With the rapid development of Internet technology, PHP, as a scripting language widely used in website development, plays a vital role in the development of various Web applications. However, due to the flexibility and openness of PHP, the security of user input has become an aspect that cannot be ignored in PHP development. This article will explore how to deal with user input security issues in PHP development.
- Verify user input
Secure PHP development requires first verifying the data entered by the user. User input can include form submissions, URL parameters, cookie values, etc. By using PHP's built-in functions (such as filter_var) or regular expressions, we can validate user input and filter illegal data. For example, you can use the filter_var function to validate an email address to ensure it conforms to the expected format. In addition, type verification can be performed on data such as numbers and dates entered by users to ensure that they meet the requirements. - Preventing SQL Injection
SQL injection is a common attack method that uses malicious code in user input to execute illegal SQL statements. To prevent SQL injection, SQL statements should be constructed using parameterized queries or prepared statements. Parameterized queries can separate user-entered variables from SQL query statements, thereby avoiding the need to splice user input directly into SQL statements. Prepared statements filter and escape user input before executing SQL statements by pre-binding parameters. These methods can effectively prevent SQL injection attacks. - Prevention of Cross-site Scripting Attacks (XSS)
Cross-site scripting attacks refer to attackers inserting malicious scripts into websites to obtain users' sensitive information or perform illegal operations. In order to prevent XSS attacks, PHP developers can use the htmlspecialchars function to escape user-entered data. This converts special characters into HTML entities, ensuring that the data is not parsed as script when displayed on the page. - Avoid file upload vulnerabilities
The file upload function is common on many websites, but improper handling of files uploaded by users may cause security vulnerabilities. To avoid file upload vulnerabilities, strict checksum restrictions should be applied to uploaded files. For example, you can check the file type, size, file name, etc. to ensure that only safe and trustworthy files are allowed to be uploaded. In addition, uploaded files can be saved in a specified directory and given appropriate permission settings to prevent the execution of malicious files. - Use session management safely
In PHP, session management is a common user authentication and state maintenance mechanism. In order to ensure the security of the session, you need to pay attention to the following aspects. First, random, complex session IDs should be used to prevent session hijacking attacks. Secondly, you can set the expiration time of the session and destroy the session information in time when the user is inactive for a long time or logs out. In addition, the transmission of session data can be encrypted by using the HTTPS protocol to ensure data confidentiality.
To sum up, the issue of user input security in PHP development is an aspect that needs attention. Through reasonable verification, filtering and processing of user input, various security attacks can be effectively prevented. In addition to the key points mentioned above, you can also use secure coding practices, key management, logging and other security measures to enhance the security of your application. Understanding and practicing these security principles will help PHP developers build more reliable and secure web applications.
The above is the detailed content of How to deal with user input security issues in PHP development. For more information, please follow other related articles on the PHP Chinese website!
 11 Best PHP URL Shortener Scripts (Free and Premium)Mar 03, 2025 am 10:49 AM
11 Best PHP URL Shortener Scripts (Free and Premium)Mar 03, 2025 am 10:49 AMLong URLs, often cluttered with keywords and tracking parameters, can deter visitors. A URL shortening script offers a solution, creating concise links ideal for social media and other platforms. These scripts are valuable for individual websites a
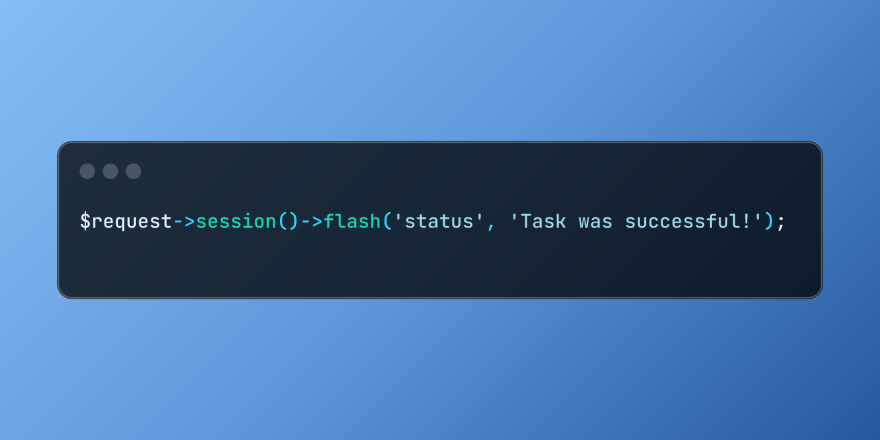 Working with Flash Session Data in LaravelMar 12, 2025 pm 05:08 PM
Working with Flash Session Data in LaravelMar 12, 2025 pm 05:08 PMLaravel simplifies handling temporary session data using its intuitive flash methods. This is perfect for displaying brief messages, alerts, or notifications within your application. Data persists only for the subsequent request by default: $request-
 Build a React App With a Laravel Back End: Part 2, ReactMar 04, 2025 am 09:33 AM
Build a React App With a Laravel Back End: Part 2, ReactMar 04, 2025 am 09:33 AMThis is the second and final part of the series on building a React application with a Laravel back-end. In the first part of the series, we created a RESTful API using Laravel for a basic product-listing application. In this tutorial, we will be dev
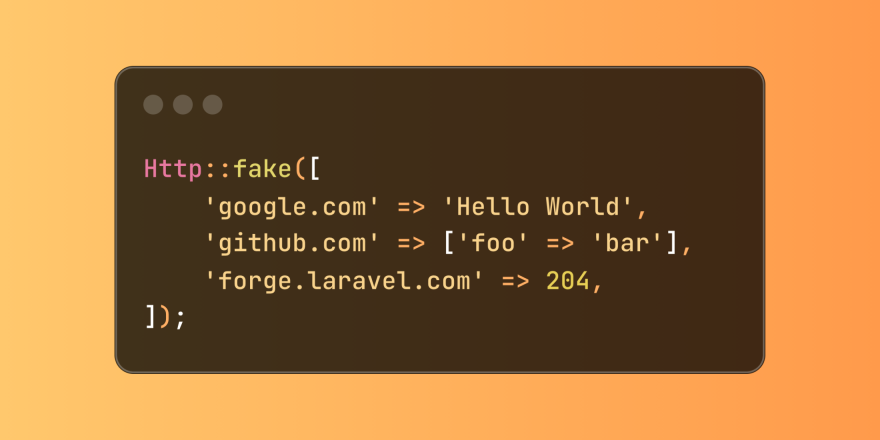 Simplified HTTP Response Mocking in Laravel TestsMar 12, 2025 pm 05:09 PM
Simplified HTTP Response Mocking in Laravel TestsMar 12, 2025 pm 05:09 PMLaravel provides concise HTTP response simulation syntax, simplifying HTTP interaction testing. This approach significantly reduces code redundancy while making your test simulation more intuitive. The basic implementation provides a variety of response type shortcuts: use Illuminate\Support\Facades\Http; Http::fake([ 'google.com' => 'Hello World', 'github.com' => ['foo' => 'bar'], 'forge.laravel.com' =>
 cURL in PHP: How to Use the PHP cURL Extension in REST APIsMar 14, 2025 am 11:42 AM
cURL in PHP: How to Use the PHP cURL Extension in REST APIsMar 14, 2025 am 11:42 AMThe PHP Client URL (cURL) extension is a powerful tool for developers, enabling seamless interaction with remote servers and REST APIs. By leveraging libcurl, a well-respected multi-protocol file transfer library, PHP cURL facilitates efficient execution of various network protocols, including HTTP, HTTPS, and FTP. This extension offers granular control over HTTP requests, supports multiple concurrent operations, and provides built-in security features.
 12 Best PHP Chat Scripts on CodeCanyonMar 13, 2025 pm 12:08 PM
12 Best PHP Chat Scripts on CodeCanyonMar 13, 2025 pm 12:08 PMDo you want to provide real-time, instant solutions to your customers' most pressing problems? Live chat lets you have real-time conversations with customers and resolve their problems instantly. It allows you to provide faster service to your custom
 Announcement of 2025 PHP Situation SurveyMar 03, 2025 pm 04:20 PM
Announcement of 2025 PHP Situation SurveyMar 03, 2025 pm 04:20 PMThe 2025 PHP Landscape Survey investigates current PHP development trends. It explores framework usage, deployment methods, and challenges, aiming to provide insights for developers and businesses. The survey anticipates growth in modern PHP versio
 Notifications in LaravelMar 04, 2025 am 09:22 AM
Notifications in LaravelMar 04, 2025 am 09:22 AMIn this article, we're going to explore the notification system in the Laravel web framework. The notification system in Laravel allows you to send notifications to users over different channels. Today, we'll discuss how you can send notifications ov


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Safe Exam Browser
Safe Exam Browser is a secure browser environment for taking online exams securely. This software turns any computer into a secure workstation. It controls access to any utility and prevents students from using unauthorized resources.

SublimeText3 Linux new version
SublimeText3 Linux latest version

SublimeText3 Chinese version
Chinese version, very easy to use

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Mac version
God-level code editing software (SublimeText3)






