What is WebShell?
Originally, Webshell was often referred to as a script for Web server administrators to remotely manage the server. Later, with the birth of some Webshell management tools, the process of obtaining Web permissions was greatly simplified, so it was gradually called a Web intrusion tool script.
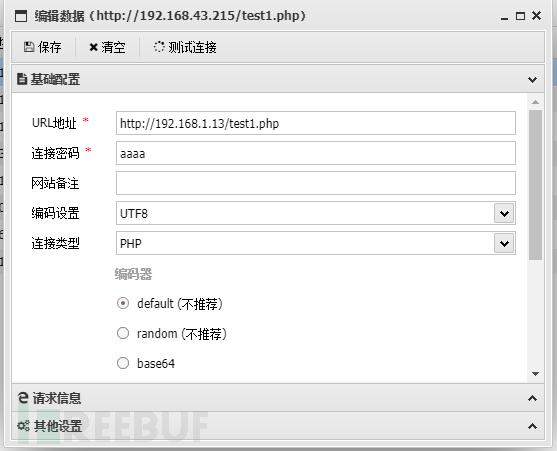
Webshell is different from vulnerabilities, but uses application vulnerabilities or server vulnerabilities (file upload vulnerabilities, file inclusion vulnerabilities, etc.) to upload script files to the server for subsequent exploitation, which belongs to the subsequent exploitation of penetration testing and ATT&CK's TA0002 Execution (execution) stage.

Figure 1 TA0002
Reference source: https://mitre-attack.github.io/attack-navigator/(ATT&CK Navigator)
In order to bypass detection and protection equipment, software, etc., attackers often change their Webshell writing methods to ensure that their scripts will not be detected while ensuring functionality. Among them, PHP scripts are more prominent because There are many available functions in the PHP scripting language, which leads to ever-changing confusion and deformation of writing methods in PHP.
One-sentence Trojans also belong to Webshell scripts. Friends who are interested in one-sentence Trojans can refer to the previous issue's "Multiple Transformations of One-Sentence Trojans" to learn and understand by themselves. This article will not go into details.
Background
When I analyzed Webshells before, I found that there is a type of Webshell that can completely bypass all kinds of detection software. This type of script often looks like it at the code level. It is meaningless and has no common Webshell features, but after digging through the layers, it is not difficult to find the idea of this type of obfuscated script. I just recently received an interesting obfuscated script, and I want to share the analysis process of the script with my friends. I also hope it can serve as a starting point.
First sight of the script
When I first saw this script, I saw the obvious eval function in its content, so I instinctively read this part of the code It was extracted, but it was not enough to prove anything, because the content was all seemingly clueless garbled code, without any trace of WebShell.
If you look carefully, you can find that in addition to eval, the three functions gzinflate, base64_decode, and str_rot13 are also called. Perhaps you can start with these three functions to find a breakthrough in analysis.

Figure 2 Script content
Function explanation
str_rot13()
ROT13 encoding moves each letter forward 13 letters in the alphabet. Numbers and non-alphabetic characters remain unchanged (Caesar cipher).
base64_decode()
Base64 encode the string content.
Gzinflate
The ZLIB_ENCODING_RAW encoding method is used by default for data, and the deflate data compression algorithm is used. In fact, LZ7 is used for compression first, and then Huffman coding is used for compression.
Analysis
1.Content Analysis

Figure 3 Calling the echo command
Using the echo command to parse the content, it was found that str_rot13() was executed, so I repeated this idea and tried to peel off the original content layer by layer.

Figure 4 Analysis results
2.Repeated analysis
After three echoes After repeated parsing of the command, what appeared was finally no longer a monotonous code, which proved that the direction of analysis was probably correct, and judging from the amount of code, it felt like a Trojan horse with multiple functions, commonly known as a horse.

Figure 5 Multiple parsing
3.Call the eval function to run the code content
Good guy, he is indeed a big horse.
After research, it was found that the functions of this Trojan include obtaining system information, reading directories, downloading files, uploading files, etc.

Picture 6 The original appearance of Malaysia
The above is the detailed content of What is the webshell analysis of obfuscated deformation?. For more information, please follow other related articles on the PHP Chinese website!
 nginx负载均衡下的webshell上传如何实现May 16, 2023 am 08:16 AM
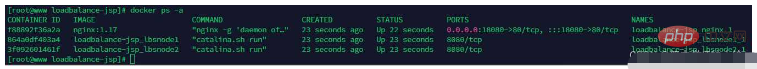
nginx负载均衡下的webshell上传如何实现May 16, 2023 am 08:16 AM场景描述假定在真实生产环境中,存在一个RCE漏洞,可以让我们获取WebShell环境的安装首先在GetHub上拉去漏洞的镜像前,需提前在centos上安装nginx和tomcat以及配置好nginx以及tomcat的相关配置文件,在使用docker将镜像拉取下来,进行漏洞的复现。1、先将docker环境搭建起来2、测试tomcat是否可以访问根据上图可以看出,后端的tomcat是可以访问的3、查看docker中nginx反向代理的负载均衡4、查看docker中lbsnode1中的ant.jsp文
 如何进行墨者靶场WebShell文件上传漏洞分析溯源Jun 01, 2023 am 08:55 AM
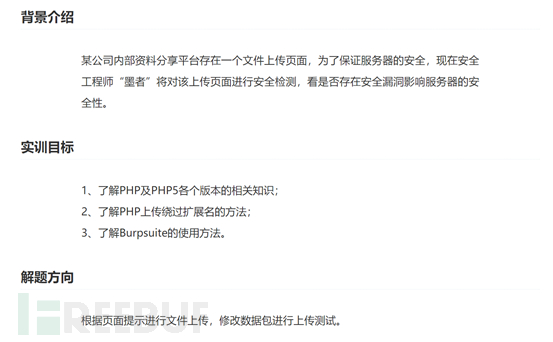
如何进行墨者靶场WebShell文件上传漏洞分析溯源Jun 01, 2023 am 08:55 AM1.打开网址后,发现是一个上传页面2.直接上传后缀名为php的文件,发现无法上传3.采用BurpSuite进行抓包,将上传的后缀为php的文件的后缀改为php5,即可绕过4.使用菜刀进行连接,在var/www/html的目录中,发现带有KEY的文件,打开即可看到key5.打开另一个网址,同时也是一个上传页面,但是设置了上传名单,仅允许以.gif.jpg.png为后缀文件通过上传6.我们写一个txt一句话木马,将其后缀改为jpg7.在上传的时候,采用BurpSiuit抓包,并对文件后缀进行修改,显
 宝塔面板的WebShell安全设置Jun 21, 2023 pm 04:35 PM
宝塔面板的WebShell安全设置Jun 21, 2023 pm 04:35 PM随着互联网安全问题的日益突出,各大网站和应用程序的安全性也成为越来越重要的问题。尤其是在网站运维管理中,常常需要使用WebShell这种工具来进行维护和修复,但WebShell也常常被黑客利用,成为攻击者入侵的一个入口。本文将介绍宝塔面板的WebShell安全设置,帮助网站管理员提高站点的安全性。一、WebShell的概念和常见用途1.概念WebShell是
 浅谈帝国cms框架的WebshellMar 16, 2021 am 10:48 AM
浅谈帝国cms框架的WebshellMar 16, 2021 am 10:48 AM本篇文章给大家介绍一下帝国cms框架的Webshell。有一定的参考价值,有需要的朋友可以参考一下,希望对大家有所帮助。
 WAF对WebShell流量检测的性能分析是怎样的May 16, 2023 pm 07:47 PM
WAF对WebShell流量检测的性能分析是怎样的May 16, 2023 pm 07:47 PM本地环境组建从保留的截图来看,对方的php版本是5.6.40,所以我要搭一个apache+php5.6.40的测试环境。打开virtualbox,链接复制出来一份centos镜像系统,按照以下流程配置一遍。1.安装apacheyuminstall-yhttpdhttpd-vServerversion:Apache/2.4.6(CentOS)Serverbuilt:Aug8201911:41:182.安装php5.6yum-yinstallepel-releaserpm-Uvhhttps://mi
 对混淆变形的Webshell分析是怎样的May 19, 2023 pm 11:07 PM
对混淆变形的Webshell分析是怎样的May 19, 2023 pm 11:07 PMWebShell是什么?在最初的时候,Webshell经常被用来作为Web服务器管理员对服务器进行远程管理的一类脚本的简称。后来,随着一些Webshell管理工具的诞生,使得获取Web权限的过程被很大程度地简易化,于是逐渐被称为Web入侵的工具脚本。Webshell不同于漏洞,而是利用应用漏洞或服务器漏洞(文件上传漏洞、文件包含漏洞等)将脚本文件上传到服务器进行后续利用,属于渗透测试的后续利用和ATT&CK的TA0002Execution(执行)阶段。图1TA0002参考来源:https
 网站漏洞修复之上传webshell漏洞修补的示例分析May 30, 2023 pm 01:49 PM
网站漏洞修复之上传webshell漏洞修补的示例分析May 30, 2023 pm 01:49 PMSINE安全在对某客户的网站进行网站漏洞检测与修复发现该网站存在严重的sql注入漏洞以及上传webshell网站木马文件漏洞,该网站使用的是某CMS系统,采用PHP语言开发,mysql数据库的架构,该网站源码目前是开源的状态。某CMS是专注于提供付费知识的社交CMS系统,知识付费在目前的互联网中有这很高的需求,该系统可以对文档进行分享,收费下载,用户发布的知识内容可以隐藏,提供给付费客户阅读。代码比较精简深受广大站长们的喜欢,该网站漏洞主要发生在上传压缩包的同时,构造恶意解压代码讲zip包里的w
 webshell被上传溯源事件的示例分析May 12, 2023 pm 02:43 PM
webshell被上传溯源事件的示例分析May 12, 2023 pm 02:43 PM巡检查杀首先,我明白自己要做的不是找到这个上传的位置是哪里出现的,我应该登上服务器进行webshel查杀,进行巡检,找找看是否被别人入侵了,是否存在后门等等情况。虽然报的是我们公司的ip地址,万一漏掉了几个webshell,被别人上传成功了没检测出来,那服务器被入侵了如何能行。所以我上去巡检了服务器,上传这个webshell查杀工具进行查杀,使用netstat-anpt和iptables-L判断是否存在后门建立,查看是否有挖矿程序占用CPU,等等,此处不详细展开了。万幸的是服务器没有被入侵,然后


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

VSCode Windows 64-bit Download
A free and powerful IDE editor launched by Microsoft

SublimeText3 Mac version
God-level code editing software (SublimeText3)

EditPlus Chinese cracked version
Small size, syntax highlighting, does not support code prompt function

MantisBT
Mantis is an easy-to-deploy web-based defect tracking tool designed to aid in product defect tracking. It requires PHP, MySQL and a web server. Check out our demo and hosting services.

mPDF
mPDF is a PHP library that can generate PDF files from UTF-8 encoded HTML. The original author, Ian Back, wrote mPDF to output PDF files "on the fly" from his website and handle different languages. It is slower than original scripts like HTML2FPDF and produces larger files when using Unicode fonts, but supports CSS styles etc. and has a lot of enhancements. Supports almost all languages, including RTL (Arabic and Hebrew) and CJK (Chinese, Japanese and Korean). Supports nested block-level elements (such as P, DIV),







