 Operation and Maintenance
Operation and Maintenance Safety
Safety What is a simple and secure API authorization mechanism based on signature algorithm?
What is a simple and secure API authorization mechanism based on signature algorithm?When I was working on an advertising system, I found that the advertising systems of most of the platforms I connected to used tokens to authorize interfaces, and this token remained unchanged and was provided by advertisers. It can be said that this is the streaking interface. However, this interface does not have high security requirements. It can only prevent malicious calls and verify the identity of the channel.
Last year, the author wrote an API unified authorization platform, which provides unified authorization management for internal service open interfaces and third-party system calls. Apart from facilitating management interface authorization, it has no other purpose, but it costs money to deploy. This is probably the most pointless project I've ever done.
The API authorization mechanism introduced today may also be a more widely used API interface authorization mechanism. I remember that when the author used to do the WeChat payment function, the payment interface provided by WeChat also used this method: signature. Advantages: Simple, no impact on performance, no additional cost.
The implementation logic of this authorization method is that the authorizer sets a unique identity (key) and independent key for each access platform, which is actually equivalent to an account password. The accessing system is required to carry three parameters in the request header every time it initiates a request, namely the identity (key), the timestamp of the request, and the signature. The authorizing system verifies the signature when receiving the request. The request will be released only if it passes.
The process of verifying the signature is to obtain the key and timestamp from the request header, then generate a signature using the same algorithm based on the key (the caller and the authorizer use the same signature algorithm), and finally compare the signature obtained from the request header Whether they are equal, if so, the verification is successful, otherwise the verification fails.
The implementation process of the authorization method based on signature algorithm is as follows:
Authorizer:
1. Define the signature algorithm and provide the signature generation algorithm for access Party, and generate a key and identity for the access party;
2. Intercept the interface that needs to verify the signature in the project, obtain the timestamp and identity from the request header, and generate a signature based on the key and signature algorithm , compare the generated signature with the signature obtained from the request header, if they are the same, continue to step 3, otherwise reject the request;
3. Verify the timeliness of the request, use the current system timestamp and the signature obtained from the request header Compare the timestamps received, and if the request is within the valid time range, the request will be released, otherwise it will be rejected and the signature will be expired.
Access party:
1. Obtain the docking document from the authorized party, and ask the authorized party for the key and identity;
2. Encapsulate the signature method according to the signature generation algorithm provided in the document;
3. When initiating a request, write the identity identifier, current timestamp, and signature into the request header.
The signature generation algorithm can be customized. For example, after splicing the identity (key), timestamp (timestamp) and key together, an irreversible algorithm is used to encrypt the string to generate a signature, such as MD5. algorithm. The more complex the rules, the harder they are to crack.
What are the benefits of adding a timestamp to a signature?
The first is to add timeliness to the signature. The authorization system can limit the validity time of the signature to one second or five seconds, using the request timestamp to compare with the current timestamp. However, the system time of both parties must be correct.
The second is security. If a hacker intercepts the request of your system, then modifies the request and then initiates the request, it will definitely take time, so when the system receives the tampered request, the validity period of the signature It has passed. If you change the timestamp passed in the request header, the authorizing system of the request will generate a different signature than the one passed in the request header, so the request will still be invalid.
If you don’t know the key, you cannot generate a valid signature without understanding the signature rules of the authorized party (broiler). Files signed using an asymmetric encryption algorithm make it nearly impossible to crack the key through brute force.
Then why use timestamp instead of formatting time string?
This may be due to consideration of time zone compatibility. If different computer rooms are in different time zones, the time will be different, but the timestamp All the same.
In order to maximize the security of this authorization method, first of all, the rules for generating signatures must be complex enough, then the encryption algorithm of the signature must be irreversible, never use an algorithm like Base64, and finally, the key must be sufficient It is sufficiently complex to ensure that even if the signature generation rules are known, it is impossible to brute force the key.
Signature rules refer to the rules for generating signature strings before encryption. For example, the rules include key, key, and timestamp, where key and key will appear twice. Assume that the key is "app", the secret key is "123", the timestamp is "11111111111111", the pre-encrypted signature generated by splicing is "app1231111111111111app123", and finally the spliced string is encrypted through the encryption algorithm to generate the final signature.
Isn’t it troublesome to write the signature logic for each interface?
No. For the authorizer, the signature verification logic can be completed through filters or interceptors; for the caller, there are different methods using different frameworks, but we can always find a way to only write the signature logic once, right?
The above is the detailed content of What is a simple and secure API authorization mechanism based on signature algorithm?. For more information, please follow other related articles on the PHP Chinese website!
 如何快速把你的 Python 代码变为 APIApr 14, 2023 pm 06:28 PM
如何快速把你的 Python 代码变为 APIApr 14, 2023 pm 06:28 PM提到API开发,你可能会想到DjangoRESTFramework,Flask,FastAPI,没错,它们完全可以用来编写API,不过,今天分享的这个框架可以让你更快把现有的函数转化为API,它就是Sanic。Sanic简介Sanic[1],是Python3.7+Web服务器和Web框架,旨在提高性能。它允许使用Python3.5中添加的async/await语法,这可以有效避免阻塞从而达到提升响应速度的目的。Sanic致力于提供一种简单且快速,集创建和启动于一体的方法
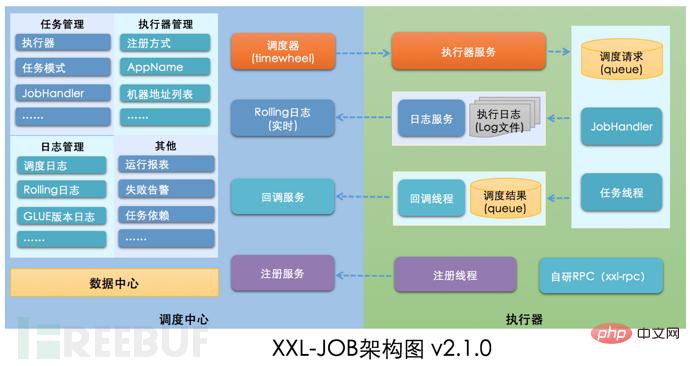 如何进行XXL-JOB API接口未授权访问RCE漏洞复现May 12, 2023 am 09:37 AM
如何进行XXL-JOB API接口未授权访问RCE漏洞复现May 12, 2023 am 09:37 AMXXL-JOB描述XXL-JOB是一个轻量级分布式任务调度平台,其核心设计目标是开发迅速、学习简单、轻量级、易扩展。现已开放源代码并接入多家公司线上产品线,开箱即用。一、漏洞详情此次漏洞核心问题是GLUE模式。XXL-JOB通过“GLUE模式”支持多语言以及脚本任务,该模式任务特点如下:●多语言支持:支持Java、Shell、Python、NodeJS、PHP、PowerShell……等类型。●WebIDE:任务以源码方式维护在调度中心,支持通过WebIDE在线开发、维护。●动态生效:用户在线通
 PHP8.0中的API客户端库:GuzzleMay 14, 2023 am 08:54 AM
PHP8.0中的API客户端库:GuzzleMay 14, 2023 am 08:54 AM随着网络技术的发展,Web应用程序和API应用程序越来越普遍。为了访问这些应用程序,需要使用API客户端库。在PHP中,Guzzle是一个广受欢迎的API客户端库,它提供了许多功能,使得在PHP中访问Web服务和API变得更加容易。Guzzle库的主要目标是提供一个简单而又强大的HTTP客户端,它可以处理任何形式的HTTP请求和响应,并且支持并发请求处理。在
 让机器人学会咖啡拉花,得从流体力学搞起!CMU&MIT推出流体模拟平台Apr 07, 2023 pm 04:46 PM
让机器人学会咖啡拉花,得从流体力学搞起!CMU&MIT推出流体模拟平台Apr 07, 2023 pm 04:46 PM机器人也能干咖啡师的活了!比如让它把奶泡和咖啡搅拌均匀,效果是这样的:然后上点难度,做杯拿铁,再用搅拌棒做个图案,也是轻松拿下:这些是在已被ICLR 2023接收为Spotlight的一项研究基础上做到的,他们推出了提出流体操控新基准FluidLab以及多材料可微物理引擎FluidEngine。研究团队成员分别来自CMU、达特茅斯学院、哥伦比亚大学、MIT、MIT-IBM Watson AI Lab、马萨诸塞大学阿默斯特分校。在FluidLab的加持下,未来机器人处理更多复杂场景下的流体工作也都
 Vue3 Composition API怎么优雅封装第三方组件May 11, 2023 pm 07:13 PM
Vue3 Composition API怎么优雅封装第三方组件May 11, 2023 pm 07:13 PM前言对于第三方组件,如何在保持第三方组件原有功能(属性props、事件events、插槽slots、方法methods)的基础上,优雅地进行功能的扩展了?以ElementPlus的el-input为例:很有可能你以前是这样玩的,封装一个MyInput组件,把要使用的属性props、事件events和插槽slots、方法methods根据自己的需要再写一遍://MyInput.vueimport{computed}from'vue'constprops=define
 Windows 11 正在获得一项新的 API 支持的功能来解决网络问题Apr 20, 2023 pm 02:28 PM
Windows 11 正在获得一项新的 API 支持的功能来解决网络问题Apr 20, 2023 pm 02:28 PM当您的WindowsPC出现网络问题时,问题出在哪里并不总是很明显。很容易想象您的ISP有问题。然而,Windows笔记本电脑上的网络并不总是顺畅的,Windows11中的许多东西可能会突然导致Wi-Fi网络中断。随机消失的Wi-Fi网络是Windows笔记本电脑上报告最多的问题之一。网络问题的原因各不相同,也可能因Microsoft的驱动程序或Windows而发生。Windows是大多数情况下的问题,建议使用内置的网络故障排除程序。在Windows11
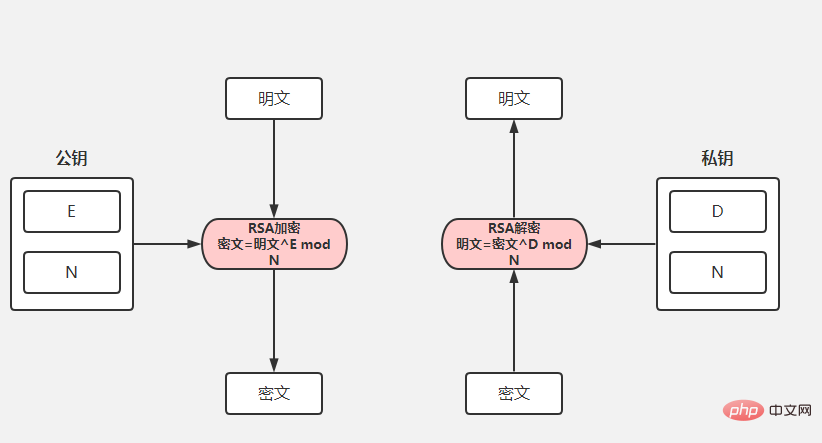 SpringBoot怎么实现api加密May 15, 2023 pm 11:10 PM
SpringBoot怎么实现api加密May 15, 2023 pm 11:10 PMSpringBoot的API加密对接在项目中,为了保证数据的安全,我们常常会对传递的数据进行加密。常用的加密算法包括对称加密(AES)和非对称加密(RSA),博主选取码云上最简单的API加密项目进行下面的讲解。下面请出我们的最亮的项目rsa-encrypt-body-spring-boot项目介绍该项目使用RSA加密方式对API接口返回的数据加密,让API数据更加安全。别人无法对提供的数据进行破解。SpringBoot接口加密,可以对返回值、参数值通过注解的方式自动加解密。什么是RSA加密首先我
 设计API接口时,要注意这些地方!Jan 09, 2023 am 11:10 AM
设计API接口时,要注意这些地方!Jan 09, 2023 am 11:10 AM本篇文章给大家带来了关于API的相关知识,其中主要介绍了设计API需要注意哪些地方?怎么设计一个优雅的API接口,感兴趣的朋友,下面一起来看一下吧,希望对大家有帮助。


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

MinGW - Minimalist GNU for Windows
This project is in the process of being migrated to osdn.net/projects/mingw, you can continue to follow us there. MinGW: A native Windows port of the GNU Compiler Collection (GCC), freely distributable import libraries and header files for building native Windows applications; includes extensions to the MSVC runtime to support C99 functionality. All MinGW software can run on 64-bit Windows platforms.

DVWA
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is very vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, to help web developers better understand the process of securing web applications, and to help teachers/students teach/learn in a classroom environment Web application security. The goal of DVWA is to practice some of the most common web vulnerabilities through a simple and straightforward interface, with varying degrees of difficulty. Please note that this software

SecLists
SecLists is the ultimate security tester's companion. It is a collection of various types of lists that are frequently used during security assessments, all in one place. SecLists helps make security testing more efficient and productive by conveniently providing all the lists a security tester might need. List types include usernames, passwords, URLs, fuzzing payloads, sensitive data patterns, web shells, and more. The tester can simply pull this repository onto a new test machine and he will have access to every type of list he needs.

WebStorm Mac version
Useful JavaScript development tools

SublimeText3 Linux new version
SublimeText3 Linux latest version





