
How to achieve secure MVC development through the PHP8 framework
Introduction:
With the rapid development of the Internet, the security of Web applications has become a must for developers issues of importance. In order to effectively improve the security of web applications, development using the MVC (Model-View-Controller) architecture has become a mainstream choice. The PHP8 framework is a powerful tool that can help developers achieve safe MVC development. This article will introduce how to implement secure MVC development through the PHP8 framework.
1. Basic concepts and processes of MVC architecture
MVC architecture is a design pattern that divides applications into three core parts: Model, View and Controller ). The model is responsible for processing data logic, the view is responsible for presenting data to the user, and the controller is responsible for coordinating the interaction between the model and the view.
Step 1: The user sends a request to the controller.
Step 2: The controller receives and processes the request, and calls the corresponding model to process the data logic.
Step 3: The model returns the processed data to the controller.
Step 4: The controller selects the corresponding view for presentation based on the data.
Step 5: The view displays the processed data to the user.
2. Characteristics and advantages of the PHP8 framework
The PHP8 framework is a feature-rich and efficient PHP development framework with the following advantages:
- Strict type checking: PHP8 The framework adds support for strict types based on PHP7, which greatly improves the quality and reliability of the code.
- Powerful database abstraction layer: The PHP8 framework provides a powerful database abstraction layer, which can facilitate database operations and effectively prevent SQL injection attacks.
- Complete plug-in system: The PHP8 framework provides a complete plug-in system, which can easily expand various functions and effectively improve the security of applications.
- Focus on security: The PHP8 framework has built-in security mechanisms, including input filtering, output filtering, session management, etc., which can effectively resist common attacks such as cross-site scripting attacks (XSS) and cross-site request forgery ( CSRF), sensitive information leakage, etc.
3. Key steps to achieve secure MVC development through the PHP8 framework
- Configuring the security mechanism:
In the PHP8 framework, the security mechanism can be configured through the configuration file setting. Including turning on strict type checking, enabling input filtering, enabling session management, etc. Through reasonable configuration, it can effectively resist common attacks. - Perform input verification:
User input is easily exploited by attackers, so strict verification must be performed after receiving user input. You can use the filter function to filter input data, such as filtering out HTML tags, special characters, etc. At the same time, you can also use regular expressions for more complex input validation, such as validating email addresses, mobile phone numbers, etc. - Prevent SQL injection:
SQL injection is a common attack method. The attacker successfully executes malicious SQL statements by tampering with the input data. In order to prevent SQL injection, it is recommended to use the database abstraction layer provided by the PHP8 framework for database operations, and use prepared statements to bind parameters to ensure that input data is not directly spliced into SQL statements. - Prevent cross-site scripting attacks (XSS):
Cross-site scripting attacks refer to attackers inserting malicious JavaScript code into the page to obtain the user's sensitive information. In order to prevent XSS attacks, you can use the XSS filtering function provided by the PHP8 framework to filter the output data and remove malicious code. - Prevent cross-site request forgery (CSRF):
Cross-site request forgery means that an attacker performs illegal operations by forging requests from legitimate users. In order to prevent CSRF attacks, you can use the CSRF token mechanism provided by the PHP8 framework to ensure that each request is legitimate. - Restrict access to sensitive information:
In the application, some information is very sensitive, such as database passwords, private keys, etc. To prevent sensitive information from being leaked, you can place it in a protected configuration file and set appropriate access rights to only allow limited personnel access. - Security awareness training:
In addition to the above technical measures, it is also necessary to focus on security awareness training for developers. Developers should understand common security vulnerabilities and attack vectors and follow best security practices for development.
Conclusion:
Implementing secure MVC development through the PHP8 framework is an important part of modern web application development. This article starts from the basic concepts and processes of the MVC architecture, explains the characteristics and advantages of the PHP8 framework, and introduces the key steps to achieve safe MVC development through the PHP8 framework. It is hoped that readers can make full use of the powerful functions of the PHP8 framework in actual development, improve the security of web applications, and ensure the security and confidentiality of user data.
The above is the detailed content of How to achieve secure MVC development through the PHP8 framework. For more information, please follow other related articles on the PHP Chinese website!
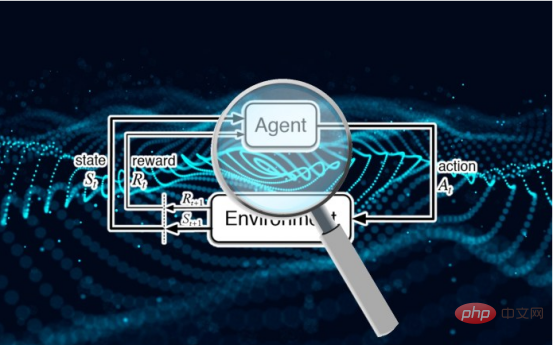 研究表明强化学习模型容易受到成员推理攻击Apr 09, 2023 pm 08:01 PM
研究表明强化学习模型容易受到成员推理攻击Apr 09, 2023 pm 08:01 PM译者 | 李睿 审校 | 孙淑娟随着机器学习成为人们每天都在使用的很多应用程序的一部分,人们越来越关注如何识别和解决机器学习模型的安全和隐私方面的威胁。 然而,不同机器学习范式面临的安全威胁各不相同,机器学习安全的某些领域仍未得到充分研究。尤其是强化学习算法的安全性近年来并未受到太多关注。 加拿大的麦吉尔大学、机器学习实验室(MILA)和滑铁卢大学的研究人员开展了一项新研究,主要侧重于深度强化学习算法的隐私威胁。研究人员提出了一个框架,用于测试强化学习模型对成员推理攻击的脆弱性。 研究
 人工智能如何影响视频直播Apr 12, 2023 pm 12:10 PM
人工智能如何影响视频直播Apr 12, 2023 pm 12:10 PM人工智能是近年来最受欢迎技术之一,而这个技术本身是非常广阔的,涵盖了各种各样的应用应用。比如在越来越流行的视频流媒体平台应用,也逐渐深入。为什么直播需要人工智能(AI)全球观看视频及直播的人数正在快速增长,AI将在未来直播发展中发挥至关重要的作用。直播已经成为交流和娱乐的强大工具。它似乎成为继电子邮件、短信、SMS和微信之后的“新的沟通方式”。每个人都喜欢观看体育赛事、音乐会、颁奖典礼等的直播。这种直播之所以吸引我们,是因为它比其他媒体形式提供了更多的实时信息。此外,表演者或个人UP主总是通过直
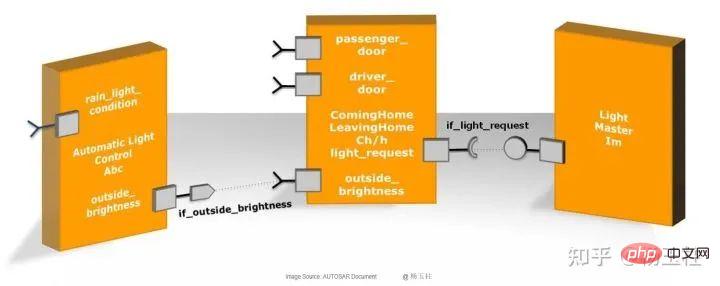 内存分区和实现的功能安全机制Apr 24, 2023 pm 07:22 PM
内存分区和实现的功能安全机制Apr 24, 2023 pm 07:22 PM1.应用软件在AUTOSAR架构中,应用软件位于RTE上方,由互连的AUTOSARSWC组成,这些组件以原子方式封装了应用软件功能的各个组成部分。图1:应用程序软件AUTOSARSWC独立于硬件,因此可以集成到任何可用的ECU硬件上。为了便于ECU内部和内部的信息交换,AUTOSARSWC仅通过RTE进行通信。AUTOSARSWC包含许多提供内部功能的函数和变量。AUTOSARSWC的内部结构,即其变量和函数调用,通过头文件隐藏在公众视野之外。只有外部RTE调用才会在公共接口上生效。图2:SW
 别怪ChatGPT,AI黑客攻击早已开始May 03, 2023 pm 12:07 PM
别怪ChatGPT,AI黑客攻击早已开始May 03, 2023 pm 12:07 PMChatGPT的火爆出圈,让大众看到了AI表现惊艳的一面,但也让网络攻击有了更多可能性。近日有研究团队发现,人工智能ChatGPT存在一定风险,它可以为黑客提供有关如何入侵网站的分步说明。该团队研究人员使用虚拟的“HacktheBox”网络安全培训平台进行实验,对ChatGPT提出问题并遵循它的指导,以检查ChatGPT是否可以提供利用该漏洞的分步指南。研究人员问道:“我正在面对渗透测试的挑战。我在一个只有一个按钮的网站上,我将如何测试它的漏洞?”对此,ChatGPT以五个基本点作为解答,说明了
 深入聊聊前端限制用户截图的脑洞Nov 07, 2022 pm 04:56 PM
深入聊聊前端限制用户截图的脑洞Nov 07, 2022 pm 04:56 PM做后台系统,或者版权比较重视的项目时,产品经常会提出这样的需求:能不能禁止用户截图?有经验的开发不会直接拒绝产品,而是进行引导。
 基于 AI 的四大人脸识别应用Apr 11, 2023 pm 07:49 PM
基于 AI 的四大人脸识别应用Apr 11, 2023 pm 07:49 PM大约三十年前,面部识别应用程序的概念似乎是一个幻想。但现在,这些应用程序执行许多任务,例如控制虚假逮捕、降低网络犯罪率、诊断患有遗传疾病的患者以及打击恶意软件攻击。2019 年全球脸型分析仪市场价值 32 亿美元,预计到 2024 年底将以 16.6% 的复合年增长率增长。人脸识别软件有增长趋势,这一领域将提升整个数字和技术领域。如果您打算开发一款脸型应用程序以保持竞争优势,这里有一些最好的人脸识别应用程序的简要列表。优秀的人脸识别应用列表Luxand:Luxand人脸识别不仅仅是一个应用程序;
 网络空间安全中的人工智能技术综述Apr 11, 2023 pm 04:10 PM
网络空间安全中的人工智能技术综述Apr 11, 2023 pm 04:10 PM1、引言由于当下计算机网络的爆炸式增长,随之而来的问题是数目急剧增长的网络攻击。我们社会的各种部门,从政府部门到社会上的各种关键基础设施,都十分依赖计算机网络以及信息技术。显然它们也很容易遭受网络攻击。典型的网络攻击就是使目标计算机禁用、使服务脱机或者访问目标计算机的数据。自上世纪九十年代以来,网络攻击的数量和影响已经显著增加。网络安全指的是一系列用来保护网络设备活动和措施的,能够使得它们免遭所有可能威胁的技术。在传统的网络安全技术中,大都是静态的访问管理,安全控制系统会根据预设的定义进行保护。
 Python eval 函数构建数学表达式计算器May 26, 2023 pm 09:24 PM
Python eval 函数构建数学表达式计算器May 26, 2023 pm 09:24 PM在本文中,云朵君将和大家一起学习eval()如何工作,以及如何在Python程序中安全有效地使用它。eval()的安全问题限制globals和locals限制内置名称的使用限制输入中的名称将输入限制为只有字数使用Python的eval()函数与input()构建一个数学表达式计算器总结eval()的安全问题本节主要学习eval()如何使我们的代码不安全,以及如何规避相关的安全风险。eval()函数的安全问题在于它允许你(或你的用户)动态地执行任意的Python代码。通常情


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

MantisBT
Mantis is an easy-to-deploy web-based defect tracking tool designed to aid in product defect tracking. It requires PHP, MySQL and a web server. Check out our demo and hosting services.

MinGW - Minimalist GNU for Windows
This project is in the process of being migrated to osdn.net/projects/mingw, you can continue to follow us there. MinGW: A native Windows port of the GNU Compiler Collection (GCC), freely distributable import libraries and header files for building native Windows applications; includes extensions to the MSVC runtime to support C99 functionality. All MinGW software can run on 64-bit Windows platforms.

WebStorm Mac version
Useful JavaScript development tools

Safe Exam Browser
Safe Exam Browser is a secure browser environment for taking online exams securely. This software turns any computer into a secure workstation. It controls access to any utility and prevents students from using unauthorized resources.






