 Backend Development
Backend Development PHP Tutorial
PHP Tutorial Security Best Practices for PHP and Vue.js Development: Preventing Session Hijacking and Tampering
Security Best Practices for PHP and Vue.js Development: Preventing Session Hijacking and TamperingSecurity Best Practices for PHP and Vue.js Development: Preventing Session Hijacking and Tampering
With the development and use of web applications, network security issues have become increasingly important. Protecting user privacy and data security becomes the responsibility of every developer. In PHP and Vue.js development, ensuring session security is a critical task. This article describes some best practices for preventing session hijacking and tampering, and provides corresponding code examples.
- Use HTTPS protocol
Using HTTPS protocol can ensure the encryption and integrity of data transmission, thereby preventing session hijacking. In PHP, HTTPS can be enabled using the following code:
// 确保页面使用HTTPS
if ($_SERVER['HTTPS'] != 'on') {
$redirect_url = "https://" . $_SERVER['HTTP_HOST'] . $_SERVER['REQUEST_URI'];
header("Location: $redirect_url");
exit;
}- Generate a secure session ID
The session ID is an important token that identifies the user session, how to generate a secure The session ID is crucial. In PHP, you can use the following code to generate a secure session ID:
// 生成安全的会话ID session_start(); session_regenerate_id(true);
- Set the session expiration time
Setting the session expiration time can ensure the timeliness of the user session. Upon expiration, the user will need to log in again. In PHP, the session expiration time can be set using the following code:
// 设置会话过期时间为30分钟
session_start();
$expire_time = 30 * 60;
if (isset($_SESSION['last_activity']) && (time() - $_SESSION['last_activity'] > $expire_time)) {
session_unset();
session_destroy();
session_start();
}
$_SESSION['last_activity'] = time();- Using the HTTP Only flag and the Secure flag
Using the HTTP Only flag prevents client scripts from accessing the session cookie to prevent session hijacking. In PHP, the HTTP Only flag can be set using the following code:
// 设置会话cookie为HTTP Only session_start(); session_set_cookie_params(0, "/", "", true, true);
Using the Secure flag further prevents hijacking by ensuring that session cookies are only transmitted within secure HTTPS connections. In PHP, the Secure flag can be set using the following code:
// 设置会话cookie为Secure
session_start();
session_set_cookie_params(0, "/", "", true, true);
ini_set('session.cookie_secure', 1);- Use CSRF token
Using CSRF (Cross-Site Request Forgery) token can prevent malicious attacks The attacker uses the session to tamper with user data. In Vue.js, the following code can be used to generate and verify CSRF tokens:
// 生成CSRF令牌
function generateCSRFToken() {
let token = Math.random()
.toString(36)
.slice(2);
localStorage.setItem('csrf_token', token);
}
// 验证CSRF令牌
function validateCSRFToken() {
let storedToken = localStorage.getItem('csrf_token');
let receivedToken = document.querySelector('meta[name="csrf-token"]').content;
if (storedToken !== receivedToken) {
// CSRF令牌验证失败,处理错误
}
}The above are some best practices in PHP and Vue.js development to prevent session hijacking and tampering. By using HTTPS, generating secure session IDs, setting session expiration time, using HTTP Only flags and Secure flags, and using CSRF tokens, we can effectively protect the security and integrity of user sessions. Remember, cybersecurity is an ever-evolving field, and we should always pay attention and take appropriate measures to protect the security of our users and data.
The above is the detailed content of Security Best Practices for PHP and Vue.js Development: Preventing Session Hijacking and Tampering. For more information, please follow other related articles on the PHP Chinese website!
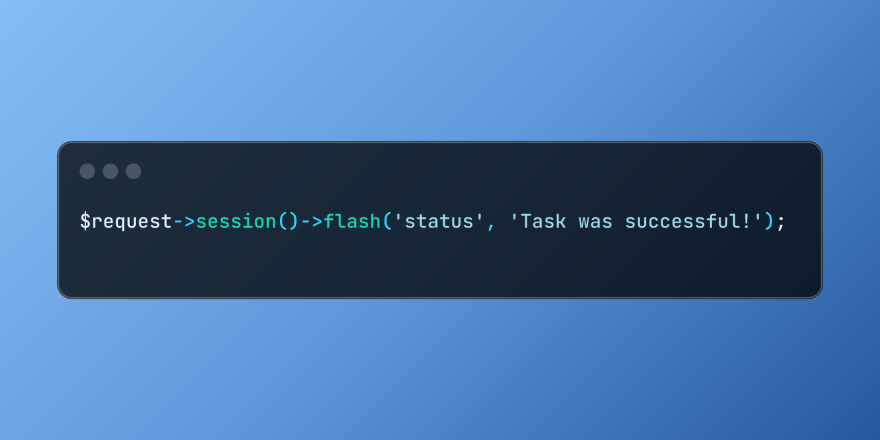 Working with Flash Session Data in LaravelMar 12, 2025 pm 05:08 PM
Working with Flash Session Data in LaravelMar 12, 2025 pm 05:08 PMLaravel simplifies handling temporary session data using its intuitive flash methods. This is perfect for displaying brief messages, alerts, or notifications within your application. Data persists only for the subsequent request by default: $request-
 Build a React App With a Laravel Back End: Part 2, ReactMar 04, 2025 am 09:33 AM
Build a React App With a Laravel Back End: Part 2, ReactMar 04, 2025 am 09:33 AMThis is the second and final part of the series on building a React application with a Laravel back-end. In the first part of the series, we created a RESTful API using Laravel for a basic product-listing application. In this tutorial, we will be dev
 cURL in PHP: How to Use the PHP cURL Extension in REST APIsMar 14, 2025 am 11:42 AM
cURL in PHP: How to Use the PHP cURL Extension in REST APIsMar 14, 2025 am 11:42 AMThe PHP Client URL (cURL) extension is a powerful tool for developers, enabling seamless interaction with remote servers and REST APIs. By leveraging libcurl, a well-respected multi-protocol file transfer library, PHP cURL facilitates efficient execution of various network protocols, including HTTP, HTTPS, and FTP. This extension offers granular control over HTTP requests, supports multiple concurrent operations, and provides built-in security features.
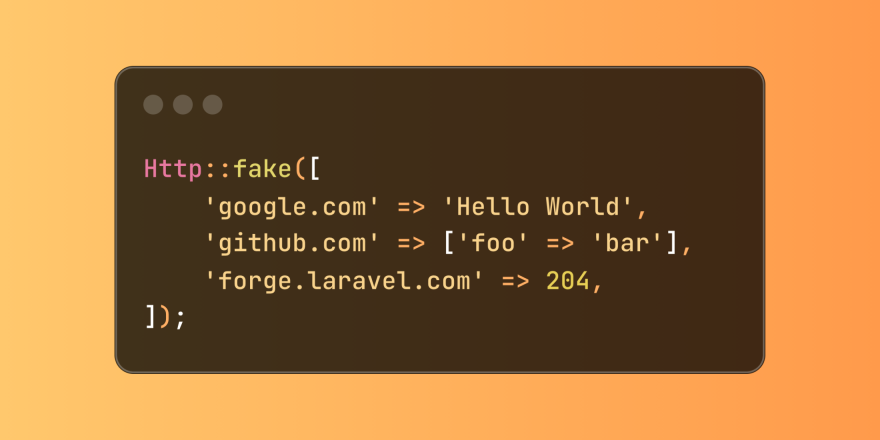 Simplified HTTP Response Mocking in Laravel TestsMar 12, 2025 pm 05:09 PM
Simplified HTTP Response Mocking in Laravel TestsMar 12, 2025 pm 05:09 PMLaravel provides concise HTTP response simulation syntax, simplifying HTTP interaction testing. This approach significantly reduces code redundancy while making your test simulation more intuitive. The basic implementation provides a variety of response type shortcuts: use Illuminate\Support\Facades\Http; Http::fake([ 'google.com' => 'Hello World', 'github.com' => ['foo' => 'bar'], 'forge.laravel.com' =>
 12 Best PHP Chat Scripts on CodeCanyonMar 13, 2025 pm 12:08 PM
12 Best PHP Chat Scripts on CodeCanyonMar 13, 2025 pm 12:08 PMDo you want to provide real-time, instant solutions to your customers' most pressing problems? Live chat lets you have real-time conversations with customers and resolve their problems instantly. It allows you to provide faster service to your custom
 Notifications in LaravelMar 04, 2025 am 09:22 AM
Notifications in LaravelMar 04, 2025 am 09:22 AMIn this article, we're going to explore the notification system in the Laravel web framework. The notification system in Laravel allows you to send notifications to users over different channels. Today, we'll discuss how you can send notifications ov
 Explain the concept of late static binding in PHP.Mar 21, 2025 pm 01:33 PM
Explain the concept of late static binding in PHP.Mar 21, 2025 pm 01:33 PMArticle discusses late static binding (LSB) in PHP, introduced in PHP 5.3, allowing runtime resolution of static method calls for more flexible inheritance.Main issue: LSB vs. traditional polymorphism; LSB's practical applications and potential perfo
 PHP Logging: Best Practices for PHP Log AnalysisMar 10, 2025 pm 02:32 PM
PHP Logging: Best Practices for PHP Log AnalysisMar 10, 2025 pm 02:32 PMPHP logging is essential for monitoring and debugging web applications, as well as capturing critical events, errors, and runtime behavior. It provides valuable insights into system performance, helps identify issues, and supports faster troubleshoot


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Atom editor mac version download
The most popular open source editor

Dreamweaver CS6
Visual web development tools

Safe Exam Browser
Safe Exam Browser is a secure browser environment for taking online exams securely. This software turns any computer into a secure workstation. It controls access to any utility and prevents students from using unauthorized resources.

MantisBT
Mantis is an easy-to-deploy web-based defect tracking tool designed to aid in product defect tracking. It requires PHP, MySQL and a web server. Check out our demo and hosting services.

Zend Studio 13.0.1
Powerful PHP integrated development environment





