
Title: Limiting factors and code examples of Ajax technology in network applications
Introduction:
With the development of the Internet and the popularity of Web applications, Ajax technology As an important front-end technology, it is widely used in network applications. Its emergence provides users with better user experience and interactivity. However, like any technology, Ajax has its limitations and limiting factors. This article will explore the limiting factors of Ajax technology in network applications and provide specific code examples.
1. Bandwidth limitation:
Ajax uses HTTP protocol for data transmission, loading data and updating pages asynchronously, which can reduce delays and improve response speed. However, when network bandwidth is low or server load is high, Ajax requests may become slow, affecting the user experience. For example, if there are a large number of Ajax requests on a page at the same time, other requests may not be responded to in a timely manner, causing the page to freeze or fail to load. The way to solve this problem is to use Ajax requests reasonably, avoid too many requests, merge requests, and reduce bandwidth pressure.
2. Browser compatibility:
Ajax technology relies on the browser's XMLHttpRequest object to send and receive asynchronous requests. However, there are some differences in the implementation of XMLHttpRequest by different browsers, resulting in possible compatibility issues. For example, some browsers may not support the latest XMLHttpRequest object or behave differently when handling cross-origin requests. For browser compatibility issues, you can use third-party libraries (such as jQuery's Ajax package) to uniformly handle compatibility issues, or choose the appropriate method by judging the browser type.
The following is a sample code that demonstrates how to use jQuery's Ajax package to send an asynchronous request:
$.ajax({
url: 'example.com/data',
method: 'GET',
dataType: 'json',
success: function(data) {
// 数据成功加载后的处理逻辑
console.log(data);
},
error: function(jqXHR, textStatus, errorThrown) {
// 请求失败的处理逻辑
console.error(textStatus, errorThrown);
}
}); 3. Security issues:
Since Ajax requests are sent asynchronously through JavaScript , so there may be security issues. For example, if a website does not properly validate and filter input data in Ajax requests, it may lead to security issues such as XSS (cross-site scripting attacks) or CSRF (cross-site request forgery). In order to ensure the security of Ajax requests, developers need to verify and filter input data, and perform necessary security checks on the server side.
4. Maintainability and scalability:
Since Ajax requests are performed in an asynchronous manner, it increases the complexity of the code and the challenge of maintainability. For example, when there are multiple Ajax requests on a page, it is difficult to control the order of the requests and the processing process. Without good organization and structure, code can become difficult to read and maintain. In order to improve the maintainability and scalability of the code, a modular development approach can be adopted, using well-encapsulated functions and classes to handle Ajax requests, and appropriate splitting and optimization based on business needs.
Summary:
Ajax technology provides better user experience and interactivity in network applications. However, it also faces limitations such as bandwidth limitations, browser compatibility, security issues, and code maintainability and scalability. Developers need to take appropriate strategies and measures to address these constraints to ensure the smooth application of Ajax technology.
References:
[1] MDN Web Docs. Ajax (Asynchronous JavaScript and XML) [EB/OL]. (2021-07-26). https://developer.mozilla.org/ en-US/docs/Web/Guide/AJAX.
[2] jQuery API Documentation. Ajax[EB/OL].(2021-07-26). https://api.jquery.com/category/ajax/.
The above is the detailed content of Constraints and Limitations of Ajax Technology in Network Applications. For more information, please follow other related articles on the PHP Chinese website!
 Replace String Characters in JavaScriptMar 11, 2025 am 12:07 AM
Replace String Characters in JavaScriptMar 11, 2025 am 12:07 AMDetailed explanation of JavaScript string replacement method and FAQ This article will explore two ways to replace string characters in JavaScript: internal JavaScript code and internal HTML for web pages. Replace string inside JavaScript code The most direct way is to use the replace() method: str = str.replace("find","replace"); This method replaces only the first match. To replace all matches, use a regular expression and add the global flag g: str = str.replace(/fi
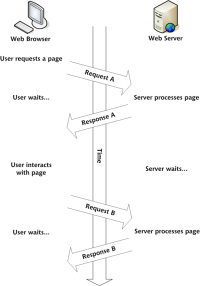 Build Your Own AJAX Web ApplicationsMar 09, 2025 am 12:11 AM
Build Your Own AJAX Web ApplicationsMar 09, 2025 am 12:11 AMSo here you are, ready to learn all about this thing called AJAX. But, what exactly is it? The term AJAX refers to a loose grouping of technologies that are used to create dynamic, interactive web content. The term AJAX, originally coined by Jesse J
 How do I create and publish my own JavaScript libraries?Mar 18, 2025 pm 03:12 PM
How do I create and publish my own JavaScript libraries?Mar 18, 2025 pm 03:12 PMArticle discusses creating, publishing, and maintaining JavaScript libraries, focusing on planning, development, testing, documentation, and promotion strategies.
 10 jQuery Fun and Games PluginsMar 08, 2025 am 12:42 AM
10 jQuery Fun and Games PluginsMar 08, 2025 am 12:42 AM10 fun jQuery game plugins to make your website more attractive and enhance user stickiness! While Flash is still the best software for developing casual web games, jQuery can also create surprising effects, and while not comparable to pure action Flash games, in some cases you can also have unexpected fun in your browser. jQuery tic toe game The "Hello world" of game programming now has a jQuery version. Source code jQuery Crazy Word Composition Game This is a fill-in-the-blank game, and it can produce some weird results due to not knowing the context of the word. Source code jQuery mine sweeping game
 jQuery Parallax Tutorial - Animated Header BackgroundMar 08, 2025 am 12:39 AM
jQuery Parallax Tutorial - Animated Header BackgroundMar 08, 2025 am 12:39 AMThis tutorial demonstrates how to create a captivating parallax background effect using jQuery. We'll build a header banner with layered images that create a stunning visual depth. The updated plugin works with jQuery 1.6.4 and later. Download the
 Auto Refresh Div Content Using jQuery and AJAXMar 08, 2025 am 12:58 AM
Auto Refresh Div Content Using jQuery and AJAXMar 08, 2025 am 12:58 AMThis article demonstrates how to automatically refresh a div's content every 5 seconds using jQuery and AJAX. The example fetches and displays the latest blog posts from an RSS feed, along with the last refresh timestamp. A loading image is optiona
 Getting Started With Matter.js: IntroductionMar 08, 2025 am 12:53 AM
Getting Started With Matter.js: IntroductionMar 08, 2025 am 12:53 AMMatter.js is a 2D rigid body physics engine written in JavaScript. This library can help you easily simulate 2D physics in your browser. It provides many features, such as the ability to create rigid bodies and assign physical properties such as mass, area, or density. You can also simulate different types of collisions and forces, such as gravity friction. Matter.js supports all mainstream browsers. Additionally, it is suitable for mobile devices as it detects touches and is responsive. All of these features make it worth your time to learn how to use the engine, as this makes it easy to create a physics-based 2D game or simulation. In this tutorial, I will cover the basics of this library, including its installation and usage, and provide a
 How do I optimize JavaScript code for performance in the browser?Mar 18, 2025 pm 03:14 PM
How do I optimize JavaScript code for performance in the browser?Mar 18, 2025 pm 03:14 PMThe article discusses strategies for optimizing JavaScript performance in browsers, focusing on reducing execution time and minimizing impact on page load speed.


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

SublimeText3 Chinese version
Chinese version, very easy to use

mPDF
mPDF is a PHP library that can generate PDF files from UTF-8 encoded HTML. The original author, Ian Back, wrote mPDF to output PDF files "on the fly" from his website and handle different languages. It is slower than original scripts like HTML2FPDF and produces larger files when using Unicode fonts, but supports CSS styles etc. and has a lot of enhancements. Supports almost all languages, including RTL (Arabic and Hebrew) and CJK (Chinese, Japanese and Korean). Supports nested block-level elements (such as P, DIV),

Notepad++7.3.1
Easy-to-use and free code editor

DVWA
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is very vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, to help web developers better understand the process of securing web applications, and to help teachers/students teach/learn in a classroom environment Web application security. The goal of DVWA is to practice some of the most common web vulnerabilities through a simple and straightforward interface, with varying degrees of difficulty. Please note that this software

SecLists
SecLists is the ultimate security tester's companion. It is a collection of various types of lists that are frequently used during security assessments, all in one place. SecLists helps make security testing more efficient and productive by conveniently providing all the lists a security tester might need. List types include usernames, passwords, URLs, fuzzing payloads, sensitive data patterns, web shells, and more. The tester can simply pull this repository onto a new test machine and he will have access to every type of list he needs.






