 Technology peripherals
Technology peripherals AI
AI Implementing MySQL Data Locking Strategy: A Java Solution to Concurrency Conflicts
Implementing MySQL Data Locking Strategy: A Java Solution to Concurrency ConflictsImplementing MySQL Data Locking Strategy: A Java Solution to Concurrency Conflicts
In a multi-threaded environment, simultaneous read and write operations on the MySQL database may cause data conflicts and inconsistencies. In order to resolve concurrency conflicts, we can use data locking strategies to ensure data consistency and integrity. Next, we will introduce how to use Java to implement MySQL data locking strategy, and provide relevant precautions and best practices
1. Causes of concurrency conflicts
If multiple threads modify the same piece of data at the same time, it will usually lead to concurrency conflicts. In this case, if no measures are taken, the following problems may occur:
2. Concurrency conflicts: When multiple threads read and modify the same data at the same time, The last modification will overwrite the previous modification, causing the previous modification to be lost
2. Dirty reading: When one thread is reading data, another thread modifies the data, causing the The data read by one thread is inconsistent
3. Non-repeatable reading: In the same transaction, if other threads modify the same data during the execution of the transaction, then both The results of reading the data will be inconsistent
4. Phantom reading: In a transaction, the result sets obtained by two queries are inconsistent because other threads inserted the data during the execution of the transaction. New data that meets the query conditions
2. The concept of lock mechanism
MySQL provides a variety of lock mechanisms to resolve concurrency conflicts. , including common lock mechanisms
1. Multiple threads can acquire shared locks at the same time for reading the same data. This lock is called a Shared Lock )
2. Exclusive Lock: Only one thread is allowed to obtain an exclusive lock for data writing operations
3 , Steps to use Java to implement MySQL data locking strategy
1.Introduce the required Java class libraries and modules, including database connection libraries and related thread libraries
2. Establish a database connection through code and use transactions to operate
3. In order to prevent concurrent modifications, use appropriate The lock mechanism locks related data
4. Complete the transaction and release the locked data
5. Disconnect the database connection
4. Code example for implementing MySQL data locking strategy in Java
This is a simple Java code example that demonstrates how to use Java to implement MySQL data Locking strategy
import java.sql.Connection;import java.sql.DriverManager;import java.sql.PreparedStatement;import java.sql.ResultSet;import java.sql.SQLException;public class MySQLDataLockingExample {public static void main(String[] args) {try (Connection connection = DriverManager.getConnection("jdbc:mysql://localhost:3306/mydatabase", "username", "password")) {connection.setAutoCommit(false);// 对需要锁定的数据执行查询操作String selectQuery = "SELECT * FROM mytable WHERE id = ? FOR UPDATE";PreparedStatement selectStatement = connection.prepareStatement(selectQuery);selectStatement.setInt(1, 1);ResultSet resultSet = selectStatement.executeQuery();// 对查询结果进行处理和修改操作// 提交事务connection.commit();} catch (SQLException e) {e.printStackTrace();}}}
In the above code example, a connection to the MySQL database is first established, and automatic submission is set to false, indicating that manual transactions are used. Then use the PreparedStatement object to execute the data query that requires locking, and achieve exclusive locking of the row of data by adding a "FOR UPDATE" statement. The query results can then be further processed and modified. Finally, commit the transaction by calling connection.commit() and catch possible SQL exceptions in exception handling.
5. Precautions and best practices
When implementing the MySQL data locking strategy in Java, you need to keep the following points and best practices in mind :
The rewritten sentence is as follows: 2. The lock scope should be minimized and only necessary data should be locked to reduce lock conflicts and improve concurrency performance
#2. In practical applications, it is necessary to think about how to detect and handle possible occurrences Deadlock, and take corresponding measures
3. In order to avoid the lock waiting time being too long, you can set the lock timeout, and the lock will be automatically released after the set time is exceeded
4. Reasonably demarcate the scope of the transaction: clarify the boundaries of the transaction to reduce the time the transaction holds the lock, thereby reducing the risk of concurrency conflicts
5 , Performance testing and optimization: Test and evaluate the data locking strategy, optimize and adjust as needed to enhance the throughput and response time of the system
By using appropriate data locking strategies, we can resolve conflict issues in a concurrent environment to ensure data consistency and integrity of the MySQL database. The steps to implement the MySQL data locking strategy include establishing a database connection, using an appropriate locking mechanism to lock related data, committing the transaction, and closing the database connection. In practice, it is necessary to pay attention to issues such as lock range, deadlock detection, and lock timeout, and perform performance testing and optimization. Adhering to these considerations and best practices can ensure the stability and reliability of Java's MySQL data locking strategy
The above is the detailed content of Implementing MySQL Data Locking Strategy: A Java Solution to Concurrency Conflicts. For more information, please follow other related articles on the PHP Chinese website!
 Personal Hacking Will Be A Pretty Fierce BearMay 11, 2025 am 11:09 AM
Personal Hacking Will Be A Pretty Fierce BearMay 11, 2025 am 11:09 AMCyberattacks are evolving. Gone are the days of generic phishing emails. The future of cybercrime is hyper-personalized, leveraging readily available online data and AI to craft highly targeted attacks. Imagine a scammer who knows your job, your f
 Pope Leo XIV Reveals How AI Influenced His Name ChoiceMay 11, 2025 am 11:07 AM
Pope Leo XIV Reveals How AI Influenced His Name ChoiceMay 11, 2025 am 11:07 AMIn his inaugural address to the College of Cardinals, Chicago-born Robert Francis Prevost, the newly elected Pope Leo XIV, discussed the influence of his namesake, Pope Leo XIII, whose papacy (1878-1903) coincided with the dawn of the automobile and
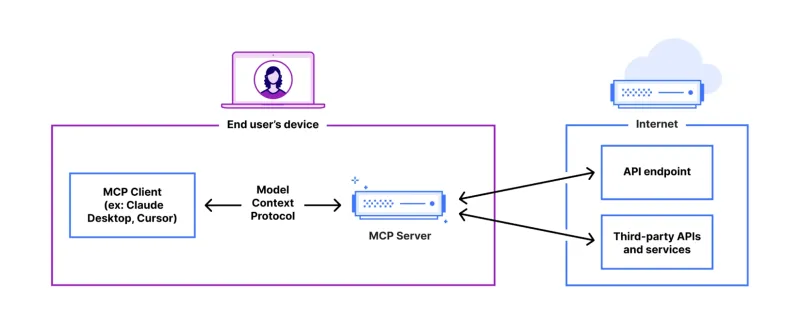 FastAPI-MCP Tutorial for Beginners and Experts - Analytics VidhyaMay 11, 2025 am 10:56 AM
FastAPI-MCP Tutorial for Beginners and Experts - Analytics VidhyaMay 11, 2025 am 10:56 AMThis tutorial demonstrates how to integrate your Large Language Model (LLM) with external tools using the Model Context Protocol (MCP) and FastAPI. We'll build a simple web application using FastAPI and convert it into an MCP server, enabling your L
 Dia-1.6B TTS : Best Text-to-Dialogue Generation Model - Analytics VidhyaMay 11, 2025 am 10:27 AM
Dia-1.6B TTS : Best Text-to-Dialogue Generation Model - Analytics VidhyaMay 11, 2025 am 10:27 AMExplore Dia-1.6B: A groundbreaking text-to-speech model developed by two undergraduates with zero funding! This 1.6 billion parameter model generates remarkably realistic speech, including nonverbal cues like laughter and sneezes. This article guide
 3 Ways AI Can Make Mentorship More Meaningful Than EverMay 10, 2025 am 11:17 AM
3 Ways AI Can Make Mentorship More Meaningful Than EverMay 10, 2025 am 11:17 AMI wholeheartedly agree. My success is inextricably linked to the guidance of my mentors. Their insights, particularly regarding business management, formed the bedrock of my beliefs and practices. This experience underscores my commitment to mentor
 AI Unearths New Potential In The Mining IndustryMay 10, 2025 am 11:16 AM
AI Unearths New Potential In The Mining IndustryMay 10, 2025 am 11:16 AMAI Enhanced Mining Equipment The mining operation environment is harsh and dangerous. Artificial intelligence systems help improve overall efficiency and security by removing humans from the most dangerous environments and enhancing human capabilities. Artificial intelligence is increasingly used to power autonomous trucks, drills and loaders used in mining operations. These AI-powered vehicles can operate accurately in hazardous environments, thereby increasing safety and productivity. Some companies have developed autonomous mining vehicles for large-scale mining operations. Equipment operating in challenging environments requires ongoing maintenance. However, maintenance can keep critical devices offline and consume resources. More precise maintenance means increased uptime for expensive and necessary equipment and significant cost savings. AI-driven
 Why AI Agents Will Trigger The Biggest Workplace Revolution In 25 YearsMay 10, 2025 am 11:15 AM
Why AI Agents Will Trigger The Biggest Workplace Revolution In 25 YearsMay 10, 2025 am 11:15 AMMarc Benioff, Salesforce CEO, predicts a monumental workplace revolution driven by AI agents, a transformation already underway within Salesforce and its client base. He envisions a shift from traditional markets to a vastly larger market focused on
 AI HR Is Going To Rock Our Worlds As AI Adoption SoarsMay 10, 2025 am 11:14 AM
AI HR Is Going To Rock Our Worlds As AI Adoption SoarsMay 10, 2025 am 11:14 AMThe Rise of AI in HR: Navigating a Workforce with Robot Colleagues The integration of AI into human resources (HR) is no longer a futuristic concept; it's rapidly becoming the new reality. This shift impacts both HR professionals and employees, dem


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

SublimeText3 Linux new version
SublimeText3 Linux latest version

WebStorm Mac version
Useful JavaScript development tools






