 Technology peripherals
Technology peripherals AI
AI Why edge computing and artificial intelligence strategies must complement each other
Why edge computing and artificial intelligence strategies must complement each otherWhy edge computing and artificial intelligence strategies must complement each other

Many enterprises have begun exploring edge computing use cases because of the ability to push computing power closer to data sources and closer to end users. At the same time, artificial intelligence or machine learning may be being explored or implemented, and the ability to automate discovery and gain data-driven insights has also been recognized. But if you don’t proactively combine edge and AI strategies, you’ll miss out on the potential for change.
Enter the field of artificial intelligence
There are clear signs that edge analysis and data analysis are converging. According to data, by 2025, the creation of edge data will increase by 33%, accounting for more than one-fifth of data. By 2023, data analysis professionals will focus more than 50% of their energy on creating and analyzing edge data. Edge solutions are very or extremely important to achieving the enterprise's mission. 78% of leaders believe the edge will have the greatest impact on AI and ML.
Traditionally, enterprises need to transport remote data to data centers or commercial clouds to perform analysis and extract value. This can be challenging in edge environments due to increased data volumes, limited or no network access, and the increasing need for faster decision-making in real-time.
But today, the enhanced availability of small-capacity chipsets, high-density compute and storage, and mesh networking technologies has laid the foundation for enterprises to deploy artificial intelligence workloads closer to the source of data production.
Getting Started with Edge Artificial Intelligence
To enable edge AI use cases, identify where near-real-time data decisions can significantly enhance the user experience and achieve mission goals. We are seeing an increasing number of edge use cases focused on next-generation flight kits to support law enforcement, cybersecurity and health investigations. Where investigators once collected data for subsequent processing, the new deployment suite includes advanced tools for processing and exploring data in the field.
Next, determine where to transmit large amounts of edge data. If the data can be processed at a remote location, then only the results need to be transferred. By moving only a small portion of your data, you free up bandwidth, reduce costs, and make decisions faster.
Leverage loosely coupled edge components to achieve the necessary computing power. A single sensor cannot perform processing. But high-speed mesh networks allow for connected nodes, some of which handle data collection, and others that process and so on. ML models can even be retrained at the edge to ensure continued prediction accuracy.
Infrastructure as Code for Remote AI
The best practice for edge AI is infrastructure code. Infrastructure code allows network and security configurations to be managed through configuration files rather than through physical hardware. Using infrastructure code, configuration files include infrastructure specifications, making it easier to change and distribute configurations and ensuring environments are consistently provisioned.
You can also consider using microservices and running them within them and leveraging development ops capabilities such as CI/CD pipelines, giitops, etc. to automate the iterative deployment of ML models into production environments at the edge and provide Write code once and use it anywhere with the flexibility.
We should seek to use consistent technologies and tools at the edge and core. This way, no specialized expertise is required, one-off issues are avoided, and it can be expanded more easily.
Edge Artificial Intelligence in the Real World and Beyond
Everyone from the military to law enforcement to agencies managing critical infrastructure is executing AI at the edge. For example, the International Space Station.
The International Space Station includes an on-site laboratory for conducting research and operating experiments. In one example, scientists focused on sequencing the DNA genomes of microorganisms discovered on the International Space Station. Genome sequencing generates vast amounts of data, but scientists only need to analyze a portion of it.
In the past, the International Space Station transmitted all data to ground stations for centralized processing, often with many terabytes of data per sequence. At transitional transmission rates, data could take weeks to reach scientists on Earth. But harnessing the power of edge and artificial intelligence, the research is done directly on the International Space Station, with only the results transmitted to the ground. Analysis can now be performed on the same day.
The system is easy to manage in environments where space and power are limited. Software updates are pushed to the edge of necessity and ML model training is performed on-site. And the system is flexible enough to handle other types of ML-based analysis in the future.
Combining artificial intelligence and edge computing allows enterprises to perform analytics anywhere. AI can be scaled and scaled at remote locations with a common framework from core to edge. By placing analytics close to where data is generated and users interact, decisions can be made faster, services can be delivered faster, and tasks can be scaled to wherever they are needed.
The above is the detailed content of Why edge computing and artificial intelligence strategies must complement each other. For more information, please follow other related articles on the PHP Chinese website!
 Let's Dance: Structured Movement To Fine-Tune Our Human Neural NetsApr 27, 2025 am 11:09 AM
Let's Dance: Structured Movement To Fine-Tune Our Human Neural NetsApr 27, 2025 am 11:09 AMScientists have extensively studied human and simpler neural networks (like those in C. elegans) to understand their functionality. However, a crucial question arises: how do we adapt our own neural networks to work effectively alongside novel AI s
 New Google Leak Reveals Subscription Changes For Gemini AIApr 27, 2025 am 11:08 AM
New Google Leak Reveals Subscription Changes For Gemini AIApr 27, 2025 am 11:08 AMGoogle's Gemini Advanced: New Subscription Tiers on the Horizon Currently, accessing Gemini Advanced requires a $19.99/month Google One AI Premium plan. However, an Android Authority report hints at upcoming changes. Code within the latest Google P
 How Data Analytics Acceleration Is Solving AI's Hidden BottleneckApr 27, 2025 am 11:07 AM
How Data Analytics Acceleration Is Solving AI's Hidden BottleneckApr 27, 2025 am 11:07 AMDespite the hype surrounding advanced AI capabilities, a significant challenge lurks within enterprise AI deployments: data processing bottlenecks. While CEOs celebrate AI advancements, engineers grapple with slow query times, overloaded pipelines, a
 MarkItDown MCP Can Convert Any Document into Markdowns!Apr 27, 2025 am 09:47 AM
MarkItDown MCP Can Convert Any Document into Markdowns!Apr 27, 2025 am 09:47 AMHandling documents is no longer just about opening files in your AI projects, it’s about transforming chaos into clarity. Docs such as PDFs, PowerPoints, and Word flood our workflows in every shape and size. Retrieving structured
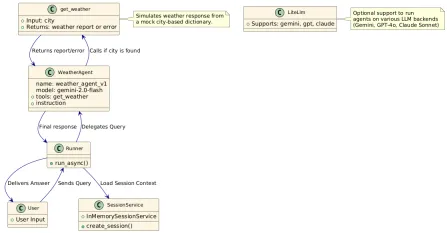 How to Use Google ADK for Building Agents? - Analytics VidhyaApr 27, 2025 am 09:42 AM
How to Use Google ADK for Building Agents? - Analytics VidhyaApr 27, 2025 am 09:42 AMHarness the power of Google's Agent Development Kit (ADK) to create intelligent agents with real-world capabilities! This tutorial guides you through building conversational agents using ADK, supporting various language models like Gemini and GPT. W
 Use of SLM over LLM for Effective Problem Solving - Analytics VidhyaApr 27, 2025 am 09:27 AM
Use of SLM over LLM for Effective Problem Solving - Analytics VidhyaApr 27, 2025 am 09:27 AMsummary: Small Language Model (SLM) is designed for efficiency. They are better than the Large Language Model (LLM) in resource-deficient, real-time and privacy-sensitive environments. Best for focus-based tasks, especially where domain specificity, controllability, and interpretability are more important than general knowledge or creativity. SLMs are not a replacement for LLMs, but they are ideal when precision, speed and cost-effectiveness are critical. Technology helps us achieve more with fewer resources. It has always been a promoter, not a driver. From the steam engine era to the Internet bubble era, the power of technology lies in the extent to which it helps us solve problems. Artificial intelligence (AI) and more recently generative AI are no exception
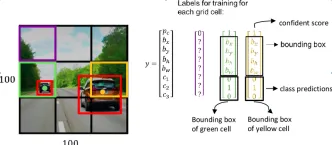 How to Use Google Gemini Models for Computer Vision Tasks? - Analytics VidhyaApr 27, 2025 am 09:26 AM
How to Use Google Gemini Models for Computer Vision Tasks? - Analytics VidhyaApr 27, 2025 am 09:26 AMHarness the Power of Google Gemini for Computer Vision: A Comprehensive Guide Google Gemini, a leading AI chatbot, extends its capabilities beyond conversation to encompass powerful computer vision functionalities. This guide details how to utilize
 Gemini 2.0 Flash vs o4-mini: Can Google Do Better Than OpenAI?Apr 27, 2025 am 09:20 AM
Gemini 2.0 Flash vs o4-mini: Can Google Do Better Than OpenAI?Apr 27, 2025 am 09:20 AMThe AI landscape of 2025 is electrifying with the arrival of Google's Gemini 2.0 Flash and OpenAI's o4-mini. These cutting-edge models, launched weeks apart, boast comparable advanced features and impressive benchmark scores. This in-depth compariso


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Atom editor mac version download
The most popular open source editor

SecLists
SecLists is the ultimate security tester's companion. It is a collection of various types of lists that are frequently used during security assessments, all in one place. SecLists helps make security testing more efficient and productive by conveniently providing all the lists a security tester might need. List types include usernames, passwords, URLs, fuzzing payloads, sensitive data patterns, web shells, and more. The tester can simply pull this repository onto a new test machine and he will have access to every type of list he needs.

Dreamweaver CS6
Visual web development tools

SublimeText3 Chinese version
Chinese version, very easy to use

DVWA
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is very vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, to help web developers better understand the process of securing web applications, and to help teachers/students teach/learn in a classroom environment Web application security. The goal of DVWA is to practice some of the most common web vulnerabilities through a simple and straightforward interface, with varying degrees of difficulty. Please note that this software






