 System Tutorial
System Tutorial Windows Series
Windows Series Microsoft is about to release the third phase of fix patches to solve the Kerberos vulnerability issue in Win10/Win11!
Microsoft is about to release the third phase of fix patches to solve the Kerberos vulnerability issue in Win10/Win11!Microsoft is about to release the third phase of fix patches to solve the Kerberos vulnerability issue in Win10/Win11!
After Phase 1 in November last year and Phase 2 in December last year, Microsoft announced that during the Patch Tuesday event on April 11, this update will also release Phase 3 to fix the vulnerability. Patches make computers more secure.

Kerberos authentication is a computer network security protocol used to authenticate the service of two or more trusted hosts on an untrusted network such as the Internet ask.
The Kerberos authentication problem encountered by Win10 and Win11 devices this time occurred after installing the cumulative update released on the Patch Tuesday event day in November this year, resulting in domain user login failure and domain user remote desktop connection failure. And printing may require domain user authentication.
The translated official description is as follows:
During the Patch Tuesday event day on April 11, 2023, we will release the third phase patch for Kerberos to fix CVEs in IT environments -2022-37967 Issues caused by the vulnerability.
Each stage will increase the default minimum value of CVE-2022-37967 security hardening changes, and continuously increase it to reduce the impact of this vulnerability on the environment.
After the release of the April 11 update, the previous method of setting the KrbtgtFullPacSignature subkey to 0 to disable adding PAC signatures no longer works. The new update mandates that the KrbtgtFullPacSignature subkey be set to a value of 1.
The above is the detailed content of Microsoft is about to release the third phase of fix patches to solve the Kerberos vulnerability issue in Win10/Win11!. For more information, please follow other related articles on the PHP Chinese website!
 How to Change Default View in File Explorer (Windows 11)May 09, 2025 pm 02:02 PM
How to Change Default View in File Explorer (Windows 11)May 09, 2025 pm 02:02 PMCustomize Your Windows 11 File Explorer: A Guide to Setting and Saving Your Preferred View Tired of File Explorer's default view? This guide shows you how to easily change and permanently save your preferred folder view in Windows 11, whether it's l
 Fedora 42 Joins the Windows Subsystem for LinuxMay 09, 2025 am 03:01 AM
Fedora 42 Joins the Windows Subsystem for LinuxMay 09, 2025 am 03:01 AMPushing the boundaries of Linux: exploring unusual applications. Purely for fun, of course. Posts 7 Technically, you can create a WSL image for any compatible Linux distribution. However, officially supported images offer a significantly smoother e
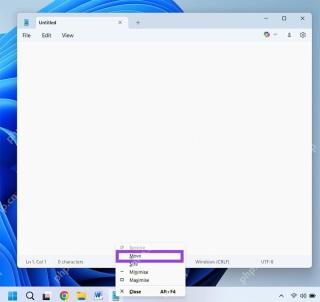 How to Move a Window When You Can't Click on the Title BarMay 09, 2025 am 01:03 AM
How to Move a Window When You Can't Click on the Title BarMay 09, 2025 am 01:03 AMWhen applications unexpectedly extend beyond your screen's edges, accessing their title bars becomes impossible. This is especially common with dual monitors but can occur on single displays as well. This guide offers solutions for regaining control
 This Limited-Edition 'Skeleton” HDD Shows You How It Writes BytesMay 08, 2025 pm 09:04 PM
This Limited-Edition 'Skeleton” HDD Shows You How It Writes BytesMay 08, 2025 pm 09:04 PMThe HD-SKL, a limited-edition hard drive, is a modern take on Buffalo's 1998 Skeleton Hard Disk. The original, a 4.3GB drive with a clear acrylic case, was produced in a limited run of 500 units. While Buffalo cites its 1978 Melco 3533 turntable as
 The New Surface Pro Doesn't Feel ProMay 08, 2025 am 06:01 AM
The New Surface Pro Doesn't Feel ProMay 08, 2025 am 06:01 AMThe new Surface Pro: A step back? Microsoft's latest Surface Pro offers connectivity via two USB-C ports, supporting charging, USB 3.2 data transfer, and DisplayPort 1.4a (up to two 4K monitors at 60Hz). However, the device ships without a power ad
 Microsoft Challenges the MacBook Air With New Surface LaptopMay 08, 2025 am 03:02 AM
Microsoft Challenges the MacBook Air With New Surface LaptopMay 08, 2025 am 03:02 AMMicrosoft's latest Surface Laptop aims to rival the MacBook Air, but with some notable compromises. The absence of a Surface Connect port marks a significant departure from previous models, reflecting the growing prevalence of Thunderbolt and USB do
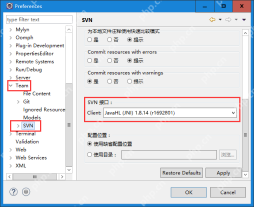 Solve the problem that the svn plugin in eclipse always prompts for password inputMay 07, 2025 pm 05:03 PM
Solve the problem that the svn plugin in eclipse always prompts for password inputMay 07, 2025 pm 05:03 PM1. Background Recently, when using the svn plug-in to manage remote warehouse code in eclipse, prompts to enter passwords are always prompted to enter passwords, which is particularly annoying. After hard work, I finally solved the problem and shared it with you~ 2. Analysis of the password mechanism of the svn plug-in and the cause of the problem. When we use the svn plug-in for the first time and enter the password, a file that saves the password will be generated, and then the svn plug-in will read the username and password information by default every time. When eclipse is started, the configuration information will be automatically read into the program cache. After the password of svn is modified, it is impossible to log in again, and there is no prompt to re-enter the password. At this time, we can delete the relevant configuration files and let the svn plugin prompt us to re-enter the password. However, ec
 How to restore the win8 system details stepsMay 07, 2025 pm 05:00 PM
How to restore the win8 system details stepsMay 07, 2025 pm 05:00 PMThe steps to start system restore in Windows 8 are: 1. Press the Windows key X to open the shortcut menu; 2. Select "Control Panel", enter "System and Security", and click "System"; 3. Select "System Protection", and click "System Restore"; 4. Enter the administrator password and select the restore point. When selecting the appropriate restore point, it is recommended to select the restore point before the problem occurs, or remember a specific date when the system is running well. During the system restore process, if you encounter "The system restore cannot be completed", you can try another restore point or use the "sfc/scannow" command to repair the system files. After restoring, you need to check the system operation status, reinstall or configure the software, and re-back up the data, and create new restore points regularly.


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

SecLists
SecLists is the ultimate security tester's companion. It is a collection of various types of lists that are frequently used during security assessments, all in one place. SecLists helps make security testing more efficient and productive by conveniently providing all the lists a security tester might need. List types include usernames, passwords, URLs, fuzzing payloads, sensitive data patterns, web shells, and more. The tester can simply pull this repository onto a new test machine and he will have access to every type of list he needs.

PhpStorm Mac version
The latest (2018.2.1) professional PHP integrated development tool

Zend Studio 13.0.1
Powerful PHP integrated development environment

SublimeText3 Linux new version
SublimeText3 Linux latest version





