 Operation and Maintenance
Operation and Maintenance Safety
Safety A complete interpretation of the black industry chain on the Internet
A complete interpretation of the black industry chain on the InternetWith the development of the Internet, the network black industry chain has gradually surfaced and become an important factor threatening network security. So, what is the Internet black industry chain? What is its composition and operation? This article will interpret the online black production chain from these aspects.
1. What is the Internet black product chain?
To put it simply, the Internet black industry chain is an industrial chain that uses the Internet to carry out illegal activities. It covers a variety of industries and individuals related to illegal network activities, including hackers, Trojan virus makers, phishers, fraud gangs, malware makers, network extortionists, etc. These people form a huge organizational system and cooperate with each other to maximize their interests.
2. The composition of the illegal network industry chain
The network illegal industry chain is composed of many different types of illegal industry elements. Specifically, it includes the following aspects:
1. Hackers
Hackers are the most core members of the network black industry chain. Their job is to hack into other people's computer systems and use them to perform illegal activities, such as stealing sensitive information and damaging websites.
2. Trojan virus makers
Trojan virus makers are another important link in the black industry chain. Their main task is to create Trojan viruses and then spread them. These viruses quietly plant backdoors into victim computers, causing system vulnerabilities and information leakage.
3. Phishers
Phishers refer to those who pretend to be trusted entities (such as banks, e-commerce platforms, etc.) and defraud individuals by sending false emails or messages. sensitive information. They are often hired by organized groups or black market solo operators.
4. Fraud gangs
Fraud gangs are groups that specialize in online fraud activities. They will set up various websites, forums and social media platforms to conduct fraudulent activities in various ways. Because they are able to use social engineering techniques to lure victims, the gains can be huge.
5. Malware creators
Malware creators are individuals or organizations that specialize in creating and distributing various types of malware. These malware include viruses, worms, spyware, adware, etc. When these software are installed in a victim's computer, they steal sensitive information and deliver malicious ads.
6. Internet extortionists
Internet extortionists refer to those who use the Internet to extort money from their victims. They will use various methods to coerce victims, such as mastering their sensitive information, locking their computer systems, attacking their websites, etc., to achieve their demands.
3. The operation mode of the Internet black industry chain
The operation method of the Internet black industry chain is usually a central organization to coordinate all actions. This organization is usually a team or a cluster of organizations that is responsible for formulating plans, grouping members' roles, assigning tasks, controlling resources, etc. The following is the typical operation mode of the Internet black industry chain.
1. Recruit new members
Hacker groups usually recruit new members on various forums, social media and black markets. These organizations require new members to have relevant skills (such as attack skills, programming skills, etc.) so that they can provide services in the black market.
2. Attack the target
Once the organization members are assigned a task, they will start attacking the target. These targets are usually large organizations (such as governments, large enterprises, etc.) because they hold large amounts of sensitive data and information that can facilitate higher profits for the organization.
3. Stealing information
After successfully attacking a target, black gangs usually steal sensitive information or directly blackmail them. This information includes financial information, personally identifiable information, sensitive documents and data, etc. Some organizations may also use this data for blackmail or extortion.
4. Sales information
Sales on the black market are very important because it is one of the main sources of income for the hacking team. Black property gangs will sell the sensitive information they obtain to other black market buyers to obtain higher profits. The price of this information on the black market depends on its value and market supply and demand.
5. Attack against software
The pattern of malware creators is different. They usually create various types of malware and distribute them in various ways. After the victim downloads and installs these malware, it causes harm to the computer system.
In the Internet black industry chain, everyone plays a different role, and everyone cooperates with each other to maximize their interests.
4. How to prevent illegal online product chains
How to prevent illegal online product chains? Here are some effective methods.
1. Use security software
Using security software (such as anti-virus software, firewalls, etc.) is one of the simplest but most important ways to prevent online black product chains. These software can help users prevent the intrusion of various malware and Trojan viruses.
2. Strengthen account security
Changing passwords frequently, using complex passwords, not using the same password, and turning on two-step verification as much as possible are also one of the important ways to prevent online black product chains.
3. Pay attention to network security education
Network security awareness education also plays a very important role in preventing illegal online production chains. When using the Internet, users should know some basic knowledge, such as how to identify fraudulent links and websites, how to avoid downloading malware, etc.
4. Regularly back up data
Regularly backing up data (including personal files and website files) will help users protect their information in the event of data leaks, data disasters, and ransomware intrusions. and data.
Conclusion
Through the introduction of this article, we can feel the harmfulness of the black industry chain in the Internet. After understanding the composition and operation methods of the illegal network industry chain, I believe that everyone will gradually strengthen their awareness of the prevention of the illegal network industry chain. Let us work together to launch a powerful counterattack against the black industry chain on the Internet.
The above is the detailed content of A complete interpretation of the black industry chain on the Internet. For more information, please follow other related articles on the PHP Chinese website!
 如何在 Windows 11 上创建移动热点Apr 17, 2023 pm 06:22 PM
如何在 Windows 11 上创建移动热点Apr 17, 2023 pm 06:22 PM当然,在Android智能手机和Windows11PC之间共享移动互联网可能很有用,尤其是在Wi-Fi不可用时。因此,当其他选项刚刚出现时,知道如何与Windows设备共享移动互联网会非常方便。就像没有Wi-Fi时iPhone可以连接到Mac一样,Android设备也允许用户通过USB和蓝牙将智能手机的互联网连接与任何Windows笔记本电脑连接。对于我们许多人来说,通过电缆连接手机和PC不是一种选择,而通过蓝牙连接互联网可能会很慢。因此,使用智能手机创建W
 实用Word技巧分享:2招轻松解决多图片排版!Apr 01, 2023 am 10:57 AM
实用Word技巧分享:2招轻松解决多图片排版!Apr 01, 2023 am 10:57 AM多图片排版,是Word编辑文档时常见场景之一,几乎每个人都会碰到,对很多人来说仍然是一大难题。当图片数量一多,很多人都不知道图片该怎么摆放,如何快速高效地搞定一组图片? 因为没有掌握系统的套路技巧,每次制作都花费大量时间,做不出满意的效果。今天我就教大家2 招,轻松解决多图片排版!
 如何在网络安全中使用AIApr 14, 2023 pm 02:10 PM
如何在网络安全中使用AIApr 14, 2023 pm 02:10 PMCybersecurity Ventures的报告显示,2021年全球网络犯罪带来的损失为6万亿美元,并预计打击网络犯罪的全球支出在2025年将增至10.5万亿美元,是2015年的三倍之多(3万亿美元)。人工智能,几乎是唯一应对方案。另一家研究机构Statista认为,2020年网络安全领域的人工智能价值已超过100亿美元,并预计到2027年将达到450亿美元。IBM则认为,缺乏人工智能安全的企业,在抵御网络攻击方面的成本是部署了AI自动化防御系统的企业的三倍。来自Meticulous的研究数据
 Microsoft Edge 102.0.1245.41 带来安全修复和 PDF 打印错误解决方案May 06, 2023 pm 07:37 PM
Microsoft Edge 102.0.1245.41 带来安全修复和 PDF 打印错误解决方案May 06, 2023 pm 07:37 PM微软在周末为其Edge浏览器发布了两个小更新。该公司在周五和今天发布了另一个安全更新。虽然周五的更新修复了影响Edge浏览器的安全问题,但今天的更新解决了影响所有基于Chromium的网络浏览器的安全问题。此外,该更新似乎解决了通过Edge浏览器访问PDF文件时无法打印的问题。稳定版本通道的Edge102.0.1245.41被标记为修复了多个漏洞的维护更新。Microsoft尚未更新发行说明。不过,该公司此前已告知Chromium和Edge浏览器存在以下漏洞:
 从“微软安全的下一步”数字活动中可以期待什么Apr 19, 2023 am 10:46 AM
从“微软安全的下一步”数字活动中可以期待什么Apr 19, 2023 am 10:46 AMMicrosoft数字活动的下一步安全计划将于太平洋时间(UTC-8)时间2月24日上午9:00至上午10:30举行。随着无处不在的威胁不断增长,为他们的公司寻找有效安全解决方案的各种组织希望在这次活动中找到一些有价值的技巧和知识。Microsoft的安全下一步计划将强调全面的安全方法对业务增长的重要性。它将欢迎不同的安全专家讨论最新的创新和技术,以减少最新的威胁风险。一些演讲者包括VasuJakkal(微软公司安全、合规和身份副总裁)和JeffPollard(F
 人工智能聊天机器人在网络安全领域的发展趋势如何?Apr 22, 2023 pm 11:13 PM
人工智能聊天机器人在网络安全领域的发展趋势如何?Apr 22, 2023 pm 11:13 PMOpenAI公司推出的聊天机器人ChatGPT有很多很好的用途,但就像任何新技术一样,有些人会利用ChatGPT用于罪恶的目的。从编写电子邮件等相对简单的任务,到撰写论文或编译代码等更复杂的工作,OpenAI公司的人工智能驱动的自然语言处理工具ChatGPT自从推出以来就引起了人们的极大兴趣。当然,ChatGPT并不完美——众所周知,当它误解了从中学习的信息时就会犯错,但许多人将它和其他人工智能工具视为互联网的未来。OpenAI公司在ChatGPT的服务条款中加入了禁止生成恶意软件的条目,其中包
 Zerodium 宣布为 Microsoft Outlook 零点击 RCE 安全漏洞支付 400,000 美元Apr 29, 2023 pm 09:28 PM
Zerodium 宣布为 Microsoft Outlook 零点击 RCE 安全漏洞支付 400,000 美元Apr 29, 2023 pm 09:28 PM<ul><li><strong>点击进入:</strong>ChatGPT工具插件导航大全</li></ul><figureclass="imageimage--expandable"><imgsrc="/uploads/2023041
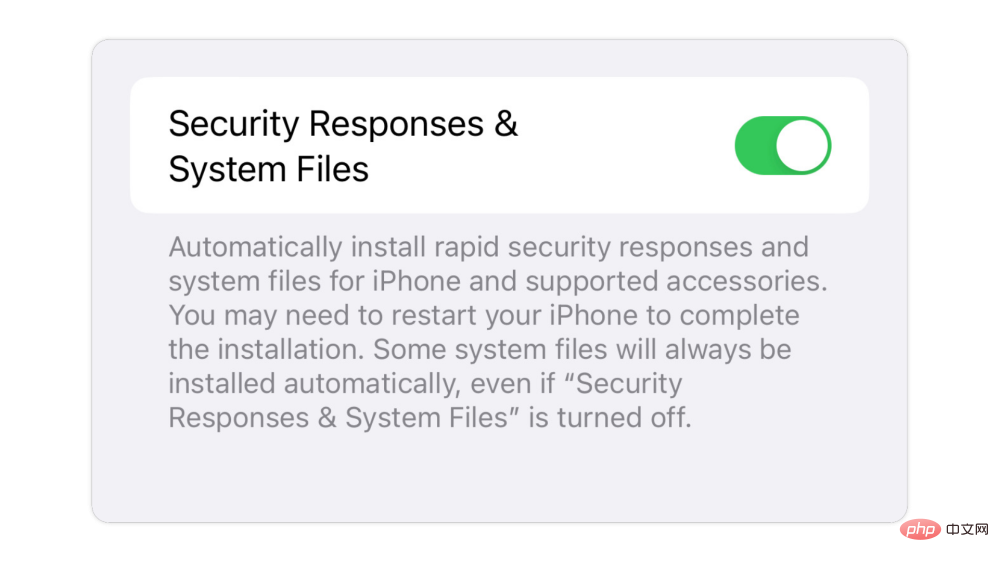 您应该了解的 5 个重要的 iPhone 安全功能Apr 18, 2023 am 09:58 AM
您应该了解的 5 个重要的 iPhone 安全功能Apr 18, 2023 am 09:58 AM虽然iOS16拥有经过重新设计的时髦锁屏,但在其下方,最新的操作系统拥有一系列全新的安全和隐私功能,旨在帮助保护您和您的数据。这里有五项新功能可以更好地保护您的iPhone免受黑客攻击,让您更加安心。快速安全响应iOS以及macOS和iPadOS现在允许自动“快速安全响应”。这使Apple能够快速修补软件(即零日漏洞或其他严重漏洞)并将其发送到数百万台设备,而无需重新启动或任何最终用户交互。这在“设置”>“通用”>“软件更新”>“自动更新”下可用有趣的是,即使关闭了这个


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

PhpStorm Mac version
The latest (2018.2.1) professional PHP integrated development tool

DVWA
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is very vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, to help web developers better understand the process of securing web applications, and to help teachers/students teach/learn in a classroom environment Web application security. The goal of DVWA is to practice some of the most common web vulnerabilities through a simple and straightforward interface, with varying degrees of difficulty. Please note that this software

SecLists
SecLists is the ultimate security tester's companion. It is a collection of various types of lists that are frequently used during security assessments, all in one place. SecLists helps make security testing more efficient and productive by conveniently providing all the lists a security tester might need. List types include usernames, passwords, URLs, fuzzing payloads, sensitive data patterns, web shells, and more. The tester can simply pull this repository onto a new test machine and he will have access to every type of list he needs.

Safe Exam Browser
Safe Exam Browser is a secure browser environment for taking online exams securely. This software turns any computer into a secure workstation. It controls access to any utility and prevents students from using unauthorized resources.

MinGW - Minimalist GNU for Windows
This project is in the process of being migrated to osdn.net/projects/mingw, you can continue to follow us there. MinGW: A native Windows port of the GNU Compiler Collection (GCC), freely distributable import libraries and header files for building native Windows applications; includes extensions to the MSVC runtime to support C99 functionality. All MinGW software can run on 64-bit Windows platforms.





