In today's Internet era, data has become a very important asset, which also means that data security is becoming more and more important. For an enterprise, once data leakage or loss occurs, it will not only affect the enterprise's reputation, but also directly affect the enterprise's income. In order to ensure data security, various encryption algorithms and security tools have emerged. Among these security tools, PHP also plays a very important role.
PHP is a very popular server-side scripting language that can be used to build various types of websites, from simple static websites to powerful dynamic websites. However, as websites become more complex, the need for data security increases. Especially when it comes to sensitive data such as users’ credit card information and social accounts, protecting user data has become a crucial task.
PHP provides a variety of security-related functions, such as encryption algorithms, hash functions and character escape functions. Among them, encryption algorithms are one of the important means to protect user data. In PHP, the most commonly used encryption algorithms are AES and RSA. AES is a symmetric encryption algorithm that uses the same key to encrypt and decrypt data. Symmetric encryption algorithms are generally faster, but there is a caveat that the keys need to be secure. RSA is an asymmetric encryption algorithm that uses a public key for encryption and a private key for decrypting data. This encryption algorithm is relatively slow but provides greater security and is often used to encrypt shorter text and numbers. In actual development, the appropriate encryption algorithm is usually selected based on specific needs.
In addition, PHP also provides a hash function for compressing messages of any length into a fixed-length hash value. This feature is sometimes used to encrypt sensitive data such as passwords. Common hash functions are MD5 and SHA1. The characteristic of this hash function is that it is irreversible, that is, the original data cannot be deduced from the hash value. This feature provides users and administrators with an additional layer of security, as even if the data is compromised, the hash value cannot be directly cracked.
In addition to encryption algorithms and hash functions, PHP also provides many character filtering and escaping functions. These functions are used to filter and escape special characters, prevent cross-site scripting attacks (XSS) and SQL injection attacks, etc. Cross-site scripting attacks usually occur on a website. The attacker injects some malicious scripts, making other users vulnerable to attacks when they visit the website. SQL injection attacks attack data by injecting malicious SQL statements into database query statement parameters. These attack methods can greatly undermine data security and cause unpredictable losses. Therefore, using character filtering and escaping functions to filter and escape user-entered data is an effective way to prevent these attacks.
In addition to PHP's own security functions, there are many third-party security tools that can be integrated into PHP. For example, OWASP (Open Web Application Security Project) provides a series of security tools and frameworks for detecting and repairing vulnerabilities in websites. These tools and frameworks can be used with PHP to provide an extra layer of security for your website.
In general, data security is a very important issue, especially when it comes to user data. Using security tools such as encryption algorithms, hash functions, character filtering and escaping functions provided by PHP can effectively improve the security of the website. At the same time, third-party security tools and frameworks can also be integrated to further enhance the security of the website. When developing and maintaining the website, protecting user data is an integral responsibility and obligation for us.
The above is the detailed content of Integration of PHP and data security. For more information, please follow other related articles on the PHP Chinese website!
 机器学习中的集成方法概述Apr 15, 2023 pm 01:52 PM
机器学习中的集成方法概述Apr 15, 2023 pm 01:52 PM想象一下,你正在网上购物,你发现有两家店铺销售同一种商品,它们的评分相同。然而,第一家只有一个人评分,第二家有100人评分。您会更信任哪个评分呢?最终您会选择购买哪家的商品呢?大多数人的答案很简单。100个人的意见肯定比只有一个人的意见更值得信赖。这被称为“群众的智慧”,这也是集成方法有效的原因。集成方法通常,我们只从训练数据中创建一个学习者(学习者=训练模型)(即,我们只在训练数据上训练一个机器学习模型)。而集成方法是让多个学习者解决同一个问题,然后将他们组合在一起。这些学习者被称为基础学习者
 PHP与ETL工具的集成May 16, 2023 am 11:30 AM
PHP与ETL工具的集成May 16, 2023 am 11:30 AM随着企业数据变得越来越庞大和复杂,数据处理和分析的需求变得愈发迫切。为了解决这一问题,ETL(抽取、转换、加载)工具逐渐成为了企业数据处理和分析的重要工具。PHP作为一门流行的Web开发语言,也可以通过与ETL工具的集成来提高数据处理和分析的效率和精度。ETL工具介绍ETL工具是一类能够提取数据、进行数据转换,并将数据加载到目标系统中的软件。其全称是抽取-转
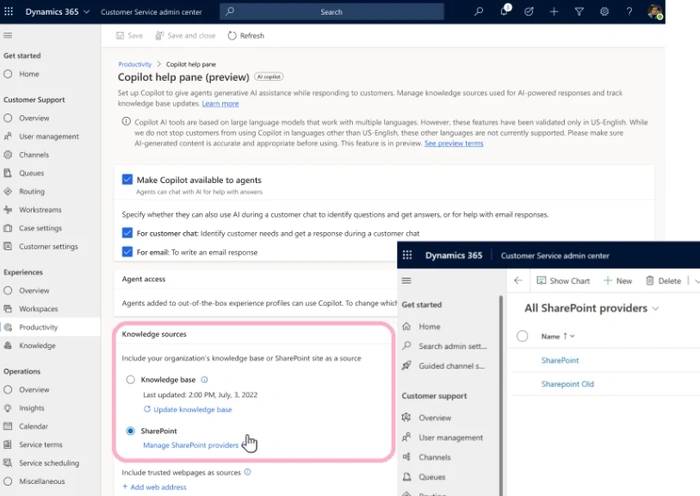 Copilot 集成:在 SharePoint 和 Dynamics 365 客户服务中的合作Aug 03, 2023 pm 09:21 PM
Copilot 集成:在 SharePoint 和 Dynamics 365 客户服务中的合作Aug 03, 2023 pm 09:21 PMMicrosoft今天宣布了Dynamics365客户服务中SharePoint与Copilot集成的早期预览版。这种集成将使客户服务代理能够访问更广泛的知识来源,从而提高生产力并改善客户互动。目前,Dynamics365客户服务中的Copilot利用内部知识库为客户服务代理提供指导。通过建议聊天和草稿电子邮件内容,Copilot已成为提高客户服务团队生产力的关键工具。但是,客户反馈表明该工具需要利用来自外部资源(如SharePoint)的知识。SharePoint协同驾驶集成为了响应这些反馈,
 Java集成阿里云OSS实现文件上传功能Jul 06, 2023 pm 04:31 PM
Java集成阿里云OSS实现文件上传功能Jul 06, 2023 pm 04:31 PMJava集成阿里云OSS实现文件上传功能阿里云OSS(ObjectStorageService)是一种简单高效、安全可靠的云存储服务,提供了海量、安全、低成本、高可靠的云存储解决方案。通过使用阿里云OSS,我们可以方便地将文件存储到云端,实现文件的上传、下载、管理等功能。本文将介绍如何使用Java语言集成阿里云OSS,实现文件上传功能。注册阿里云OSS账
 Django框架中集成WebSocketJun 17, 2023 pm 12:00 PM
Django框架中集成WebSocketJun 17, 2023 pm 12:00 PMWebSocket是一种实时通信的协议,比起HTTP协议更加轻量级和高效,可以实现类似于聊天室、实时通知等功能。在Django中,我们可以通过利用DjangoChannels库将WebSocket集成到框架中,实现实时通信。首先,我们需要安装Django和DjangoChannels库。可以通过pip工具进行安装,也可以使用conda等其他包管理工具。p
 Vue.js与Swift语言的集成,实现高级iOS应用的开发和测试的建议和技术指导Jul 29, 2023 pm 01:06 PM
Vue.js与Swift语言的集成,实现高级iOS应用的开发和测试的建议和技术指导Jul 29, 2023 pm 01:06 PMVue.js与Swift语言的集成,实现高级iOS应用的开发和测试的建议和技术指导引言移动应用的开发和测试是一个复杂而且需要专业技术的领域。两个主要的技术栈分别是前端的Vue.js和iOS平台的Swift语言。本文将介绍如何将Vue.js和Swift语言进行集成,以便开发和测试高级的iOS应用。Vue.js的基本原理和功能Vue.js是一种用于构建用户界面的
 如何在Java项目中集成并使用百度AI接口的智能图像识别功能Aug 12, 2023 pm 08:31 PM
如何在Java项目中集成并使用百度AI接口的智能图像识别功能Aug 12, 2023 pm 08:31 PM如何在Java项目中集成并使用百度AI接口的智能图像识别功能引言:随着人工智能的快速发展,图像识别技术逐渐渗透到各个领域,并提供了许多应用场景。百度AI接口提供了强大的图像识别功能,可以帮助我们在Java项目中实现图像的智能识别。本文将介绍如何在Java项目中集成并使用百度AI接口的智能图像识别功能,并提供相关的代码示例。步骤一:注册百度AI接口账号首先,我
 PHP与Cassandra的集成May 15, 2023 pm 06:51 PM
PHP与Cassandra的集成May 15, 2023 pm 06:51 PM随着大数据时代的到来以及数据增长量的不断增加,Cassandra已经成为了一种流行的分布式数据库技术。而PHP语言作为最流行的Web编程语言之一,则是Web开发领域的主流技术之一,如何让PHP和Cassandra进行无缝的集成呢?安装Cassandra在开始使用Cassandra之前,需要先安装Cassandra。Cassandra可以在官网上下载到最新的版


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

PhpStorm Mac version
The latest (2018.2.1) professional PHP integrated development tool

DVWA
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is very vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, to help web developers better understand the process of securing web applications, and to help teachers/students teach/learn in a classroom environment Web application security. The goal of DVWA is to practice some of the most common web vulnerabilities through a simple and straightforward interface, with varying degrees of difficulty. Please note that this software

SecLists
SecLists is the ultimate security tester's companion. It is a collection of various types of lists that are frequently used during security assessments, all in one place. SecLists helps make security testing more efficient and productive by conveniently providing all the lists a security tester might need. List types include usernames, passwords, URLs, fuzzing payloads, sensitive data patterns, web shells, and more. The tester can simply pull this repository onto a new test machine and he will have access to every type of list he needs.

Safe Exam Browser
Safe Exam Browser is a secure browser environment for taking online exams securely. This software turns any computer into a secure workstation. It controls access to any utility and prevents students from using unauthorized resources.

MinGW - Minimalist GNU for Windows
This project is in the process of being migrated to osdn.net/projects/mingw, you can continue to follow us there. MinGW: A native Windows port of the GNU Compiler Collection (GCC), freely distributable import libraries and header files for building native Windows applications; includes extensions to the MSVC runtime to support C99 functionality. All MinGW software can run on 64-bit Windows platforms.






