 Backend Development
Backend Development PHP Tutorial
PHP Tutorial Introduction to password blacklist filtering solution based on PHP bloom filter
Introduction to password blacklist filtering solution based on PHP bloom filterIntroduction to the password blacklist filtering solution based on PHP Bloom filter
In the field of network security, password blacklist filtering is a common security method used to prevent users from using weak passwords. These commonly used weak passwords are blacklisted and prohibited from use in the policy. Traditional blacklist filtering methods include using hash tables or databases to store blacklisted passwords and comparing them when users register or reset their passwords. However, this method will face performance bottlenecks in large-scale user scenarios.
In order to solve this problem, this article will introduce a password blacklist filtering solution based on PHP Bloom Filter. Bloom filter is an efficient data structure, a probabilistic data structure used to determine whether an element belongs to a set. Its main features are high query efficiency and low storage space usage.
In PHP, you can use the Bloom Filter extension library bloom_filter to implement password blacklist filtering based on Bloom filters. First, you need to use Composer to install the extension library. You can add the following dependencies in the composer.json file:
{
"require": {
"joshtronic/php-bloom-filter": "1.7.*"
}
} Then, run composer install to install it. After the installation is complete, introduce the relevant library files into the PHP code:
require_once 'vendor/autoload.php';
Next, create a blacklist filter instance and add commonly used weak passwords to the filter:
use JoshtronicBloomFilterBloomFilter;
$blacklist = [
'123456',
'password',
// 添加其他常用的弱密码
];
$filter = new BloomFilter(['hash_function' => 'sha256']);
foreach ($blacklist as $password) {
$filter->add(strtolower($password));
} Above In the code, the sha256 algorithm is used as the hash function, and the blacklist password is converted into lowercase letters and added to the filter.
Next, you can filter by checking whether the password entered by the user is in the filter:
$username = $_POST['username'];
$password = $_POST['password'];
if ($filter->has(strtolower($password))) {
echo '密码太弱,请重新输入!';
} else {
// 密码安全,继续其他操作
}In the above code, use the has method to check the password entered by the user exists in the filter. If it exists, the password is considered weak and the user needs to be prompted to re-enter it; if it does not exist, the password is considered safe and other operations can continue.
By using the password blacklist filtering solution based on PHP Bloom filter, the efficiency and performance of password blacklist filtering can be improved. Bloom filters have high query efficiency and low storage space usage, and are especially suitable in large-scale user scenarios. At the same time, the parameters of the Bloom filter can be adjusted according to actual needs to balance the misjudgment rate and storage space requirements.
In practical applications, blacklist passwords need to be updated regularly to deal with password leaks and new weak passwords. The latest blacklist password list can be obtained from a reliable source regularly and the bloom filter can be updated. In addition, other password policies can be combined, such as password length restrictions, special characters must be included, etc., to improve password security.
To sum up, the password blacklist filtering solution based on PHP Bloom filter is an efficient and excellent password security mechanism. By properly configuring Bloom filter parameters, you can achieve a lower false positive rate and lower storage space usage, improving website security and user experience.
The above is the detailed content of Introduction to password blacklist filtering solution based on PHP bloom filter. For more information, please follow other related articles on the PHP Chinese website!
 11 Best PHP URL Shortener Scripts (Free and Premium)Mar 03, 2025 am 10:49 AM
11 Best PHP URL Shortener Scripts (Free and Premium)Mar 03, 2025 am 10:49 AMLong URLs, often cluttered with keywords and tracking parameters, can deter visitors. A URL shortening script offers a solution, creating concise links ideal for social media and other platforms. These scripts are valuable for individual websites a
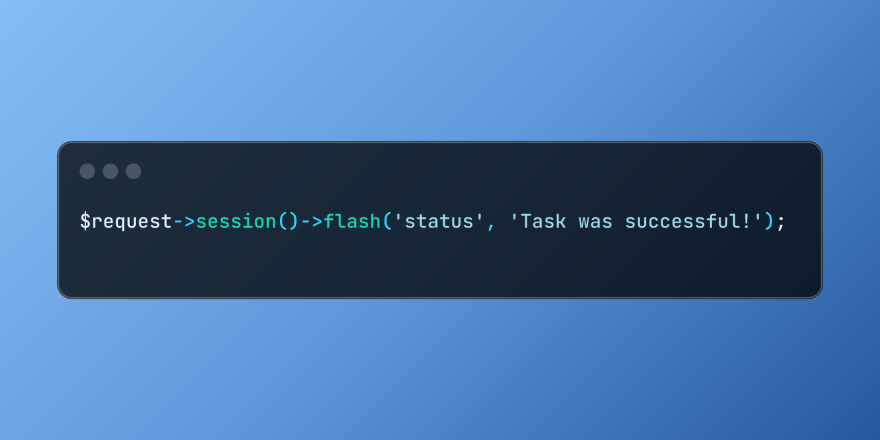 Working with Flash Session Data in LaravelMar 12, 2025 pm 05:08 PM
Working with Flash Session Data in LaravelMar 12, 2025 pm 05:08 PMLaravel simplifies handling temporary session data using its intuitive flash methods. This is perfect for displaying brief messages, alerts, or notifications within your application. Data persists only for the subsequent request by default: $request-
 Build a React App With a Laravel Back End: Part 2, ReactMar 04, 2025 am 09:33 AM
Build a React App With a Laravel Back End: Part 2, ReactMar 04, 2025 am 09:33 AMThis is the second and final part of the series on building a React application with a Laravel back-end. In the first part of the series, we created a RESTful API using Laravel for a basic product-listing application. In this tutorial, we will be dev
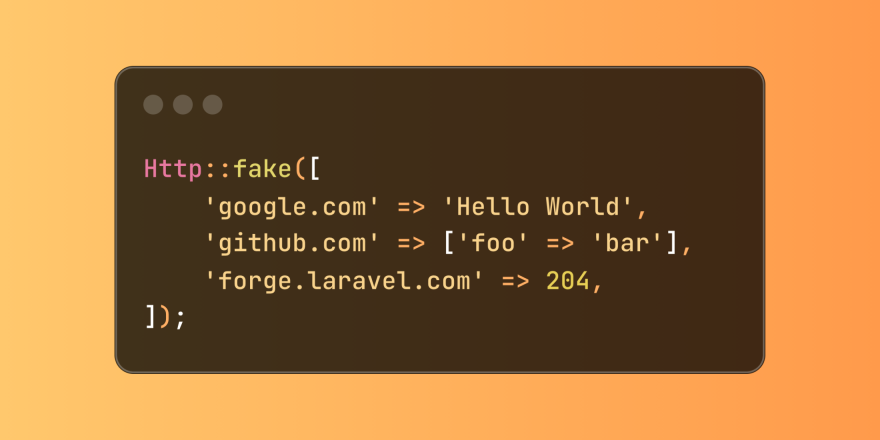 Simplified HTTP Response Mocking in Laravel TestsMar 12, 2025 pm 05:09 PM
Simplified HTTP Response Mocking in Laravel TestsMar 12, 2025 pm 05:09 PMLaravel provides concise HTTP response simulation syntax, simplifying HTTP interaction testing. This approach significantly reduces code redundancy while making your test simulation more intuitive. The basic implementation provides a variety of response type shortcuts: use Illuminate\Support\Facades\Http; Http::fake([ 'google.com' => 'Hello World', 'github.com' => ['foo' => 'bar'], 'forge.laravel.com' =>
 cURL in PHP: How to Use the PHP cURL Extension in REST APIsMar 14, 2025 am 11:42 AM
cURL in PHP: How to Use the PHP cURL Extension in REST APIsMar 14, 2025 am 11:42 AMThe PHP Client URL (cURL) extension is a powerful tool for developers, enabling seamless interaction with remote servers and REST APIs. By leveraging libcurl, a well-respected multi-protocol file transfer library, PHP cURL facilitates efficient execution of various network protocols, including HTTP, HTTPS, and FTP. This extension offers granular control over HTTP requests, supports multiple concurrent operations, and provides built-in security features.
 12 Best PHP Chat Scripts on CodeCanyonMar 13, 2025 pm 12:08 PM
12 Best PHP Chat Scripts on CodeCanyonMar 13, 2025 pm 12:08 PMDo you want to provide real-time, instant solutions to your customers' most pressing problems? Live chat lets you have real-time conversations with customers and resolve their problems instantly. It allows you to provide faster service to your custom
 Announcement of 2025 PHP Situation SurveyMar 03, 2025 pm 04:20 PM
Announcement of 2025 PHP Situation SurveyMar 03, 2025 pm 04:20 PMThe 2025 PHP Landscape Survey investigates current PHP development trends. It explores framework usage, deployment methods, and challenges, aiming to provide insights for developers and businesses. The survey anticipates growth in modern PHP versio
 Notifications in LaravelMar 04, 2025 am 09:22 AM
Notifications in LaravelMar 04, 2025 am 09:22 AMIn this article, we're going to explore the notification system in the Laravel web framework. The notification system in Laravel allows you to send notifications to users over different channels. Today, we'll discuss how you can send notifications ov


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

SAP NetWeaver Server Adapter for Eclipse
Integrate Eclipse with SAP NetWeaver application server.

EditPlus Chinese cracked version
Small size, syntax highlighting, does not support code prompt function

Dreamweaver Mac version
Visual web development tools

Notepad++7.3.1
Easy-to-use and free code editor

VSCode Windows 64-bit Download
A free and powerful IDE editor launched by Microsoft





