HTTP honeypot technology in Nginx
HTTP honeypot technology refers to simulating a website or web application in order to detect and block potential attackers. In this process, honeypots serve as bait to attract attackers in order to identify and learn attack techniques and strategies, and find vulnerabilities to improve. Currently, HTTP honeypot technology is widely used in the security protection of websites and web applications. Nginx is a high-performance web server that has some great HTTP honeypot technology to protect websites from attacks.
- Access Log module
Nginx Access Log module can capture information including request method, URL, HTTP status code, request source and visitor IP address. The Access Log module provides some extremely useful data for HTTP honeypot technology. This data can be used to create a dummy website or web application to provide attacker bait.
You can use the following configuration to add the Access Log module to the Nginx configuration file.
http {
...
access_log path format;
...
}- Error Log module
The Nginx Error Log module can record all web server errors. These errors include syntax errors, file not found, and invalid requests, as well as most error types. The Error Log module can provide more data for HTTP honeypot technology, allowing you to better monitor potential attackers and more easily protect your servers through learning and improvement.
You can use the following configuration to add the Error Log module to the Nginx configuration file.
http {
...
error_log path;
...
}- Rewrite module
Nginx Rewrite module can rewrite URL request paths using regular expressions. You can use the Rewrite module to create a virtual website that looks like a real website or web application. This dummy website can be used with HTTP honeypot techniques to lure attackers in.
The following is a simple Rewrite module configuration example:
http {
...
server {
listen 80;
server_name honeypot.example.com;
rewrite ^(.*)$ https://maybefakesite.com$request_uri? redirect;
}
...
}- HTTP Referer module
Nginx HTTP Referer module can capture the access point from which website own website, which provides a more comprehensive security guarantee for HTTP honeypot technology. With the help of the HTTP Referer module, you can log the origin of requests, identify attackers’ intentions, and learn improvements.
You can use the following configuration to add the HTTP Referer module to the Nginx configuration file.
http {
...
server {
listen 80;
server_name honeypot.example.com;
if ($http_referer ~* (badreferer.com|anotherbadsite.com)) {
return 403;
}
}
...
}- Limit_req module
Nginx Limit_req module can limit the request frequency, which is very effective in dealing with DoS or DDoS attacks. At the same time, it is also a good choice for HTTP honeypot technology.
The following is an example of a Limit_req module configuration:
http {
...
limit_req_zone $binary_remote_addr zone=honeypot:10m rate=1r/s;
server {
listen 80;
server_name honeypot.example.com;
location / {
limit_req zone=honeypot burst=5 nodelay;
...
}
}
...
}When using HTTP honeypot technology, it is very important to maintain the current attack mode and situation. You need to closely monitor the activity taking place on your virtual website or web application in order to understand the attackers' strategies and tools. Learning to improve your honeypot and Nginx configuration is an ongoing process as you learn more harmful behaviors and attack strategies. Nginx is a very powerful HTTP server that provides some great HTTP honeypot technology to protect your website security.
The above is the detailed content of HTTP honeypot technology in Nginx. For more information, please follow other related articles on the PHP Chinese website!
 Springboot怎么使用内置tomcat禁止不安全HTTPMay 12, 2023 am 11:49 AM
Springboot怎么使用内置tomcat禁止不安全HTTPMay 12, 2023 am 11:49 AMSpringboot内置tomcat禁止不安全HTTP方法1、在tomcat的web.xml中可以配置如下内容让tomcat禁止不安全的HTTP方法/*PUTDELETEHEADOPTIONSTRACEBASIC2、Springboot使用内置tomcat没有web.xml配置文件,可以通过以下配置进行,简单来说就是要注入到Spring容器中@ConfigurationpublicclassTomcatConfig{@BeanpublicEmbeddedServletContainerFacto
 JAVA发送HTTP请求的方式有哪些Apr 15, 2023 am 09:04 AM
JAVA发送HTTP请求的方式有哪些Apr 15, 2023 am 09:04 AM1.HttpURLConnection使用JDK原生提供的net,无需其他jar包,代码如下:importcom.alibaba.fastjson.JSON;importjava.io.BufferedReader;importjava.io.InputStream;importjava.io.InputStreamReader;importjava.io.OutputStream;importjava.net.HttpURLConnection;
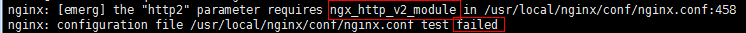 nginx中如何升级到支持HTTP2.0May 24, 2023 pm 10:58 PM
nginx中如何升级到支持HTTP2.0May 24, 2023 pm 10:58 PM一、前言#ssl写在443端口后面。这样http和https的链接都可以用listen443sslhttp2default_server;server_namechat.chengxinsong.cn;#hsts的合理使用,max-age表明hsts在浏览器中的缓存时间,includesubdomainscam参数指定应该在所有子域上启用hsts,preload参数表示预加载,通过strict-transport-security:max-age=0将缓存设置为0可以撤销hstsadd_head
 Nginx的HTTP2协议优化与安全设置Jun 10, 2023 am 10:24 AM
Nginx的HTTP2协议优化与安全设置Jun 10, 2023 am 10:24 AM随着互联网的不断发展和改善,Web服务器在速度和性能上的需求也越来越高。为了满足这样的需求,Nginx已经成功地掌握了HTTP2协议并将其融入其服务器的性能中。HTTP2协议要比早期的HTTP协议更加高效,但同时也存在着特定的安全问题。本文将为您详细介绍如何进行Nginx的HTTP2协议优化和安全设置。一、Nginx的HTTP2协议优化1.启用HTTP2在N
 Nginx中HTTP的keepalive怎么配置May 12, 2023 am 11:28 AM
Nginx中HTTP的keepalive怎么配置May 12, 2023 am 11:28 AMhttpkeepalive在http早期,每个http请求都要求打开一个tpcsocket连接,并且使用一次之后就断开这个tcp连接。使用keep-alive可以改善这种状态,即在一次tcp连接中可以持续发送多份数据而不会断开连接。通过使用keep-alive机制,可以减少tcp连接建立次数,也意味着可以减少time_wait状态连接,以此提高性能和提高httpd服务器的吞吐率(更少的tcp连接意味着更少的系统内核调用,socket的accept()和close()调用)。但是,keep-ali
 Python的HTTP客户端模块urllib与urllib3怎么使用May 20, 2023 pm 07:58 PM
Python的HTTP客户端模块urllib与urllib3怎么使用May 20, 2023 pm 07:58 PM一、urllib概述:urllib是Python中请求url连接的官方标准库,就是你安装了python,这个库就已经可以直接使用了,基本上涵盖了基础的网络请求功能。在Python2中主要为urllib和urllib2,在Python3中整合成了urllib。Python3.x中将urllib2合并到了urllib,之后此包分成了以下四个模块:urllib.request:它是最基本的http请求模块,用来模拟发送请求urllib.error:异常处理模块,如果出现错误可以捕获这些异常urllib
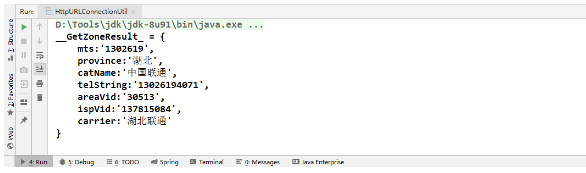 怎么利用Java实现调用http请求Jun 02, 2023 pm 04:57 PM
怎么利用Java实现调用http请求Jun 02, 2023 pm 04:57 PM一、概述在实际开发过程中,我们经常需要调用对方提供的接口或测试自己写的接口是否合适。很多项目都会封装规定好本身项目的接口规范,所以大多数需要去调用对方提供的接口或第三方接口(短信、天气等)。在Java项目中调用第三方接口的方式有:1、通过JDK网络类Java.net.HttpURLConnection;2、通过common封装好的HttpClient;3、通过Apache封装好的CloseableHttpClient;4、通过SpringBoot-RestTemplate;二、Java调用第三方
 Nginx http运行状况健康检查如何配置May 14, 2023 pm 06:10 PM
Nginx http运行状况健康检查如何配置May 14, 2023 pm 06:10 PM被动检查对于被动健康检查,nginx和nginxplus会在事件发生时对其进行监控,并尝试恢复失败的连接。如果仍然无法恢复正常,nginx开源版和nginxplus会将服务器标记为不可用,并暂时停止向其发送请求,直到它再次标记为活动状态。上游服务器标记为不可用的条件是为每个上游服务器定义的,其中包含块中server指令的参数upstream:fail_timeout-设置服务器标记为不可用时必须进行多次失败尝试的时间,以及服务器标记为不可用的时间(默认为10秒)。max_fails-设置在fai


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Safe Exam Browser
Safe Exam Browser is a secure browser environment for taking online exams securely. This software turns any computer into a secure workstation. It controls access to any utility and prevents students from using unauthorized resources.

ZendStudio 13.5.1 Mac
Powerful PHP integrated development environment

SublimeText3 English version
Recommended: Win version, supports code prompts!

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools






