Artificial Intelligence and Security: Closely Connected Partners
Artificial intelligence and security are two very important and interesting fields. Although there is a large body of work in each field, little attention has been paid to their integration. When thinking about artificial intelligence in particular, we have entered a stage where the "whitewash" is no longer interesting; we need to apply artificial intelligence to specific verticals and disciplines to benefit from the clear progress

Security has been considered very important for decades but is still not fully engaged and integrated into so-called “core business” functions. Recently, however, as organizations digitize, cloud computing has proven to be the core intermediary between customers, partners, employees, and various processes and experiences between these organizations, and security is getting its due attention. Nearly every organization is beginning to realize that true digital transformation success can only be achieved if security is ensured
Many organizations are still hesitating to what extent they need to continue to invest in security. With the emergence of AI and its operationalization, this will change - not only because AI is the ultimate expression of digital transformation (which means security), but also because attack vectors will multiply and be enabled by AI Gain strength. We are in the age of extreme speed
Therefore, the convergence of artificial intelligence and security can be viewed from two aspects - enabled security and disabled security, the former gives enterprises an advantage, while the latter provides attackers with a large number of wealth.
Let’s pick three interesting areas from each –
Implementing Security – Enterprise Advantage
1. Access Control – Before Artificial Intelligence , UBA (User Behavior Analysis) is just pie in the sky. Now this has become a reality. Enterprises can eventually implement intelligent access control systems that dynamically grant and remove access based on user behavior.
Violation Awareness - Artificial intelligence turns crude pattern matching into intelligent analysis of previously unimaginable volumes of data. Rewritten content: 2. Violation awareness - artificial intelligence turns rough pattern matching into intelligent analysis of previously unimaginable amounts of data
Internal malfeasance refers to employees violating professional ethics and laws and regulations at work the behavior of. By combining the knowledge of an LLM with no-code/low-code tools, security analysts are able to build threat models more efficiently. This approach can help organizations better identify and respond to internal malfeasance, protecting the interests and reputation of the enterprise. Attackers are constantly improving their ability to trick targets into leaking LLM information
2. Spear phishing - Attackers can use artificial intelligence to pinpoint targeting - crafting content that matches culture, gender, region and persona message and even imitate the tone and style.
3. Sophistication of attack patterns – Artificial intelligence enables attackers to make the same data analysis improvements as enterprises. As a result, attack patterns have become more efficient and attack vectors have grown exponentially
In fact, the worlds of artificial intelligence and cybersecurity are intertwined and connected. Both areas must be understood as important parts of the business "operating system". As IT and business merge into one, security and artificial intelligence are becoming watchwords.
However, what makes security different from other fields is that artificial intelligence can not only help enterprises pursue safe operations, but also help bad actors seek to destroy or create chaos
The above is the detailed content of Artificial Intelligence and Security: Closely Connected Partners. For more information, please follow other related articles on the PHP Chinese website!
 AI Game Development Enters Its Agentic Era With Upheaval's Dreamer PortalMay 02, 2025 am 11:17 AM
AI Game Development Enters Its Agentic Era With Upheaval's Dreamer PortalMay 02, 2025 am 11:17 AMUpheaval Games: Revolutionizing Game Development with AI Agents Upheaval, a game development studio comprised of veterans from industry giants like Blizzard and Obsidian, is poised to revolutionize game creation with its innovative AI-powered platfor
 Uber Wants To Be Your Robotaxi Shop, Will Providers Let Them?May 02, 2025 am 11:16 AM
Uber Wants To Be Your Robotaxi Shop, Will Providers Let Them?May 02, 2025 am 11:16 AMUber's RoboTaxi Strategy: A Ride-Hail Ecosystem for Autonomous Vehicles At the recent Curbivore conference, Uber's Richard Willder unveiled their strategy to become the ride-hail platform for robotaxi providers. Leveraging their dominant position in
 AI Agents Playing Video Games Will Transform Future RobotsMay 02, 2025 am 11:15 AM
AI Agents Playing Video Games Will Transform Future RobotsMay 02, 2025 am 11:15 AMVideo games are proving to be invaluable testing grounds for cutting-edge AI research, particularly in the development of autonomous agents and real-world robots, even potentially contributing to the quest for Artificial General Intelligence (AGI). A
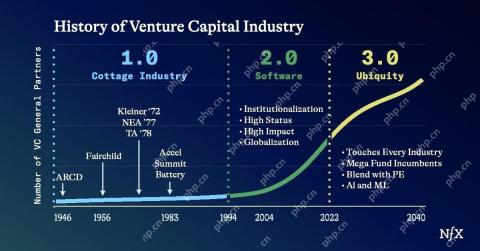 The Startup Industrial Complex, VC 3.0, And James Currier's ManifestoMay 02, 2025 am 11:14 AM
The Startup Industrial Complex, VC 3.0, And James Currier's ManifestoMay 02, 2025 am 11:14 AMThe impact of the evolving venture capital landscape is evident in the media, financial reports, and everyday conversations. However, the specific consequences for investors, startups, and funds are often overlooked. Venture Capital 3.0: A Paradigm
 Adobe Updates Creative Cloud And Firefly At Adobe MAX London 2025May 02, 2025 am 11:13 AM
Adobe Updates Creative Cloud And Firefly At Adobe MAX London 2025May 02, 2025 am 11:13 AMAdobe MAX London 2025 delivered significant updates to Creative Cloud and Firefly, reflecting a strategic shift towards accessibility and generative AI. This analysis incorporates insights from pre-event briefings with Adobe leadership. (Note: Adob
 Everything Meta Announced At LlamaConMay 02, 2025 am 11:12 AM
Everything Meta Announced At LlamaConMay 02, 2025 am 11:12 AMMeta's LlamaCon announcements showcase a comprehensive AI strategy designed to compete directly with closed AI systems like OpenAI's, while simultaneously creating new revenue streams for its open-source models. This multifaceted approach targets bo
 The Brewing Controversy Over The Proposition That AI Is Nothing More Than Just Normal TechnologyMay 02, 2025 am 11:10 AM
The Brewing Controversy Over The Proposition That AI Is Nothing More Than Just Normal TechnologyMay 02, 2025 am 11:10 AMThere are serious differences in the field of artificial intelligence on this conclusion. Some insist that it is time to expose the "emperor's new clothes", while others strongly oppose the idea that artificial intelligence is just ordinary technology. Let's discuss it. An analysis of this innovative AI breakthrough is part of my ongoing Forbes column that covers the latest advancements in the field of AI, including identifying and explaining a variety of influential AI complexities (click here to view the link). Artificial intelligence as a common technology First, some basic knowledge is needed to lay the foundation for this important discussion. There is currently a large amount of research dedicated to further developing artificial intelligence. The overall goal is to achieve artificial general intelligence (AGI) and even possible artificial super intelligence (AS)
 Model Citizens, Why AI Value Is The Next Business YardstickMay 02, 2025 am 11:09 AM
Model Citizens, Why AI Value Is The Next Business YardstickMay 02, 2025 am 11:09 AMThe effectiveness of a company's AI model is now a key performance indicator. Since the AI boom, generative AI has been used for everything from composing birthday invitations to writing software code. This has led to a proliferation of language mod


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

SecLists
SecLists is the ultimate security tester's companion. It is a collection of various types of lists that are frequently used during security assessments, all in one place. SecLists helps make security testing more efficient and productive by conveniently providing all the lists a security tester might need. List types include usernames, passwords, URLs, fuzzing payloads, sensitive data patterns, web shells, and more. The tester can simply pull this repository onto a new test machine and he will have access to every type of list he needs.

Notepad++7.3.1
Easy-to-use and free code editor

DVWA
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is very vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, to help web developers better understand the process of securing web applications, and to help teachers/students teach/learn in a classroom environment Web application security. The goal of DVWA is to practice some of the most common web vulnerabilities through a simple and straightforward interface, with varying degrees of difficulty. Please note that this software

Dreamweaver CS6
Visual web development tools

MinGW - Minimalist GNU for Windows
This project is in the process of being migrated to osdn.net/projects/mingw, you can continue to follow us there. MinGW: A native Windows port of the GNU Compiler Collection (GCC), freely distributable import libraries and header files for building native Windows applications; includes extensions to the MSVC runtime to support C99 functionality. All MinGW software can run on 64-bit Windows platforms.







