How to install crx file in Edge browser? The Crx file is a browser extension application plug-in, and the plug-in format of many browsers is Crx, even the Edge browser is no exception. So how do we install the crx file for the Edge browser? In fact, this operation is very simple. Let’s take a look at the specific operation method with the editor.
How to install crx files in Edge
1. First open the edge browser and click on the top address bar.
2. Enter "edge://flags/#extensions-on-edge-urls" in the address bar and press Enter.

#3. After entering, change the icon option to "Disabled".

#4. After the modification is completed, click the "three dots" in the upper right corner.

5. Open "Extensions" in the drop-down menu.

#6. Then click the "three horizontal lines" in the upper left corner.

7. Then turn on "Developer Mode" in the lower left corner.

#8. Finally, hold down the crx file with the mouse and drag it to the edge browser to install it.

The above is the detailed content of Edge browser plug-in installation tutorial: How to install crx file. For more information, please follow other related articles on the PHP Chinese website!
 How to Scan Credit Card Numbers in Safari for iPhoneMay 15, 2025 am 09:35 AM
How to Scan Credit Card Numbers in Safari for iPhoneMay 15, 2025 am 09:35 AMThis guide outlines the process of scanning a credit card on an iPhone to add it to Safari's AutoFill library for Saved Cards.Adding a Credit Card to Safari's Saved Credit CardsOnce you scan a credit card into Safari's Saved Credit Cards, you can uti
 Is Baidu a search engine?May 13, 2025 pm 04:45 PM
Is Baidu a search engine?May 13, 2025 pm 04:45 PMBaidu, a leading Chinese search engine, offers tailored features like Baidu Baike and Maps, but its effectiveness drops for non-Chinese searches due to localization.
 Is Yandex safe search?May 13, 2025 pm 04:44 PM
Is Yandex safe search?May 13, 2025 pm 04:44 PMYandex's safe search aims to filter out inappropriate content for safer browsing, especially for kids. Its effectiveness and privacy protection vary, striving to meet international child safety standards.
 Is Yandex a good search engine?May 13, 2025 pm 04:43 PM
Is Yandex a good search engine?May 13, 2025 pm 04:43 PMYandex excels as a search engine in Russia/Eastern Europe, offering superior localized results and unique features like Yandex.Alice and Yandex.Maps, tailored for regional users.
 Is Yandex a Russian search engine?May 13, 2025 pm 04:42 PM
Is Yandex a Russian search engine?May 13, 2025 pm 04:42 PMYandex, a dominant Russian search engine since 1997, outperforms competitors with localized services and Russian language optimization. It offers unique features like Yandex.Metrica and Yandex.Taxi, setting it apart from Google.
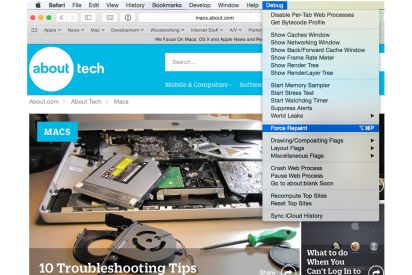 How to Enable Safari's Debug Menu to Gain Added CapabilitiesMay 13, 2025 am 09:41 AM
How to Enable Safari's Debug Menu to Gain Added CapabilitiesMay 13, 2025 am 09:41 AMSafari long had a hidden Debug menu that contained useful capabilities. Originally intended to assist developers in debugging web pages and the JavaScript code that runs on them, the debug menu was hidden away because the commands that were included
 Our Favorite Web Browsers for the iPadMay 12, 2025 am 09:20 AM
Our Favorite Web Browsers for the iPadMay 12, 2025 am 09:20 AMiPad browser competition: Chrome, iCab, Diigo and others Chrome: All-round browser Advantages: Frequent updates, high security; rich extensions, highly customized; simple interface; powerful search engine support. Disadvantages: High resource utilization; may involve personal data collection. Chrome has been the most popular alternative to Safari since its launch, offering a fast and convenient browsing experience and supports sync with Chrome browser on your desktop/laptop. Its unique cross-device webpage opening feature allows you to continue browsing open webpages on other devices on your iPad. iCab: Efficiency improvement device Advantages: Customizable search engine;
 6 Website Time Limiter Apps to Minimize DistractionsMay 11, 2025 am 09:48 AM
6 Website Time Limiter Apps to Minimize DistractionsMay 11, 2025 am 09:48 AMEfficient time management: Six best time management applications recommended This article recommends six excellent applications and extensions to help you effectively manage time, improve work efficiency, and say goodbye to time waste. 1. StayFocused (Chrome extension): Accurately control website access time StayFocused is a Chrome extension that helps you manage your time by limiting your access to websites that are prone to waste time. You can set the maximum daily visit time for each website, and once the limit is reached, these sites will be blocked until the end of the day. Insufficient: There are limited options and some features need to be paid. 2. SelfControl (Mac application): Complete screen


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Atom editor mac version download
The most popular open source editor

WebStorm Mac version
Useful JavaScript development tools

SublimeText3 English version
Recommended: Win version, supports code prompts!

Dreamweaver Mac version
Visual web development tools

Safe Exam Browser
Safe Exam Browser is a secure browser environment for taking online exams securely. This software turns any computer into a secure workstation. It controls access to any utility and prevents students from using unauthorized resources.






