 Technology peripherals
Technology peripherals AI
AI Clarke Rodgers, director of corporate strategy at Amazon Cloud Technology, explains security strategies in the era of generative AI
Clarke Rodgers, director of corporate strategy at Amazon Cloud Technology, explains security strategies in the era of generative AIAs generative artificial intelligence develops rapidly around the world, how can we quickly keep up with business changes and build a zero-trust system to ensure the effectiveness of security practices?
"Security has always been the top priority of Amazon Cloud Technology. We have embedded security, compliance and privacy protection functions into product applications, and users do not need to worry about the security of the underlying infrastructure. Even in the era of generative AI, Users can still get the same experience!" Clarke Rodgers, Director of Enterprise Strategy at Amazon Cloud Technology, said in an interview with the media during the re:Invent Global Conference that compared with other companies that provide large models, Amazon Cloud Technology can ensure that users are more private. Use large models in the environment to ensure that the company's sensitive data will not be leaked, let alone used for other companies' large model training. Users can focus on building applications on the cloud and introduce large models into actual business scenarios of the enterprise

Clarke Rodgers, Director of Corporate Strategy, Amazon Cloud Technology
Before joining Amazon Cloud Technology, Clarke Rodgers was a leader in enterprise digital transformation and large-scale cloud business migration. He specializes in listening to clients, gaining experience, and guiding business development. In the seven years since he entered Amazon Cloud Technology, he has been understanding the latest trends in the market in the same way. Over the years, he has met with more than 750 business executives, proving that enterprises are using the latest technologies related to security compliance and privacy protection while using the cloud. Not only do they want to use the latest security solutions on the cloud, they also want to apply these solutions to the entire business network of the enterprise
Rewritten content: with secure platform and tools
Although generative AI has become the protagonist of global technological innovation this year, Amazon Cloud Technology began its security strategic actions as early as the era of artificial intelligence. For example, Amazon Inspector and Amazon Detective are important products launched by Amazon in the past few years
Amazon Inspector is a vulnerability management service that continuously scans enterprise workloads for software vulnerabilities and potential security risks. Amazon Checker automatically discovers and scans running Amazon EC2 instances, container images in the Amazon Elastic Container Registry (Amazon ECR), and Lambda functions for known software vulnerabilities and accidental network leaks. If there are vulnerabilities in the user's use of generative artificial intelligence, Amazon Checker can make suggestions for fixing the vulnerabilities by inspecting the Lambda code. Usage of the app is gradually increasing
Similarly, Amazon Detective is also a popular application that is often used by chief security officers, information directors, etc., mainly to check whether there are security issues in critical applications or infrastructure. Amazon Detective's newest feature uses artificial intelligence and machine learning to detect problems in applications or infrastructure and group them for easy viewing and analysis by analysts. Detective provides pre-built data aggregation, summarization and contextual capabilities to help users quickly analyze and determine the nature and scope of possible security issues, etc.
Whether it is artificial intelligence or Internet application scenarios, new changes often occur in the security field. We must go all out in terms of technology and strategies to protect the door of security. Taking data loss as an example, although corporate employees have strong security awareness in terms of subjective awareness, they may have shared customer data unconsciously. For example, customer data was used in an artificial intelligence program based on the public network, but it fell into a dangerous situation without knowing it
Safe large model
Many applications of Amazon Cloud Technology can fundamentally prevent security incidents from occurring. For example, Amazon Bedrock adopts a safer and more responsible technology system to enable users to introduce generative artificial intelligence into enterprise production scenarios in the simplest way. Based on years of enterprise-level data management experience, Amazon Cloud Technology knows how to protect data, ensure that sensitive data is used correctly through reasonable management mechanisms and powerful applications, and truly achieve data manageability and availability!
On Amazon Bedrock, all customer data of the user is encrypted and only the user can access it. Amazon Bedrock ensures from a platform design perspective that customer data and related information will not be used to further train the model
If customers want to transfer data, they can use Amazon PrivateLink. With dedicated secure connections to Amazon Bedrock and Virtual Private Networks (VPCs), you ensure data is not exposed on the public network
For users with highly regulatory needs, Amazon Bedrock is HIPAA (Health Insurance Portability and Accountability Act) compliant and can be used under GDPR (EU General Data Protection Regulation) compliance standards. Thus enabling more enterprises to benefit from generative artificial intelligence
Overall, Amazon Cloud Technology has expanded the boundaries of zero trust. Zero trust not only requires customers and systems to strictly prove their identity and credibility, but also allows users to control application access, data and Find a balance between systems to meet the needs of the current business in the new state and new environment.
The above is the detailed content of Clarke Rodgers, director of corporate strategy at Amazon Cloud Technology, explains security strategies in the era of generative AI. For more information, please follow other related articles on the PHP Chinese website!
 I Tried Vibe Coding with Cursor AI and It's Amazing!Mar 20, 2025 pm 03:34 PM
I Tried Vibe Coding with Cursor AI and It's Amazing!Mar 20, 2025 pm 03:34 PMVibe coding is reshaping the world of software development by letting us create applications using natural language instead of endless lines of code. Inspired by visionaries like Andrej Karpathy, this innovative approach lets dev
 How to Use DALL-E 3: Tips, Examples, and FeaturesMar 09, 2025 pm 01:00 PM
How to Use DALL-E 3: Tips, Examples, and FeaturesMar 09, 2025 pm 01:00 PMDALL-E 3: A Generative AI Image Creation Tool Generative AI is revolutionizing content creation, and DALL-E 3, OpenAI's latest image generation model, is at the forefront. Released in October 2023, it builds upon its predecessors, DALL-E and DALL-E 2
 Top 5 GenAI Launches of February 2025: GPT-4.5, Grok-3 & More!Mar 22, 2025 am 10:58 AM
Top 5 GenAI Launches of February 2025: GPT-4.5, Grok-3 & More!Mar 22, 2025 am 10:58 AMFebruary 2025 has been yet another game-changing month for generative AI, bringing us some of the most anticipated model upgrades and groundbreaking new features. From xAI’s Grok 3 and Anthropic’s Claude 3.7 Sonnet, to OpenAI’s G
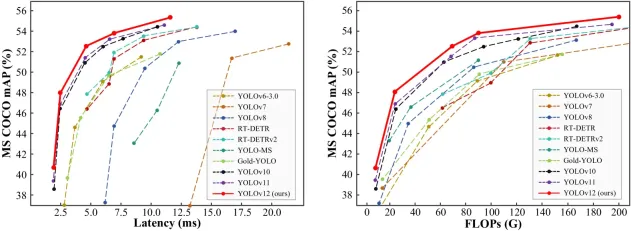 How to Use YOLO v12 for Object Detection?Mar 22, 2025 am 11:07 AM
How to Use YOLO v12 for Object Detection?Mar 22, 2025 am 11:07 AMYOLO (You Only Look Once) has been a leading real-time object detection framework, with each iteration improving upon the previous versions. The latest version YOLO v12 introduces advancements that significantly enhance accuracy
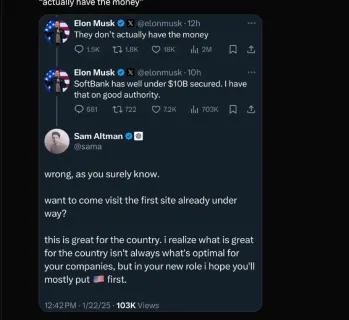 Elon Musk & Sam Altman Clash over $500 Billion Stargate ProjectMar 08, 2025 am 11:15 AM
Elon Musk & Sam Altman Clash over $500 Billion Stargate ProjectMar 08, 2025 am 11:15 AMThe $500 billion Stargate AI project, backed by tech giants like OpenAI, SoftBank, Oracle, and Nvidia, and supported by the U.S. government, aims to solidify American AI leadership. This ambitious undertaking promises a future shaped by AI advanceme
 Sora vs Veo 2: Which One Creates More Realistic Videos?Mar 10, 2025 pm 12:22 PM
Sora vs Veo 2: Which One Creates More Realistic Videos?Mar 10, 2025 pm 12:22 PMGoogle's Veo 2 and OpenAI's Sora: Which AI video generator reigns supreme? Both platforms generate impressive AI videos, but their strengths lie in different areas. This comparison, using various prompts, reveals which tool best suits your needs. T
 Google's GenCast: Weather Forecasting With GenCast Mini DemoMar 16, 2025 pm 01:46 PM
Google's GenCast: Weather Forecasting With GenCast Mini DemoMar 16, 2025 pm 01:46 PMGoogle DeepMind's GenCast: A Revolutionary AI for Weather Forecasting Weather forecasting has undergone a dramatic transformation, moving from rudimentary observations to sophisticated AI-powered predictions. Google DeepMind's GenCast, a groundbreak
 Which AI is better than ChatGPT?Mar 18, 2025 pm 06:05 PM
Which AI is better than ChatGPT?Mar 18, 2025 pm 06:05 PMThe article discusses AI models surpassing ChatGPT, like LaMDA, LLaMA, and Grok, highlighting their advantages in accuracy, understanding, and industry impact.(159 characters)


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

EditPlus Chinese cracked version
Small size, syntax highlighting, does not support code prompt function

Safe Exam Browser
Safe Exam Browser is a secure browser environment for taking online exams securely. This software turns any computer into a secure workstation. It controls access to any utility and prevents students from using unauthorized resources.

Dreamweaver CS6
Visual web development tools

SublimeText3 Linux new version
SublimeText3 Linux latest version

mPDF
mPDF is a PHP library that can generate PDF files from UTF-8 encoded HTML. The original author, Ian Back, wrote mPDF to output PDF files "on the fly" from his website and handle different languages. It is slower than original scripts like HTML2FPDF and produces larger files when using Unicode fonts, but supports CSS styles etc. and has a lot of enhancements. Supports almost all languages, including RTL (Arabic and Hebrew) and CJK (Chinese, Japanese and Korean). Supports nested block-level elements (such as P, DIV),





