How to use MTR to detect and repair database security vulnerabilities
Database security vulnerabilities are a serious challenge faced by many Internet applications and systems. Hackers and malicious attackers can exploit these vulnerabilities to obtain sensitive information, tamper with data, or cause the system to crash. In order to protect the security of the database, developers need to perform regular security testing and repairs on the database. In this article, we will introduce how to use MTR (MySQL Testing Toolset) to detect and repair database security vulnerabilities.
MTR is a testing tool set officially provided by MySQL, which can help developers conduct functional testing and performance testing of the database. At the same time, MTR also provides some tools and interfaces that can be used to detect security vulnerabilities in the database. Below we will introduce in detail how to use MTR to complete these tasks.
The first step is to install MTR. MTR is a directory in the MySQL source code. You can get the MTR by downloading the MySQL source code and compiling it. In the Ubuntu system, you can install MTR through the following command:
sudo apt-get install mysql-server mysql-source -y
After the installation is completed, you can find MTR in the mysql-test directory of the MySQL source code.
The second step is to write test cases. MTR uses a simple language called MTR script to describe the test cases that need to be executed. The following is an example MTR script:
--source include/have_innodb.inc create table test (id int primary key, name varchar(10)); insert into test values (1, 'Alice'); insert into test values (2, 'Bob'); select * from test;
This script creates a table named test, inserts two rows of data into it, and finally queries all the data in the table. You can write test cases according to your needs.
The third step is to run the MTR test. You can use the following command to run the MTR test:
./mtr test_script.mtr
where test_script.mtr is the file name of the MTR script you wrote. MTR will execute the test cases in the order described in the script and output the execution results to the terminal.
By running MTR tests, you can discover some potential security vulnerabilities in the database. For example, if your database does not have password authentication enabled, then anyone can connect directly to the database and perform operations. In the MTR test, you can use the following command to detect whether password authentication is enabled:
--source include/have_authentication.inc connect (con1, localhost, root, );
This command attempts to connect to the database. If the connection is successful, it means that password authentication is enabled; if the connection fails, it means that it is not. Enable password authentication.
The fourth step is to fix the security vulnerability. Once you discover a security vulnerability in your database, you need to take prompt steps to fix it. For example, if you find that password authentication is not enabled in the database, you need to modify the database configuration file and restart the database to enable password authentication to take effect.
Fixing security vulnerabilities is a complex process that requires developers to have extensive database experience and security awareness. Before fixing, you can use MTR testing to verify that the fix is effective.
In short, by using MTR to detect and repair database security vulnerabilities, potential security risks can be discovered and eliminated at the earliest stage, ensuring the security of the database. However, it should be noted that MTR is only one of the auxiliary tools, and developers also need to combine other tools and methods to implement comprehensive database security protection measures.
The above is the detailed content of How to use MTR to detect and repair database security vulnerabilities. For more information, please follow other related articles on the PHP Chinese website!
 修复:Windows 中的 Discord 游戏检测不工作问题Apr 13, 2023 pm 03:34 PM
修复:Windows 中的 Discord 游戏检测不工作问题Apr 13, 2023 pm 03:34 PMDiscord 是游戏玩家与其他用户交流时首选的最受欢迎的 VOIP 应用程序。它具有内置的游戏检测功能,允许用户将他/她正在玩的当前游戏的名称广播给其他人。但是,许多用户报告说 Discord 无法检测到他们正在玩的当前游戏。您是否正在为discord中的游戏检测功能停止工作而烦恼?那么你已经到达了正确的帖子。在这里,我们列出了一些故障排除策略,可以帮助您在 Windows PC 上解决此问题。修复 1 – 启用 Discord 游戏检测1. 单击任务栏上的Windows开始按钮。在 Wind
 如何在 Windows 11/10 上修复 FFMPEG.DLL Not Found 错误Apr 14, 2023 pm 07:10 PM
如何在 Windows 11/10 上修复 FFMPEG.DLL Not Found 错误Apr 14, 2023 pm 07:10 PM最近,Windows用户报告遇到ffmpeg.dll文件丢失或未找到错误。基本上,此错误可能会在应用程序安装时、系统启动时或访问某些网站时引发。当系统文件损坏时,可能会出现ffmpeg.dll错误,从而使系统目录无法发现DLL文件。此错误还与MicrosoftTeams、Skype、Discord、适用于Windows的WhatsApp、Deezer等应用程序相关联。向用户显示的错误消息是:程序无法启动,因为您的计算机缺少ffmpeg.dll。尝试重新安装程序以解决此问题。如果
 如何修复 Microsoft Office 365 卡在准备就绪上Apr 13, 2023 pm 06:28 PM
如何修复 Microsoft Office 365 卡在准备就绪上Apr 13, 2023 pm 06:28 PM许多用户在他们的 Windows PC 上安装Microsoft Office 365时报告了一个问题。问题是安装程序卡在“我们正在准备就绪” 消息上。看到此消息后,用户将无法再次安装 Office 365。当以前的 Office 365 文件未正确安装或损坏时,可能会发生这种情况。有时兼容性问题或安装过程中缺少某些权限可能会导致此错误。在 Office 365 安装过程中,您是否还停留在“准备就绪”错误?然后,继续阅读这篇文章。在这里,我们讨论了一些故障排除策略,可以帮助您解决计算机上的此错误
 修复:Windows 11 中的黑色桌面背景显示问题Apr 14, 2023 am 10:49 AM
修复:Windows 11 中的黑色桌面背景显示问题Apr 14, 2023 am 10:49 AMWindows 11 用户面临的问题之一是从 Windows 10 升级后随机显示黑色桌面背景。根据大多数用户的说法,他们在更改主题或使用新壁纸时在显示器上看到黑色壁纸. 还有一些人在尝试打开“开始”菜单时遇到了显示背景变黑的情况。Windows 11 上出现此问题的原因尚不清楚,但遇到此问题的其他用户已成功尝试了一些修复程序。在本文中,列出了一些可以帮助您在 Windows 11 PC 上解决此问题的解决方案。在继续尝试下面提到的修复之前,请执行系统重新启动并检查是否可以解决问题。修复 1 –
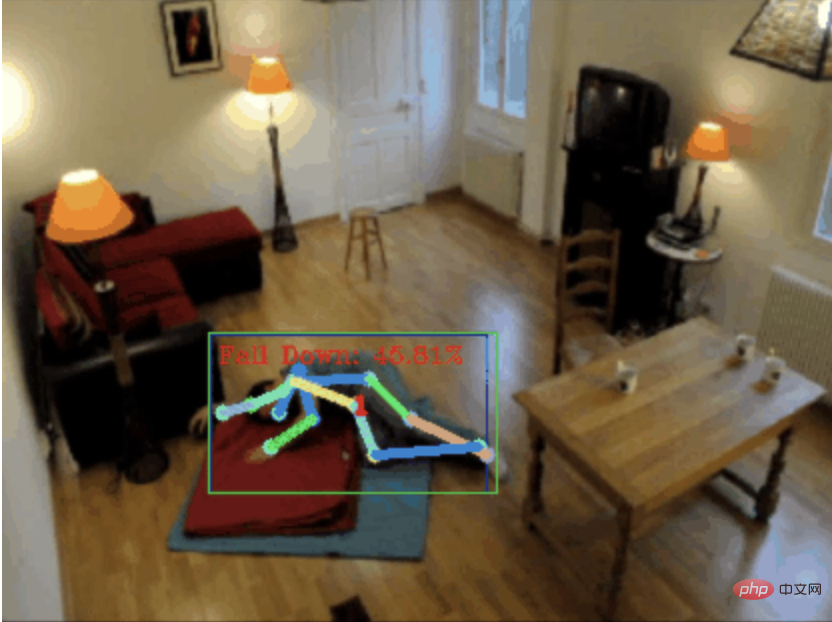 摔倒检测,基于骨骼点人体动作识别,部分代码用 Chatgpt 完成Apr 12, 2023 am 08:19 AM
摔倒检测,基于骨骼点人体动作识别,部分代码用 Chatgpt 完成Apr 12, 2023 am 08:19 AM哈喽,大家好。今天给大家分享一个摔倒检测项目,准确地说是基于骨骼点的人体动作识别。大概分为三个步骤识别人体识别人体骨骼点动作分类项目源码已经打包好了,获取方式见文末。0. chatgpt首先,我们需要获取监控的视频流。这段代码比较固定,我们可以直接让chatgpt完成chatgpt写的这段代码是没有问题的,可以直接使用。但后面涉及到业务型任务,比如:用mediapipe识别人体骨骼点,chatgpt给出的代码是不对的。我觉得chatgpt可以作为一个工具箱,能独立于业务逻辑,都可以试着交给c
 i7-7700无法升级至Windows 11的解决方案Dec 26, 2023 pm 06:52 PM
i7-7700无法升级至Windows 11的解决方案Dec 26, 2023 pm 06:52 PMi77700的性能运行win11完全足够,但是用户却发现自己的i77700不能升级win11,这主要是受到了微软硬性条件的限制,所以只要跳过该限制就能安装了。i77700不能升级win11:1、因为微软限制了cpu的版本。2、intel只有第八代及以上版本可以直升win11。3、而i77700作为7代,无法满足win11的升级需求。4、但是i77700在性能上是完全能流畅使用win11的。5、所以大家可以使用本站的win11直装系统。6、下载完成后,右键“装载”该文件。7、再双击运行其中的“一键
 Windows无法在本地计算机上启动音频服务:修复Apr 13, 2023 pm 07:34 PM
Windows无法在本地计算机上启动音频服务:修复Apr 13, 2023 pm 07:34 PM无法从PC中发出声音是您会遇到的烦人问题之一。用户报告在任务栏上的音量图标上看到一个红叉标记,并且显示一条错误消息,显示 Windows 无法启动本地计算机错误0x80070005上的 Windows 音频服务。访问被拒绝。此外,打开Windows音频服务也没有帮助用户解决此问题。那么,如何解决此错误?好吧,这正是我们将在本指南中向您展示的内容。为什么我得到Windows无法启动本地计算机上的Windows音频服务错误?下面是可能在本地计算机错误0x80070005上触发 Windows 音频服
 MIT最新力作:用GPT-3.5解决时间序列异常检测问题Jun 08, 2024 pm 06:09 PM
MIT最新力作:用GPT-3.5解决时间序列异常检测问题Jun 08, 2024 pm 06:09 PM今天给大家介绍一篇MIT上周发表的文章,使用GPT-3.5-turbo解决时间序列异常检测问题,初步验证了LLM在时间序列异常检测中的有效性。整个过程没有进行finetune,直接使用GPT-3.5-turbo进行异常检测,文中的核心是如何将时间序列转换成GPT-3.5-turbo可识别的输入,以及如何设计prompt或者pipeline让LLM解决异常检测任务。下面给大家详细介绍一下这篇工作。图片论文标题:Largelanguagemodelscanbezero-shotanomalydete


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

SAP NetWeaver Server Adapter for Eclipse
Integrate Eclipse with SAP NetWeaver application server.

SublimeText3 Linux new version
SublimeText3 Linux latest version

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Zend Studio 13.0.1
Powerful PHP integrated development environment

SublimeText3 Chinese version
Chinese version, very easy to use






