1. The finishing touch
The adjacency list is a chain storage method for graphs. Its data structure consists of two parts: nodes and adjacency points.
Adjacency lists can be used to represent undirected graphs, directed graphs and networks. This is explained using an undirected graph.
1. Undirected graph
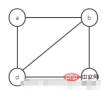
2. Linked table of undirected graph
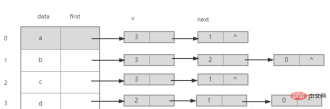
3 .Explanation
The adjacent points of node a are nodes b and d, and the storage subscripts of their adjacent points are 1 and 3. Put them into the singly linked list behind node a according to the head interpolation method (reverse order).
The adjacent points of node b are nodes a, c, and d. The storage subscripts of their adjacent points are 0, 2, and 3. Put them into the singly linked list behind node b according to the head interpolation method (reverse order). middle.
The adjacent points of node c are nodes b and d, and the storage subscripts of their adjacent points are 1 and 3. They are put into the singly linked list behind node c according to the head insertion method (reverse order).
The adjacent points of node d are nodes a, b, and c. The storage subscripts of their adjacent points are 0, 1, and 2. They are put into the singly linked list behind node d according to the head interpolation method (reverse order). middle.
4. Undirected graph
The characteristics of the adjacency list are as follows. If there are n nodes and e edges in the undirected graph, then there are n nodes in the node table and 2e in the neighbor node table. nodes.
The degree of a node is the number of nodes in the singly linked list behind the node.
2. Data structure of adjacency list
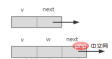
1. Node
includes node information data and a pointer to the first adjacent point first.

2. Adjacency point
Includes the storage subscript v of the adjacent point and the pointer to the next adjacent point next, if it is an adjacent point of the network , then a weight domain w needs to be added, as shown in the figure below.
3. Algorithm steps
1 Enter the number of nodes and edges.
2 Enter the node information in turn, store it in the data field of the node array Vex[], and leave the Vex[] first field blank.
3 Enter the two nodes attached to each edge in turn. If it is a network, you also need to enter the weight of the edge.
If it is an undirected graph, enter a b, query nodes a, b, store the subscripts i, j in the node array Vex[], create a new adjacent point s, let s.v = j;s .next=null;Then insert node s before the first adjacent point of the i-th node (head interpolation method). In an undirected graph, there is an edge from node a to node b, and there is an edge from node b to node a, so a new adjacency point s2 needs to be created, let s2.v = i;s2.next=null; and then let The s2 node is inserted before the first adjacent point of the j-th node (head interpolation method).
If it is an undirected graph, enter a b, query nodes a, b, store the subscripts i, j in the node array Vex[], create a new adjacent point s, let s.v = j;s .next=null;Then insert node s before the first adjacent point of the i-th node (head interpolation method).
If it is an undirected network or a directed network, it is processed in the same way as an undirected graph or a directed graph, except that the neighboring nodes have an additional weight domain.
4. Implementation
package graph;
import java.util.Scanner;
public class CreateALGraph {
static final int MaxVnum = 100; // 顶点数最大值
public static void main(String[] args) {
ALGraph G = new ALGraph();
for (int i = 0; i < G.Vex.length; i++) {
G.Vex[i] = new VexNode();
}
CreateALGraph(G); // 创建有向图邻接表
printg(G); // 输出邻接表
}
static int locatevex(ALGraph G, char x) {
for (int i = 0; i < G.vexnum; i++) // 查找顶点信息的下标
if (x == G.Vex[i].data)
return i;
return -1; // 没找到
}
// 插入一条边
static void insertedge(ALGraph G, int i, int j) {
AdjNode s = new AdjNode();
s.v = j;
s.next = G.Vex[i].first;
G.Vex[i].first = s;
}
// 输出邻接表
static void printg(ALGraph G) {
System.out.println("----------邻接表如下:----------");
for (int i = 0; i < G.vexnum; i++) {
AdjNode t = G.Vex[i].first;
System.out.print(G.Vex[i].data + ": ");
while (t != null) {
System.out.print("[" + t.v + "]\t");
t = t.next;
}
System.out.println();
}
}
// 创建有向图邻接表
static void CreateALGraph(ALGraph G) {
int i, j;
char u, v;
System.out.println("请输入顶点数和边数:");
Scanner scanner = new Scanner(System.in);
G.vexnum = scanner.nextInt();
G.edgenum = scanner.nextInt();
System.out.println("请输入顶点信息:");
for (i = 0; i < G.vexnum; i++)//输入顶点信息,存入顶点信息数组
G.Vex[i].data = scanner.next().charAt(0);
for (i = 0; i < G.vexnum; i++)
G.Vex[i].first = null;
System.out.println("请依次输入每条边的两个顶点u,v");
while (G.edgenum-- > 0) {
u = scanner.next().charAt(0);
v = scanner.next().charAt(0);
i = locatevex(G, u); // 查找顶点 u 的存储下标
j = locatevex(G, v); // 查找顶点 v 的存储下标
if (i != -1 && j != -1)
insertedge(G, i, j);
else {
System.out.println("输入顶点信息错!请重新输入!");
G.edgenum++; // 本次输入不算
}
}
}
}
// 定义邻接点类型
class AdjNode {
int v; // 邻接点下标
AdjNode next; // 指向下一个邻接点
}
// 定义顶点类型
class VexNode {
char data; // VexType为顶点的数据类型,根据需要定义
AdjNode first; // 指向第一个邻接点
}
// 定义邻接表类型
class ALGraph {
VexNode Vex[] = new VexNode[CreateALGraph.MaxVnum];
int vexnum; // 顶点数
int edgenum; // 边数
}5. Test
White is output, green is input
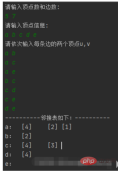
The above is the detailed content of How to use adjacency list to store graph in Java. For more information, please follow other related articles on the PHP Chinese website!
 Is Java Platform Independent if then how?May 09, 2025 am 12:11 AM
Is Java Platform Independent if then how?May 09, 2025 am 12:11 AMJava is platform-independent because of its "write once, run everywhere" design philosophy, which relies on Java virtual machines (JVMs) and bytecode. 1) Java code is compiled into bytecode, interpreted by the JVM or compiled on the fly locally. 2) Pay attention to library dependencies, performance differences and environment configuration. 3) Using standard libraries, cross-platform testing and version management is the best practice to ensure platform independence.
 The Truth About Java's Platform Independence: Is It Really That Simple?May 09, 2025 am 12:10 AM
The Truth About Java's Platform Independence: Is It Really That Simple?May 09, 2025 am 12:10 AMJava'splatformindependenceisnotsimple;itinvolvescomplexities.1)JVMcompatibilitymustbeensuredacrossplatforms.2)Nativelibrariesandsystemcallsneedcarefulhandling.3)Dependenciesandlibrariesrequirecross-platformcompatibility.4)Performanceoptimizationacros
 Java Platform Independence: Advantages for web applicationsMay 09, 2025 am 12:08 AM
Java Platform Independence: Advantages for web applicationsMay 09, 2025 am 12:08 AMJava'splatformindependencebenefitswebapplicationsbyallowingcodetorunonanysystemwithaJVM,simplifyingdeploymentandscaling.Itenables:1)easydeploymentacrossdifferentservers,2)seamlessscalingacrosscloudplatforms,and3)consistentdevelopmenttodeploymentproce
 JVM Explained: A Comprehensive Guide to the Java Virtual MachineMay 09, 2025 am 12:04 AM
JVM Explained: A Comprehensive Guide to the Java Virtual MachineMay 09, 2025 am 12:04 AMTheJVMistheruntimeenvironmentforexecutingJavabytecode,crucialforJava's"writeonce,runanywhere"capability.Itmanagesmemory,executesthreads,andensuressecurity,makingitessentialforJavadeveloperstounderstandforefficientandrobustapplicationdevelop
 Key Features of Java: Why It Remains a Top Programming LanguageMay 09, 2025 am 12:04 AM
Key Features of Java: Why It Remains a Top Programming LanguageMay 09, 2025 am 12:04 AMJavaremainsatopchoicefordevelopersduetoitsplatformindependence,object-orienteddesign,strongtyping,automaticmemorymanagement,andcomprehensivestandardlibrary.ThesefeaturesmakeJavaversatileandpowerful,suitableforawiderangeofapplications,despitesomechall
 Java Platform Independence: What does it mean for developers?May 08, 2025 am 12:27 AM
Java Platform Independence: What does it mean for developers?May 08, 2025 am 12:27 AMJava'splatformindependencemeansdeveloperscanwritecodeonceandrunitonanydevicewithoutrecompiling.ThisisachievedthroughtheJavaVirtualMachine(JVM),whichtranslatesbytecodeintomachine-specificinstructions,allowinguniversalcompatibilityacrossplatforms.Howev
 How to set up JVM for first usage?May 08, 2025 am 12:21 AM
How to set up JVM for first usage?May 08, 2025 am 12:21 AMTo set up the JVM, you need to follow the following steps: 1) Download and install the JDK, 2) Set environment variables, 3) Verify the installation, 4) Set the IDE, 5) Test the runner program. Setting up a JVM is not just about making it work, it also involves optimizing memory allocation, garbage collection, performance tuning, and error handling to ensure optimal operation.
 How can I check Java platform independence for my product?May 08, 2025 am 12:12 AM
How can I check Java platform independence for my product?May 08, 2025 am 12:12 AMToensureJavaplatformindependence,followthesesteps:1)CompileandrunyourapplicationonmultipleplatformsusingdifferentOSandJVMversions.2)UtilizeCI/CDpipelineslikeJenkinsorGitHubActionsforautomatedcross-platformtesting.3)Usecross-platformtestingframeworkss


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

MinGW - Minimalist GNU for Windows
This project is in the process of being migrated to osdn.net/projects/mingw, you can continue to follow us there. MinGW: A native Windows port of the GNU Compiler Collection (GCC), freely distributable import libraries and header files for building native Windows applications; includes extensions to the MSVC runtime to support C99 functionality. All MinGW software can run on 64-bit Windows platforms.

VSCode Windows 64-bit Download
A free and powerful IDE editor launched by Microsoft

SAP NetWeaver Server Adapter for Eclipse
Integrate Eclipse with SAP NetWeaver application server.

SublimeText3 Chinese version
Chinese version, very easy to use

MantisBT
Mantis is an easy-to-deploy web-based defect tracking tool designed to aid in product defect tracking. It requires PHP, MySQL and a web server. Check out our demo and hosting services.







