 Operation and Maintenance
Operation and Maintenance Linux Operation and Maintenance
Linux Operation and Maintenance Linux Server Network Security: Protecting Web Interfaces from CSRF Attacks.
Linux Server Network Security: Protecting Web Interfaces from CSRF Attacks.
Linux Server Network Security: Protecting Web Interfaces from CSRF Attacks
In recent years, with the popularity and development of the Internet, people have paid more and more attention to network security. Come higher and higher. As an operating system based on open source principles, Linux has extensive applications and recognition in the field of network security. In the use of Linux servers, protecting the web interface from CSRF (Cross-Site Request Forgery) attacks is a crucial task.
CSRF attack is an attack method that uses malicious code implanted on a trusted website when the victim visits the website to perform illegal operations without the victim's knowledge. This kind of attack takes advantage of design flaws in web applications and performs malicious operations by forging legitimate requests, which may lead to user information leakage, account hijacking, or even more serious consequences.
In order to protect the web interface on the Linux server from CSRF attacks, some effective defense measures will be introduced below.
- Reasonable use of CSRF tokens
CSRF tokens are an important means of defending against CSRF attacks. The server generates and embeds a unique CSRF token when sending the form page to the browser. When the browser submits the form data, the server verifies the validity of the token. If there is no valid CSRF token in the request, the server will reject the request.
- Use the Referer field in the HTTP request header
The Referer field is part of the HTTP request header and is used to indicate the source of the request. By validating the Referer field on the server side, cross-site request forgery can be prevented. Only accept requests from the same site, rejecting requests from illegal sites.
- Restrict the scope and access permissions of Cookies
On a Linux server, you can reduce the risk of CSRF attacks by configuring the scope and access permissions of Cookies. Restricting cookies to specific domain names and setting them to only be transmitted over secure HTTPS connections can effectively reduce the probability of being attacked by hijacked cookies.
- Implementing secure CORS policies
CORS (Cross-Origin Resource Sharing) is a browser mechanism used to limit permissions for cross-domain requests. By adding appropriate CORS policies to the server's response headers, you can restrict requests from specific domain names to pass through, thereby reducing the possibility of CSRF attacks.
- Update and patch systems and applications in a timely manner
The security of a Linux server is closely related to the version of its operating system and applications. Regularly updating systems and applications and promptly patching known vulnerabilities can minimize the risk of CSRF attacks.
To sum up, in terms of protecting the web interface of the Linux server from CSRF attacks, use CSRF tokens reasonably, verify the Referer field, limit the scope and access permissions of cookies, implement secure CORS policies, and timely update and Patching systems and applications are critical protective measures.
Network security is an eternal topic. In the context of the constant emergence of new security threats and attack methods, protecting the server's Web interface from CSRF attacks is an issue that network administrators must take seriously and deal with. By taking effective defensive measures, the security of the system and users can be better protected.
The above is the detailed content of Linux Server Network Security: Protecting Web Interfaces from CSRF Attacks.. For more information, please follow other related articles on the PHP Chinese website!
 如何在 Windows 11 上创建移动热点Apr 17, 2023 pm 06:22 PM
如何在 Windows 11 上创建移动热点Apr 17, 2023 pm 06:22 PM当然,在Android智能手机和Windows11PC之间共享移动互联网可能很有用,尤其是在Wi-Fi不可用时。因此,当其他选项刚刚出现时,知道如何与Windows设备共享移动互联网会非常方便。就像没有Wi-Fi时iPhone可以连接到Mac一样,Android设备也允许用户通过USB和蓝牙将智能手机的互联网连接与任何Windows笔记本电脑连接。对于我们许多人来说,通过电缆连接手机和PC不是一种选择,而通过蓝牙连接互联网可能会很慢。因此,使用智能手机创建W
 实用Word技巧分享:2招轻松解决多图片排版!Apr 01, 2023 am 10:57 AM
实用Word技巧分享:2招轻松解决多图片排版!Apr 01, 2023 am 10:57 AM多图片排版,是Word编辑文档时常见场景之一,几乎每个人都会碰到,对很多人来说仍然是一大难题。当图片数量一多,很多人都不知道图片该怎么摆放,如何快速高效地搞定一组图片? 因为没有掌握系统的套路技巧,每次制作都花费大量时间,做不出满意的效果。今天我就教大家2 招,轻松解决多图片排版!
 如何在网络安全中使用AIApr 14, 2023 pm 02:10 PM
如何在网络安全中使用AIApr 14, 2023 pm 02:10 PMCybersecurity Ventures的报告显示,2021年全球网络犯罪带来的损失为6万亿美元,并预计打击网络犯罪的全球支出在2025年将增至10.5万亿美元,是2015年的三倍之多(3万亿美元)。人工智能,几乎是唯一应对方案。另一家研究机构Statista认为,2020年网络安全领域的人工智能价值已超过100亿美元,并预计到2027年将达到450亿美元。IBM则认为,缺乏人工智能安全的企业,在抵御网络攻击方面的成本是部署了AI自动化防御系统的企业的三倍。来自Meticulous的研究数据
 Microsoft Edge 102.0.1245.41 带来安全修复和 PDF 打印错误解决方案May 06, 2023 pm 07:37 PM
Microsoft Edge 102.0.1245.41 带来安全修复和 PDF 打印错误解决方案May 06, 2023 pm 07:37 PM微软在周末为其Edge浏览器发布了两个小更新。该公司在周五和今天发布了另一个安全更新。虽然周五的更新修复了影响Edge浏览器的安全问题,但今天的更新解决了影响所有基于Chromium的网络浏览器的安全问题。此外,该更新似乎解决了通过Edge浏览器访问PDF文件时无法打印的问题。稳定版本通道的Edge102.0.1245.41被标记为修复了多个漏洞的维护更新。Microsoft尚未更新发行说明。不过,该公司此前已告知Chromium和Edge浏览器存在以下漏洞:
 从“微软安全的下一步”数字活动中可以期待什么Apr 19, 2023 am 10:46 AM
从“微软安全的下一步”数字活动中可以期待什么Apr 19, 2023 am 10:46 AMMicrosoft数字活动的下一步安全计划将于太平洋时间(UTC-8)时间2月24日上午9:00至上午10:30举行。随着无处不在的威胁不断增长,为他们的公司寻找有效安全解决方案的各种组织希望在这次活动中找到一些有价值的技巧和知识。Microsoft的安全下一步计划将强调全面的安全方法对业务增长的重要性。它将欢迎不同的安全专家讨论最新的创新和技术,以减少最新的威胁风险。一些演讲者包括VasuJakkal(微软公司安全、合规和身份副总裁)和JeffPollard(F
 人工智能聊天机器人在网络安全领域的发展趋势如何?Apr 22, 2023 pm 11:13 PM
人工智能聊天机器人在网络安全领域的发展趋势如何?Apr 22, 2023 pm 11:13 PMOpenAI公司推出的聊天机器人ChatGPT有很多很好的用途,但就像任何新技术一样,有些人会利用ChatGPT用于罪恶的目的。从编写电子邮件等相对简单的任务,到撰写论文或编译代码等更复杂的工作,OpenAI公司的人工智能驱动的自然语言处理工具ChatGPT自从推出以来就引起了人们的极大兴趣。当然,ChatGPT并不完美——众所周知,当它误解了从中学习的信息时就会犯错,但许多人将它和其他人工智能工具视为互联网的未来。OpenAI公司在ChatGPT的服务条款中加入了禁止生成恶意软件的条目,其中包
 Zerodium 宣布为 Microsoft Outlook 零点击 RCE 安全漏洞支付 400,000 美元Apr 29, 2023 pm 09:28 PM
Zerodium 宣布为 Microsoft Outlook 零点击 RCE 安全漏洞支付 400,000 美元Apr 29, 2023 pm 09:28 PM<ul><li><strong>点击进入:</strong>ChatGPT工具插件导航大全</li></ul><figureclass="imageimage--expandable"><imgsrc="/uploads/2023041
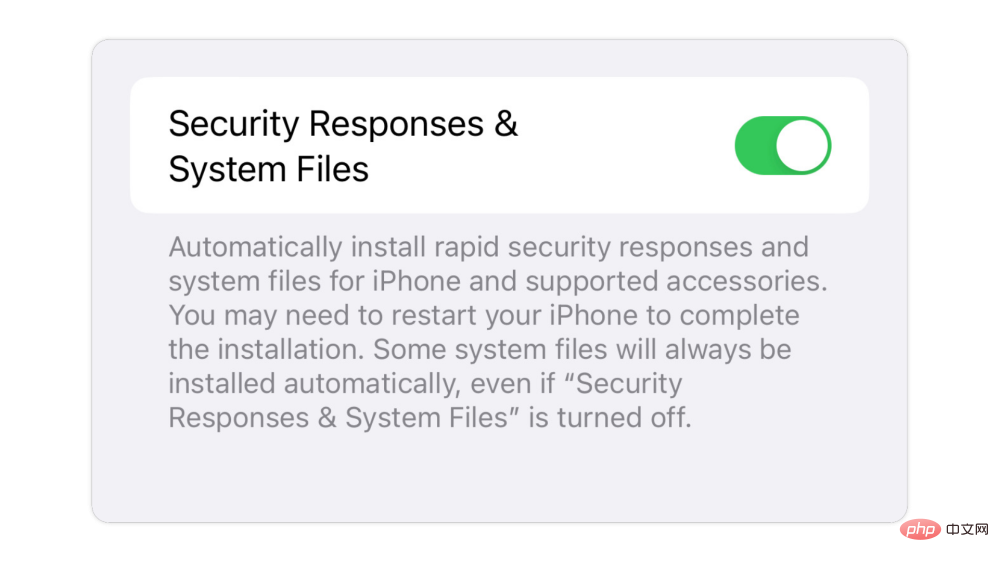 您应该了解的 5 个重要的 iPhone 安全功能Apr 18, 2023 am 09:58 AM
您应该了解的 5 个重要的 iPhone 安全功能Apr 18, 2023 am 09:58 AM虽然iOS16拥有经过重新设计的时髦锁屏,但在其下方,最新的操作系统拥有一系列全新的安全和隐私功能,旨在帮助保护您和您的数据。这里有五项新功能可以更好地保护您的iPhone免受黑客攻击,让您更加安心。快速安全响应iOS以及macOS和iPadOS现在允许自动“快速安全响应”。这使Apple能够快速修补软件(即零日漏洞或其他严重漏洞)并将其发送到数百万台设备,而无需重新启动或任何最终用户交互。这在“设置”>“通用”>“软件更新”>“自动更新”下可用有趣的是,即使关闭了这个


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Dreamweaver CS6
Visual web development tools

ZendStudio 13.5.1 Mac
Powerful PHP integrated development environment

Atom editor mac version download
The most popular open source editor

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Safe Exam Browser
Safe Exam Browser is a secure browser environment for taking online exams securely. This software turns any computer into a secure workstation. It controls access to any utility and prevents students from using unauthorized resources.





