 Backend Development
Backend Development PHP Tutorial
PHP Tutorial PHP learning steps: How to use the permission control management system
PHP learning steps: How to use the permission control management system
PHP learning steps: How to use the permission control management system
Introduction:
In modern software development, permission control is a very important part. Whether it is a website management system or a backend management system, permission control is an essential function. This article will introduce how to use the PHP programming language to implement a basic permission control management system.
Step 1: Create a database table
First, we need to create a database to store user and permission information. We can use MySQL or other relational databases to create tables.
CREATE TABLE `users` ( `id` int(11) NOT NULL AUTO_INCREMENT, `username` varchar(255) NOT NULL, `password` varchar(255) NOT NULL, PRIMARY KEY (`id`) ); CREATE TABLE `permissions` ( `id` int(11) NOT NULL AUTO_INCREMENT, `user_id` int(11) NOT NULL, `permission` varchar(255) NOT NULL, PRIMARY KEY (`id`), FOREIGN KEY (`user_id`) REFERENCES `users`(`id`) ON DELETE CASCADE );
The above table will be used to store user information and permission information. The 'users' table is used to store user names and passwords, and the 'permissions' table is used to store the correspondence between users and permissions, where 'user_id' is the foreign key of the 'user' table.
Step 2: Create PHP code
We will use PHP to write code to implement the permission control management system. First, we need to connect to the database.
<?php
$servername = "localhost";
$username = "your_username";
$password = "your_password";
$dbname = "your_database";
$conn = new mysqli($servername, $username, $password, $dbname);
if ($conn->connect_error) {
die("连接失败: " . $conn->connect_error);
}
// 程序继续执行...
?>In the above code, you need to replace 'your_username' and 'your_password' with your own database username and password. 'your_database' needs to be replaced with your own database name.
Step 3: User login and verification
Next, we need to implement the user login and verification functions. First, create a login form.
<form action="login.php" method="POST"> <input type="text" name="username" placeholder="用户名"> <input type="password" name="password" placeholder="密码"> <input type="submit" value="登录"> </form>
Then, create a new file called 'login.php' to handle form submission.
<?php
session_start();
if ($_SERVER["REQUEST_METHOD"] == "POST") {
$username = $_POST["username"];
$password = $_POST["password"];
$sql = "SELECT * FROM users WHERE username = '$username' AND password = '$password'";
$result = $conn->query($sql);
if ($result->num_rows > 0) {
$row = $result->fetch_assoc();
$_SESSION["user_id"] = $row["id"];
header("Location: dashboard.php");
} else {
echo "用户名或密码错误";
}
}
$conn->close();
?>In the above code, we use the $_SESSION variable to store the user's id for permission verification in other pages. If the login is successful, we will redirect the user to a new page called 'dashboard.php'.
Step 4: Permission verification
In each page that requires permission control, we need to first verify whether the user has the corresponding permissions. The following is the code of a sample page:
<?php
session_start();
if(!isset($_SESSION["user_id"])){
header("Location: login.php");
exit;
}
$user_id = $_SESSION["user_id"];
$sql = "SELECT * FROM permissions WHERE user_id = $user_id AND permission = 'admin'";
$result = $conn->query($sql);
if ($result->num_rows == 0) {
echo "权限不足";
exit;
}
// 程序继续执行...
?>
In the above code, we first verify whether $_SESSION["user_id"] exists, and if it does not exist, redirect the user to the login page . We then query the database based on the user id and check if the user has permission named 'admin'. If there is no permission, the program will output "Insufficient permissions" and stop execution.
Conclusion:
Through the above steps, we successfully implemented a basic permission control management system. You can continue to extend this system and add more permissions and functions.
Of course, this is just an entry-level example. In actual projects, you may need more functions and more complex permission control logic. Based on in-depth study of PHP and databases, you can further improve your permission control capabilities.
I hope this article will be helpful to you in learning PHP and implementing a permission control management system!
The above is the detailed content of PHP learning steps: How to use the permission control management system. For more information, please follow other related articles on the PHP Chinese website!
 11 Best PHP URL Shortener Scripts (Free and Premium)Mar 03, 2025 am 10:49 AM
11 Best PHP URL Shortener Scripts (Free and Premium)Mar 03, 2025 am 10:49 AMLong URLs, often cluttered with keywords and tracking parameters, can deter visitors. A URL shortening script offers a solution, creating concise links ideal for social media and other platforms. These scripts are valuable for individual websites a
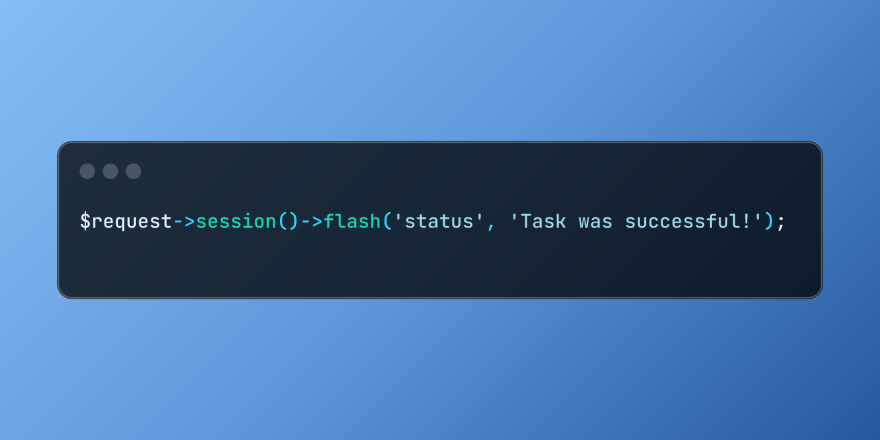 Working with Flash Session Data in LaravelMar 12, 2025 pm 05:08 PM
Working with Flash Session Data in LaravelMar 12, 2025 pm 05:08 PMLaravel simplifies handling temporary session data using its intuitive flash methods. This is perfect for displaying brief messages, alerts, or notifications within your application. Data persists only for the subsequent request by default: $request-
 Build a React App With a Laravel Back End: Part 2, ReactMar 04, 2025 am 09:33 AM
Build a React App With a Laravel Back End: Part 2, ReactMar 04, 2025 am 09:33 AMThis is the second and final part of the series on building a React application with a Laravel back-end. In the first part of the series, we created a RESTful API using Laravel for a basic product-listing application. In this tutorial, we will be dev
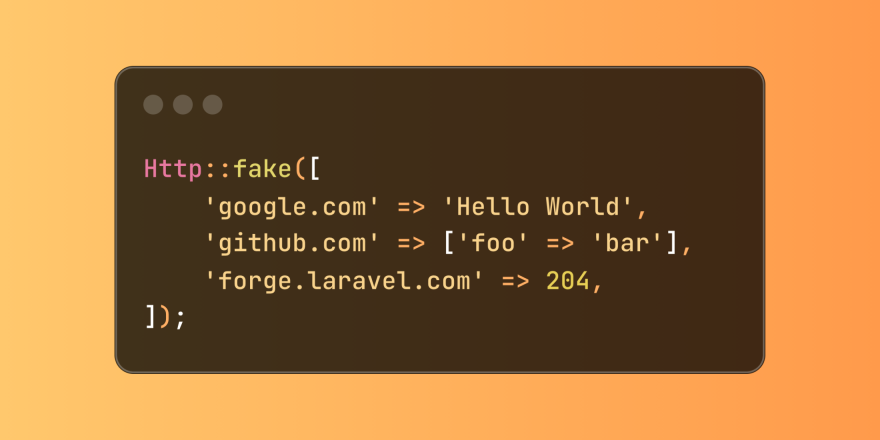 Simplified HTTP Response Mocking in Laravel TestsMar 12, 2025 pm 05:09 PM
Simplified HTTP Response Mocking in Laravel TestsMar 12, 2025 pm 05:09 PMLaravel provides concise HTTP response simulation syntax, simplifying HTTP interaction testing. This approach significantly reduces code redundancy while making your test simulation more intuitive. The basic implementation provides a variety of response type shortcuts: use Illuminate\Support\Facades\Http; Http::fake([ 'google.com' => 'Hello World', 'github.com' => ['foo' => 'bar'], 'forge.laravel.com' =>
 cURL in PHP: How to Use the PHP cURL Extension in REST APIsMar 14, 2025 am 11:42 AM
cURL in PHP: How to Use the PHP cURL Extension in REST APIsMar 14, 2025 am 11:42 AMThe PHP Client URL (cURL) extension is a powerful tool for developers, enabling seamless interaction with remote servers and REST APIs. By leveraging libcurl, a well-respected multi-protocol file transfer library, PHP cURL facilitates efficient execution of various network protocols, including HTTP, HTTPS, and FTP. This extension offers granular control over HTTP requests, supports multiple concurrent operations, and provides built-in security features.
 12 Best PHP Chat Scripts on CodeCanyonMar 13, 2025 pm 12:08 PM
12 Best PHP Chat Scripts on CodeCanyonMar 13, 2025 pm 12:08 PMDo you want to provide real-time, instant solutions to your customers' most pressing problems? Live chat lets you have real-time conversations with customers and resolve their problems instantly. It allows you to provide faster service to your custom
 Announcement of 2025 PHP Situation SurveyMar 03, 2025 pm 04:20 PM
Announcement of 2025 PHP Situation SurveyMar 03, 2025 pm 04:20 PMThe 2025 PHP Landscape Survey investigates current PHP development trends. It explores framework usage, deployment methods, and challenges, aiming to provide insights for developers and businesses. The survey anticipates growth in modern PHP versio
 Notifications in LaravelMar 04, 2025 am 09:22 AM
Notifications in LaravelMar 04, 2025 am 09:22 AMIn this article, we're going to explore the notification system in the Laravel web framework. The notification system in Laravel allows you to send notifications to users over different channels. Today, we'll discuss how you can send notifications ov


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Safe Exam Browser
Safe Exam Browser is a secure browser environment for taking online exams securely. This software turns any computer into a secure workstation. It controls access to any utility and prevents students from using unauthorized resources.

SublimeText3 Linux new version
SublimeText3 Linux latest version

SublimeText3 Chinese version
Chinese version, very easy to use

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Mac version
God-level code editing software (SublimeText3)





