 07:39 PM贝尔曼福特算法(BellmanFord)可以找到从目标节点到加权图其他节点的最短路径。这一点和Dijkstra算法很相似,贝尔曼福特算法可以处理负权重的图,从实现来看也相对简单。贝尔曼福特算法原理详解贝尔曼福特算法通过高估从起始顶点到所有其他顶点的路径长度,迭代寻找比高估路径更短的新路径。因为我们要记录每个节点的路径距离,可以将其存储在大小为n的数组中,n也代表了节点的数量。实例图1、选择起始节点,并无限指定给其他所有顶点,记录路径值。2、访问每条边,并进行松弛操作,不断更新最短路径。3、我们需
 乌鸦搜索算法的原理和最佳解逻辑Jan 19, 2024 pm 08:12 PM
乌鸦搜索算法的原理和最佳解逻辑Jan 19, 2024 pm 08:12 PM乌鸦搜索算法(CSA)是一种受乌鸦行为启发的群体智能优化算法。与其他受自然启发的元启发式算法类似,CSA模拟了乌鸦隐藏和取回食物的行为。这种算法具有结构简单、控制参数少、易于实现等特点。然而,与大多数优化算法一样,CSA也存在一些缺点,比如收敛速度较慢和容易陷入局部最优解。尽管如此,CSA仍然是一个有潜力的算法,可以在某些问题上表现出良好的优化能力。为什么使用乌鸦搜索算法?乌鸦搜索算法(CSA)的特点在于它能够收集来自不同事物的响应,并将它们作为整体计算,从而找到问题的最佳解决方案。这种方法的优

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Dreamweaver Mac version
Visual web development tools

mPDF
mPDF is a PHP library that can generate PDF files from UTF-8 encoded HTML. The original author, Ian Back, wrote mPDF to output PDF files "on the fly" from his website and handle different languages. It is slower than original scripts like HTML2FPDF and produces larger files when using Unicode fonts, but supports CSS styles etc. and has a lot of enhancements. Supports almost all languages, including RTL (Arabic and Hebrew) and CJK (Chinese, Japanese and Korean). Supports nested block-level elements (such as P, DIV),

PhpStorm Mac version
The latest (2018.2.1) professional PHP integrated development tool

SublimeText3 Chinese version
Chinese version, very easy to use

MinGW - Minimalist GNU for Windows
This project is in the process of being migrated to osdn.net/projects/mingw, you can continue to follow us there. MinGW: A native Windows port of the GNU Compiler Collection (GCC), freely distributable import libraries and header files for building native Windows applications; includes extensions to the MSVC runtime to support C99 functionality. All MinGW software can run on 64-bit Windows platforms.







