The traditional approach is generally:
1. Modify the log level in the configuration
2. Restart the application
3. Check the error log to troubleshoot the problem when the problem occurs
This process requires restarting the application, which is more troublesome and less efficient. Moreover, for large-scale online projects, it is impossible to stop and restart at will. So is there a way to dynamically change the log level without restarting the application?
Now, let Lao Wan teach you how to dynamically modify the log level through SpringBoot's actuator component.
1. Add dependencies
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-actuator</artifactId>
</dependency>2. Configure the port exposed by actuator
#启用actuator端口 management.endpoints.enabled-by-default=fasle #设置actuator的访问根路径,默认是/actuator management.endpoints.web.base-path=/message #启用的端点 management.endpoints.web.exposure.include=loggers
Here I modified the default access path of actuator/actuator to /message, for It is saved consistent with the basic access path of the project.
Two configuration methods to enable the port:
Method 1: (Recommended)
management.endpoints.web.exposure.include=loggers
Method 2: (Test in this way Not effective)
management.endpoint.loggers.enabled=true
Additional: How to disable the info port
management.endpoints.enabled-by-default=false management.endpoint.info.enabled=true
About the actuator component, it is called one of the four major components of spring boot and has powerful functions. Everyone can find some information on the Internet to learn more.
actuator’s endpoint port description:
| ID | Description | Enabled by default |
|---|---|---|
| auditevents | Display the audit event information of the current application | Yes |
| beans | Display a complete list of all Spring Beans in an application | Yes |
| conditions | Display configuration and auto-configuration classes configuration classes) and the reasons why they are applied or not applied | Yes |
| configprops | Display a collection list of all @ConfigurationProperties | Yes |
| env | Display properties of ConfigurableEnvironment from Spring | Yes |
| flyway | Display the database migration path, if any | Yes |
| health | Display the health information of the application (when A simple "status" is displayed when accessing using an unauthenticated connection, and full information details are displayed when accessing using an authenticated connection) | Yes |
| info | Display any application information | Yes |
| liquibase | Display any Liquibase database migration path, if any | Yes |
| metrics | Display the metrics information of the current application | Yes |
| mappings | Display a collection list of all @RequestMapping paths | Yes |
| scheduledtasks | Display scheduled tasks in the application | Yes |
| sessions | Allows the retrieval and deletion of user sessions from the session store supported by Spring sessions. Not available when using Spring Session's support for reactive web applications. | Yes |
| shutdown | Allow apps to shut down gracefully (not enabled by default) | No |
| threaddump | Execute a thread dump | Yes |
If using web application (Spring MVC, Spring WebFlux, or Jersey), you can also use the following endpoints:
| ID | Description | Enabled by default |
|---|---|---|
| heapdum | Return a GZip compressed hprof heap dump file | Yes |
| jolokia | Exposing JMX beans over HTTP (WebFlux is not available when Jolokia is on the classpath) | Yes |
| logfile | Return Log file content (if the logging.file or logging.path attribute is set), supports using the HTTP Range header to receive partial information about the log file content | Yes |
| Display metrics information in a format that can be crawled by the Prometheus server | Yes |
| Default | |
|---|---|
| * | ##management.endpoints.jmx.exposure.include |
| management.endpoints.web.exposure.exclude | |
| ##management.endpoints.web.exposure.include | |
|
*可以用来选择所有端点。 例如,要通过HTTP公开除env和beans端点之外的所有内容,请使用以下属性: management.endpoints.web.exposure.include=* management.endpoints.web.exposure.exclude=env,beans 三、关闭鉴权一般我们会将actuator和spring security鉴权组件结合使用,防止这些功能端口被随便调用。由于这里是功能演示,先放开actuator相关端口的权限认证。
此外,如果存在Spring Security,则需要添加自定义安全配置,以允许对端点进行未经身份验证的访问,如以下示例所示:放开所有Endpoint端点进行匹配 @Configuration
public class ActuatorSecurity extends WebSecurityConfigurerAdapter {
@Override
protected void configure(HttpSecurity http) throws Exception {
http.requestMatcher(EndpointRequest.toAnyEndpoint()).authorizeRequests()
.anyRequest().permitAll()
}
}四 、通过/loggers端口查看日志级别
注意上面我说过的,我调整了management.endpoints.web.base-path=/message。如果没有设置此参数,则使用默认的/actuator去访问。
五、发起http请求修改日志级别这里演示,修改目录com.wxswj.provider.message.controller的日志级别为debug 请求类型为POST,参数格式是JSON curl -H "Content-Type: application/json" -X POST --data
"
{
"configuredLevel": "DEBUG"
}
"
http://localhost:8090/message/loggers/com.wxswj.provider.message.controller大家可以在服务器上通过curl发起http请求,或者通过Postman发起请求。 curl -H "Content-Type: application/json" -X POST --data "{"configuredLevel": "DEBUG"}" http://localhost:8090/loggers/com.wxswj.provider.message.controller六、查询日志级别修改结果
{
"configuredLevel": "DEBUG",
"effectiveLevel": "DEBUG"
}说明我们的修改日志级别的请求生效。 |
The above is the detailed content of What is the operation of SpringBoot to dynamically modify the log level?. For more information, please follow other related articles on the PHP Chinese website!
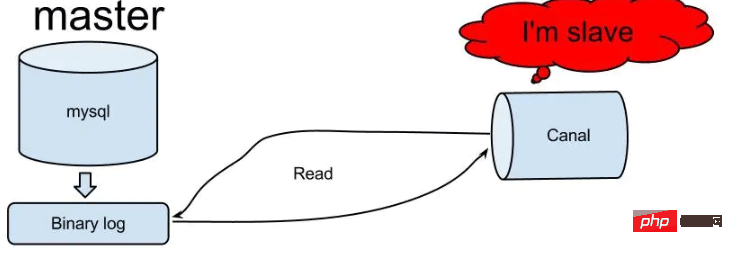 怎么使用SpringBoot+Canal实现数据库实时监控May 10, 2023 pm 06:25 PM
怎么使用SpringBoot+Canal实现数据库实时监控May 10, 2023 pm 06:25 PMCanal工作原理Canal模拟MySQLslave的交互协议,伪装自己为MySQLslave,向MySQLmaster发送dump协议MySQLmaster收到dump请求,开始推送binarylog给slave(也就是Canal)Canal解析binarylog对象(原始为byte流)MySQL打开binlog模式在MySQL配置文件my.cnf设置如下信息:[mysqld]#打开binloglog-bin=mysql-bin#选择ROW(行)模式binlog-format=ROW#配置My
 Spring Boot怎么使用SSE方式向前端推送数据May 10, 2023 pm 05:31 PM
Spring Boot怎么使用SSE方式向前端推送数据May 10, 2023 pm 05:31 PM前言SSE简单的来说就是服务器主动向前端推送数据的一种技术,它是单向的,也就是说前端是不能向服务器发送数据的。SSE适用于消息推送,监控等只需要服务器推送数据的场景中,下面是使用SpringBoot来实现一个简单的模拟向前端推动进度数据,前端页面接受后展示进度条。服务端在SpringBoot中使用时需要注意,最好使用SpringWeb提供的SseEmitter这个类来进行操作,我在刚开始时使用网上说的将Content-Type设置为text-stream这种方式发现每次前端每次都会重新创建接。最
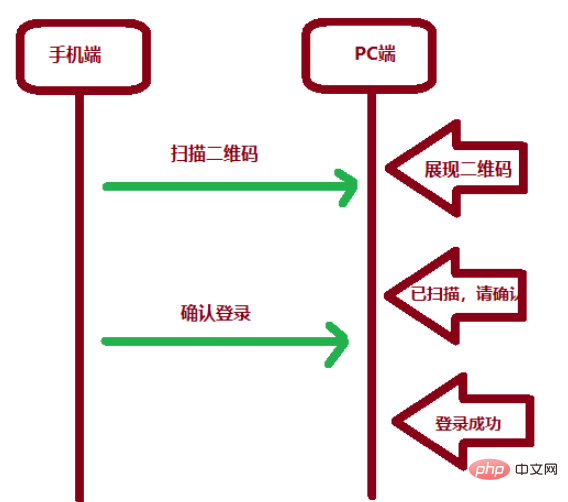 SpringBoot怎么实现二维码扫码登录May 10, 2023 pm 08:25 PM
SpringBoot怎么实现二维码扫码登录May 10, 2023 pm 08:25 PM一、手机扫二维码登录的原理二维码扫码登录是一种基于OAuth3.0协议的授权登录方式。在这种方式下,应用程序不需要获取用户的用户名和密码,只需要获取用户的授权即可。二维码扫码登录主要有以下几个步骤:应用程序生成一个二维码,并将该二维码展示给用户。用户使用扫码工具扫描该二维码,并在授权页面中授权。用户授权后,应用程序会获取一个授权码。应用程序使用该授权码向授权服务器请求访问令牌。授权服务器返回一个访问令牌给应用程序。应用程序使用该访问令牌访问资源服务器。通过以上步骤,二维码扫码登录可以实现用户的快
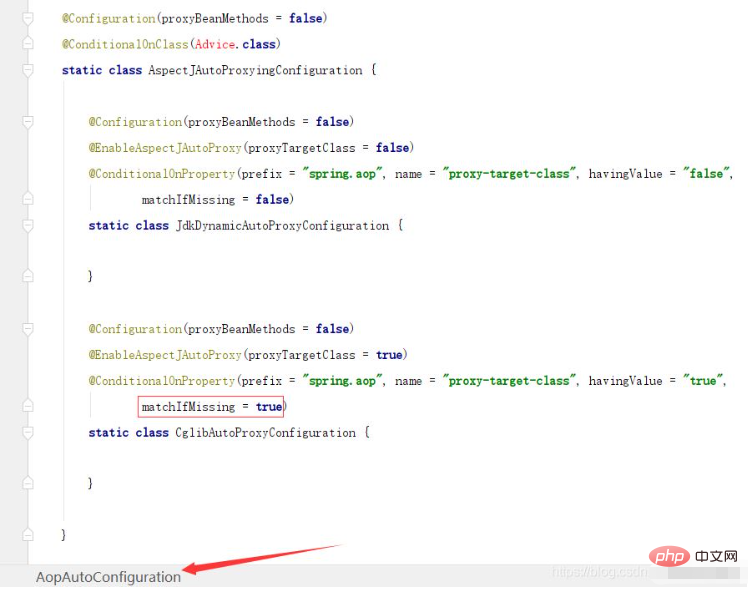 SpringBoot/Spring AOP默认动态代理方式是什么May 10, 2023 pm 03:52 PM
SpringBoot/Spring AOP默认动态代理方式是什么May 10, 2023 pm 03:52 PM1.springboot2.x及以上版本在SpringBoot2.xAOP中会默认使用Cglib来实现,但是Spring5中默认还是使用jdk动态代理。SpringAOP默认使用JDK动态代理,如果对象没有实现接口,则使用CGLIB代理。当然,也可以强制使用CGLIB代理。在SpringBoot中,通过AopAutoConfiguration来自动装配AOP.2.Springboot1.xSpringboot1.xAOP默认还是使用JDK动态代理的3.SpringBoot2.x为何默认使用Cgl
 spring boot怎么对敏感信息进行加解密May 10, 2023 pm 02:46 PM
spring boot怎么对敏感信息进行加解密May 10, 2023 pm 02:46 PM我们使用jasypt最新版本对敏感信息进行加解密。1.在项目pom文件中加入如下依赖:com.github.ulisesbocchiojasypt-spring-boot-starter3.0.32.创建加解密公用类:packagecom.myproject.common.utils;importorg.jasypt.encryption.pbe.PooledPBEStringEncryptor;importorg.jasypt.encryption.pbe.config.SimpleStrin
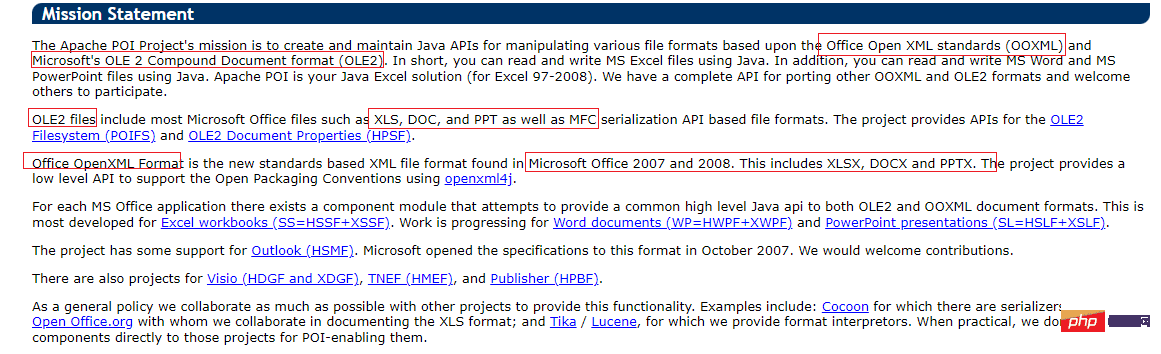 使用Java SpringBoot集成POI实现Word文档导出Apr 21, 2023 pm 12:19 PM
使用Java SpringBoot集成POI实现Word文档导出Apr 21, 2023 pm 12:19 PM知识准备需要理解ApachePOI遵循的标准(OfficeOpenXML(OOXML)标准和微软的OLE2复合文档格式(OLE2)),这将对应着API的依赖包。什么是POIApachePOI是用Java编写的免费开源的跨平台的JavaAPI,ApachePOI提供API给Java程序对MicrosoftOffice格式档案读和写的功能。POI为“PoorObfuscationImplementation”的首字母缩写,意为“简洁版的模糊实现”。ApachePOI是创建和维护操作各种符合Offic
 springboot怎么整合shiro实现多验证登录功能May 10, 2023 pm 04:19 PM
springboot怎么整合shiro实现多验证登录功能May 10, 2023 pm 04:19 PM1.首先新建一个shiroConfigshiro的配置类,代码如下:@ConfigurationpublicclassSpringShiroConfig{/***@paramrealms这儿使用接口集合是为了实现多验证登录时使用的*@return*/@BeanpublicSecurityManagersecurityManager(Collectionrealms){DefaultWebSecurityManagersManager=newDefaultWebSecurityManager();
 Springboot如何实现视频上传及压缩功能May 10, 2023 pm 05:16 PM
Springboot如何实现视频上传及压缩功能May 10, 2023 pm 05:16 PM一、定义视频上传请求接口publicAjaxResultvideoUploadFile(MultipartFilefile){try{if(null==file||file.isEmpty()){returnAjaxResult.error("文件为空");}StringossFilePrefix=StringUtils.genUUID();StringfileName=ossFilePrefix+"-"+file.getOriginalFilename(


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

DVWA
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is very vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, to help web developers better understand the process of securing web applications, and to help teachers/students teach/learn in a classroom environment Web application security. The goal of DVWA is to practice some of the most common web vulnerabilities through a simple and straightforward interface, with varying degrees of difficulty. Please note that this software

SublimeText3 Mac version
God-level code editing software (SublimeText3)

PhpStorm Mac version
The latest (2018.2.1) professional PHP integrated development tool

Safe Exam Browser
Safe Exam Browser is a secure browser environment for taking online exams securely. This software turns any computer into a secure workstation. It controls access to any utility and prevents students from using unauthorized resources.

Zend Studio 13.0.1
Powerful PHP integrated development environment









