 Operation and Maintenance
Operation and Maintenance Linux Operation and Maintenance
Linux Operation and Maintenance Securing your Linux server: Authentication with the command line
Securing your Linux server: Authentication with the command line
Protect your Linux server: Use the command line for authentication
In the Internet era, server security issues have become particularly important. As a server administrator, you must ensure that your Linux server is secure on the network. In addition to using firewalls and encryption protocols, an effective authentication mechanism is an important part of protecting your server from unauthorized access. In this article, we will discuss how to secure your Linux server using command line authentication.
In Linux systems, there are several common authentication mechanisms, such as password authentication, key authentication, and two-factor authentication. Below are some common command line tools and examples that can help you set up and manage these authentication mechanisms.
- Password Authentication
Password authentication is the most common authentication method where users can verify their identity by entering their username and password. In Linux systems, the passwd command is used to set and change user passwords.
To set a password for a user, use the following command:
sudo passwd username
After entering the above command, you will be prompted for a new password twice. Make sure your password is complex enough and changed regularly.
- Key Authentication
Key authentication is a more secure and convenient authentication method. It is an encryption/decryption mechanism based on public and private keys. First, you need to generate a key pair for the user. Use the following command to generate a key pair:
ssh-keygen -t rsa
The above command will generate an RSA key pair and save it in the .ssh directory under the user's home directory. The public key (id_rsa.pub) will be used for authentication and the private key (id_rsa) will be saved locally on your computer. You can copy the public key to the ~/.ssh/authorized_keys file on the remote server like this:
cat ~/.ssh/id_rsa.pub | ssh username@remote_host "mkdir -p ~/.ssh && cat >> ~/.ssh/authorized_keys"
Now, every time you try to connect to the remote server using ssh, the system will use the public key Authenticate.
- Two-factor authentication
Two-factor authentication combines a password and other factors, such as fingerprint recognition or one-time passwords. For this authentication method, you can use Google Authenticator, an open source two-factor authentication system.
First, you need to install the Google Authenticator client. On Ubuntu, you can install it using the following command:
sudo apt-get install libpam-google-authenticator
You will then need to generate keys for each user you want to enable two-factor authentication. Use the following command:
google-authenticator
The above command will generate a key and a QR code. You can use an app like Google Authenticator to scan the QR code and associate the generated one-time password with the user.
Finally, you need to update the PAM (Pluggable Authentication Modules) configuration file to enable two-factor authentication. Open the /etc/pam.d/sshd file and add the following lines:
auth required pam_google_authenticator.so
After saving and closing the file, restart the SSH service.
This article only introduces some basic command line tools and examples for protecting your Linux server. There are other, more advanced authentication methods and tools available, such as using LDAP or RADIUS for authentication. Whichever method you choose, make sure you update your passwords/keys regularly and only grant access to trusted users.
By leveraging command line tools and authentication mechanisms, you can provide additional security for your Linux server, ensuring that only authorized users can access and manage the server. Remember, protecting your servers is an ongoing task that requires regularly reviewing and updating your security policies.
Protect your server, protect your data, protect your users!
The above is the detailed content of Securing your Linux server: Authentication with the command line. For more information, please follow other related articles on the PHP Chinese website!
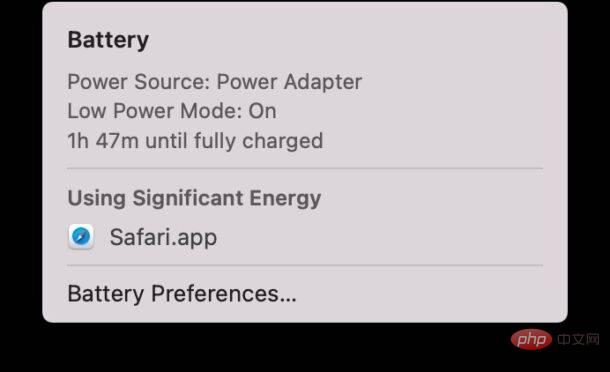 通过命令行在 Mac 上启用低功耗模式Apr 14, 2023 pm 12:13 PM
通过命令行在 Mac 上启用低功耗模式Apr 14, 2023 pm 12:13 PM对于不熟悉的人来说,低功耗模式会减少 Mac 的能源使用,可能会延长电池寿命,但会暂时牺牲性能,但它的处理得很好,对于大多数用户来说,他们不会注意到任何特别的退化。如果您是 Mac 笔记本电脑用户,并试图从 MacBook Pro 或 Air 中获得尽可能长的电池寿命,那么这是一种非常有用的模式。从命令行启用 Mac 低功耗模式从终端,在任何 Mac 笔记本电脑上键入以下命令字符串:sudo pmset -a lowpowermode 1按 sudo 的要求按回车键并输入管理员密码进行身份验证。
 Linux系统中的常用命令和快捷方式Jun 18, 2023 am 08:46 AM
Linux系统中的常用命令和快捷方式Jun 18, 2023 am 08:46 AM随着Linux操作系统的广泛应用,越来越多的人开始需要学习和了解Linux系统中的基本命令和快捷方式。在本文中,我们将介绍一些常用的Linux命令和快捷方式,帮助初学者了解Linux系统,提高工作效率。常用命令1.1ls命令ls命令是Linux中最常用的命令之一。它主要用于列出当前目录下的文件和子目录。常用的选项有:-l:以长格式显示文件信息,包括文件类型
 如何利用MySQL和C++开发一个基于命令行的图书管理系统Sep 20, 2023 pm 01:48 PM
如何利用MySQL和C++开发一个基于命令行的图书管理系统Sep 20, 2023 pm 01:48 PM如何利用MySQL和C++开发一个基于命令行的图书管理系统概要:在本文中,我们将介绍如何使用MySQL和C++开发一个简单的基于命令行的图书管理系统。我们将涵盖从数据库设计到C++代码实现的整个过程,并提供具体的代码示例。介绍:图书管理系统是一个常见的应用程序,用于管理图书馆或个人的图书收藏。通过使用MySQL作为数据库和C++作为编程语言,我们可以方便地实
 javac不是内部或外部命令也不是可运行的程序怎么解决Jun 08, 2023 pm 04:54 PM
javac不是内部或外部命令也不是可运行的程序怎么解决Jun 08, 2023 pm 04:54 PMjavac不是内部或外部命令也不是可运行的程序的解决方法: 1、首先官网下载JDK的最新版本并安装;2、进行系统环境变量配置,在path中添加jdk安装的路径;3、进入电脑命令行界面,输入“java -v”出现版本号即可。
 如何通过Linux命令行工具进行日志聚合和统计?Jul 30, 2023 pm 10:07 PM
如何通过Linux命令行工具进行日志聚合和统计?Jul 30, 2023 pm 10:07 PM如何通过Linux命令行工具进行日志聚合和统计?在管理和维护Linux系统时,日志记录是非常重要的一项工作。通过日志可以查看系统运行情况、排查问题以及进行性能分析。而对于大规模的系统,日志的数量往往非常庞大,如何高效地对日志进行聚合和统计,成为了运维人员面临的一个挑战。在Linux系统中,我们可以利用命令行工具来进行日志聚合和统计。下面将介绍几个常用的命令行
 详解如何增加Linux安全组端口(命令行方式)Jan 29, 2023 pm 04:51 PM
详解如何增加Linux安全组端口(命令行方式)Jan 29, 2023 pm 04:51 PM本篇文章给大家带来了关于Linux的相关知识,其中主要介绍了以 Centos7.x 为例,怎么使用命令行方式来增加Linux的安全组端口,下面一起来看一下,希望对大家有帮助。
 如何使用ThinkPHP6的命令行工具Jun 21, 2023 pm 05:53 PM
如何使用ThinkPHP6的命令行工具Jun 21, 2023 pm 05:53 PM如何使用ThinkPHP6的命令行工具ThinkPHP6是一款开源的PHP框架,它具有丰富的功能和易于使用的特性。其中,命令行工具是ThinkPHP6的一个重要功能,在开发过程中可以提高开发效率和便捷性。本文将介绍如何使用ThinkPHP6的命令行工具。安装ThinkPHP6首先,需要安装ThinkPHP6。可以通过composer命令安装:composer
 测试MySQL连接的高并发性能应如何在命令行进行?Jun 30, 2023 pm 07:25 PM
测试MySQL连接的高并发性能应如何在命令行进行?Jun 30, 2023 pm 07:25 PM如何在命令行中测试MySQL连接的高并发性能?随着互联网应用的不断普及,数据库的高并发性能成为了很多需求的关注点之一。而MySQL作为一个流行的开源数据库,其高并发性能也是被广泛关注的。在测试MySQL连接的高并发性能之前,我们需要先明确一些概念和准备工作:并发连接:指的是同时有多个客户端与数据库建立连接,并且这些连接同时进行数据库操作。连接数限制:MySQ


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

mPDF
mPDF is a PHP library that can generate PDF files from UTF-8 encoded HTML. The original author, Ian Back, wrote mPDF to output PDF files "on the fly" from his website and handle different languages. It is slower than original scripts like HTML2FPDF and produces larger files when using Unicode fonts, but supports CSS styles etc. and has a lot of enhancements. Supports almost all languages, including RTL (Arabic and Hebrew) and CJK (Chinese, Japanese and Korean). Supports nested block-level elements (such as P, DIV),

SublimeText3 English version
Recommended: Win version, supports code prompts!

MinGW - Minimalist GNU for Windows
This project is in the process of being migrated to osdn.net/projects/mingw, you can continue to follow us there. MinGW: A native Windows port of the GNU Compiler Collection (GCC), freely distributable import libraries and header files for building native Windows applications; includes extensions to the MSVC runtime to support C99 functionality. All MinGW software can run on 64-bit Windows platforms.

ZendStudio 13.5.1 Mac
Powerful PHP integrated development environment

Zend Studio 13.0.1
Powerful PHP integrated development environment




