With the development of technology, voice verification code has become one of the important ways to verify user identity. Compared with traditional SMS verification codes, voice verification codes are more secure and convenient, so they have received more and more attention. This article will introduce how to use PHP to implement voice verification codes to better protect the security of user accounts.
1. The principle of voice verification code
The principle of voice verification code is actually very simple. That is, when the user needs to verify their identity, the server will automatically make a call to the user's mobile phone and play a paragraph. Voice content containing verification code. Users only need to listen to the voice content and enter the correct verification code to complete identity verification.
2. Steps to implement voice verification code in PHP
1. Prepare the environment
First, we need to prepare the PHP environment and some necessary libraries and plug-ins. The specific libraries and plug-ins that need to be downloaded are as follows:
• PEAR Net_Socket library
• PEAR Net_URL2 library
• PEAR HTTP_Request2 library
• PEAR Net_RouterOS library
• libcurl plug-in
These libraries and plug-ins can be downloaded through the PHP official website. After the download is completed, they need to be configured and installed. After installing all libraries and plug-ins, you can start writing PHP programs.
2. Write a PHP program
Next we will write a simple PHP program to implement the voice verification code. First, we need to define a verification code function. The code is as follows:
function generate_code() {
return rand(1000,9999);
}
In this function, we use the rand function to generate a A 4-digit random number as the content of the verification code.
The next step is to implement the function of making calls. We can use Twilio, an API platform, which provides a global voice verification code service. Twilio's API is very simple and easy to use. We only need to introduce the API library into the code and then pass the parameters as required by the official documentation. The code is as follows:
require_once "Twilio/autoload.php";
use TwilioRestClient;
$twilio_sid = 'your_account_SID';
$twilio_token = 'your_auth_token';
$twilio_number = 'your_twilio_number';
$client = new Client($twilio_sid,$twilio_token);
$call = $client->account->calls->create(
$user_number,
$twilio_number,
array(
'url' => 'http://your_server_url/twilio_voice_message.php?code='.urlencode($code)
));
In the above code, we used Twilio's PHP library and passed in the account SID, authorization token, and Twilio number. In addition, we called the account->calls->create method of the Client object to make the call and pass in the necessary parameters.
Note: The user number needs to be a number in E.164 format, and format conversion needs to be performed before passing parameters, for example, convert 8613801234567 to 13801234567.
In the complete program, we also need to write a PHP script to implement the voice verification code reading function and return it to the Twilio server. This script needs to be accessed via a specified URL link through Twilio's API. The specific code is as follows:
header("content-type: text/xml");
$code = $_REQUEST['code'];
? >
<Say voice="alice">你的验证码是<?php echo $code; ?> </Say>
In the above code, we use the Voice API provided by Twilio to play the voice content of the verification code. The implementation of this API is very simple. You only need to use the
3. Implementing the security of voice verification codes
Although voice verification codes are more secure than SMS verification codes, there is still a risk of being attacked. Therefore, when using voice verification codes, we need to pay attention to the following points to ensure security:
1. Use random numbers
In order to avoid attackers guessing the content of the verification code, we need to use Random number to generate verification code. An attacker can try to crack the verification code through brute force or other methods. If we use a simple combination of numbers or letters to generate the verification code, it will provide an opportunity for the attacker to exploit.
2. Limit the validity period of the verification code
Since the validity period of the verification code is very limited, the attacker must crack the verification code within the specified time, otherwise he will lose the opportunity to attack. Therefore, we can limit the validity period of the verification code when sending it, for example, the verification must be completed within 5 minutes, otherwise it will automatically expire.
3. Bind to the user
In order to prevent attackers from impersonating users to attack, we can bind the verification code to the user. The specific method is that when sending a voice verification code to the user, the server needs to record the user's IP address, device information and other data at the same time, so that it can be checked when the user completes the verification.
Summary:
This article mainly introduces how to use PHP to implement voice verification codes and use Twilio's API platform to make calls and play voice content. Compared with traditional SMS verification codes, voice verification codes are more secure and convenient. Of course, when using voice verification codes, you need to pay attention to details such as the validity period of the verification code and the use of random numbers to improve the security of the user account.
The above is the detailed content of How to implement voice verification code using PHP. For more information, please follow other related articles on the PHP Chinese website!
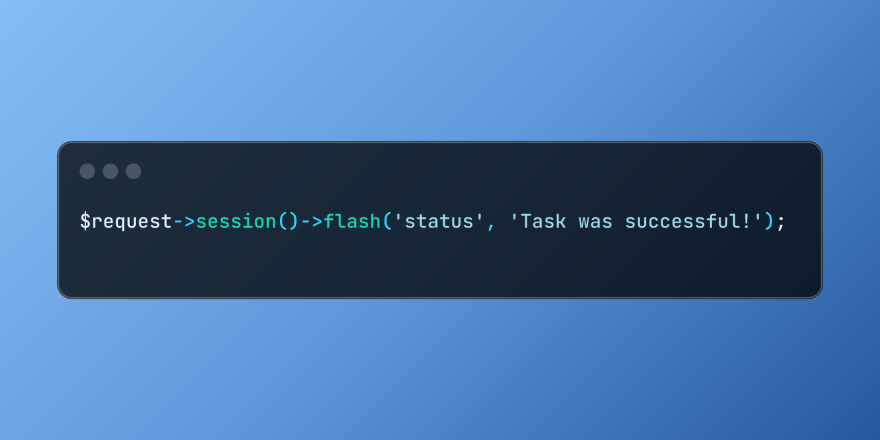 Working with Flash Session Data in LaravelMar 12, 2025 pm 05:08 PM
Working with Flash Session Data in LaravelMar 12, 2025 pm 05:08 PMLaravel simplifies handling temporary session data using its intuitive flash methods. This is perfect for displaying brief messages, alerts, or notifications within your application. Data persists only for the subsequent request by default: $request-
 cURL in PHP: How to Use the PHP cURL Extension in REST APIsMar 14, 2025 am 11:42 AM
cURL in PHP: How to Use the PHP cURL Extension in REST APIsMar 14, 2025 am 11:42 AMThe PHP Client URL (cURL) extension is a powerful tool for developers, enabling seamless interaction with remote servers and REST APIs. By leveraging libcurl, a well-respected multi-protocol file transfer library, PHP cURL facilitates efficient execution of various network protocols, including HTTP, HTTPS, and FTP. This extension offers granular control over HTTP requests, supports multiple concurrent operations, and provides built-in security features.
 Build a React App With a Laravel Back End: Part 2, ReactMar 04, 2025 am 09:33 AM
Build a React App With a Laravel Back End: Part 2, ReactMar 04, 2025 am 09:33 AMThis is the second and final part of the series on building a React application with a Laravel back-end. In the first part of the series, we created a RESTful API using Laravel for a basic product-listing application. In this tutorial, we will be dev
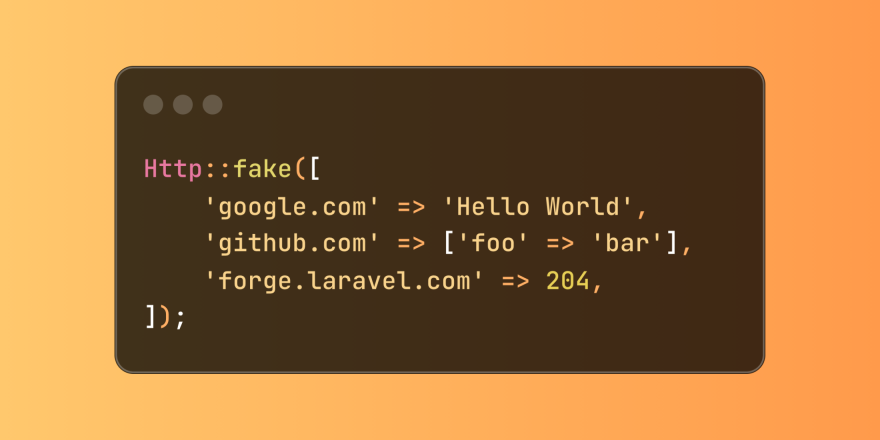 Simplified HTTP Response Mocking in Laravel TestsMar 12, 2025 pm 05:09 PM
Simplified HTTP Response Mocking in Laravel TestsMar 12, 2025 pm 05:09 PMLaravel provides concise HTTP response simulation syntax, simplifying HTTP interaction testing. This approach significantly reduces code redundancy while making your test simulation more intuitive. The basic implementation provides a variety of response type shortcuts: use Illuminate\Support\Facades\Http; Http::fake([ 'google.com' => 'Hello World', 'github.com' => ['foo' => 'bar'], 'forge.laravel.com' =>
 12 Best PHP Chat Scripts on CodeCanyonMar 13, 2025 pm 12:08 PM
12 Best PHP Chat Scripts on CodeCanyonMar 13, 2025 pm 12:08 PMDo you want to provide real-time, instant solutions to your customers' most pressing problems? Live chat lets you have real-time conversations with customers and resolve their problems instantly. It allows you to provide faster service to your custom
 Notifications in LaravelMar 04, 2025 am 09:22 AM
Notifications in LaravelMar 04, 2025 am 09:22 AMIn this article, we're going to explore the notification system in the Laravel web framework. The notification system in Laravel allows you to send notifications to users over different channels. Today, we'll discuss how you can send notifications ov
 Explain the concept of late static binding in PHP.Mar 21, 2025 pm 01:33 PM
Explain the concept of late static binding in PHP.Mar 21, 2025 pm 01:33 PMArticle discusses late static binding (LSB) in PHP, introduced in PHP 5.3, allowing runtime resolution of static method calls for more flexible inheritance.Main issue: LSB vs. traditional polymorphism; LSB's practical applications and potential perfo
 PHP Logging: Best Practices for PHP Log AnalysisMar 10, 2025 pm 02:32 PM
PHP Logging: Best Practices for PHP Log AnalysisMar 10, 2025 pm 02:32 PMPHP logging is essential for monitoring and debugging web applications, as well as capturing critical events, errors, and runtime behavior. It provides valuable insights into system performance, helps identify issues, and supports faster troubleshoot


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

SublimeText3 English version
Recommended: Win version, supports code prompts!

Safe Exam Browser
Safe Exam Browser is a secure browser environment for taking online exams securely. This software turns any computer into a secure workstation. It controls access to any utility and prevents students from using unauthorized resources.

Zend Studio 13.0.1
Powerful PHP integrated development environment

DVWA
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is very vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, to help web developers better understand the process of securing web applications, and to help teachers/students teach/learn in a classroom environment Web application security. The goal of DVWA is to practice some of the most common web vulnerabilities through a simple and straightforward interface, with varying degrees of difficulty. Please note that this software

mPDF
mPDF is a PHP library that can generate PDF files from UTF-8 encoded HTML. The original author, Ian Back, wrote mPDF to output PDF files "on the fly" from his website and handle different languages. It is slower than original scripts like HTML2FPDF and produces larger files when using Unicode fonts, but supports CSS styles etc. and has a lot of enhancements. Supports almost all languages, including RTL (Arabic and Hebrew) and CJK (Chinese, Japanese and Korean). Supports nested block-level elements (such as P, DIV),






