 Java
Java javaTutorial
javaTutorial How to use Spring Boot to implement security authentication and authorization management
How to use Spring Boot to implement security authentication and authorization managementWith the development of the Internet, the security of applications has become very important, and every programmer needs to pay attention to security issues. Since the Spring framework is widely used in large-scale enterprise-level applications, Spring Boot is a very popular choice to develop web applications. In this article, we will learn how to use Spring Boot to implement security authentication and authorization management.
1. Authentication and Authorization
Before we start discussing Spring Boot’s implementation of security authentication and authorization, we need to understand what authentication and authorization are.
Authentication is to confirm whether the identity of an entity is legal. In web applications, it is usually to confirm whether the user is a legitimate user.
Authorization is to grant specific operation permissions to an entity after confirming that it is legal. In web applications, it is common to confirm that the user has appropriate access rights to the requested resource.
2. Spring Boot Security Framework
Spring Boot provides a security framework that can easily implement security authentication and authorization management for web applications. Spring Security is part of the Spring Boot security framework. It provides a configurable framework to ensure applications can run securely.
Spring Security provides the following functions:
1. Security authentication and authorization
2. HTTPS support
3. Session management
4. Cross-domain request support
5. Method-level authorization
6. LDAP support
7. OpenID support
8. OAuth 2.0 support
3. Spring Boot security configuration
Before starting to use Spring Boot to implement security authentication and authorization, we need to understand the security configuration of Spring Boot.
Spring Boot uses Java configuration and annotations to configure security. Security configuration is defined in a class that is annotated with @EnableWebSecurity to enable Security, and then defines a class that inherits from WebSecurityConfigurerAdapter to configure Security.
The following is an example of a basic Spring Boot security configuration:
@Configuration
@EnableWebSecurity
public class SecurityConfig extends WebSecurityConfigurerAdapter {
@Override
protected void configure(HttpSecurity http) throws Exception {
http
.authorizeRequests()
.antMatchers("/admin/**").hasRole("ADMIN")
.antMatchers("/user/**").hasAnyRole("ADMIN", "USER")
.anyRequest().authenticated()
.and()
.formLogin()
.loginPage("/login")
.permitAll()
.and()
.logout()
.permitAll();
}
@Autowired
public void configureGlobal(AuthenticationManagerBuilder auth) throws Exception {
auth
.inMemoryAuthentication()
.withUser("admin").password("admin").roles("ADMIN")
.and()
.withUser("user").password("user").roles("USER");
}
}In the above configuration, we enable Security using the @EnableWebSecurity annotation, and then define a class that inherits from WebSecurityConfigurerAdapter.
Theconfigure() method will be called when the application starts to set the rules for HTTP request security. In this example, we define three rules:
1. Any URL starting with /admin/ is only allowed to be accessed by users with the role of ADMIN.
2. Any URL starting with /user/ allows users with roles of ADMIN or USER to access.
3. All other requests require authentication.
The formLogin() method defines the location of the login form and allows all users to access it.
The logout() method sets the logout function and allows access to all users.
The configureGlobal() method configures an in-memory authentication scheme, including username and password and assigned roles.
This is just a simple example, more complex security configurations can be set up using various Spring Security options.
4. Authentication provider
In the above configuration example, we used an in-memory authentication scheme. However, in reality we usually use a database to store user information. Spring Security provides us with authentication providers to handle authentication.
In Spring Security, an authentication provider is an interface that needs to implement the authenticate() method to perform authentication. Authentication providers can be in-memory, relational database or LDAP based etc.
The following is an example of a database-based authentication provider:
@Service
public class UserDetailsServiceImp implements UserDetailsService {
@Autowired
private UserRepository userRepository;
@Override
public UserDetails loadUserByUsername(String username) throws UsernameNotFoundException {
User user = userRepository.findByName(username);
if (user == null) {
throw new UsernameNotFoundException("User not found");
}
return new org.springframework.security.core.userdetails.User(user.getName(), user.getPassword(),
AuthorityUtils.createAuthorityList(user.getAuthorities()));
}
}In the above code, we define a UserDetailsServiceImp class, which implements the UserDetailsService interface. The loadUserByUsername() method loads user information from the database and returns Spring Security's UserDetails object, which contains username, password, and authorization.
5. Authorization Management
In Spring Boot, we can use Spring Security for role-based authorization management. Spring Security provides two methods for authorization management: declarative and programmatic.
1. Declarative
In declarative authorization, we can use the @PreAuthorize and @PostAuthorize annotations to set access control rules. @PreAuthorize is used to specify the conditions that need to be met before accessing the method, while @PostAuthorize is used to specify the conditions that should be met before returning.
The following is an example of declarative-based authorization management:
@Service
public class ProductService {
@PreAuthorize("hasRole('ROLE_ADMIN')")
public void addProduct() {
// add product
}
@PreAuthorize("hasRole('ROLE_USER')")
@PostAuthorize("returnObject.owner == authentication.name")
public Product findProductByName(String name) {
// find product by name
}
}In the above code, we added @PreAuthorize annotations to the addProduct() and findProductByName() methods to set access control rules .
In the addProduct() method, we restrict users with the role ROLE_ADMIN to access this method.
In the findProductByName() method, we restrict users with the role ROLE_USER to access the method, and set another access control rule using the @PostAuthorize annotation to ensure that only all users owned by the returned product The product will be returned only when the user is the same as the authenticated user.
2. Programmatic
In programmatic authorization, we can use the Spring Security API to set access control rules.
The following is an example of programmatic authorization management:
@Configuration
@EnableWebSecurity
public class SecurityConfig extends WebSecurityConfigurerAdapter {
@Autowired
private UserService userService;
@Override
protected void configure(HttpSecurity http) throws Exception {
http
.authorizeRequests()
.antMatchers("/admin/**").hasRole("ADMIN")
.antMatchers("/user/**").hasAnyRole("ADMIN", "USER")
.anyRequest().authenticated()
.and()
.formLogin()
.loginPage("/login")
.permitAll()
.and()
.logout()
.permitAll()
.and()
.csrf().disable()
.exceptionHandling().accessDeniedHandler(accessDeniedHandler());
}
@Override
protected void configure(AuthenticationManagerBuilder auth) throws Exception {
auth.userDetailsService(userService).passwordEncoder(passwordEncoder());
}
@Bean
public AccessDeniedHandler accessDeniedHandler(){
return new CustomAccessDeniedHandler();
}
@Bean
public PasswordEncoder passwordEncoder() {
return new BCryptPasswordEncoder();
}
}在上面的代码中,我们定义了一个UserService类来处理用户信息,并在configure()方法中使用了accessDeniedHandler()方法来定制访问被拒绝时的错误信息。
我们还实现了一个CustomAccessDeniedHandler类来自定义访问被拒绝时的响应。
最后,我们使用了PasswordEncoder来编码密码。
六、结论
在本文中,我们了解了如何使用Spring Boot实现安全认证和授权管理。我们已经讨论了Spring Boot安全框架、安全配置、身份验证提供器和授权管理等关键概念。我们还讨论了如何使用声明式和编程式授权管理。通过使用Spring Boot的安全框架,我们可以轻松地为Web应用程序提供安全性,并确保应用程序可以安全地运行。
The above is the detailed content of How to use Spring Boot to implement security authentication and authorization management. For more information, please follow other related articles on the PHP Chinese website!
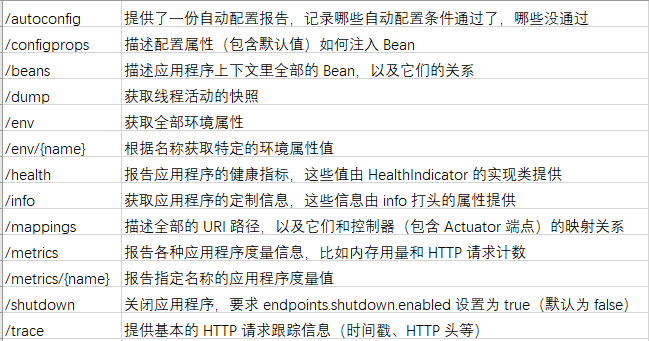 Spring Boot Actuator从未授权访问到getshell的示例分析May 23, 2023 am 08:56 AM
Spring Boot Actuator从未授权访问到getshell的示例分析May 23, 2023 am 08:56 AM前言部门大佬在某src上挖到了这个漏洞,是一个比较老的洞了,我觉得有点意思,就动手在本地搭了个环境测试一下。Actuator是springboot提供的用来对应用系统进行自省和监控的功能模块,借助于Actuator开发者可以很方便地对应用系统某些监控指标进行查看、统计等。在Actuator启用的情况下,如果没有做好相关权限控制,非法用户可通过访问默认的执行器端点(endpoints)来获取应用系统中的监控信息,从而导致信息泄露甚至服务器被接管的事件发生。如上所示,actuator是springb
 如何利用Spring Boot构建区块链应用和智能合约Jun 22, 2023 am 09:33 AM
如何利用Spring Boot构建区块链应用和智能合约Jun 22, 2023 am 09:33 AM随着比特币等数字货币的兴起,区块链技术也逐渐成为热门话题。而智能合约,则可视为区块链技术的重要组成部分。SpringBoot作为一种流行的Java后端开发框架,也能够用来构建区块链应用和智能合约。本文将介绍如何利用SpringBoot搭建基于区块链技术的应用和智能合约。一、SpringBoot与区块链首先,我们需要了解一些与区块链相关的基本概念。区块链
 使用Spring Boot和Apache ServiceMix构建ESB系统Jun 22, 2023 pm 12:30 PM
使用Spring Boot和Apache ServiceMix构建ESB系统Jun 22, 2023 pm 12:30 PM随着现代企业越来越依赖于各种不同的应用程序和系统,企业集成变得愈发重要。企业服务总线(ESB)就是一种集成架构模式,通过将不同系统和应用程序连接在一起,提供通用的数据交换和消息路由服务,从而实现企业级应用程序集成。使用SpringBoot和ApacheServiceMix,我们可以轻松构建一个ESB系统,这篇文章将介绍如何实现。SpringBoot和A
 基于Spring Boot的分布式数据缓存和存储系统Jun 22, 2023 am 09:48 AM
基于Spring Boot的分布式数据缓存和存储系统Jun 22, 2023 am 09:48 AM随着互联网的不断发展和普及,数据的处理和存储需求也越来越大,如何高效且可靠地处理和存储数据成为了业界和研究人员的热门话题。基于SpringBoot的分布式数据缓存和存储系统是近年来备受关注的一种解决方案。什么是分布式数据缓存和存储系统?分布式数据缓存和存储系统是指通过多个节点(服务器)分布式地存储数据,提高了数据的安全性和可靠性,同时也可以提升数据的处理性
 基于Spring Boot和MyBatis Plus实现ORM映射Jun 22, 2023 pm 09:27 PM
基于Spring Boot和MyBatis Plus实现ORM映射Jun 22, 2023 pm 09:27 PM在Javaweb应用开发过程中,ORM(Object-RelationalMapping)映射技术用来将数据库中的关系型数据映射到Java对象中,方便开发者进行数据访问和操作。SpringBoot作为目前最流行的Javaweb开发框架之一,已经提供了集成MyBatis的方式,而MyBatisPlus则是在MyBatis的基础上扩展的一种ORM框架。
 Spring Boot与NoSQL数据库的整合使用Jun 22, 2023 pm 10:34 PM
Spring Boot与NoSQL数据库的整合使用Jun 22, 2023 pm 10:34 PM随着互联网的发展,大数据分析和实时信息处理成为了企业的一个重要需求。为了满足这样的需求,传统的关系型数据库已经不再满足业务和技术发展的需要。相反,使用NoSQL数据库已经成为了一个重要的选择。在这篇文章中,我们将讨论SpringBoot与NoSQL数据库的整合使用,以实现现代应用程序的开发和部署。什么是NoSQL数据库?NoSQL是notonlySQL
 使用Spring Boot和JavaFX构建桌面应用程序Jun 22, 2023 am 10:55 AM
使用Spring Boot和JavaFX构建桌面应用程序Jun 22, 2023 am 10:55 AM随着技术的不断发展,我们现在可以使用不同的技术来构建桌面应用程序。而SpringBoot和JavaFX则是现在较为流行的选择之一。本文将重点介绍如何使用这两个框架来构建一个功能丰富的桌面应用程序。一、介绍SpringBoot和JavaFXSpringBoot是一个基于Spring框架的快速开发框架。它可以帮助开发者快速构建Web应用程序,同时提供一组开
 Spring Boot的任务调度和定时任务实现方法Jun 22, 2023 pm 11:58 PM
Spring Boot的任务调度和定时任务实现方法Jun 22, 2023 pm 11:58 PMSpringBoot是一款非常流行的Java开发框架,不仅具有快速开发的优势,而且还内置了很多实用的功能,其中,任务调度和定时任务就是其常用的功能之一。本文将探讨SpringBoot的任务调度和定时任务实现方法。一、SpringBoot任务调度简介SpringBoot任务调度(TaskScheduling)是指在特定的时间点或某个条件下,执行一些特


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Dreamweaver CS6
Visual web development tools

ZendStudio 13.5.1 Mac
Powerful PHP integrated development environment

Safe Exam Browser
Safe Exam Browser is a secure browser environment for taking online exams securely. This software turns any computer into a secure workstation. It controls access to any utility and prevents students from using unauthorized resources.

PhpStorm Mac version
The latest (2018.2.1) professional PHP integrated development tool





