
How to use PHP to implement user rights management
User rights management is a very important part of website development. It can be used to limit user access rights and protect sensitive data. and function. In PHP, user rights management can be achieved through some simple code.
1. Database design
First, we need to design a database table to store user and permission information. The following is a simple example table structure:
CREATE TABLE `users` ( `id` int(11) NOT NULL AUTO_INCREMENT, `username` varchar(50) NOT NULL, `password` varchar(255) NOT NULL, PRIMARY KEY (`id`) ); CREATE TABLE `permissions` ( `id` int(11) NOT NULL AUTO_INCREMENT, `permission` varchar(50) NOT NULL, PRIMARY KEY (`id`) ); CREATE TABLE `user_permissions` ( `id` int(11) NOT NULL AUTO_INCREMENT, `user_id` int(11) NOT NULL, `permission_id` int(11) NOT NULL, PRIMARY KEY (`id`) );
Stores user information in the users table, including the user’s unique identifier id, username and encrypted password.
Store permission information in the permissions table, including the permission's unique identifier id and the permission name permission.
Storage the relationship between users and permissions in the user_permissions table, including association identification id, user ID user_id and permission ID permission_id.
2. User login and permission verification
- User login
User login is the prerequisite for obtaining user permissions. The following is an example login code:
<?php
session_start();
// 数据库连接信息
$servername = "localhost";
$username = "root";
$password = "password";
$dbname = "mydb";
$con = mysqli_connect($servername, $username, $password, $dbname);
// 获取登录表单提交的用户名和密码
$username = $_POST["username"];
$password = $_POST["password"];
// 验证用户名和密码
$sql = "SELECT * FROM users WHERE username = '$username' AND password = '$password'";
$result = mysqli_query($con, $sql);
$row = mysqli_fetch_assoc($result);
if ($row) {
// 用户登录成功,保存用户信息到 session
$_SESSION["user_id"] = $row["id"];
} else {
// 用户名或密码错误,返回登录页面或给出错误提示
}
?>In the above code, first connect to the database through the mysqli_connect function and obtain the username and password from the login form. Then use an SQL query to verify that the username and password entered by the user match those in the database. If the verification passes, use the $_SESSION global variable to save the user's id for subsequent use in permission verification.
- Permission verification
Once the user logs in successfully, we can verify the user's permissions through the following code:
<?php
session_start();
// 验证用户是否登录
if (!isset($_SESSION["user_id"])) {
// 如果用户未登录,根据需求,可以重定向到登录页面或给出错误提示
}
// 获取用户的权限列表
$user_id = $_SESSION["user_id"];
$sql = "SELECT permissions.permission FROM user_permissions INNER JOIN permissions ON user_permissions.permission_id = permissions.id WHERE user_permissions.user_id = $user_id";
$result = mysqli_query($con, $sql);
$permissions = array();
while ($row = mysqli_fetch_assoc($result)) {
$permissions[] = $row["permission"];
}
// 验证用户是否有指定权限
function hasPermission($permission) {
global $permissions;
return in_array($permission, $permissions);
}
?>In the above code, the user is first verified Are you logged in? If the user is not logged in, you can redirect to the login page or give an error prompt based on actual needs.
Then, query the database through the user's id, obtain the user's permission list, and save it in an array. Finally, we can define a hasPermission function that checks whether the user has the specified permissions.
3. Permission Control Example
The following is a simple example that demonstrates how to use user permissions to control website functions:
<?php
require_once "auth.php";
// 验证用户是否有编辑文章的权限
if (hasPermission("edit_article")) {
// 显示编辑文章的按钮
}
?>In the above code, we have introduced the authentication code , and use the hasPermission function to verify whether the user has the edit_article permission. If the user has this permission, a button to edit the article will appear.
Summary:
Through the above code examples, we can see how to use PHP to implement user rights management. First, we need to design a database table to store user and permission information. Then, through user login and permission verification, we can restrict user access and protect sensitive data and functionality. Finally, the functional display of the website can be controlled according to the user's permissions.
The above is the detailed content of How to use PHP to implement user rights management. For more information, please follow other related articles on the PHP Chinese website!
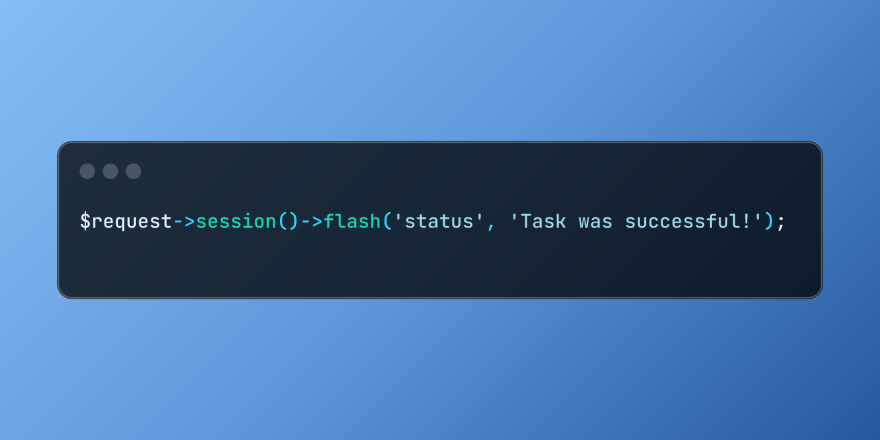 Working with Flash Session Data in LaravelMar 12, 2025 pm 05:08 PM
Working with Flash Session Data in LaravelMar 12, 2025 pm 05:08 PMLaravel simplifies handling temporary session data using its intuitive flash methods. This is perfect for displaying brief messages, alerts, or notifications within your application. Data persists only for the subsequent request by default: $request-
 Build a React App With a Laravel Back End: Part 2, ReactMar 04, 2025 am 09:33 AM
Build a React App With a Laravel Back End: Part 2, ReactMar 04, 2025 am 09:33 AMThis is the second and final part of the series on building a React application with a Laravel back-end. In the first part of the series, we created a RESTful API using Laravel for a basic product-listing application. In this tutorial, we will be dev
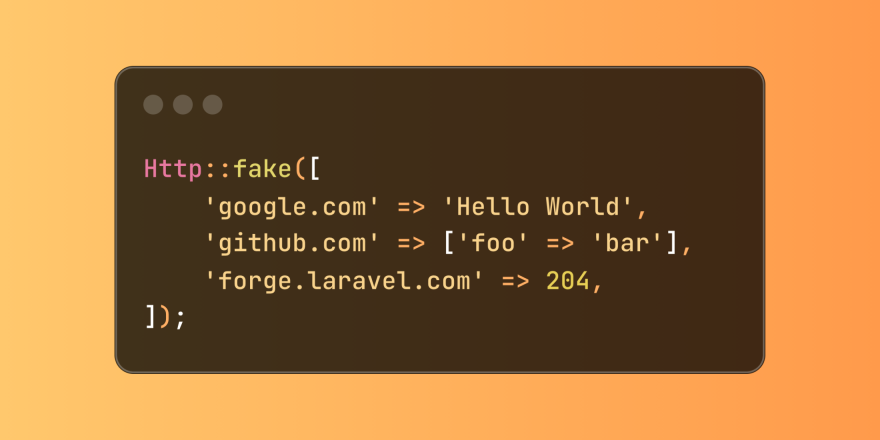 Simplified HTTP Response Mocking in Laravel TestsMar 12, 2025 pm 05:09 PM
Simplified HTTP Response Mocking in Laravel TestsMar 12, 2025 pm 05:09 PMLaravel provides concise HTTP response simulation syntax, simplifying HTTP interaction testing. This approach significantly reduces code redundancy while making your test simulation more intuitive. The basic implementation provides a variety of response type shortcuts: use Illuminate\Support\Facades\Http; Http::fake([ 'google.com' => 'Hello World', 'github.com' => ['foo' => 'bar'], 'forge.laravel.com' =>
 cURL in PHP: How to Use the PHP cURL Extension in REST APIsMar 14, 2025 am 11:42 AM
cURL in PHP: How to Use the PHP cURL Extension in REST APIsMar 14, 2025 am 11:42 AMThe PHP Client URL (cURL) extension is a powerful tool for developers, enabling seamless interaction with remote servers and REST APIs. By leveraging libcurl, a well-respected multi-protocol file transfer library, PHP cURL facilitates efficient execution of various network protocols, including HTTP, HTTPS, and FTP. This extension offers granular control over HTTP requests, supports multiple concurrent operations, and provides built-in security features.
 12 Best PHP Chat Scripts on CodeCanyonMar 13, 2025 pm 12:08 PM
12 Best PHP Chat Scripts on CodeCanyonMar 13, 2025 pm 12:08 PMDo you want to provide real-time, instant solutions to your customers' most pressing problems? Live chat lets you have real-time conversations with customers and resolve their problems instantly. It allows you to provide faster service to your custom
 Notifications in LaravelMar 04, 2025 am 09:22 AM
Notifications in LaravelMar 04, 2025 am 09:22 AMIn this article, we're going to explore the notification system in the Laravel web framework. The notification system in Laravel allows you to send notifications to users over different channels. Today, we'll discuss how you can send notifications ov
 Explain the concept of late static binding in PHP.Mar 21, 2025 pm 01:33 PM
Explain the concept of late static binding in PHP.Mar 21, 2025 pm 01:33 PMArticle discusses late static binding (LSB) in PHP, introduced in PHP 5.3, allowing runtime resolution of static method calls for more flexible inheritance.Main issue: LSB vs. traditional polymorphism; LSB's practical applications and potential perfo
 PHP Logging: Best Practices for PHP Log AnalysisMar 10, 2025 pm 02:32 PM
PHP Logging: Best Practices for PHP Log AnalysisMar 10, 2025 pm 02:32 PMPHP logging is essential for monitoring and debugging web applications, as well as capturing critical events, errors, and runtime behavior. It provides valuable insights into system performance, helps identify issues, and supports faster troubleshoot


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

SAP NetWeaver Server Adapter for Eclipse
Integrate Eclipse with SAP NetWeaver application server.

Dreamweaver Mac version
Visual web development tools

ZendStudio 13.5.1 Mac
Powerful PHP integrated development environment

Atom editor mac version download
The most popular open source editor

SublimeText3 Linux new version
SublimeText3 Linux latest version






